Native VLANs
Sections:
Use Case Scenarios:
- Native VLANs are typically used to carry management traffic such as CDP and Spanning Tree
Overview:
- Now that we have learned about Trunk ports, Native VLANs are closely associated with trunk ports
- The Native VLAN carries untagged traffic (frame without a VLAN tag) on a trunk link
- If a switch sends an untagged frame over a trunk link, the receiving switch or firewall/router will assign the frame to the native VLAN
- By default, the native VLAN is set to VLAN1 on Cisco switches
- It is best practice to change the native VLAN to an unused VLAN other than 1 for security purposes
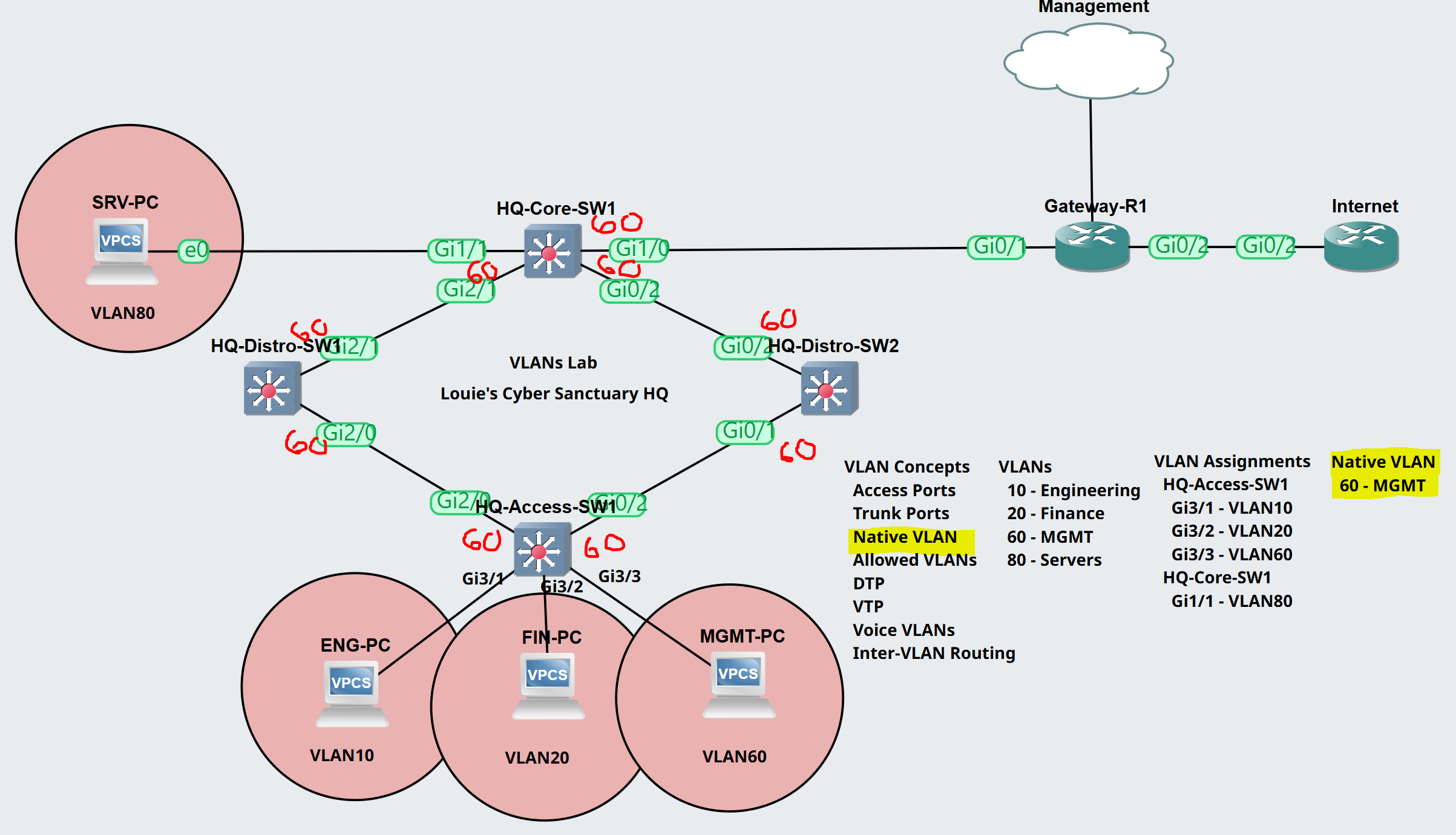
Lab Topology
Scenario:
- In this lab topology scenario I will configure the native VLAN on all ends of the trunk links between switches including the uplink towards Gateway-R1 from HQ-Core-SW1
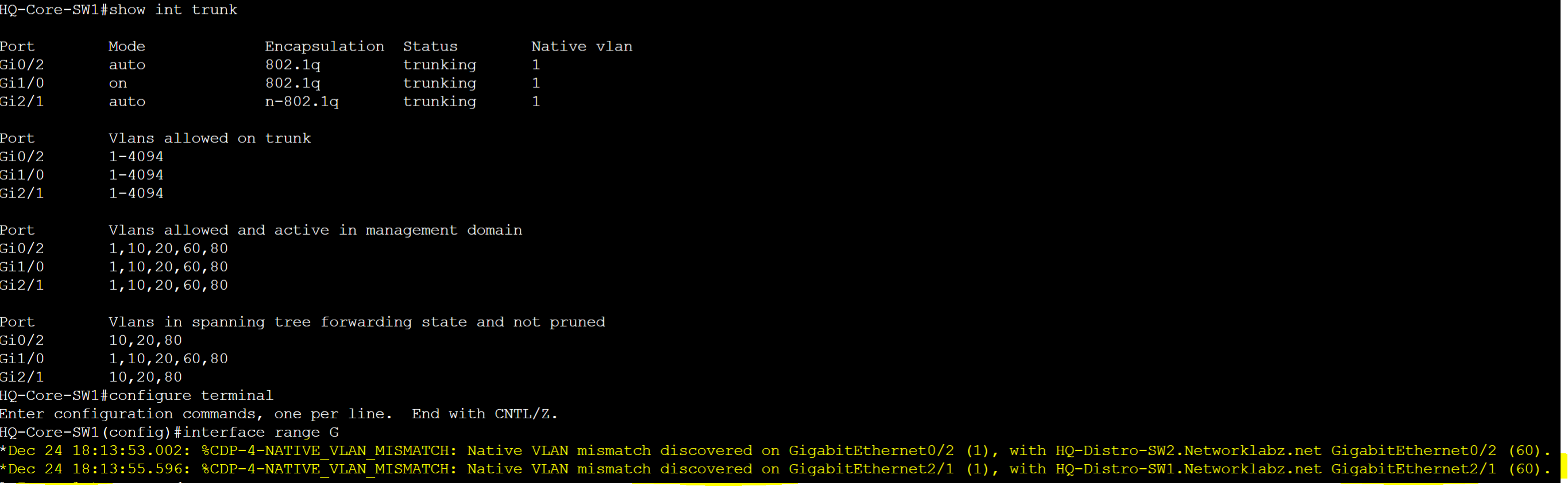
- Native VLAN Mismatch
- It's important to ensure both sides of a trunk link have the same native VLAN configured to avoid issues and ensure correct frame handling
Native VLAN Configuration
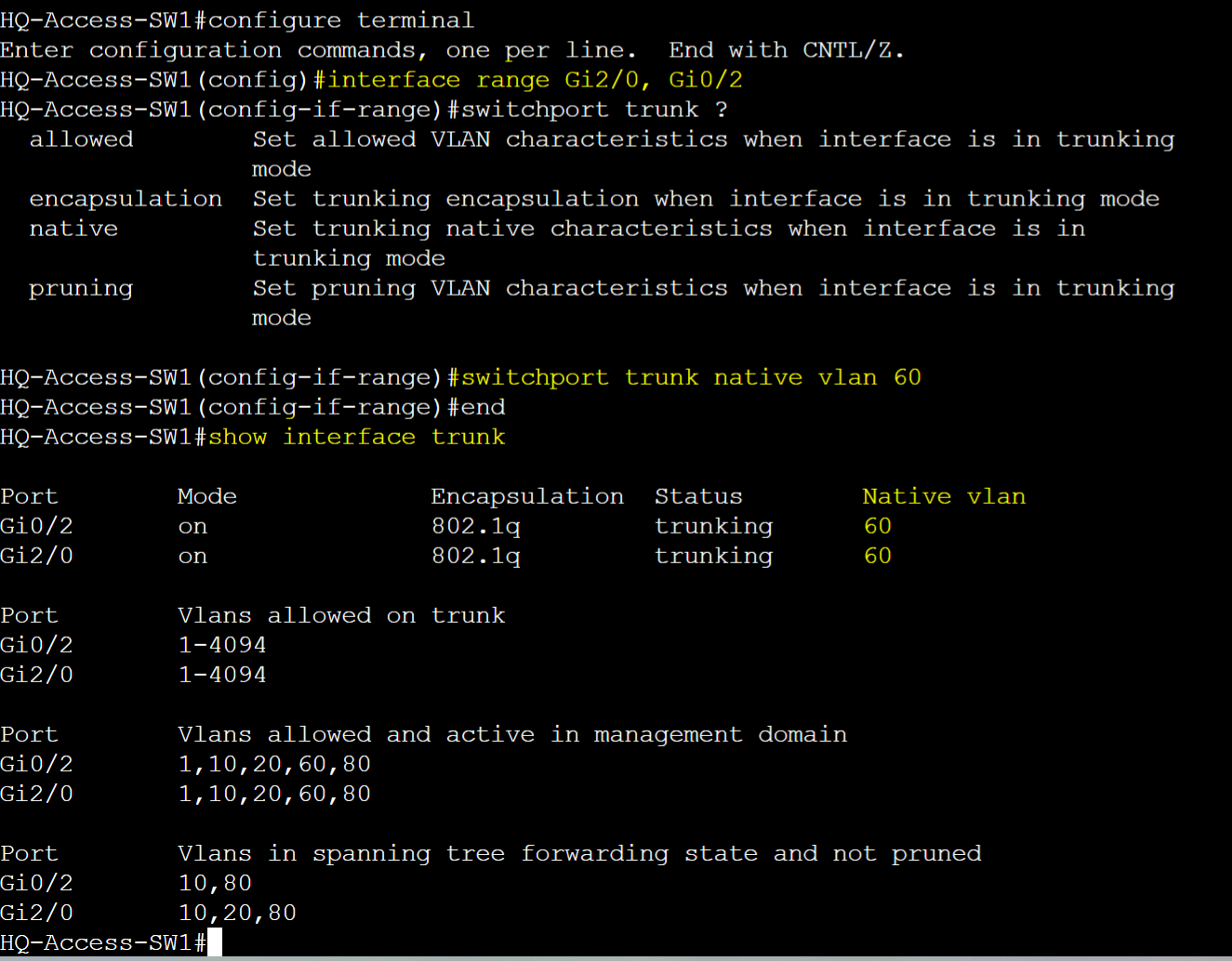
HQ-Access-SW1
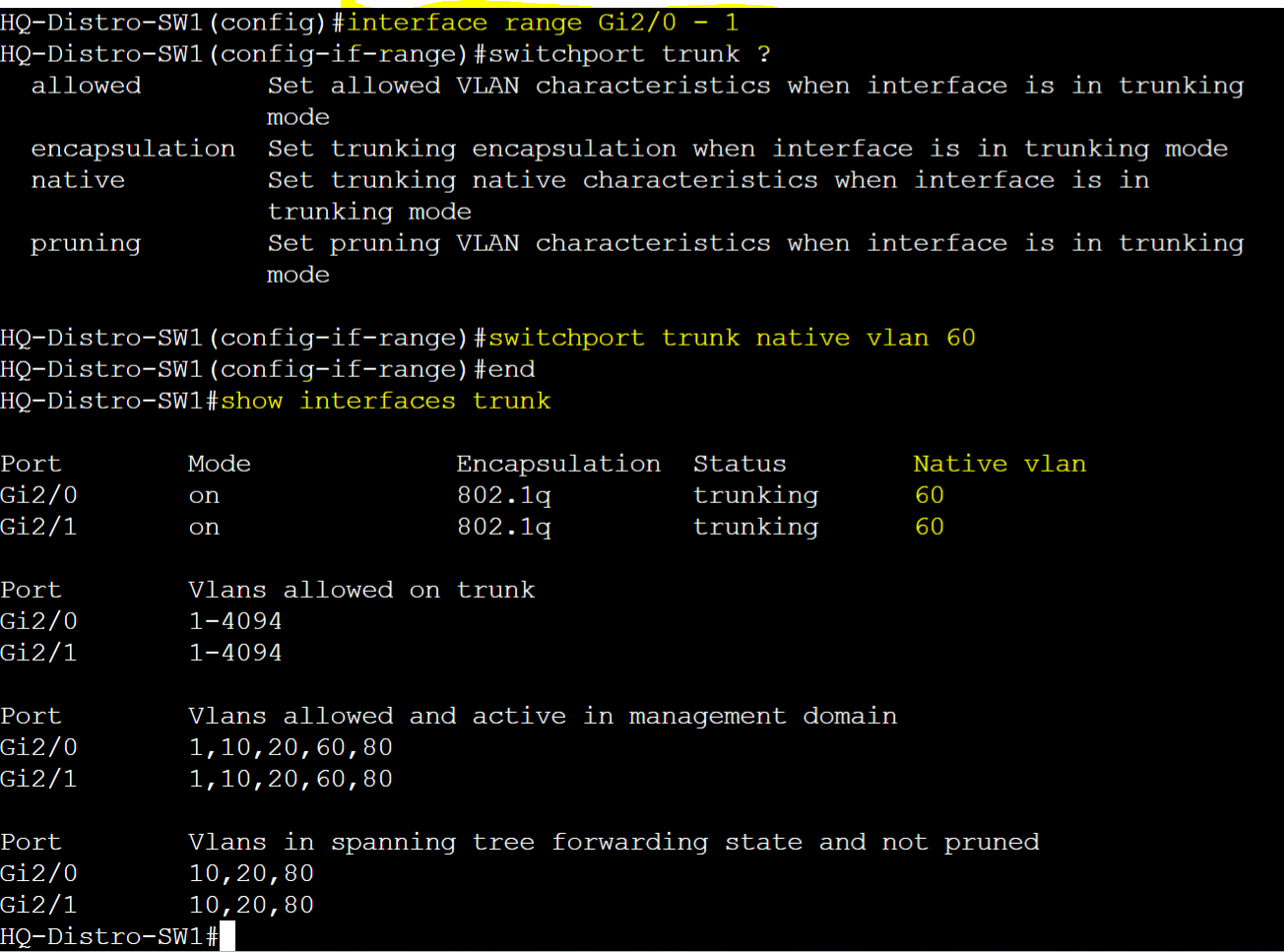
HQ-Distro-SW1
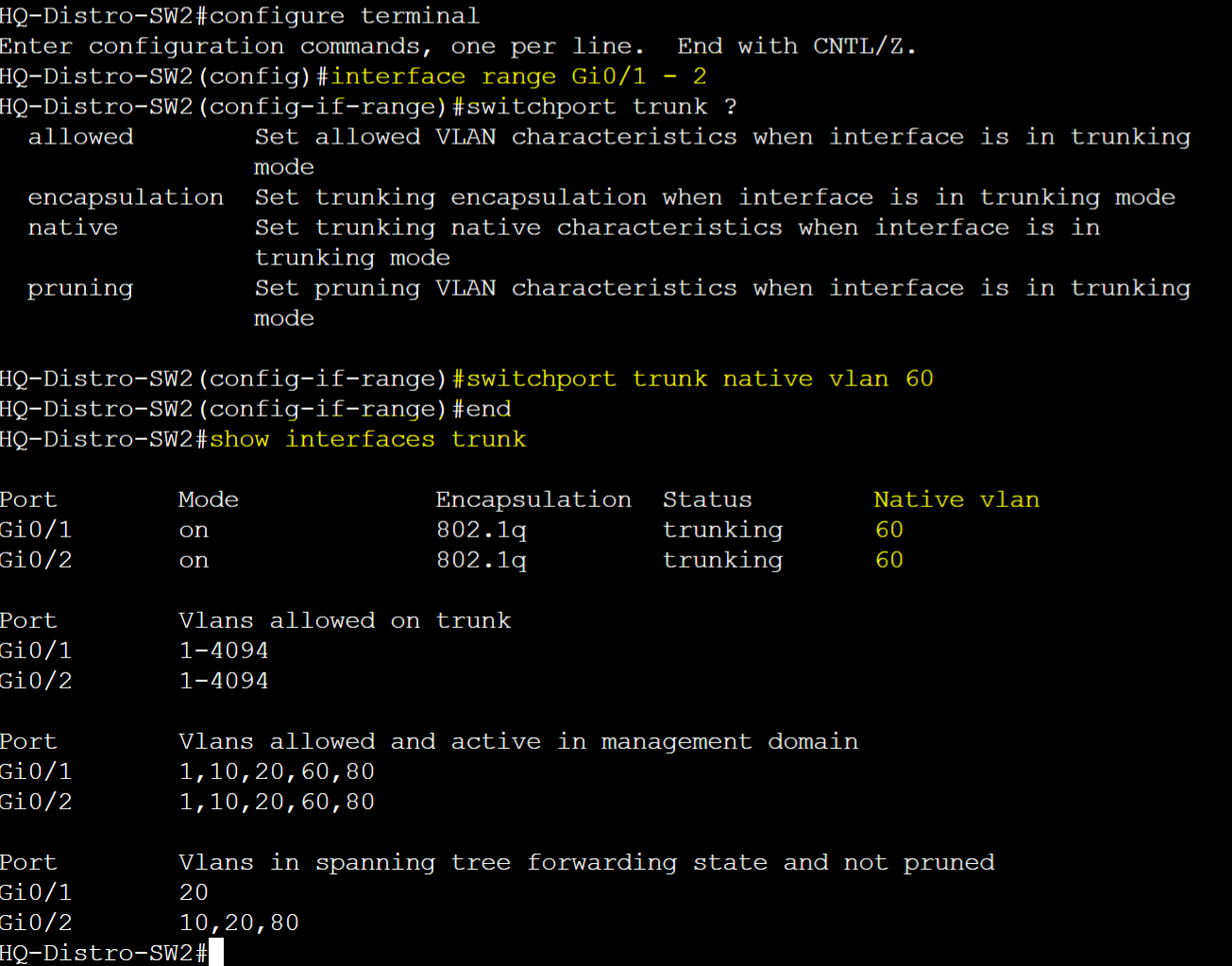
HQ-Distro-SW2
HQ-Core-SW1
