Legacy Layer 3 Firewall Configuration
Sections:
- Stateful vs Stateless Overview
- Lab Topology
- Meraki Legacy Firewall Configuration
- Layer 3 Verification
Resources:
Overview:
- Legacy firewalls refer to the traditional method of controlling traffic based on IP addresses, subnets, and protocols at the Layer 3 Network layer of the OSI model
- The Meraki MX appliances, known for their cloud managed security features, provide firewall functionality with layer 3 capabilities
- In this section, I will go through configuring Layer 3 firewall rules on a Meraki MX appliance
Stateful vs Stateless Firewalls
Overview:
- Stateful and stateless firewalls are two different approaches to network security, each with its own characteristics and ways of handling network traffic
- In a Meraki solution, a layer 3 firewall rule on a MX security appliance is stateful in nature and can be based on protocol, source and destination IP address or port numbers
- In a later section, I will take a deep dive into Meraki's MR access points as they can also utilize layer 3 firewall rules but in a stateless nature approach
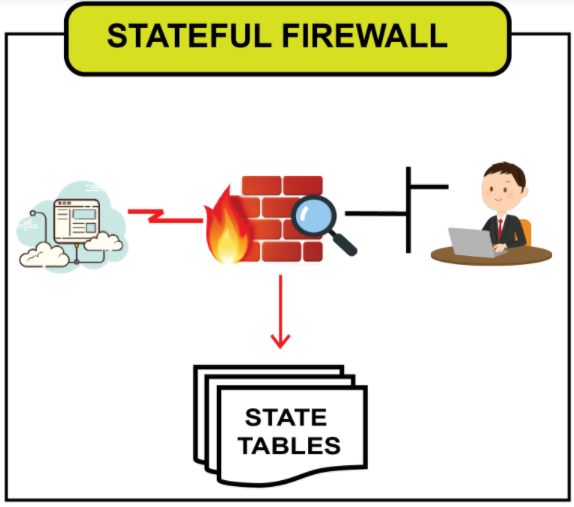
