Next Generation Layer 7 Firewall Configuration
Sections:
- Next Gen Firewall Features
- Lab Topology
- Meraki Layer 3 & 7 Firewall Configuration
- Layer 3 & 7 Firewall Verification
Resources:
- Creating a Layer 7 Firewall Rule
- Layer 3 and 7 Firewall Processing Order
- Implementing Firewall Rules on a Security Appliance
Overview:
- Cisco Meraki MX security appliances provide the ability to create layer 7 firewall rules to deny certain traffic based on traffic type
- In most traditional firewalls, firewall rules typically only inspect headers at the layer 3, layer 4, and layer 5 of the OSI model. With next generation firewalls being more common in today's networks, a layer 7 application rule inspects the entire payload of packets to match against known application types such as Facebook, YouTube, and other services that are not possible with traditional firewalls
- Meraki's layer 7 firewall leverages Application Visibility and Control (AVC) to detect and filter based on applications, allowing granular control over types of applications and services
Next Generation Firewall Features
Overview:
- Next generation firewalls provide a variety of new features that are not present with traditional firewalls
- In this section, I will go over some of the notable features that are common on next generation firewalls
Next Generation Firewall Features
Deep Packet Inspection (DPI)
- NGFWs perform deep packet inspection, analyzing the payload of packets and allowing these types of firewalls to detect malicious content hidden within the traffic. This feature is beneficial to identify threats that may have been missed by traditional firewalls
Intrusion Prevention System (IPS)
- Intrusion Prevention Systems are integrated into NGFWs to detect and block network based attacks such as SQL injections, cross site scripting, buffer overflows, and other exploits. These systems proactively block attack attempts based on known attack signatures
SSL/TLS Inspection
- In today's networks, many modern websites and applications use encrypted traffic (SSL/TLS). NGFWs have the capability to decrypt and inspect this encrypted traffic for threats, ensuring that malicious content does not go undetected
Advanced Malware Protection
