DAI Dynamic ARP Inspection
Sections:
- What is ARP Poisoning?
- Lab Topology
- Ettercap Setup
- ARP Poisoning Effects
- DAI Configuration
- DAI Validation
Overview:
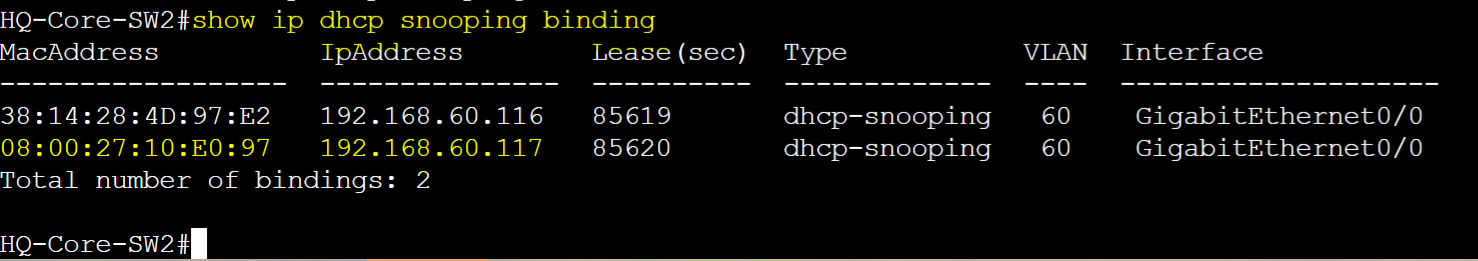
- Just like DHCP Snooping, Dynamic ARP Inspection is a security feature that helps protect the network from ARP spoofing or ARP poisoning attacks
- ARP Spoofing is a MITM attack technique used to send fake ARP messages onto the network most commonly attackers associating their own MAC address with the IP address of another device such as the default gateway of the network
- Dynamic ARP Inspection can only be enabled in conjunction with DHCP Snooping as switches use the DHCP Snooping binding table to validate ARP packets being forwarded onto the network based on the IP-MAC address pairs
- DAI ensures that devices can only associate IP addresses with the correct MAC addresses from the DHCP Snooping binding table, preventing attackers from spoofing ARP messages
- By default all ports are untrusted when DAI is enabled
- DAI trusted ports allow network devices such as switches to send ARP packets without being inspected
- DAI untrusted ports have their ARP packets validated against the DHCP Snooping binding table to ensure only legitimate devices can send ARP responses
- Just like DHCP Snooping, DAI supports features such as Rate Limit and Rate Limit bursting
ARP Poisoning
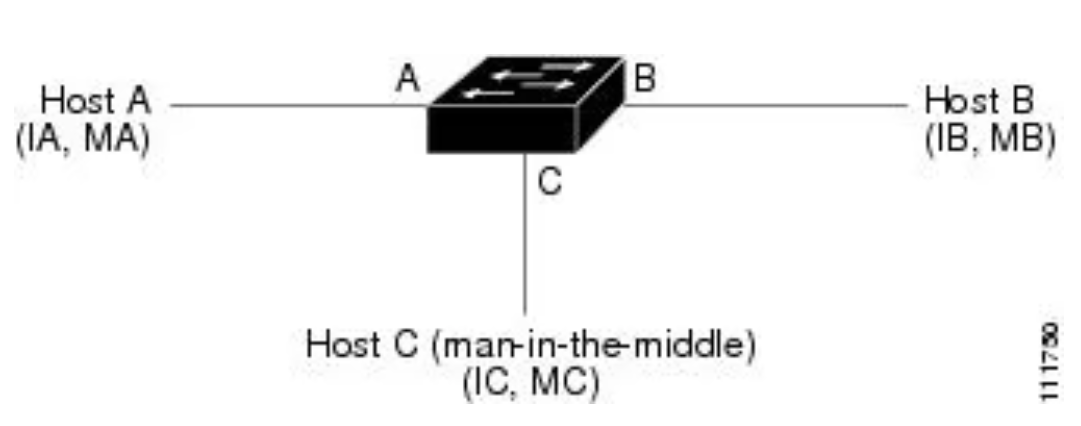
To better understand DAI, let's go over an example of how attackers poison ARP tables of other hosts. ARP is a layer 2 protocol that is used in a broadcast domain to map an IP address to a MAC address. For example, Host A wants to communicate with Host B but does not have the MAC address of Host B in its ARP cache. Host A generates an ARP broadcast message for all hosts within the broadcast domain to ideally obtain the MAC address associated with the IP address of Host B. Host B responds with its MAC address but consequently, the ARP protocol allows for gratuitous reply messages from any host even if an ARP request was not received. This in turn increases the risk for an ARP spoofing/poisoning attack. After the results of an attack, all traffic from affected hosts will flow through the attacker's device and eventually to the host representing a successful MITM attack.
