Allowed VLANs
Sections:
Overview:
- The Allowed VLANs concept allows us to permit specific VLANs to travel across a trunk link between two network devices like switches, routers, or firewalls
- By default in Cisco IOS, all VLANs are allowed on a trunk link
- It is best practice to tighten up the security posture of Cisco devices by reducing the amount of unused VLANs traversing through trunk links
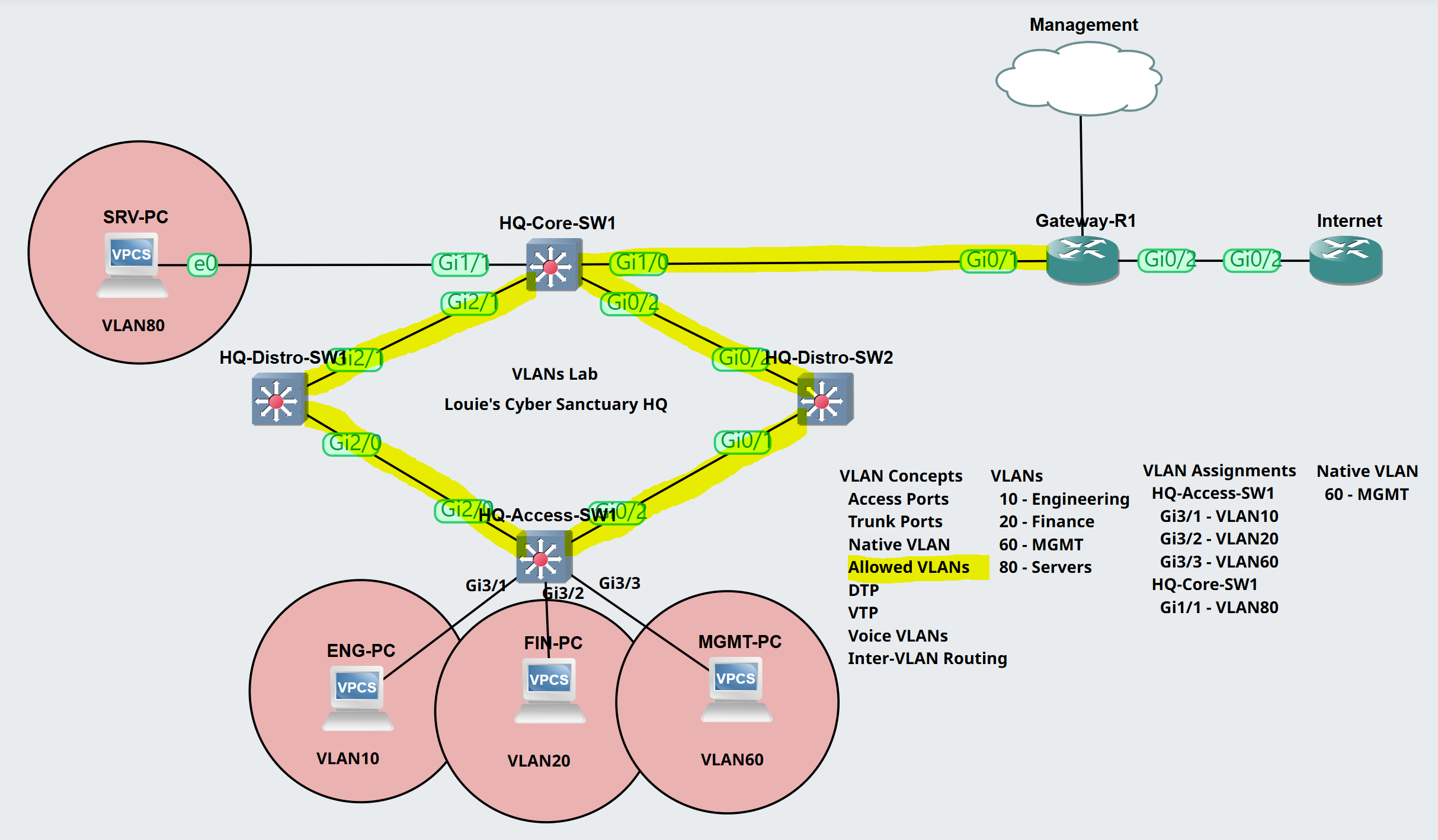
Lab Topology
Scenario: In this lab topology scenario we will restrict the allowed VLANs to only allow the necessary VLANs to be carried between trunk links
Allowed VLAN Configuration