Stateful Firewall Overview
- By definition, stateful firewalls keep track of the state of active connections and make decisions based on the context of the traffic
- Stateful firewalls maintain a 'state table' that tracks the connection state for ongoing communications, allowing them to determine if a packet is part of an established connection or if it's an unrequested attempt to start a new one
- Stateful firewalls are generally considered more secure, as they can monitor the state of the connection and ensure that only valid packets for that session are allowed
- Use Case Scenarios:
- Stateful firewalls are effective in scenarios that require tracking the state of the network connections and making dynamic decisions based on the context of traffic
- These types of firewalls are also used in environments where security needs to be more granular, with deep inspection and protection against more sophisticated threats
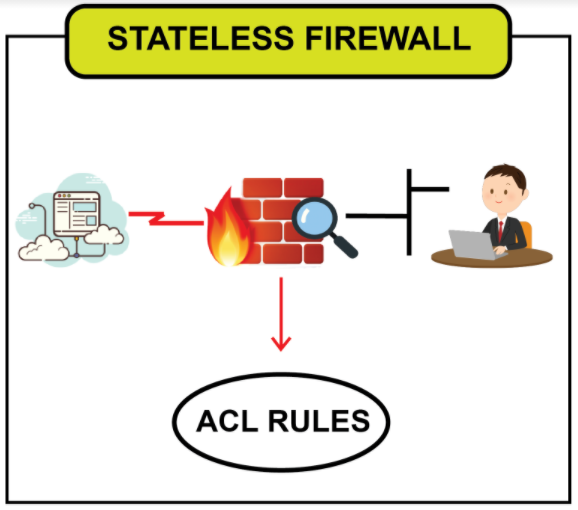
Stateless Firewall Overview
- By definition, stateless firewalls filter network traffic based solely on predefined rules without keeping track of the state of active connections