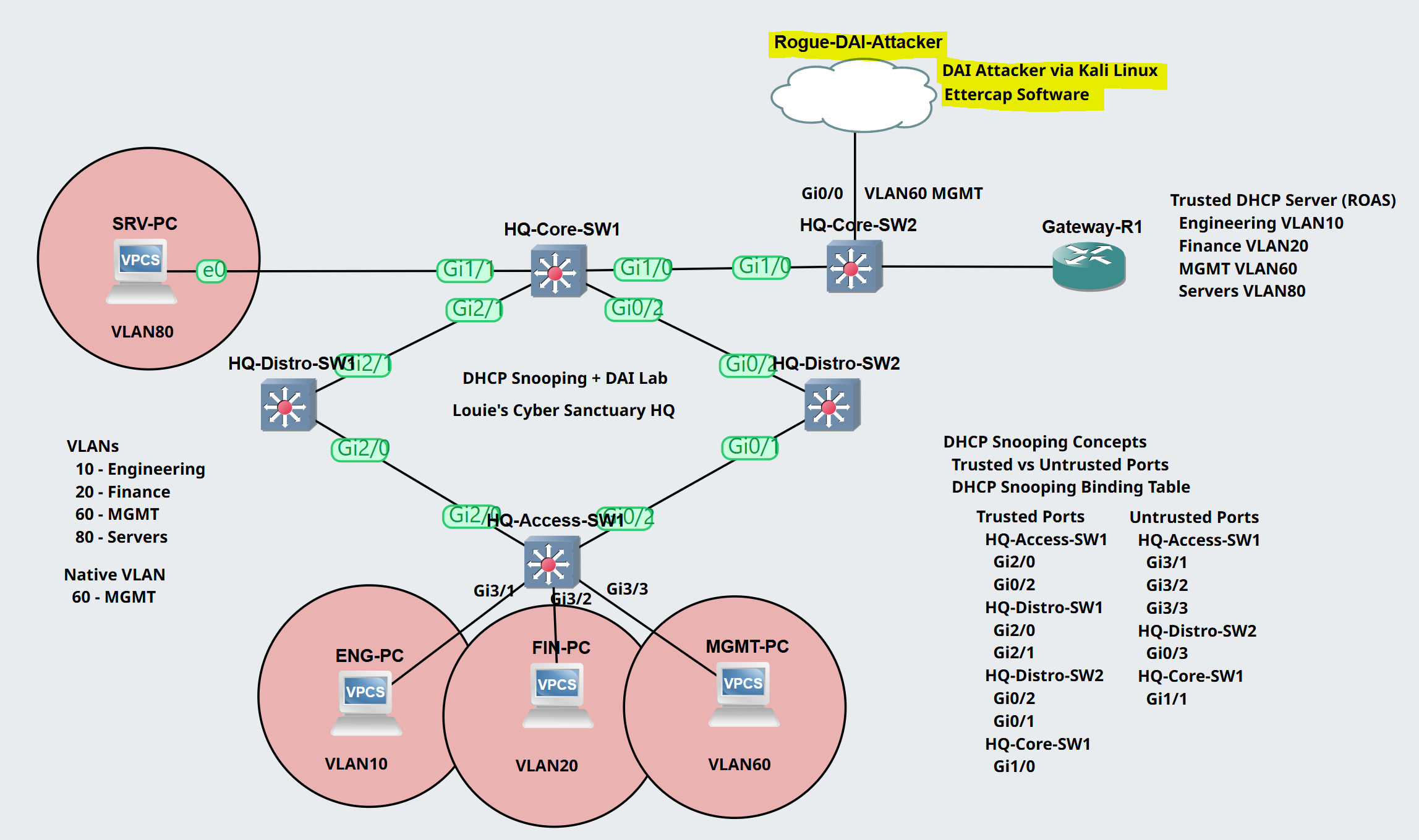
Lab Topology - ARP Poisoning Attack with Kali Linux
Scenario:
- In this lab scenario, we will utilize Kali Linux to poison the ARP caches of the MGMT PC on VLAN60 and the Gateway-R1 router to establish a Man in the Middle attack
- Trunk links, VLAN assignments, and ROAS Inter-VLAN routing have already been configured at the HQ site topology. The Kali Linux VM will receive an IP address from the VLAN60 DHCP pool on Gateway-R1
- In this lab example, I will demonstrate a Wireshark capture from the Kali Linux ethernet interface displaying poisoned ARP packet entries towards the affected hosts
- I will then analyze the poisoned ARP cache entry of the MGMT PC and the Gateway-R1 router
Ettercap Setup
In this example, I have brought up a Kali Linux VM instance using Oracle VirtualBox that includes the Ettercap software.