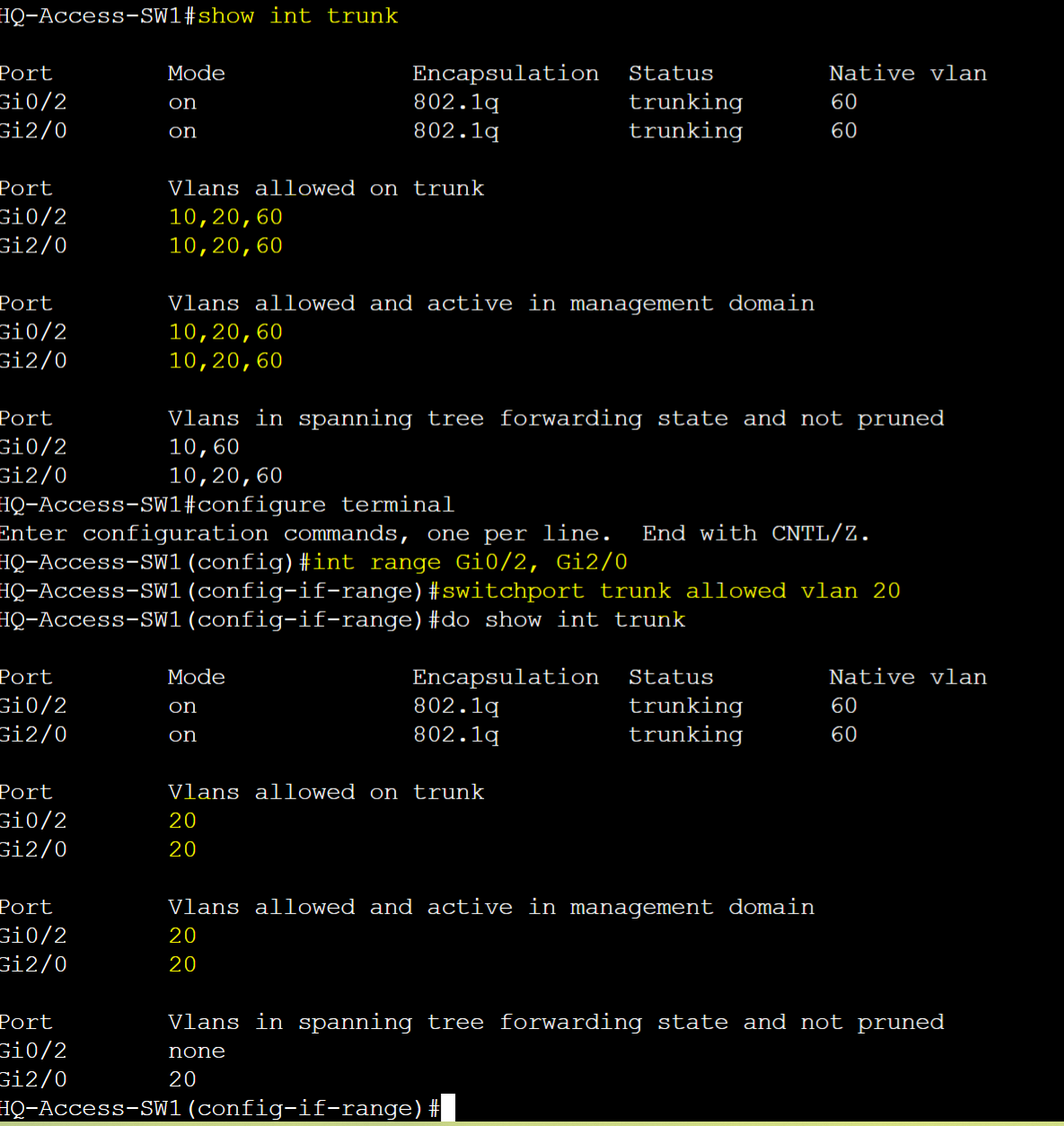
HQ-Access-SW1
HQ-Distro-SW1
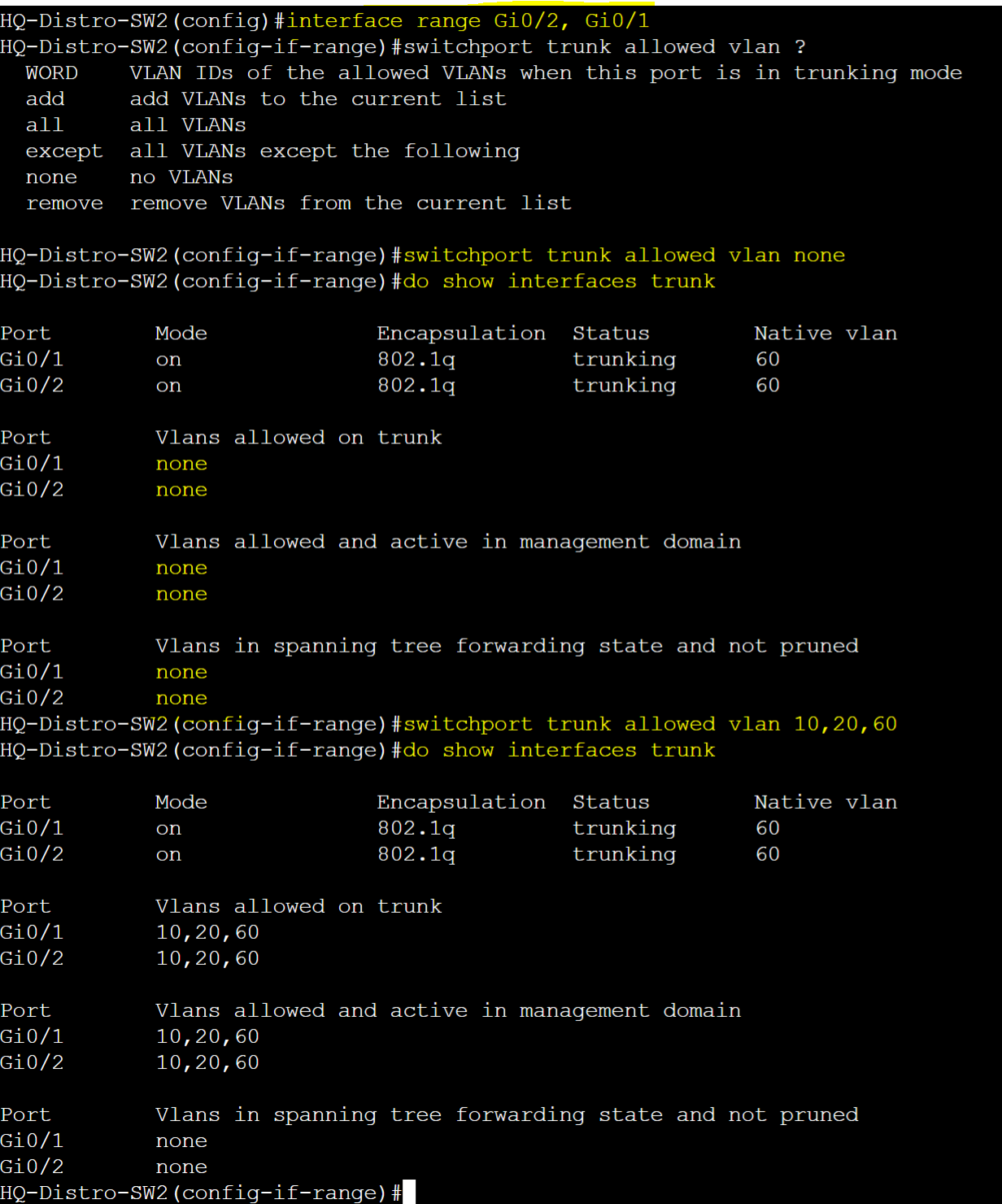
HQ-Distro-SW2
HQ-Core-SW1
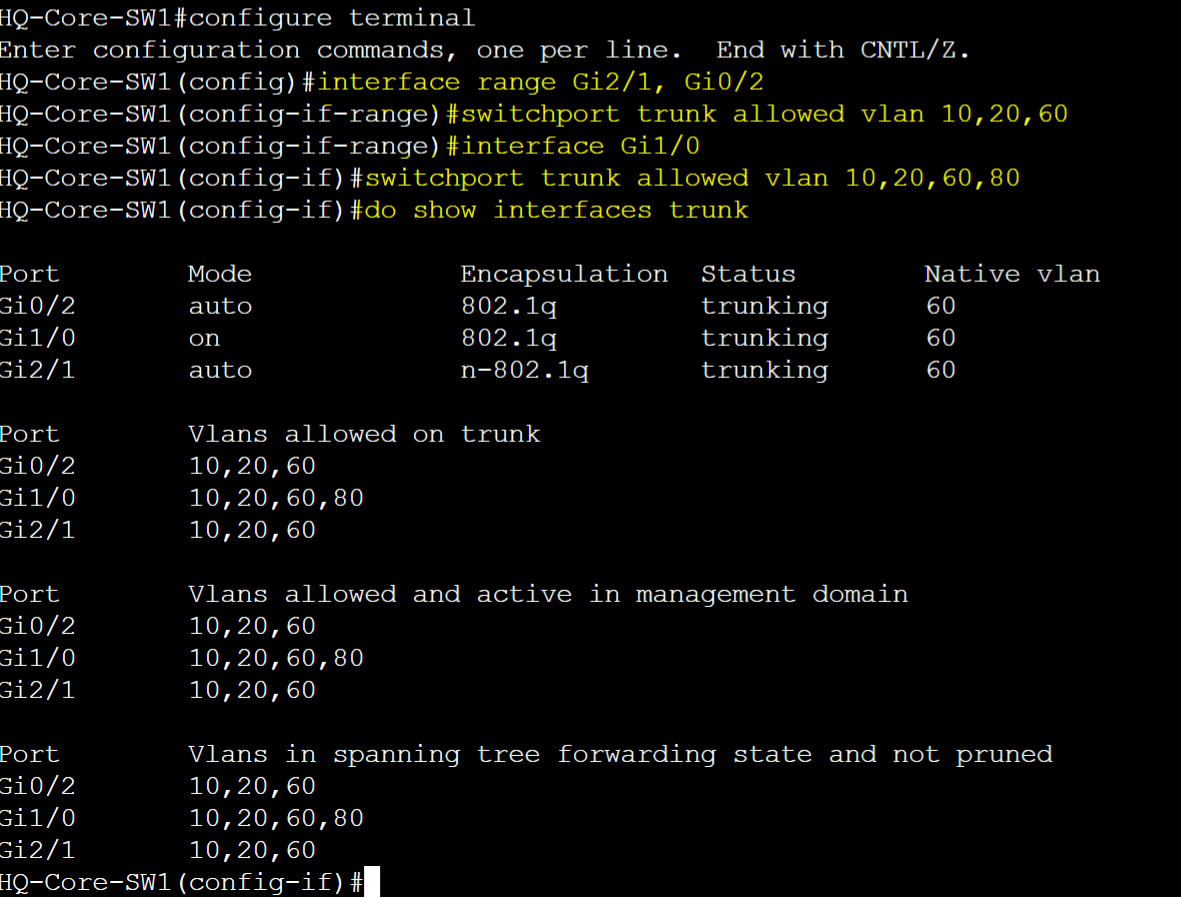
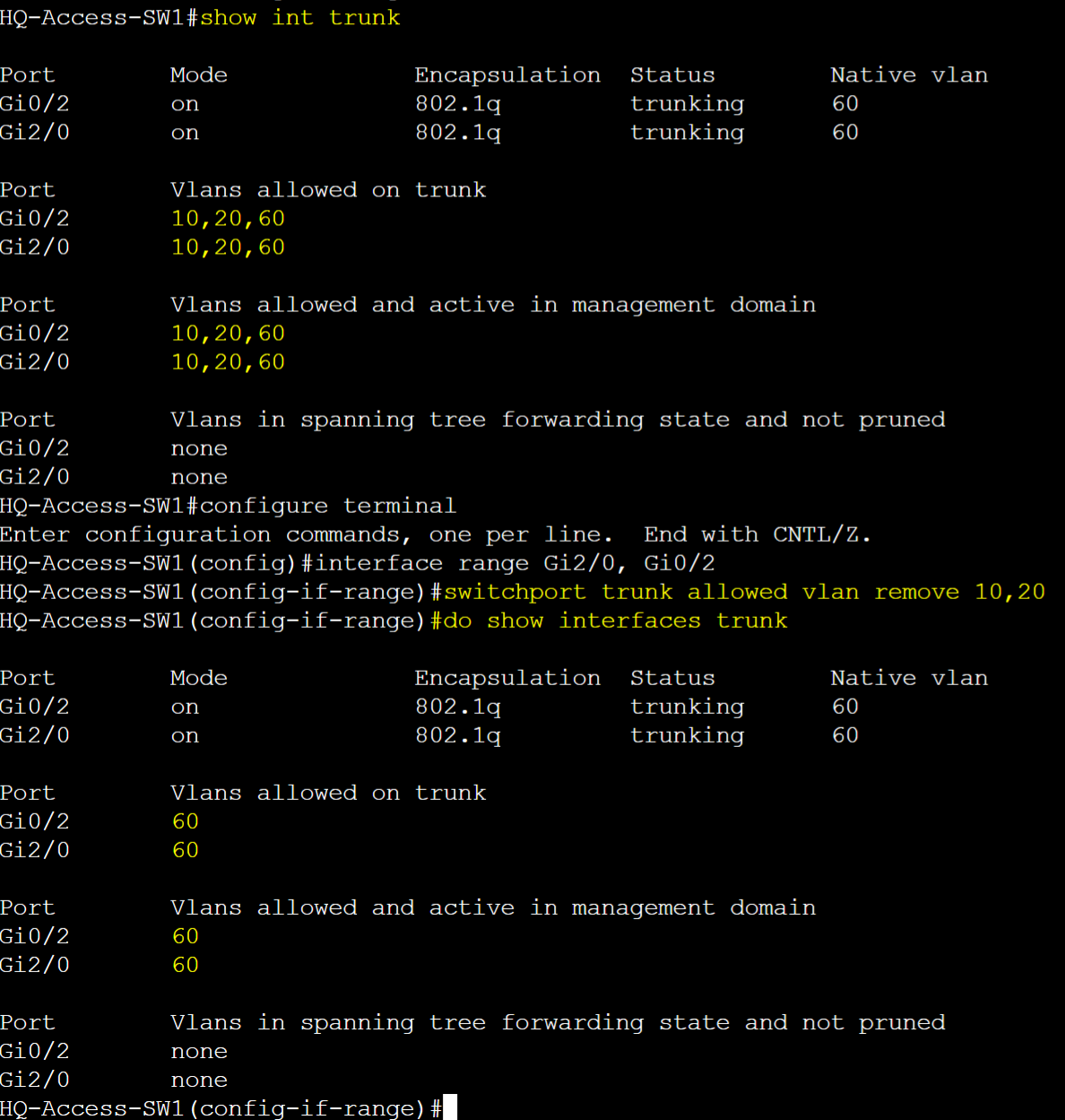
To summarize the scenario, the allowed VLANs list of each switch have been restricted to only allow the VLANs necessary.
Note: Both sides of a trunk link will need to consist of the same allowed VLANs for proper communication between the switches. If VLANs are allowed on one side of the trunk but not on the other, the traffic for those VLANs will be dropped causing communication failures between devices on those VLANs across the switches.