- Stateless firewalls examine each packet in isolation, considering only the source and destination IP addresses, ports, and protocols. They don't retain information about previous packets or the state of a connection
- Comparing stateful and stateless firewalls, stateless firewalls are considered simpler and faster as they don't have to store connection states. However, stateless firewalls are less secure as they are unable to differentiate between legitimate and malicious traffic based on the context of previous packets
- Use Case Scenarios:
- Stateless firewalls, due to their simplicity and speed, are useful in network scenarios where advanced connection tracking or deep inspection of traffic is not necessary
- Logically, stateless firewall rules can be used as an extra layer of defense alongside a stateful firewall appliance providing additional security benefits
- By adding stateless firewall devices alongside a stateful firewall, it optimizes network security by providing fast, basic filtering and reducing the load on the stateful firewall, allowing it to focus on more complex tasks
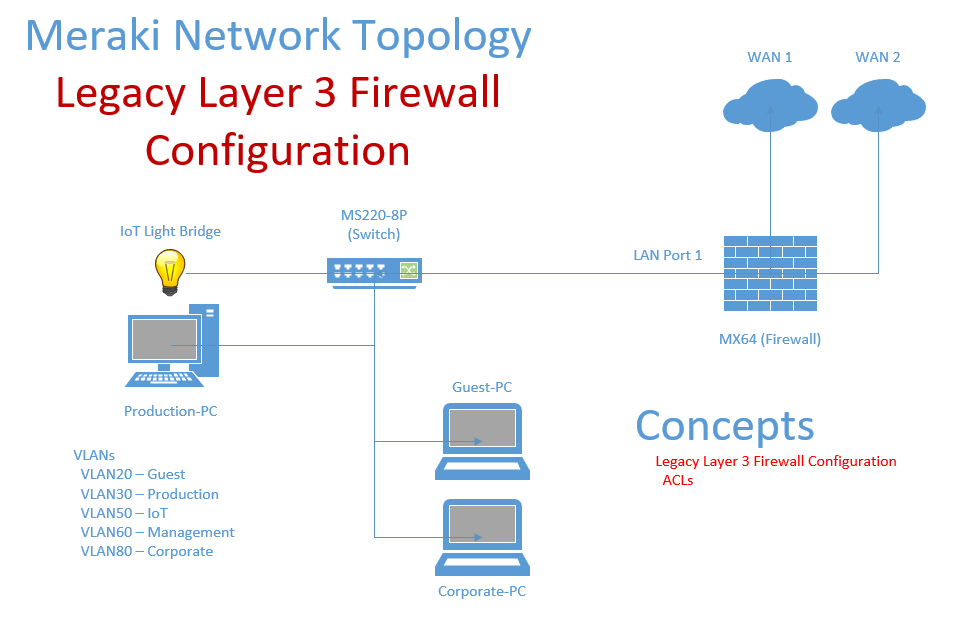
Lab Topology
Overview:
- In this section, lets take a look into configuring stateful legacy layer 3 firewall rules on a Meraki MX security appliance
Meraki Layer 3 Firewall Configuration
Scenario:
- In this lab exercise, I will create layer 3 firewall rules that will prevent the Guest-PC from communicating with all other VLAN networks in the Meraki LAN. Outbound Web traffic will only be allowed for the Guest, Corporate, and Management VLAN networks. All other traffic that do not match the defined rule criteria will be explicitly denied
- By default, the Meraki MX security appliance does not consist of any pre-defined outbound layer 3 firewall rules but allows all traffic by default including inter-VLAN routing
Menu to create firewall rules
Notes:
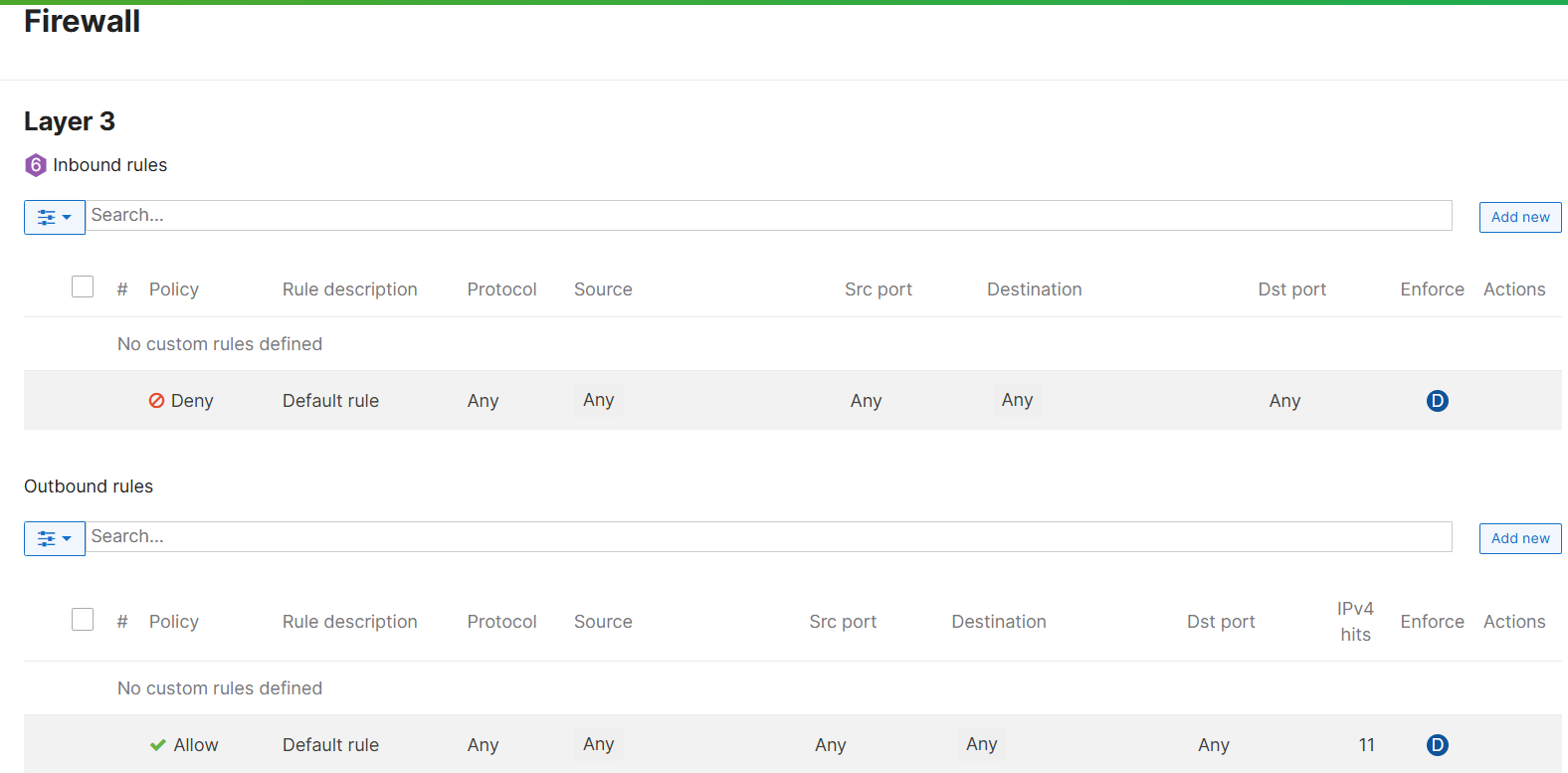
- By default, Meraki's Layer 3 inbound rules list only consists of a single deny 'any any' rule. This is due to the stateful nature of a stateful firewall by blocking all inbound traffic that isn't return traffic from an outbound flow. There are some use cases to enable inbound ipv4 firewall rules by reaching out to Meraki support but these cases will only be applicable if you're having Meraki support disable NAT on the WAN interface