Ettercap is an open-source network security tool primarily used for man-in-the-middle (MITM) attacks on LANs. It is designed for packet sniffing, interception, and modification of network traffic, making it a useful tool for network analysis, security testing, and troubleshooting.

Kali Linux
Kali Linux VM GUI

Enabling DHCP on the Linux interface to receive an address from Gateway-R1 router
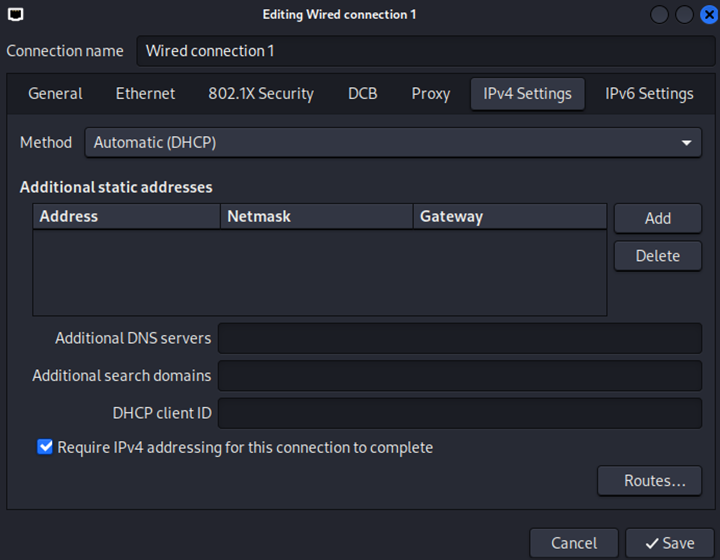
DHCP IP address received and assigned to the ethernet interface. The MAC address of the ethernet interface ending in ':e0:97' will play a big role during ARP entry modifications
Ettercap software GUI
Starting packet capture on Linux machine via its ethernet interface
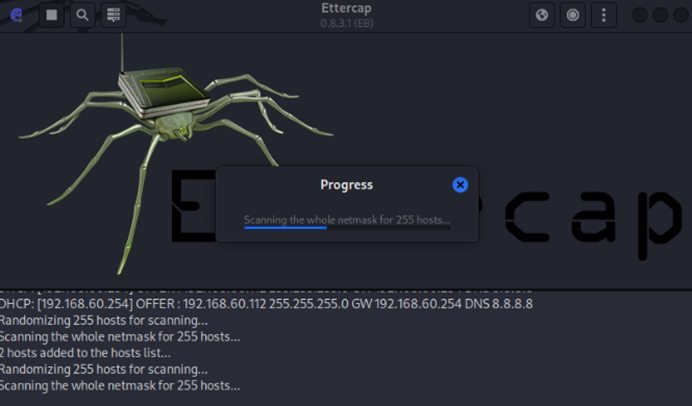
Sending ARP broadcast messages to entire VLAN60 subnet to identify active hosts
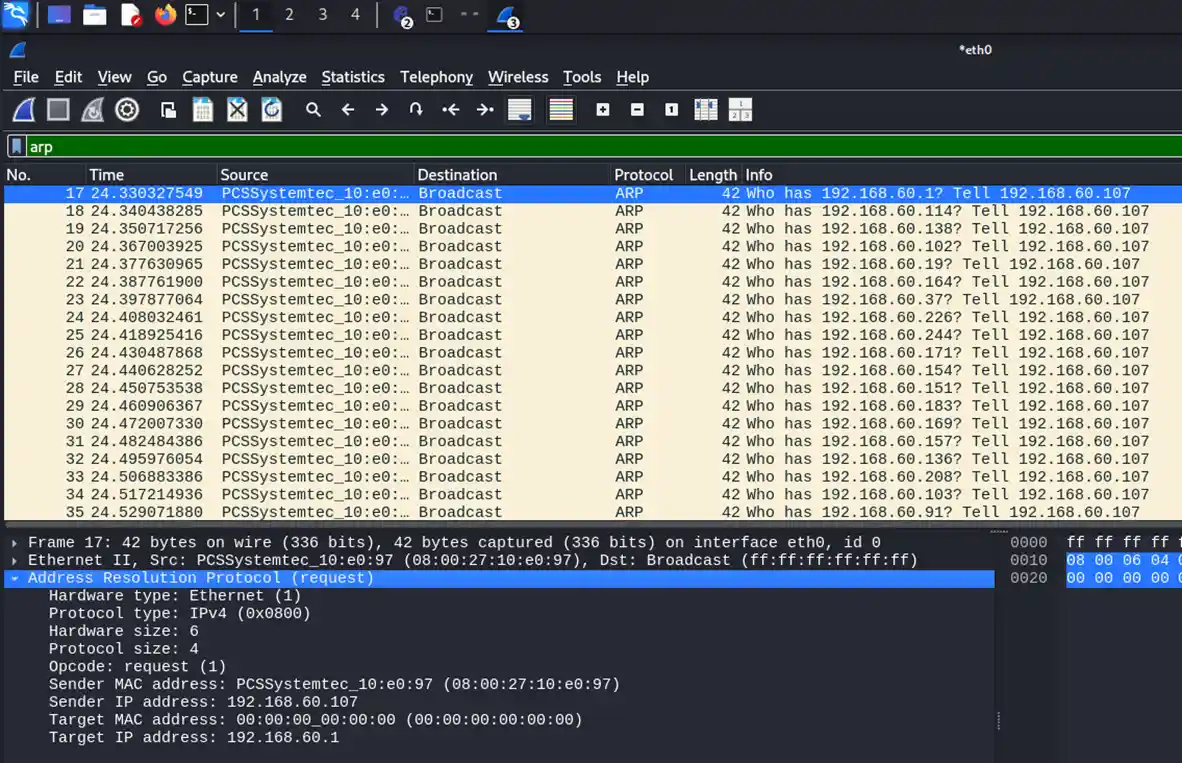
ARP broadcast packets to the HQ network via Wireshark
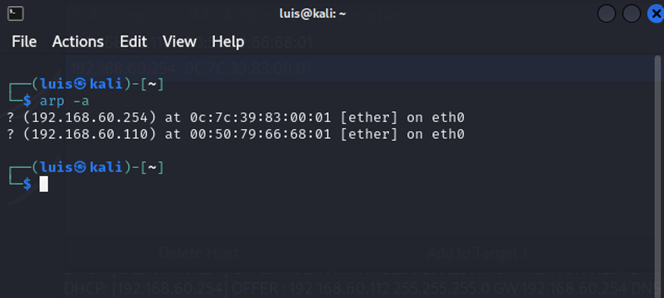