- NGFWs often integrate with sandboxing or advanced threat intelligence to detect, analyze, and block zero day malware and advanced threats. These suspected threats can therefore be analyzed in a safe environment before they reach their destination
URL Filtering
- NGFWs can filter traffic based on URLs or domain names, blocking access to specific websites or categories of websites helping reduce distractions, ensure compliance, and protect against malicious websites
Threat Intelligence Integration
- NGFWs often integrate with external threat intelligence feeds to identify and block known malicious IP addresses, URLs, and domains in real time
Advanced Logging and Analytics
- NGFWs have the ability to generate detailed logs of network activity, which can be analyzed to detect anomalies, trends, or signs of an attack
Lab Topology
Overview:
- In this section, I will take a look into configuring stateful legacy layer 3 firewall rules on a Meraki MX security appliance
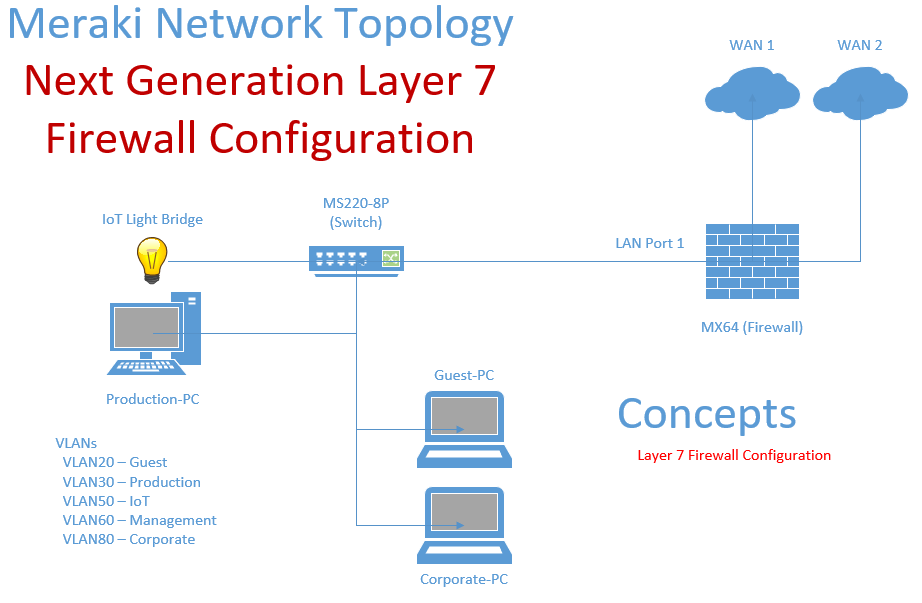
Meraki Layer 3 & 7 Firewall Configuration
Scenario:
- In this lab exercise, I will create layer 7 firewall rules alongside traditional layer 3 rules
Menu to create firewall rules
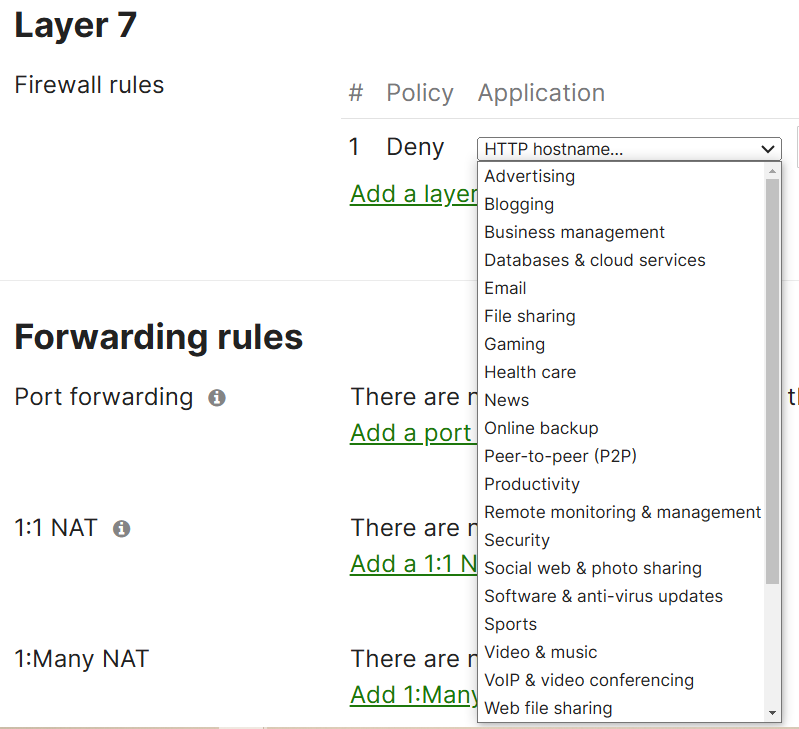
Layer 7 Firewall Rule Section
Pre-defined Layer 7 Application Types