- In this scenario, the goal to successfully restrict the Guest-PC from communicating with other PCs located in different VLAN networks is to configure an outbound rule on the Meraki MX appliance originating from the Guest VLAN. To summarize, any traffic hitting the firewall and destined to an external network or the Internet is an outbound scenario
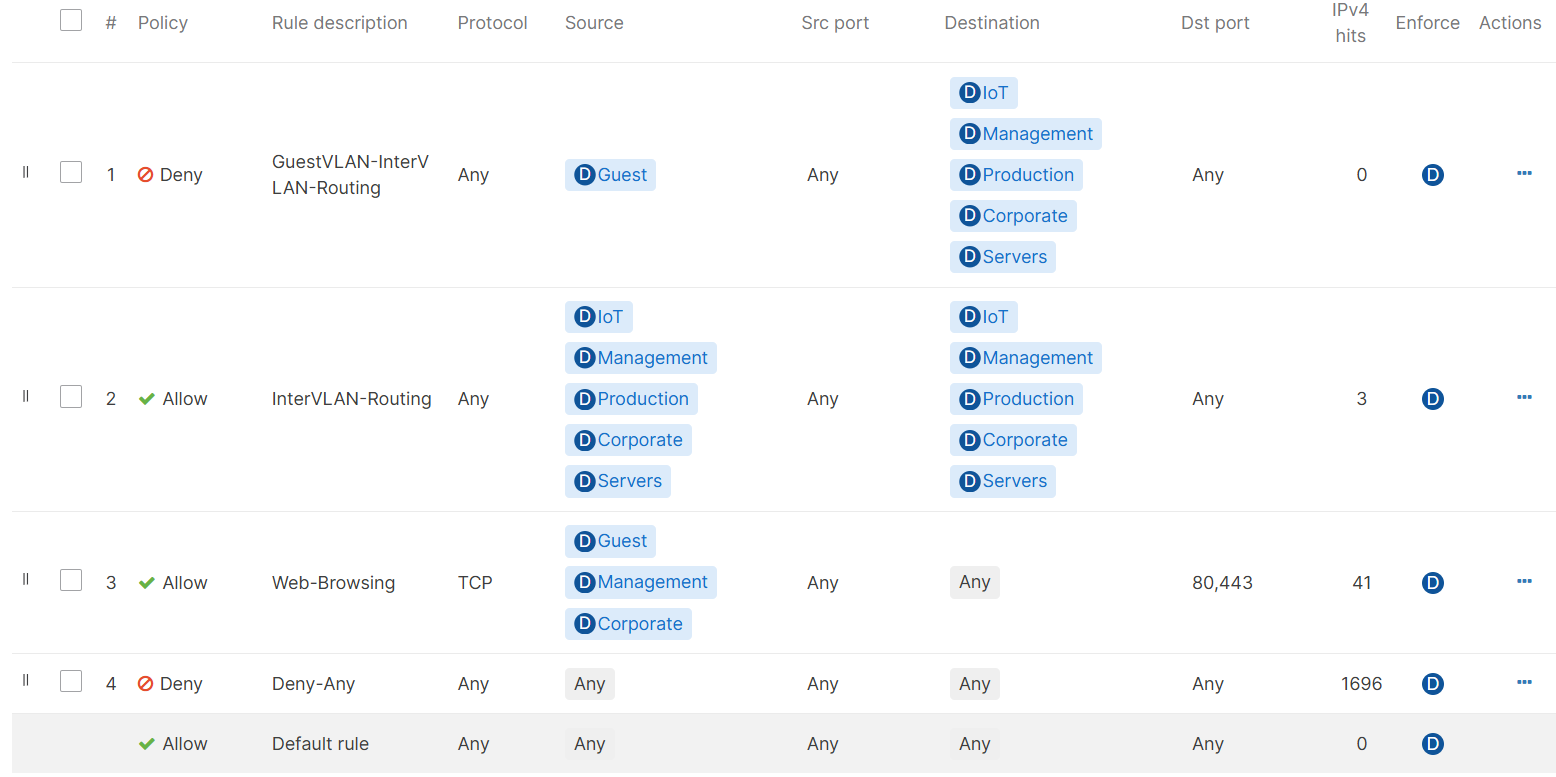
Overview: In this scenario, I have created three outbound rules. Let's go over the purpose of the three defined rules
Defined Outbound Rules
- Rule 1:
- Rule 1 denies the Guest VLAN network from communicating with the devices in other VLANs therefore isolating the Guest VLAN for security
- Rule 2:
- Rule 2 allows Inter-VLAN routing for the IoT, Management, Production, Corporate, and Servers VLAN networks
- Rule 3:
- Rule 3 allows only the Guest, Management, and Corporate VLAN networks to access the Web on ports 80 and 443. VLAN networks IoT, Production, and Servers are restricted to access the Web
- Rule 4:
- Rule 4 is best practice to configure as defining an explicit 'deny any' rule will deny and catch all other traffic that does not match the criteria of the top most rules. In Cisco Meraki, layer 3 firewall rules are processed in a top-down approach
Verification - Layer 3 Firewall Rules
Production PC Client
Overview:
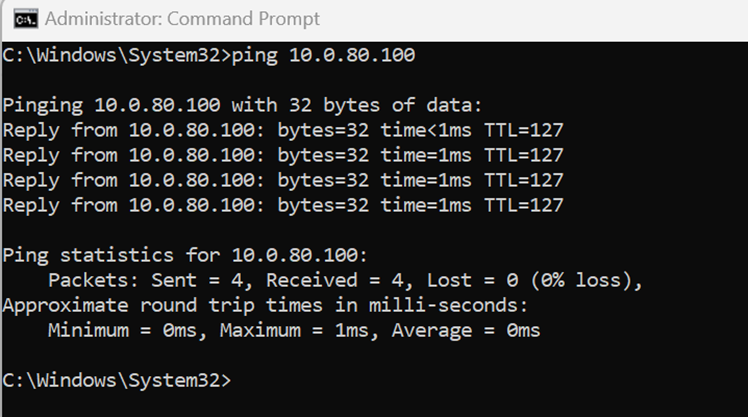
- Based on the layer 3 outbound firewall rules that were defined in the previous step, the Production VLAN is restricted to access the Web but is allowed to participate in Inter-VLAN routing to other VLANs facilitated by the MX firewall
IP Configuration of Production client
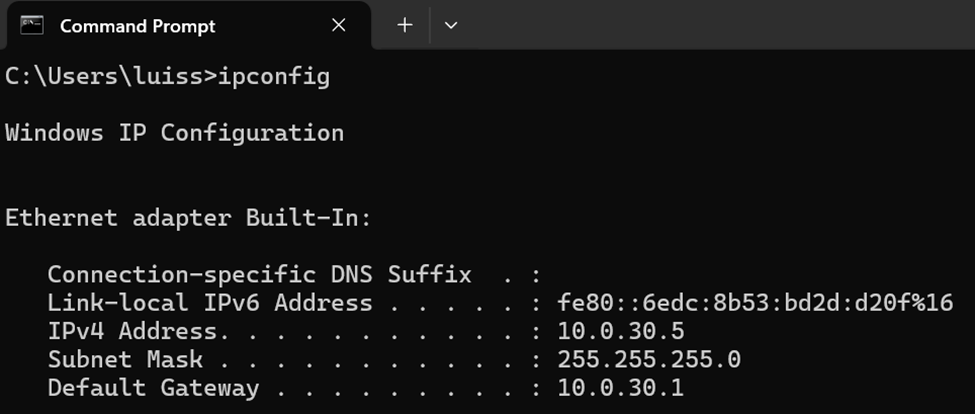
Successful Inter-VLAN routing
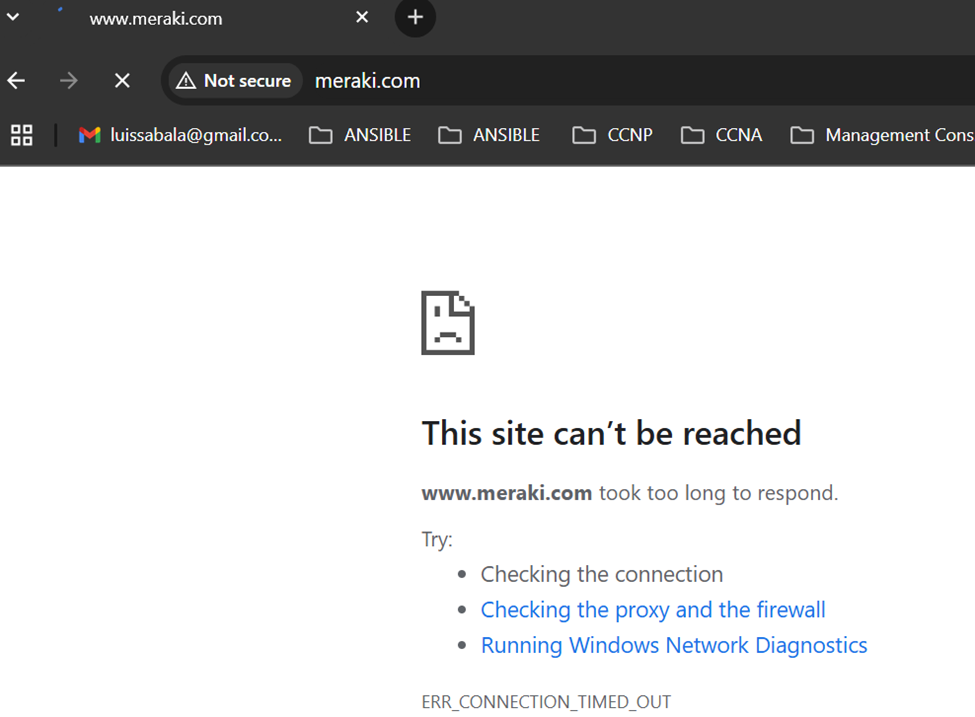
Restricted Web access
Guest PC Client
Overview:
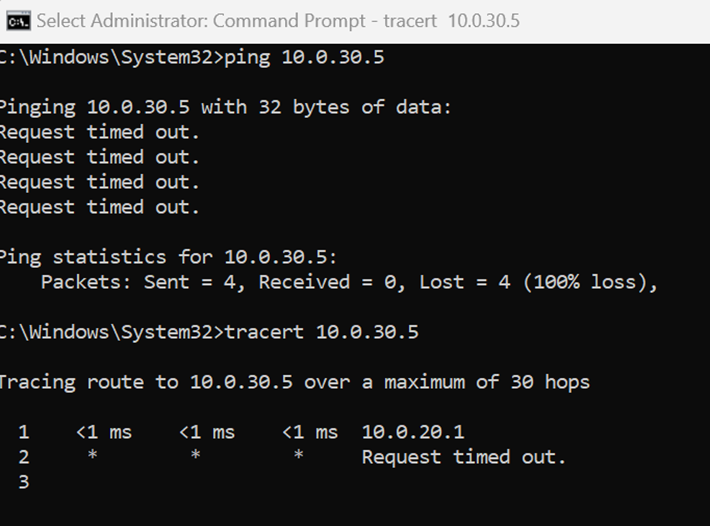
- Based on the layer 3 outbound firewall rules that were defined in the previous step, the Guest VLAN is restricted for Inter-VLAN routing to other VLANs but is allowed Web access out to the Internet
IP Configuration of Guest client
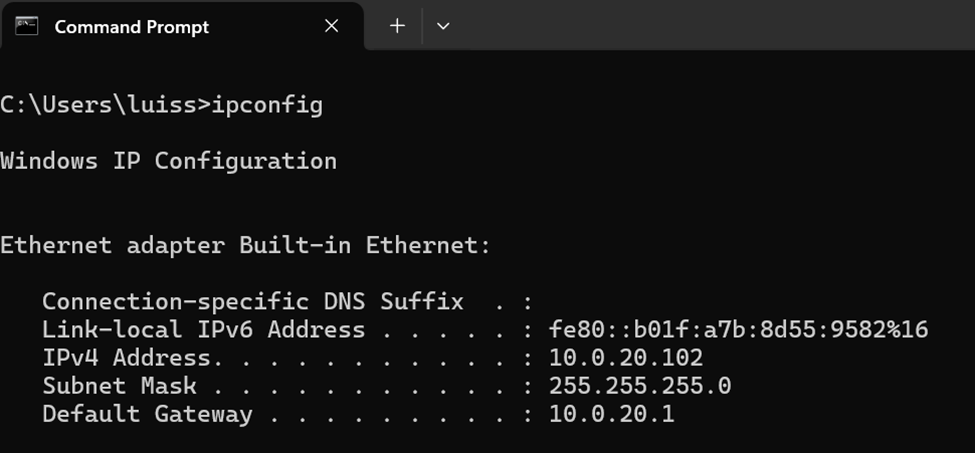
Inter-VLAN routing restricted
Permitted Web access