ARP table displaying active hosts on the Linux machine
- 192.168.60.254 - Default Gateway / VLAN60 sub-interface of Gateway-R1
- 192.168.60.110 - MGMT PC on VLAN60
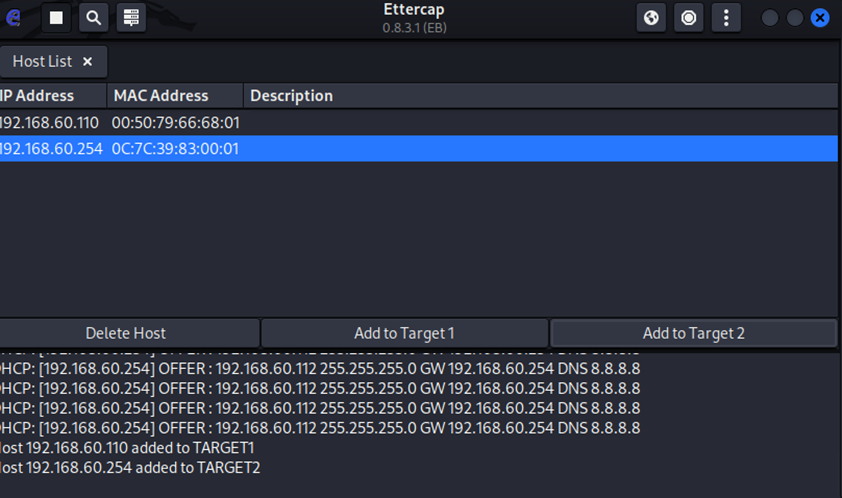
Active host list in Ettercap after performing the ARP broadcast. Assigning both host victims as targets for the ARP poison attack
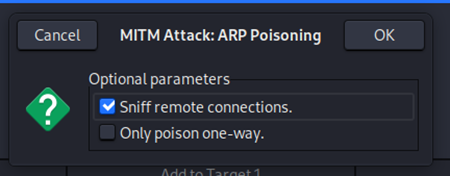
Menu option in Ettercap to perform the ARP poison attack
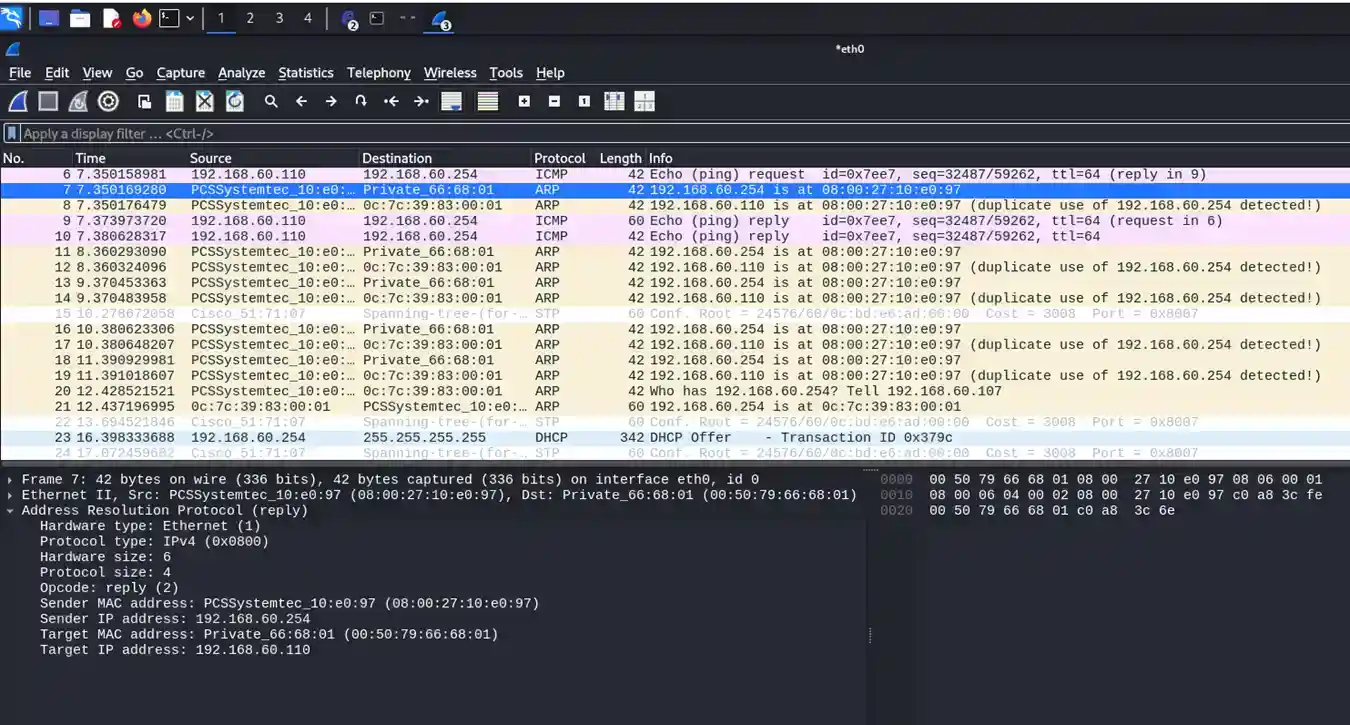
Wireshark capture of gratuitous ARP messages being sent out via Linux's ethernet interface to poison the ARP caches of MGMT PC and the VLAN60 default gateway
- IP Addresses
- MGMT PC: 192.168.60.110
- VLAN60 gateway: 192.168.60.254
- Both victim IP addresses assigned to the MAC address of the attack Linux machine
- Attack machine MAC address: 0800.2710.e097
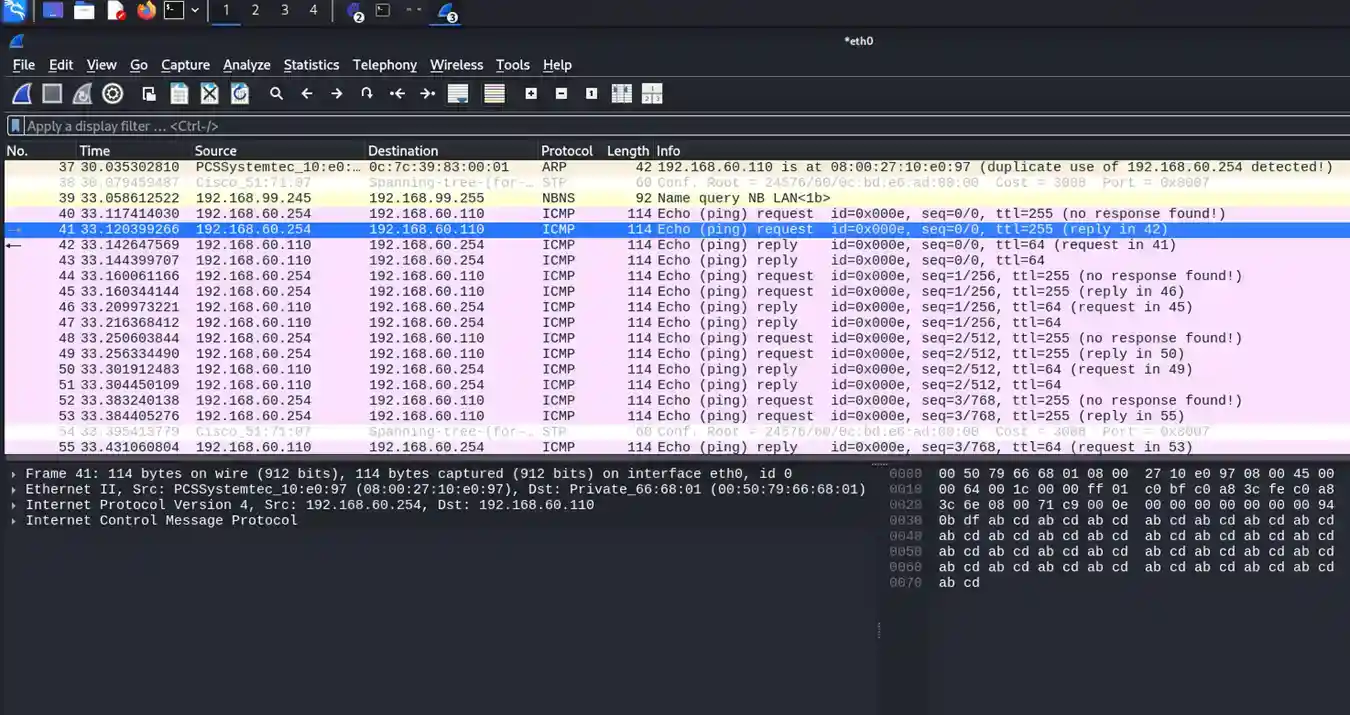