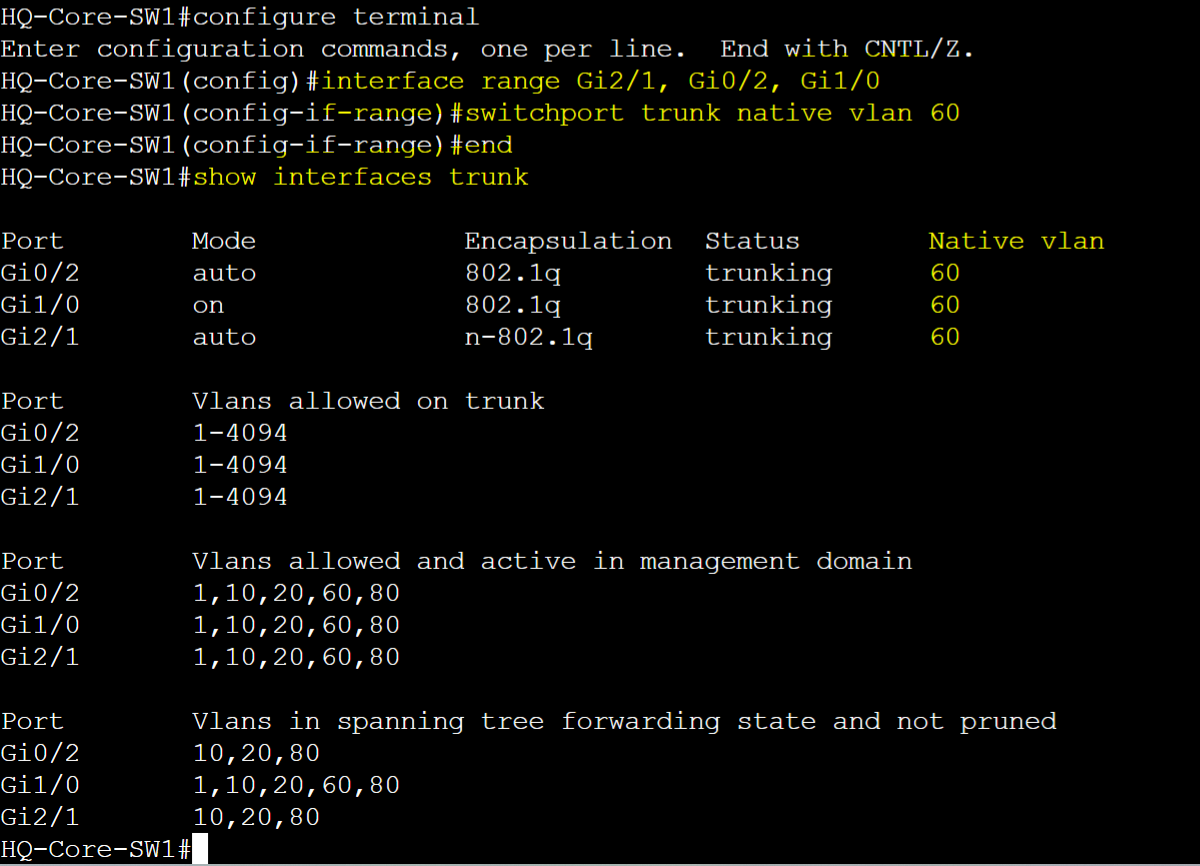
Native VLAN Mismatch on HQ-Core-SW1
To summarize the scenario, the native VLAN of 60 has been configured on both ends of the trunk links between switches.
Note: If CDP is enabled on the Cisco switches, CDP will detect and notify you of a Native VLAN mismatch to correct
- Interface Configuration Commands
- To set the native VLAN
- switchport trunk native vlan <vlanID>
- To verify native VLAN on trunk ports
- show interfaces trunk
- To set the native VLAN
VLAN Hopping Attacks
Scenario:
- In this scenario lets discuss two VLAN Hopping attack methods that can occur if best practices are not followed
Double Tagging