Note: However in this example, VLAN 80 has not been allowed on the trunk links between the downstream links of HQ-Core-Sw1
- The reason for this is because there are no other VLAN 80 devices located downstream off of HQ-Core-SW1. If VLAN 80 needs to communicate with devices in VLANs 10,20, or 60 or vice versa, inter-VLAN routing will need to be handled by a layer 3 device such as a router, firewall, or layer 3 switch. The layer 3 device will re-tag the incoming VLANID of the source device with the VLANID of the destination device and vice versa
- Inter-VLAN routing will be discussed in detail in a future lesson
- Interface Configuration Commands
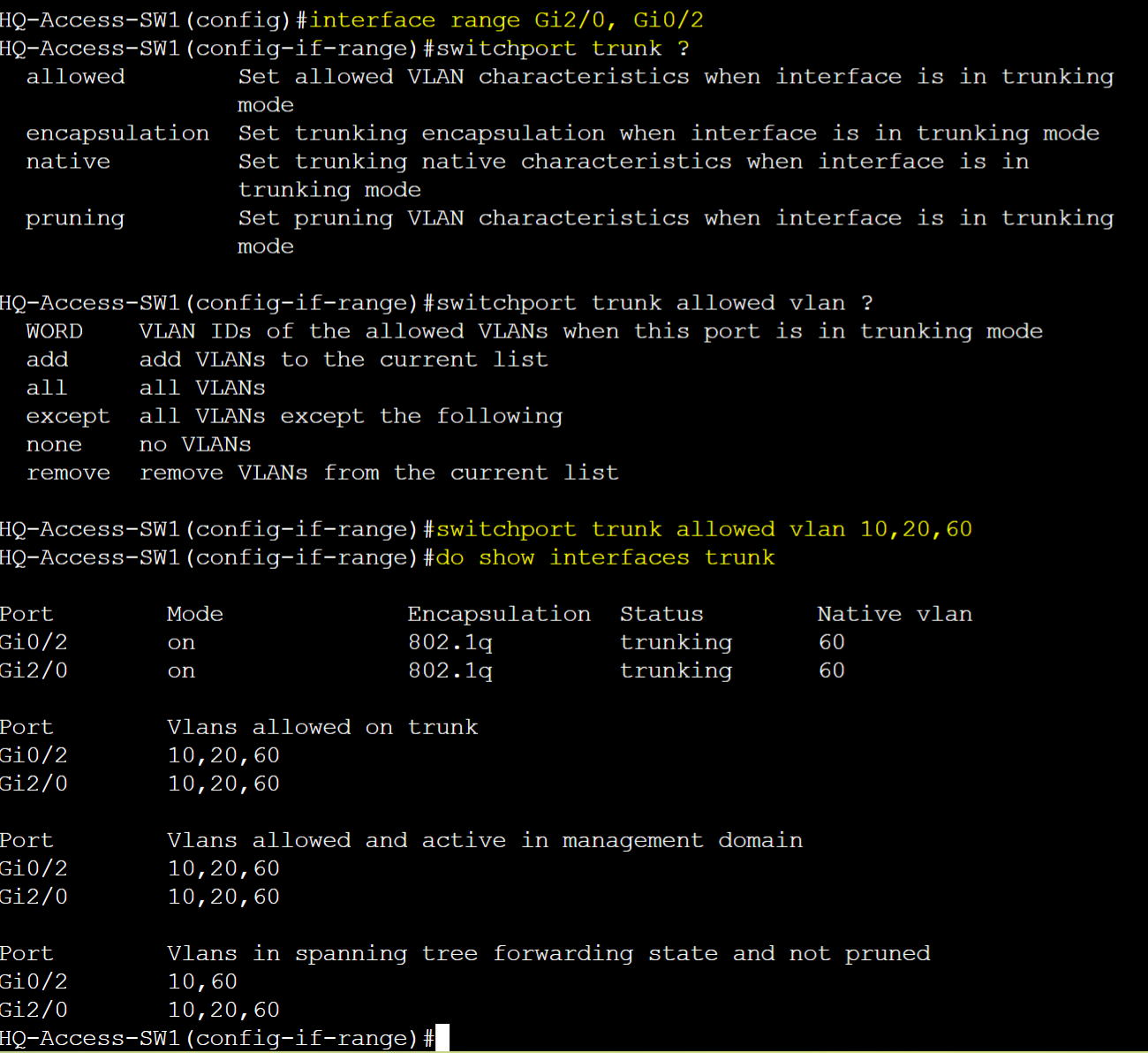
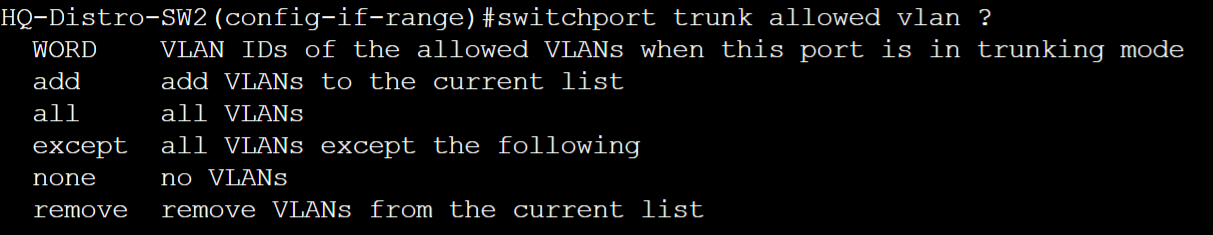
- To set the allowed VLANs list
- switchport trunk allowed vlan [add | all | except | none | remove | WORD]
- To verify allowed VLANs list
- show interfaces trunk
- To set the allowed VLANs list
Allowed VLANs Configuration Parameters
How it Works:
- When configuring the allowed VLANs list on a Cisco switch, there are several parameters that can be used to restrict VLANs
- WORD
- add
- all
- except
- none
- remove
WORD
- When restricting VLANs in a trunk, the 'WORD' parameter allows you to specify a VLAN or list of VLANs and will overwrite the current Allowed VLAN list with the VLANs you specify