Wireshark capture of ICMP messages between MGMT PC & Gateway-R1 redirected back to the attack machine
ARP Poisoning Effects
MGMT PC VLAN60
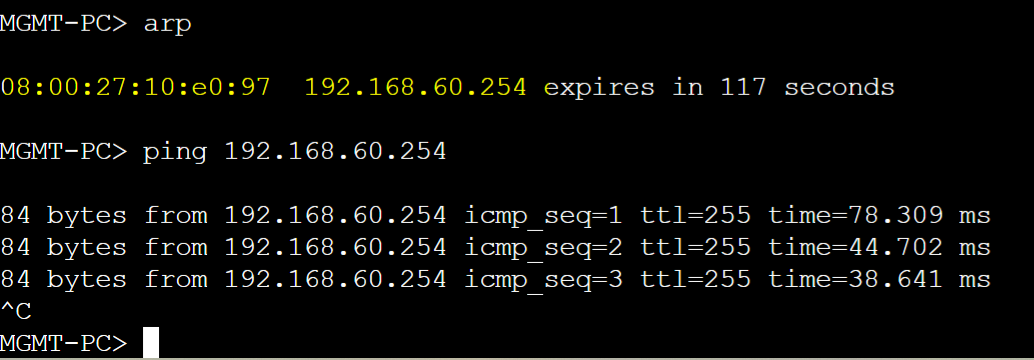
Poisoned Gateway-R1 ARP entry displayed on MGMT PC ARP table
Gateway-R1
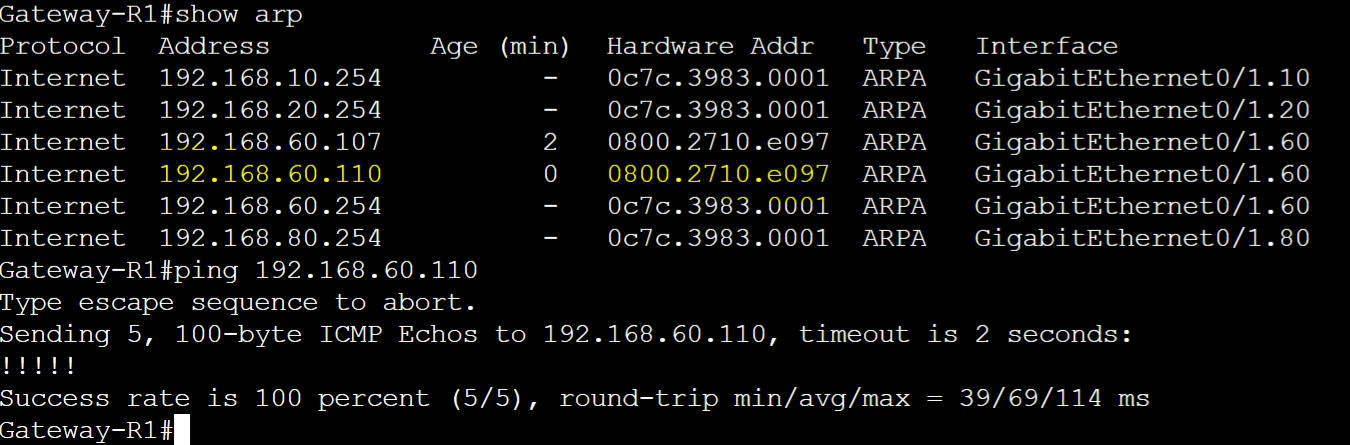
Poisoned MGMT-PC ARP entry displayed on Gateway-R1 ARP table
DAI Dynamic ARP Inspection Configuration
Scenario:
- In this lab scenario, we will configure Dynamic ARP Inspection as an added layer of security in conjunction with DHCP Snooping
- Trunk links, VLAN assignments, and ROAS Inter-VLAN routing have already been configured at the HQ site topology
- After configuring DAI on all untrusted ports on the switches, I will attempt to perform an ARP poison attack from the Kali Linux attack machine off of HQ-Core-SW2

HQ-Access-SW1
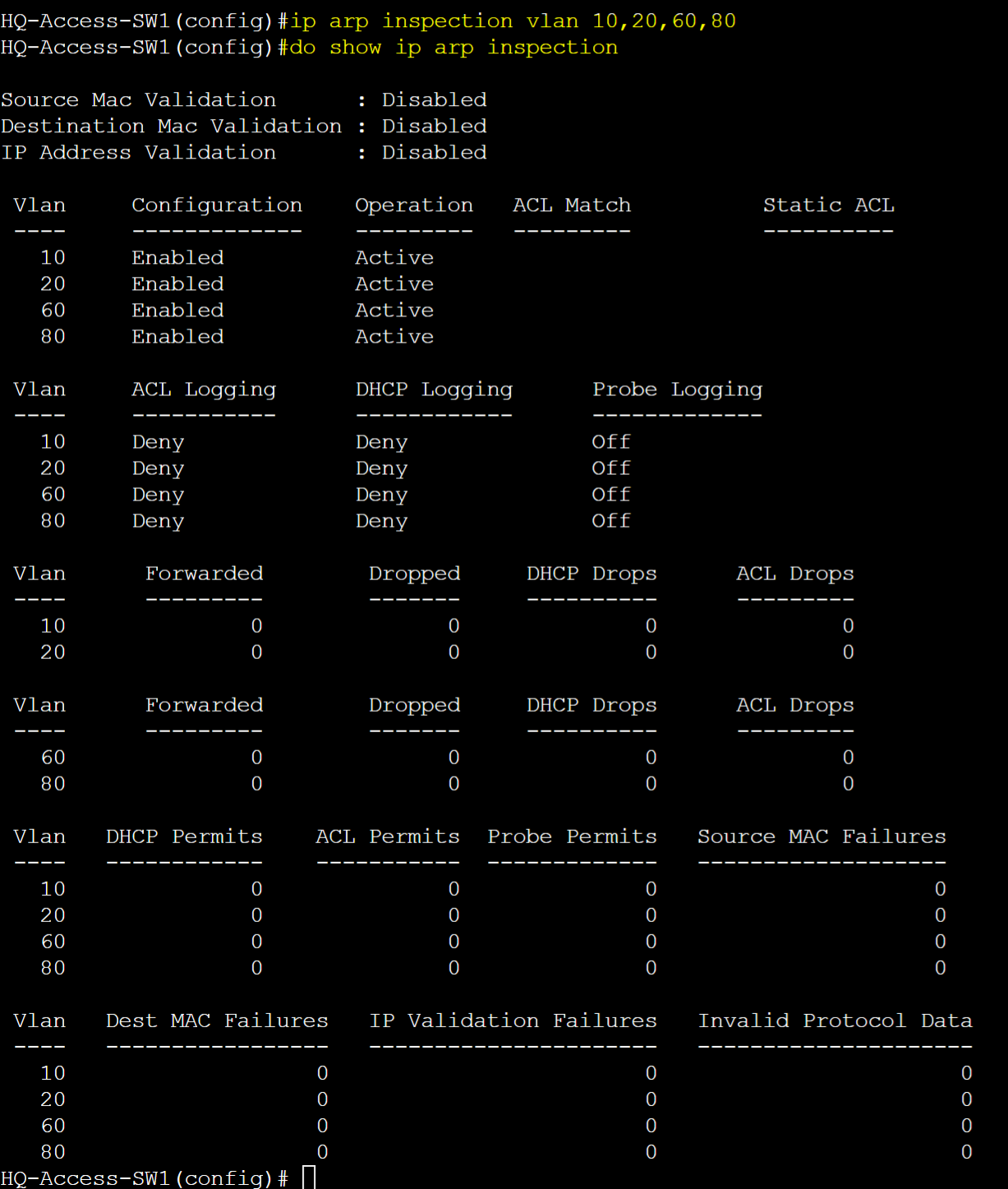
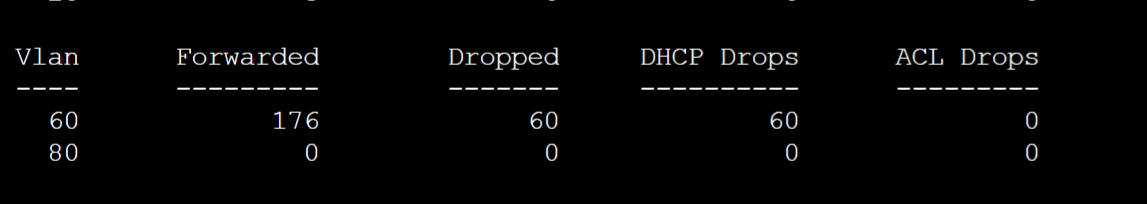