How it Works:
- A VLAN hopping attack occurs when an attacker sends traffic from one VLAN to another bypassing normal VLAN isolation
- This attack allows the attacker to gain unauthorized access to traffic in other VLANs compromising sensitive data
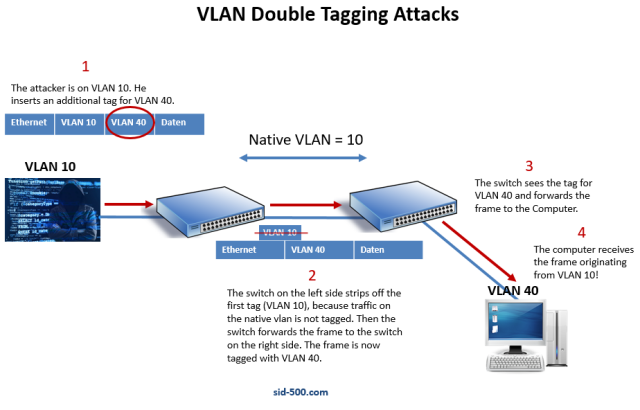
- Using the Double Tagging method, the attacker modifies the packet it intends to send by attaching a second inner VLAN tag in addition to the first outer tag corresponding to the target VLAN (often VLAN 1)
- A key concept with 802.1Q is that frames of the native VLAN are never tagged which in this scenario, causes the first switch in the path to