Overview
- In the following firewall rule scenario, I have created outbound layer 3 and layer 7 rules that will be processed together to tighten the security posture
- By default, outbound traffic will be allowed through the firewall unless explicitly blocked by a layer 3 or layer 7 rule. To mitigate this default behavior, I've created an explicit deny 'any' rule for any traffic that does not match any configured rule
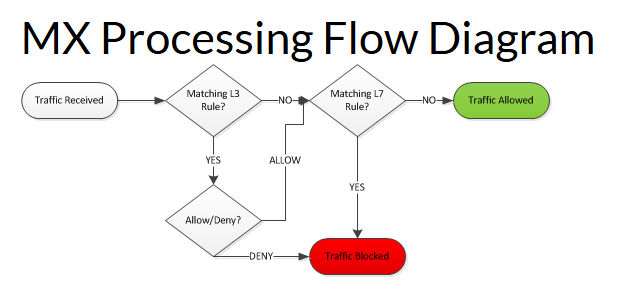
- The MX Processing Flow Diagram by Cisco is an important diagram to understand to ensure firewall rules are acting as intended. Layer 3 firewall rules in Cisco Meraki are checked first before layer 7 firewall rules. Once traffic has a match on a layer 3 rule, the next step would be to check if the traffic also matches a layer 7 rule
MX Processing Flow Diagram
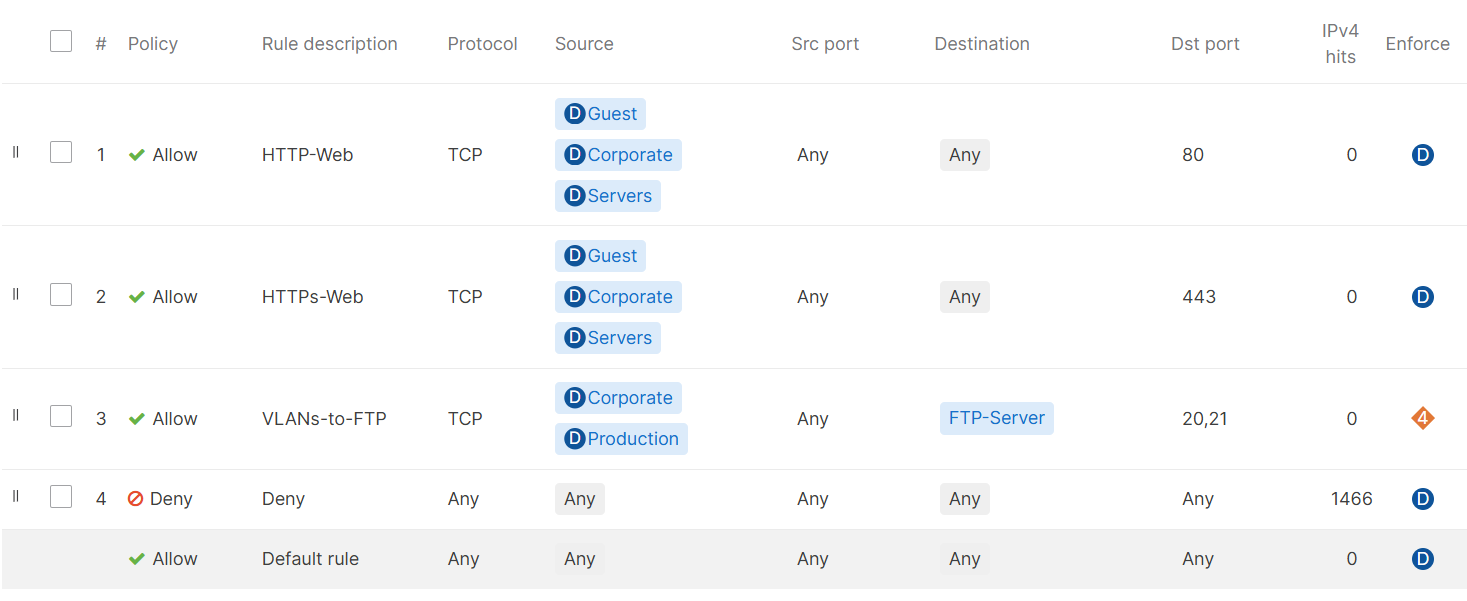
Defined Layer 3 Outbound Rules
- Rule 1:
- Rule 1 allows outbound HTTP web traffic for the Guest, Corporate, & Servers VLAN networks
- Rule 2:
- Rule 2 allows outbound HTTPs web traffic for the Guest, Corporate, & Servers VLAN networks
- Rule 3:
- Rule 3 allows outbound FTP traffic for the Corporate and Production VLAN networks