Base configuration of DAI applied to specific VLANs. Show command to analyze vlan statistics
Notes:
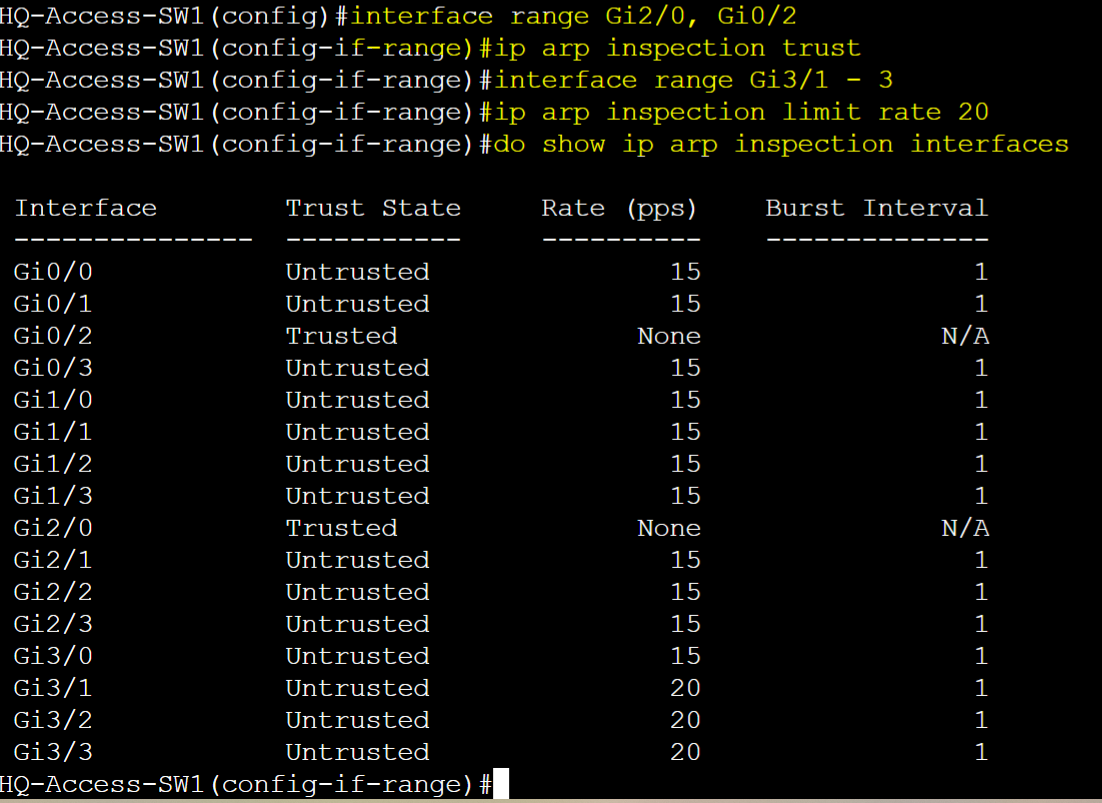
- Trunk ports defined as trusted ports. For demonstration, Rate limit feature has been changed from the default value of 15 to 20 for the untrusted access ports. Show command to view trusted and untrusted port rate limit statistics
- If an access port sends more than 20 ARP packets in a second, the interface is error disabled
- Trusted ports do not get checked by DAI and is best practice to configure trusted ports on trunk links or point to point links towards other network devices such as switches
- Untrusted ports should be assigned to all access ports connecting to clients so DAI on the switch can perform DAI inspections
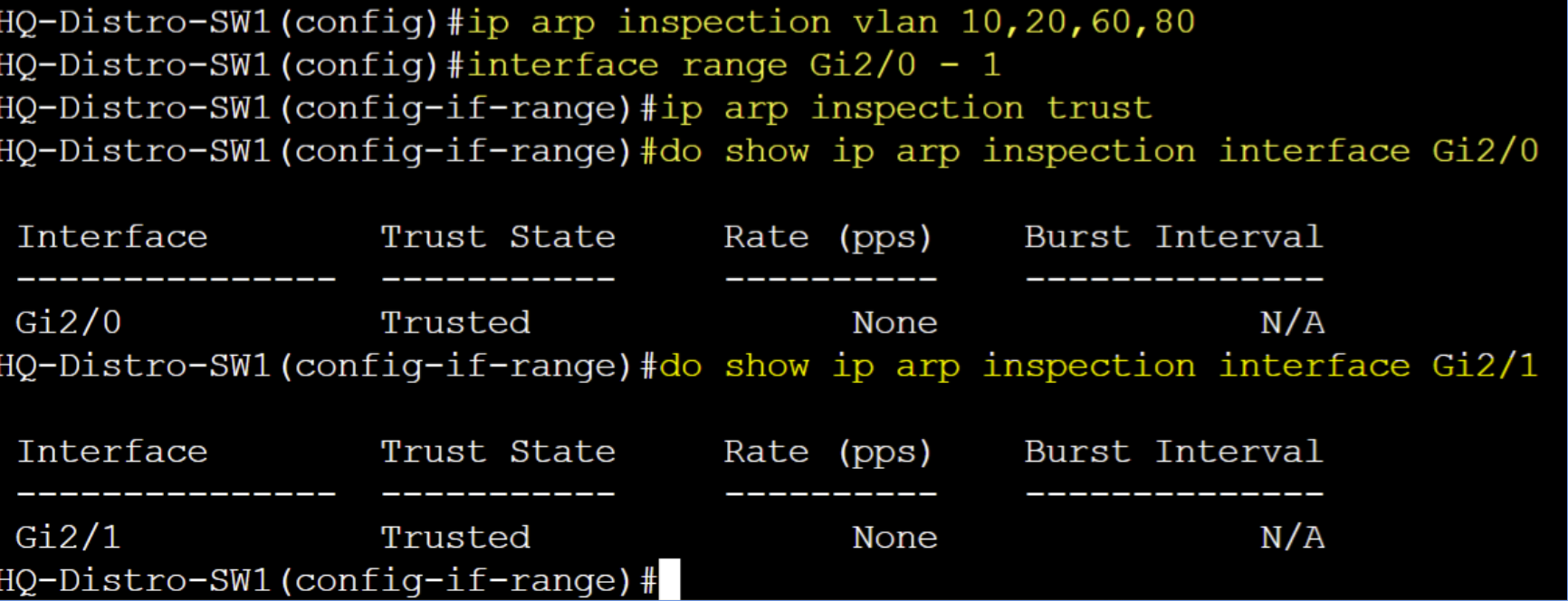
HQ-Distro-SW1
DAI enabled for each VLAN. Trusted ports for trunk links defined. Verify trusted ports.