strip off the outer tag leaving the malicious second inner VLAN tag to be forwarded onto the next switch
- At this point, the next switch sees the VLAN tag that was maliciously inserted in the packet by the attacker and forwards it to a VLAN that is different from the attacker breaking the rules of VLAN isolation
Double Tagging Mitigations:
- By default all switchports are assigned to native VLAN 1
- Best practice is to change the Native VLAN on trunk ports as attackers often target VLAN 1 as it is commonly used as the native VLAN for trunk ports
- Disable VLAN 1 on Trunk ports
- Ensure trunk ports only carry the VLANs that are needed
Switch Spoofing
How it Works:
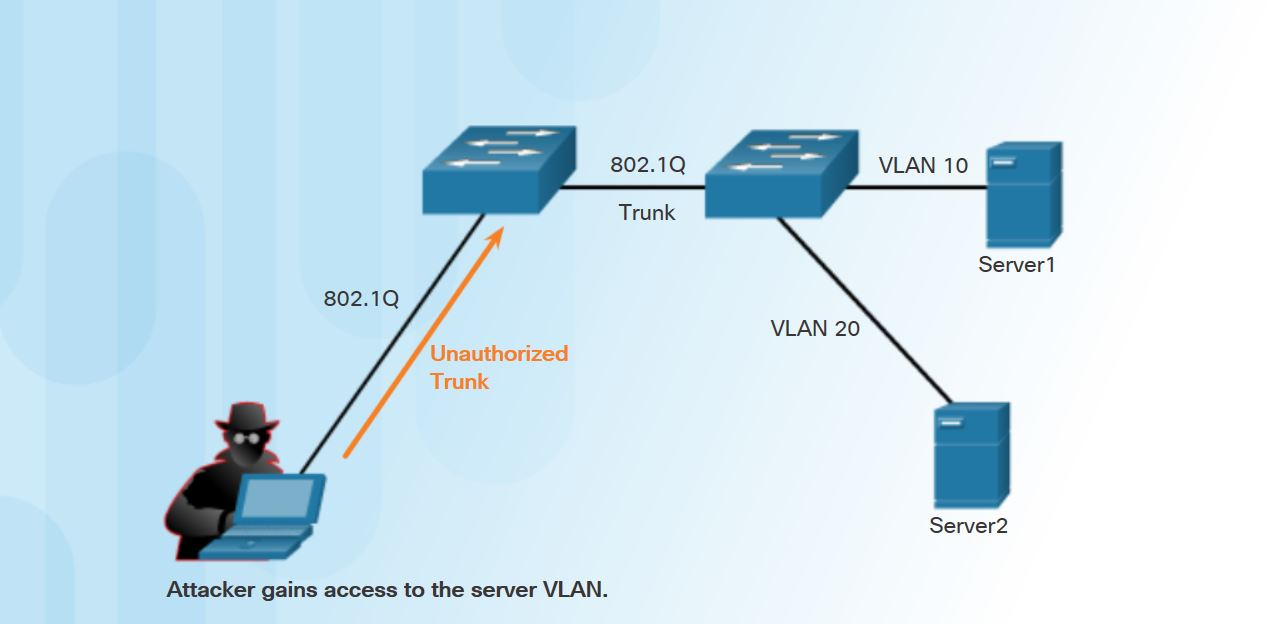
- Using the Switch Spoofing method, a rogue switch establishes a trunk link with a production switch gaining unauthorized access to multiple VLANs in the network
- This method exploits the DTP or Dynamic Trunking Protocol which is used by switches to negotiate trunking automatically between connected switches
- The attacker can either utilize a rogue switch or configure their machine to behave like a switch by enabling DTP on their PC interface
- Once the attacker forms a trunk link with a production switch, the attacker can now send tagged frames for any VLAN on the trunk gaining unauthorized access to sensitive information
Switch Spoofing Mitigations:
- Disable DTP
- It is best practice to disable the DTP protocol on switches to prevent switches forming trunk links with unauthorized switches
- In a future concept we will dive deep into how DTP works
- Manually configure Trunk links to disable dynamic trunking
- Set ports to Access mode for End Devices
Other VLAN Hopping Mitigations:
There are various other best practices to avoid VLAN Hopping attacks and will be discussed more in depth in future lessons.
- Implement Port Security
- Implement ACLs
- Implement 802.1X
- Implement DHCP Snooping & DAI