- Note: It is important to understand that specifying the VLANs will overwrite the current list. If the goal is to add the VLANs to the current list, the 'add' keyword is recommended
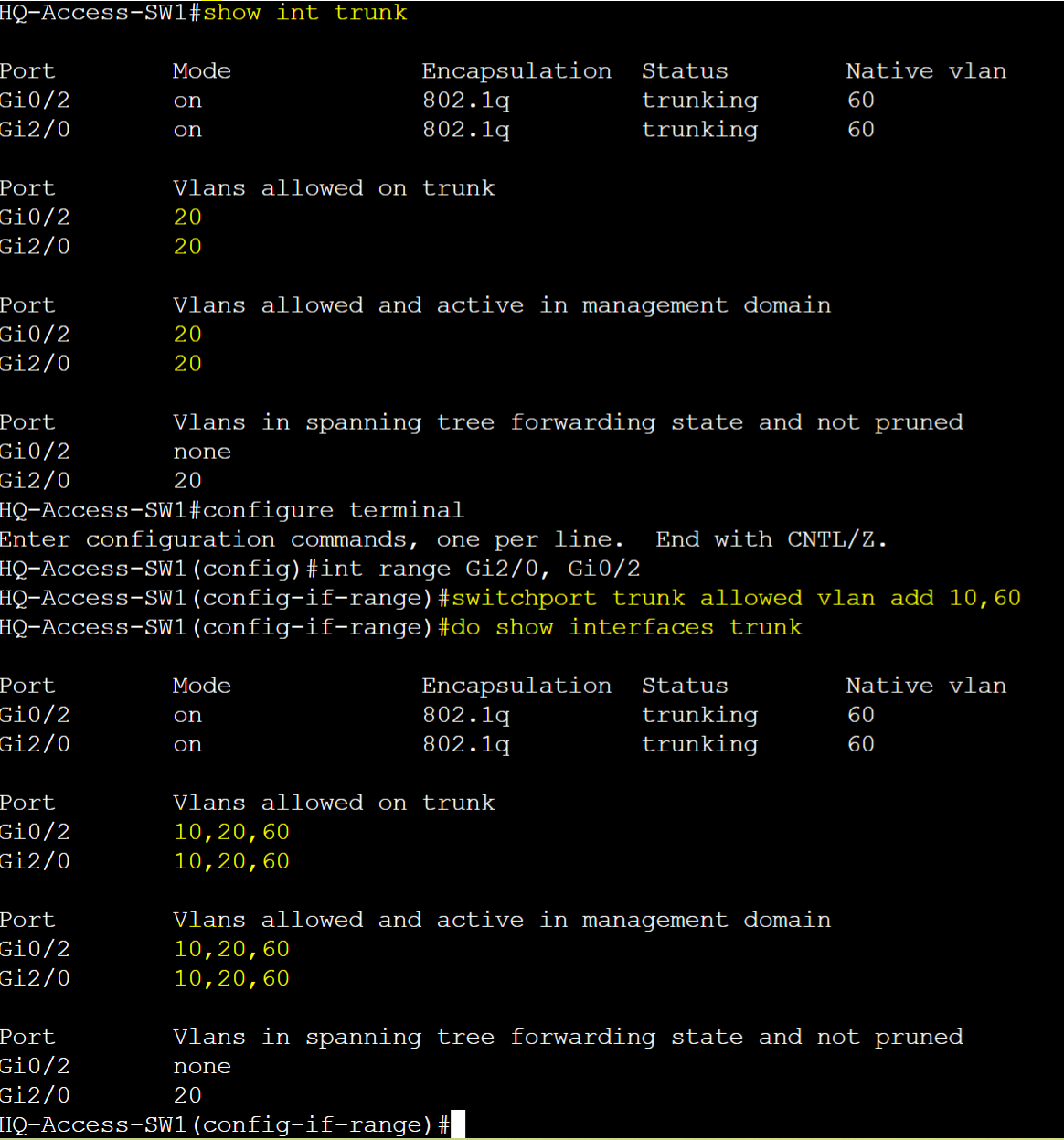
Add
- When restricting VLANs on a trunk, the 'Add' parameter allows you to add a VLAN or list of VLANs to the current Allowed VLANs list
All
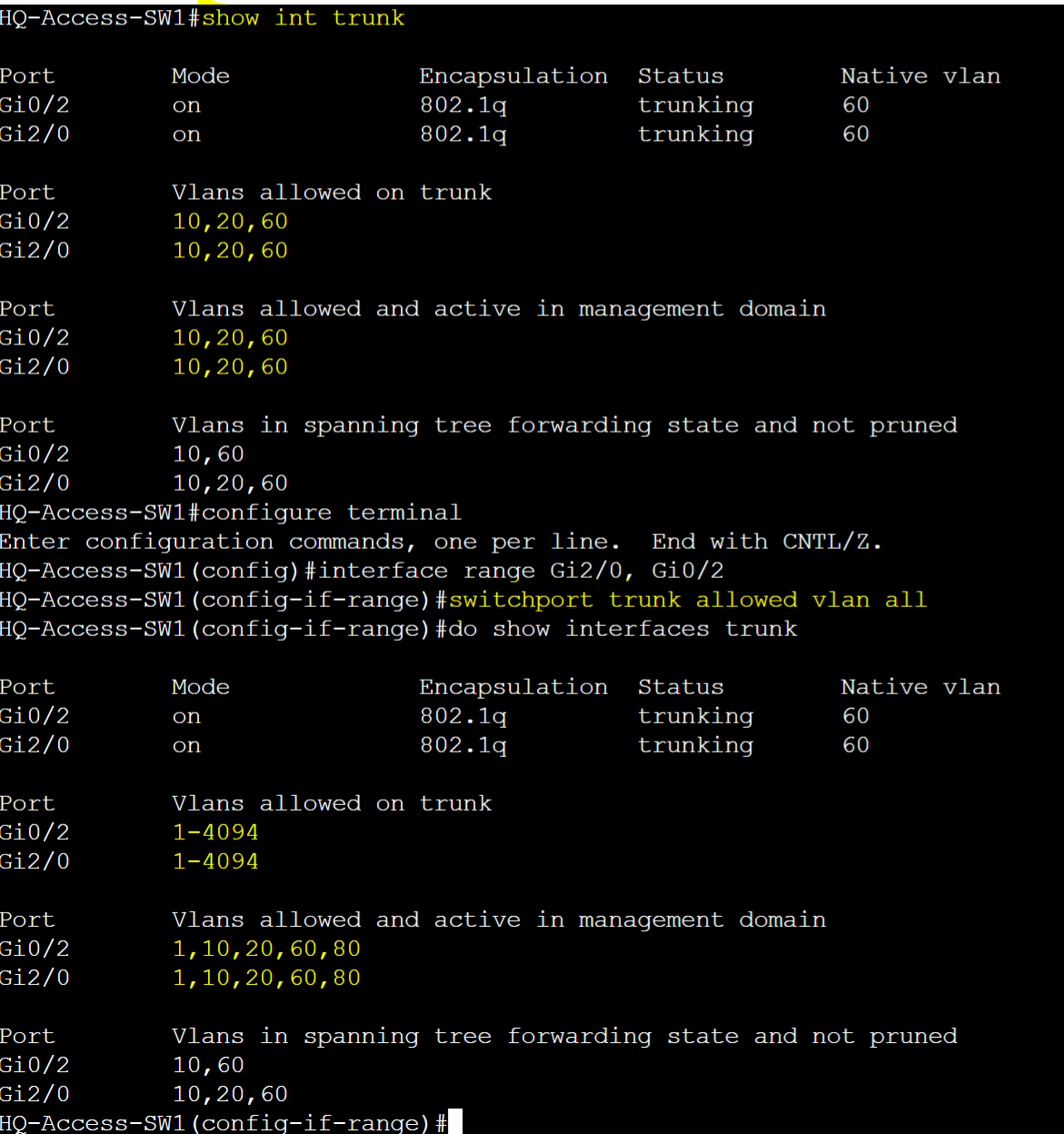
- When restricting VLANs on a trunk, the 'All' parameter allows you to add all VLANs 1-4094 to the trunk link