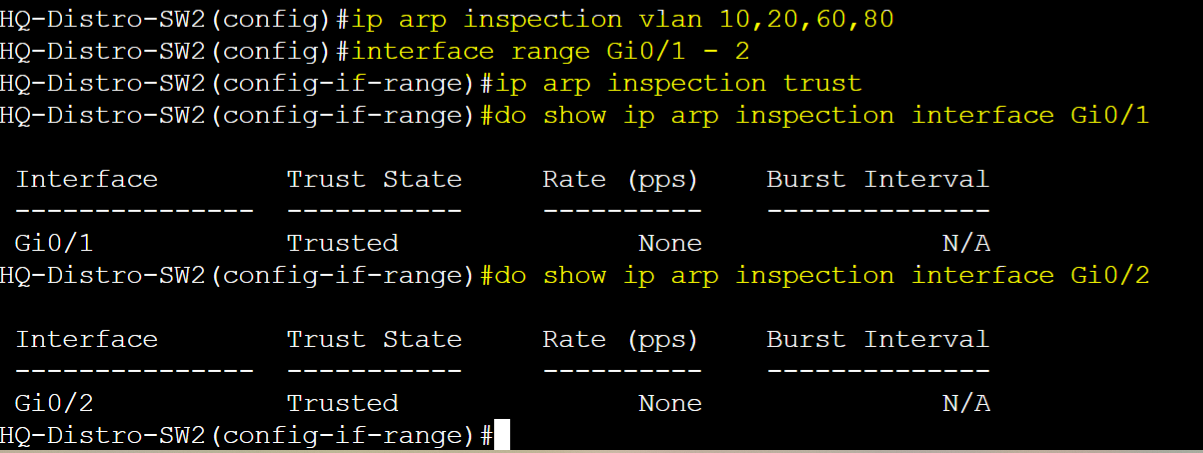
HQ-Distro-SW2
DAI enabled for each VLAN. Trusted ports for trunk links defined. Verify trusted ports.
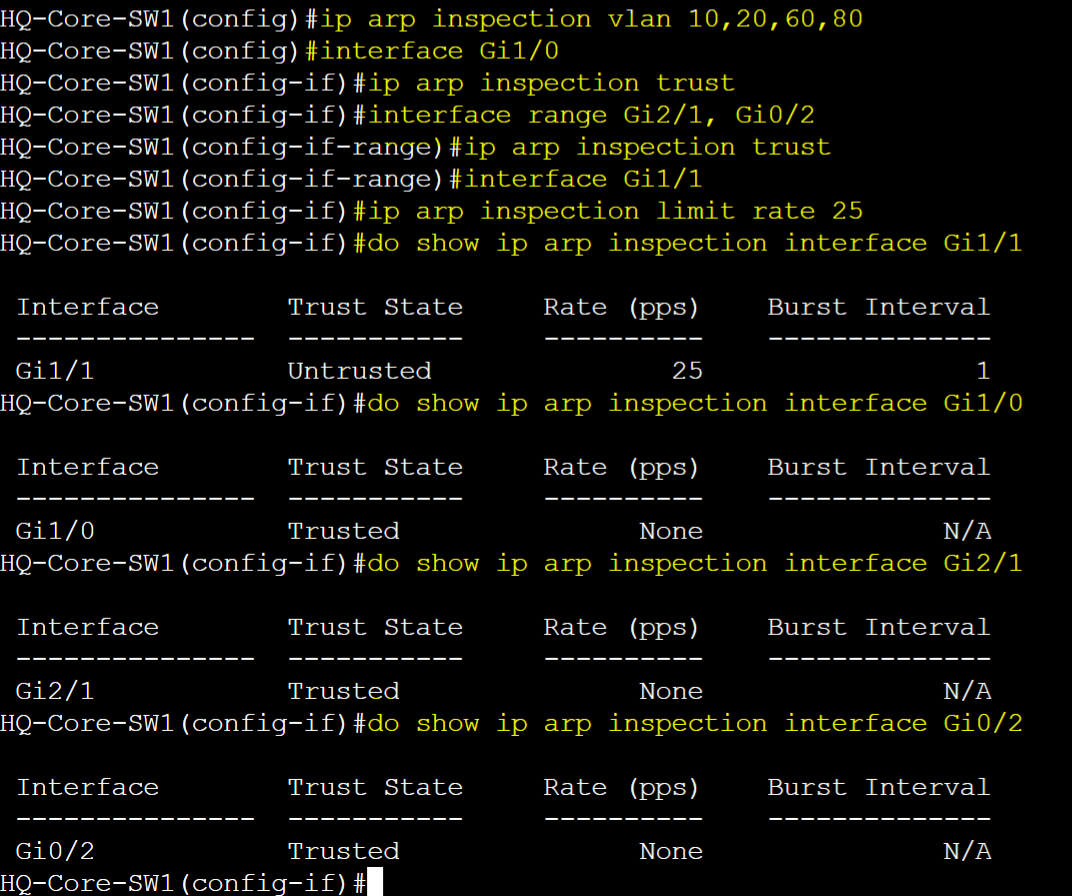
HQ-Core-SW1
DAI enabled for each VLAN. Trusted ports for trunk links defined. Verify trusted ports. For demonstration, increase the rate limit value on the untrusted access port from 15 to 25.