- Rule 4:
- Rule 4 is an explicit 'deny any' rule to deny traffic that has not been matched by any of the previous layer 3 firewall rules
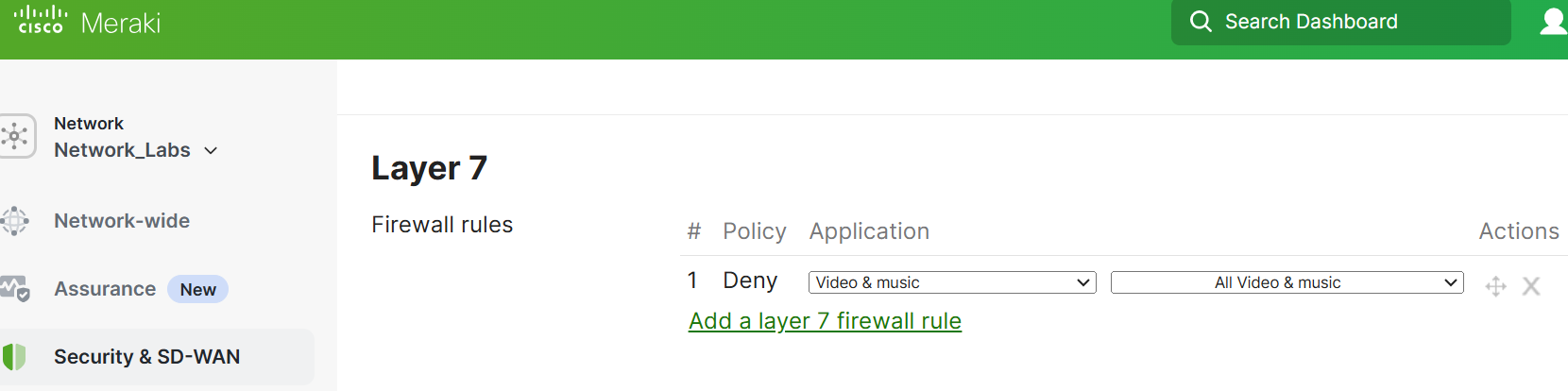
Defined Layer 7 Outbound Rules
- Rule 1:
- If traffic matches any of the 'allow' layer 3 firewall rules, then proceed on checking layer 7 firewall rules. If the traffic also matches the layer 7 rule, deny Web traffic destined for websites categorized as video and music. In this case, Rules 1 and 2 of the layer 3 rules are checked against the layer 7 rule
Verification - Layer 3 & 7 Firewall Rules
Corporate PC Client (VLAN80)
Overview:
- Based on the defined layer 3 and layer 7 outbound firewall rules in the previous step, lets verify the firewall rules are working as intended
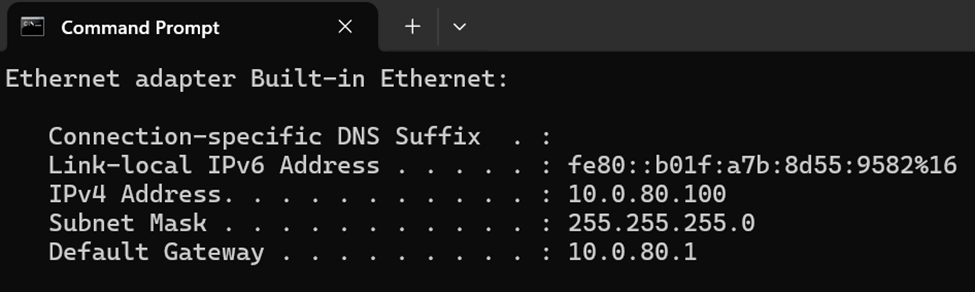
IP Configuration of Corporate client
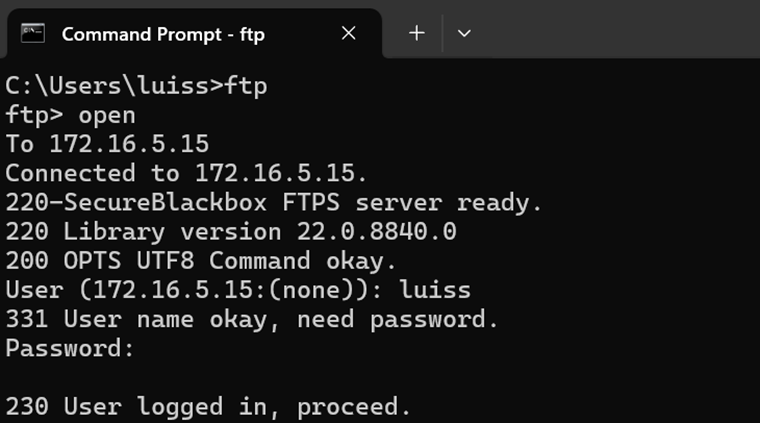
Successful FTP connection defined in layer 3 FW - rule 3 (VLANs-to-FTP)
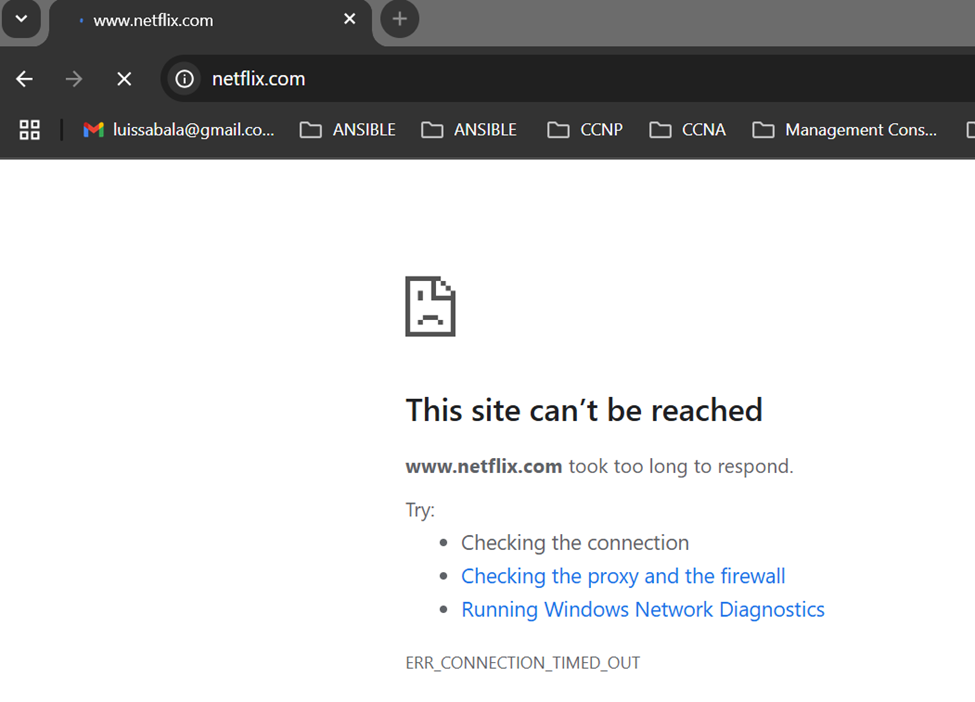
Restricted Netflix access defined in layer 7 FW - rule 1
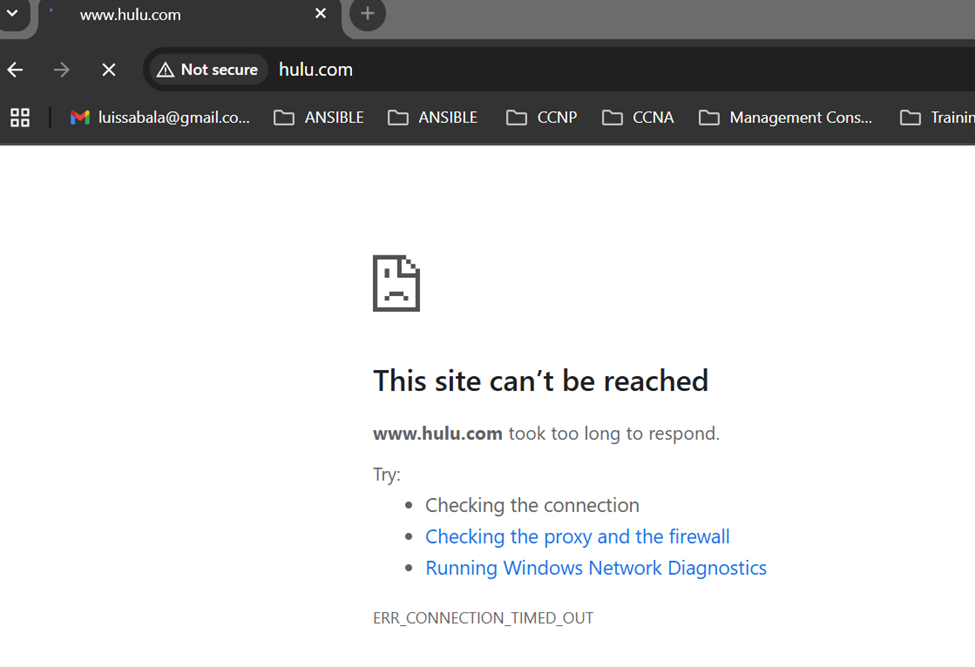
Restricted Hulu access defined in layer 7 FW - rule 1