- Note: The 'VLANs allowed on trunk' list will specify all VLANs 1-4094 but the 'VLANs allowed and active in management domain' will only specify the VLANs that are created and defined on the switch itself
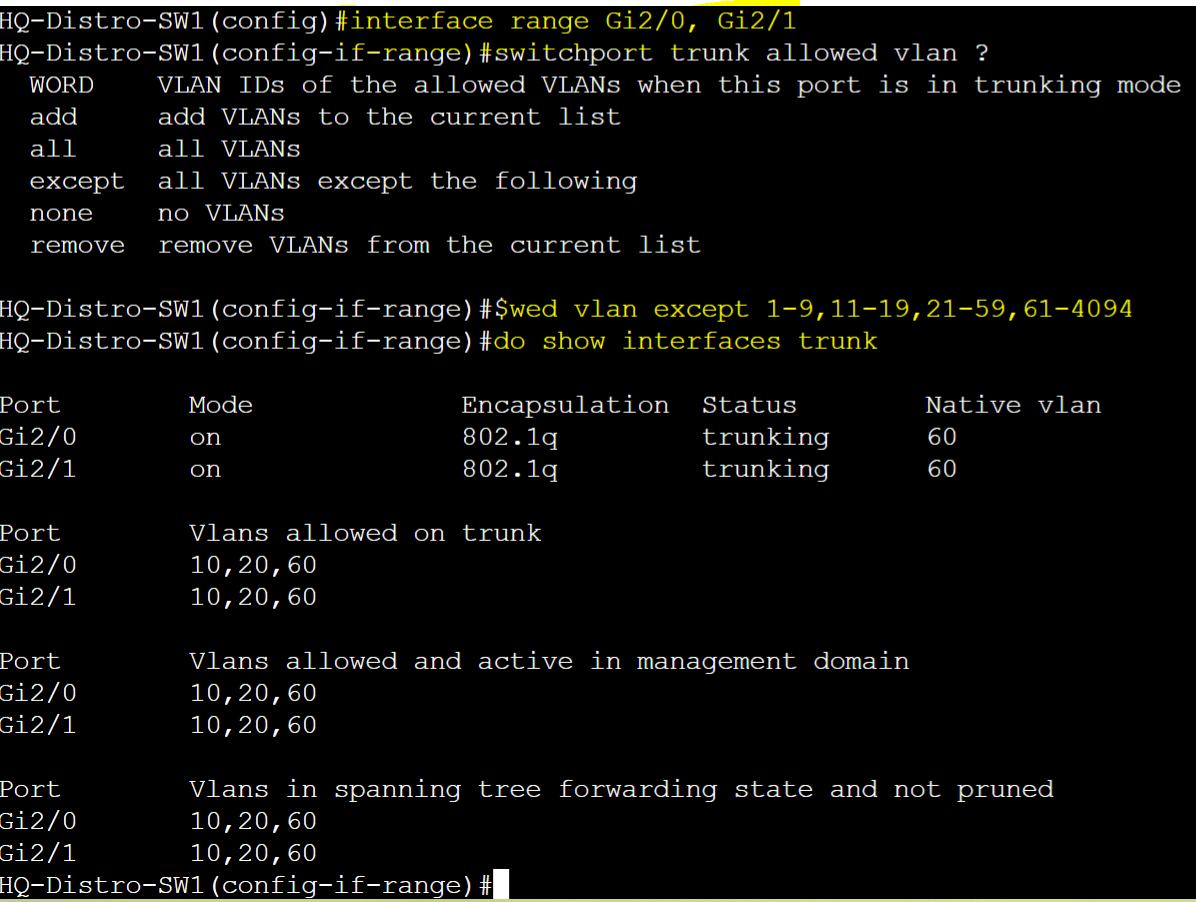
Except
- When restricting VLANs on a trunk, the 'Except' parameter allows you to add all VLANs except the following VLANs you specify

None
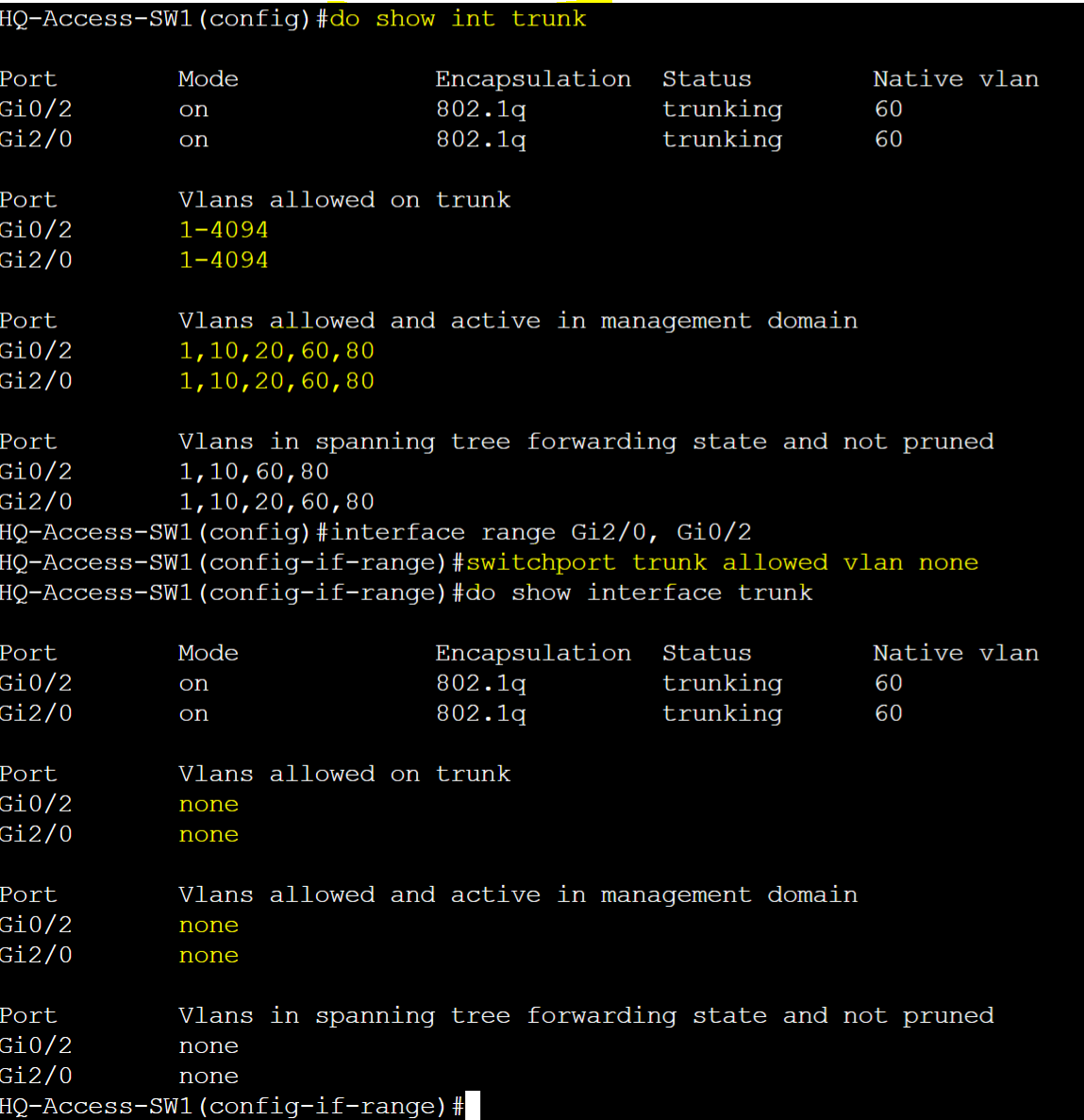
- When restricting VLANs on a trunk, the 'None' parameter allows you to remove all VLANs that are currently in the Allowed VLANs list
Remove
- When restricting VLANs on a trunk, the 'Remove' parameter allows you to remove a VLAN or list of VLANs that are currently in the Allowed VLANs list