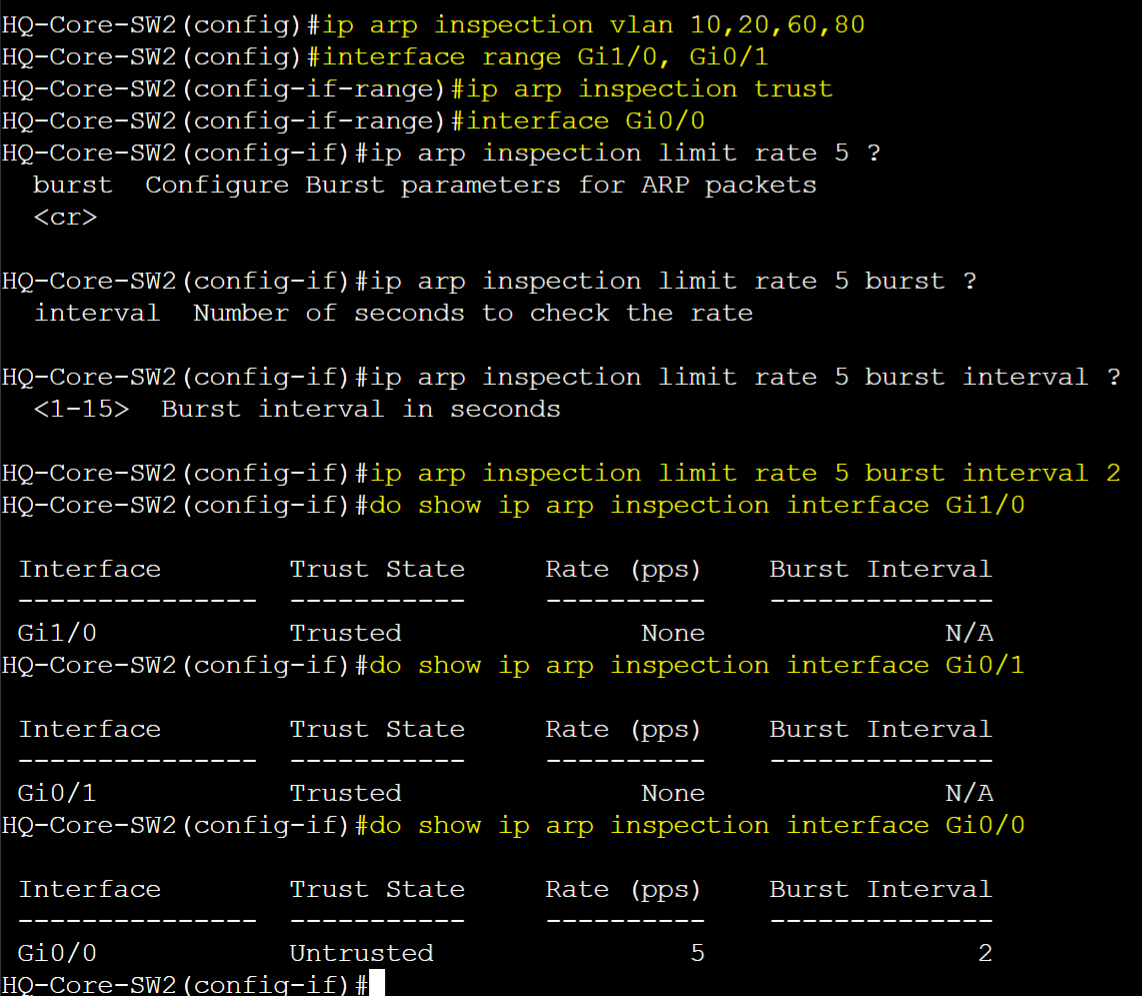
HQ-Core-SW2
Notes:
- DAI enabled for each VLAN. Trusted ports for trunk links defined. Verify trusted ports. For demonstration, increase the rate limit value on the untrusted access port towards the Linux VM from 15 to 5 with a burst interval of 2 seconds
- The burst parameter in the Limit Rate feature command allows you to specify the maximum number of ARP packets that are allowed to pass through a port within a short burst of time in seconds
- In the configuration example, if ARP packets were to exceed 5 packets in both those seconds, the interface will be error-disabled. If ARP packets were to exceed for 1 second but not for the last second, the interface will not be error-disabled
DAI Dynamic ARP Inspection Validation
Scenario:
- In this lab scenario, we will attempt to poison the ARP caches of Gateway-R1 and the MGMT PC in VLAN60 from the Kali Linux VM using Ettercap
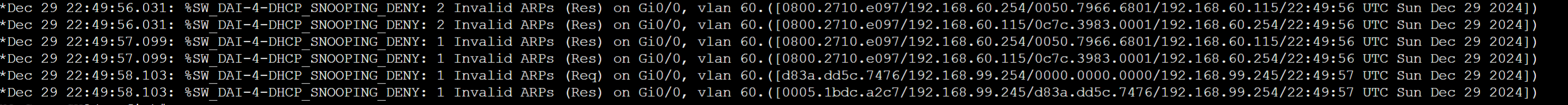
- With DAI configured on interface Gi0/0 of HQ-Core-SW2, DAI will detect and error disable the interface during the ARP broadcast scan via Ettercap
- To simulate the switch to allow Ettercap to perform the ARP broadcast scan for active host detection, I will purposely increase the rate limit value of the Gi0/0 interface
- After the ARP broadcast scan has been completed, I have decreased the rate limit value of the Gi0/0 interface for DAI. At this point when Ettercap attempts to poison the ARP caches of the host victims, DAI will block these ARP responses because the modified IP to MAC pairs in the gratuitous ARP responses will not correspond with the DHCP Snooping binding table entry of the Kali Linux VM and its actual MAC address during DHCP assignment

Kali Linux Attacker
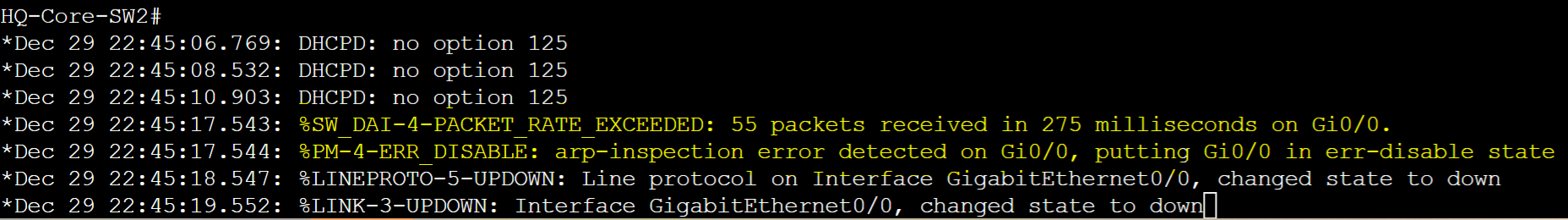
Port Gi0/0 on HQ-Core-SW2 connected to the Kali Linux attacker goes into an error disabled state if the number of ARP messages exceed the configured rate limit. From the Kali Linux machine, I issued an ARP broadcast scan to the entire subnet once again but DAI took action.
Notes:
- In this lab example, I raised the limit rate on Gi0/0 to the highest value to demonstrate what happens if the attack host sends out gratuitous ARP messages to the Gateway-R1 router and MGMT PC in VLAN60 for the goal to poison their ARP caches
- DAI took action by comparing the IP to MAC pairs of the incoming poisoned ARP entries with the DHCP Snooping binding table. Since the DHCP snooping binding table has an IP to MAC entry for the attack Linux machine during DHCP assignment, the switch dropped the gratuitous ARP replies because the modified IP to MAC address pairs do not match the table values