Monitoring Meraki Wireless Networks
Sections:
Resources:
Overview:
- The Monitoring section of Cisco Meraki MR access points is a crucial aspect of network management
- It allows admins to keep track of the performance, health, and security of the wireless network
- In the Meraki Dashboard, various monitoring tools and reports are available to give real time insights into how the network is operating and a source to analyze potential issues
- In this section, I will demonstrate the different monitoring tools Meraki access points have to offer
Monitoring Access Points
Overview:
- The Access Points Monitoring section within the Meraki Dashboard provides detailed insights into the performance, status, and health of each access point in your network
- This section allows network admins to monitor various metrics in real time, troubleshoot issues, and optimize the wireless network
Access Points Menu
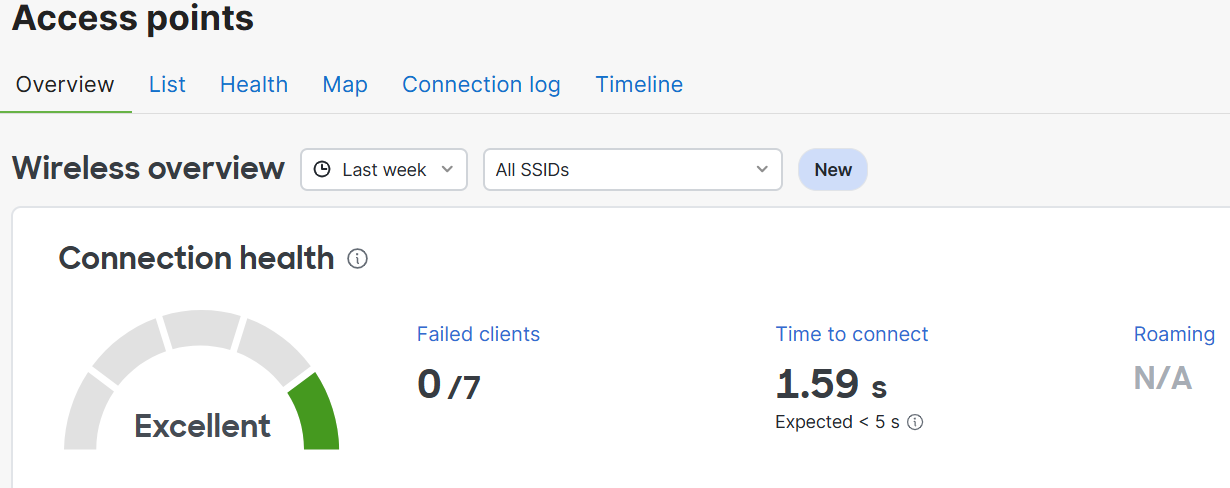
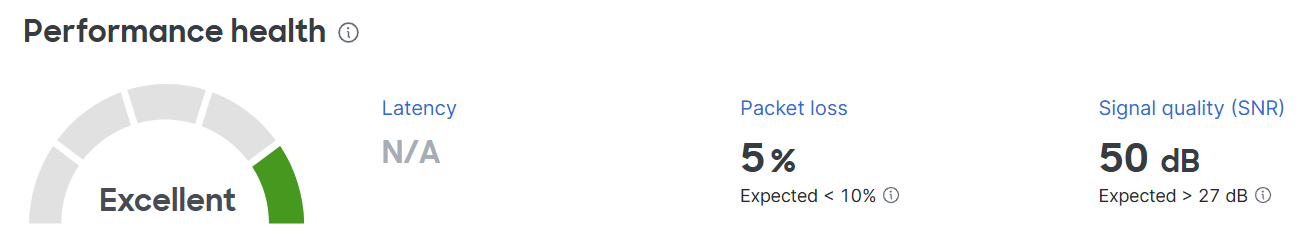
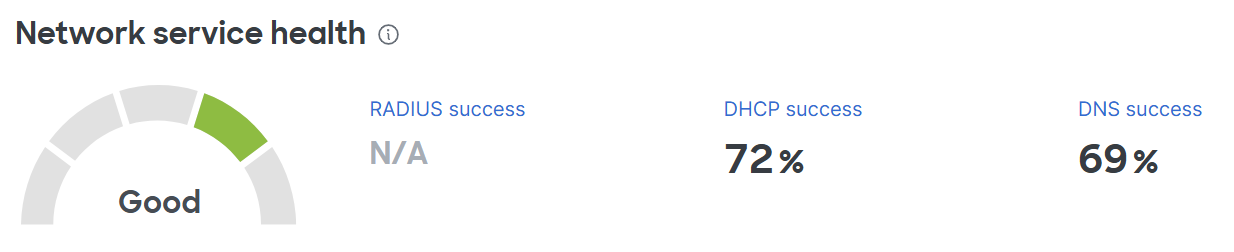
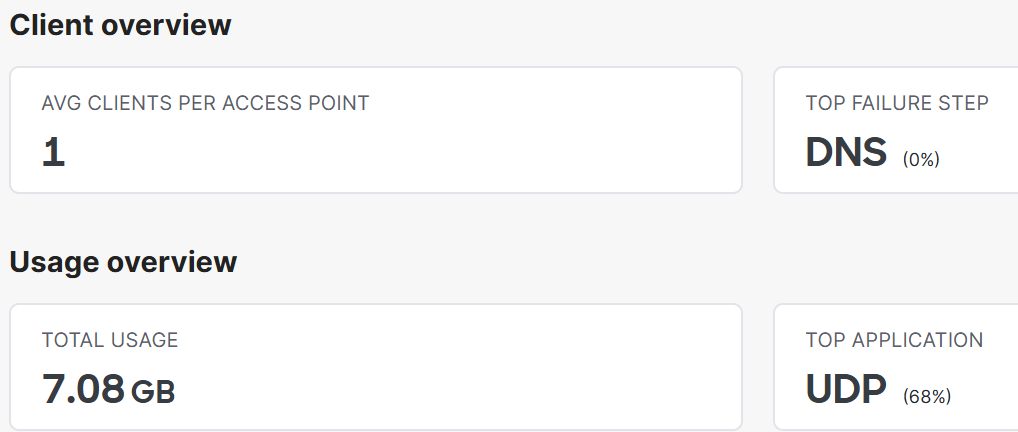
Overview Section
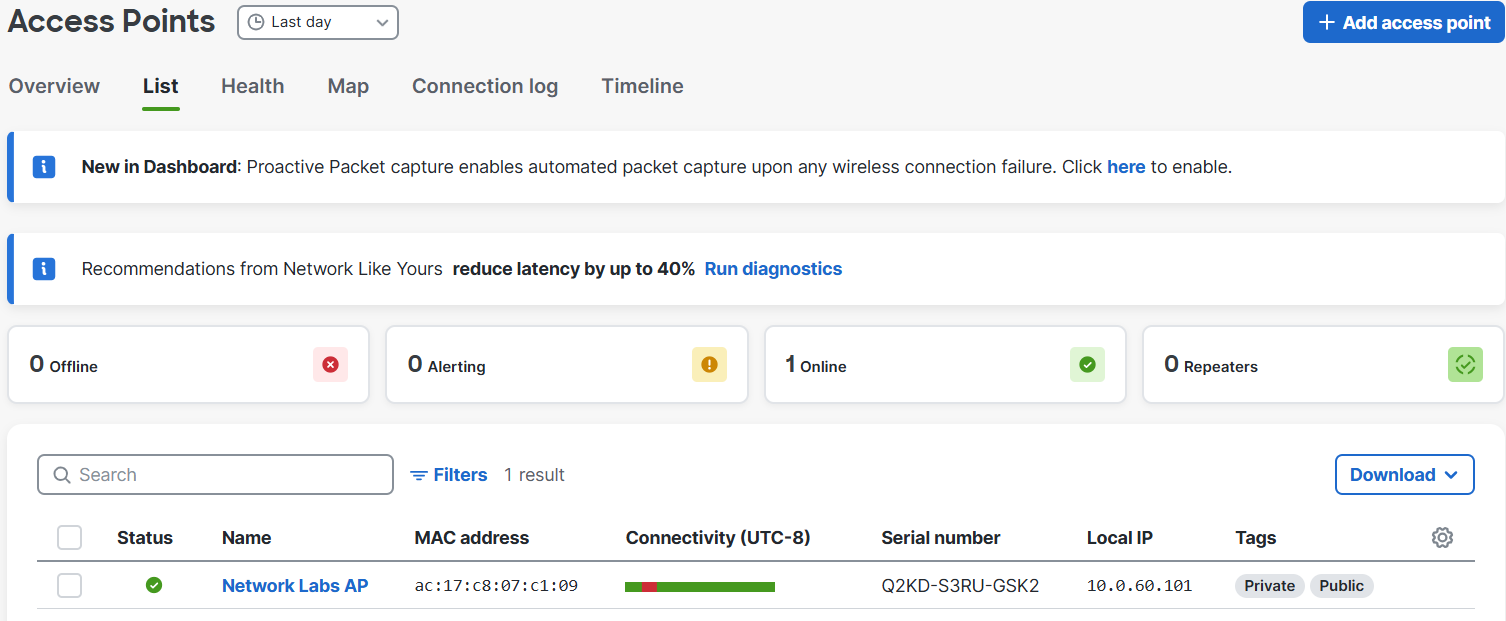
List Section
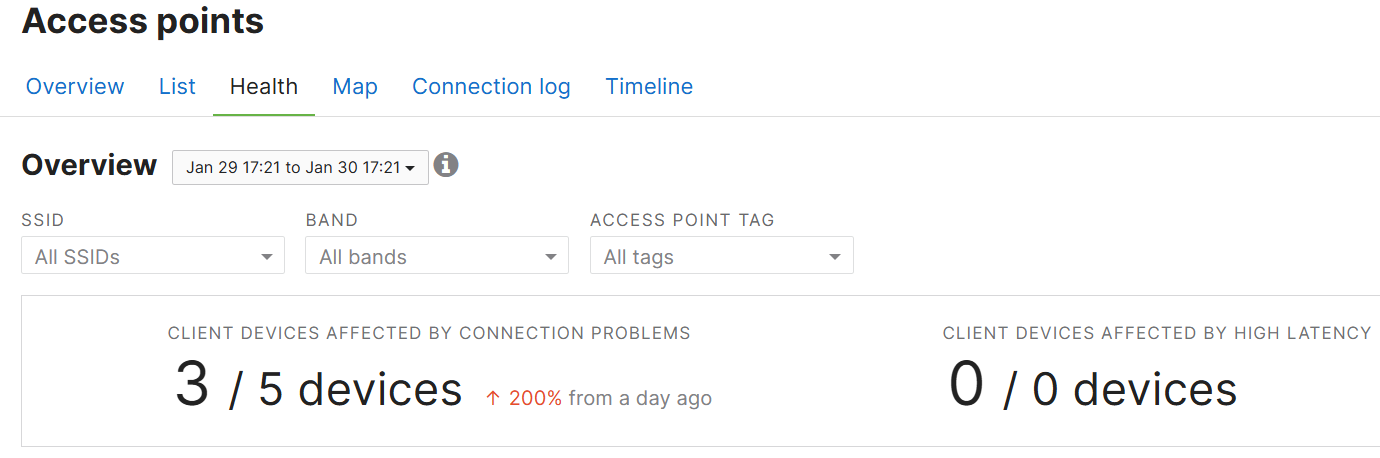
Health Section
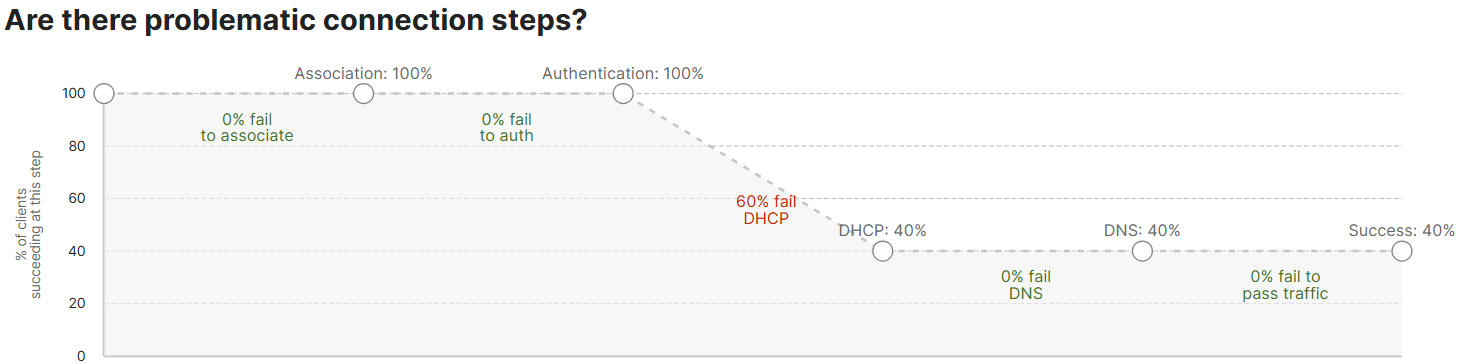
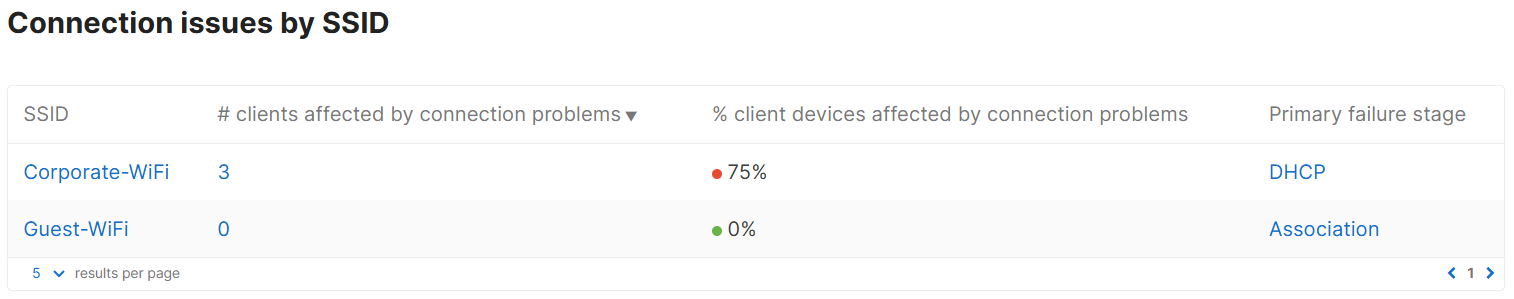
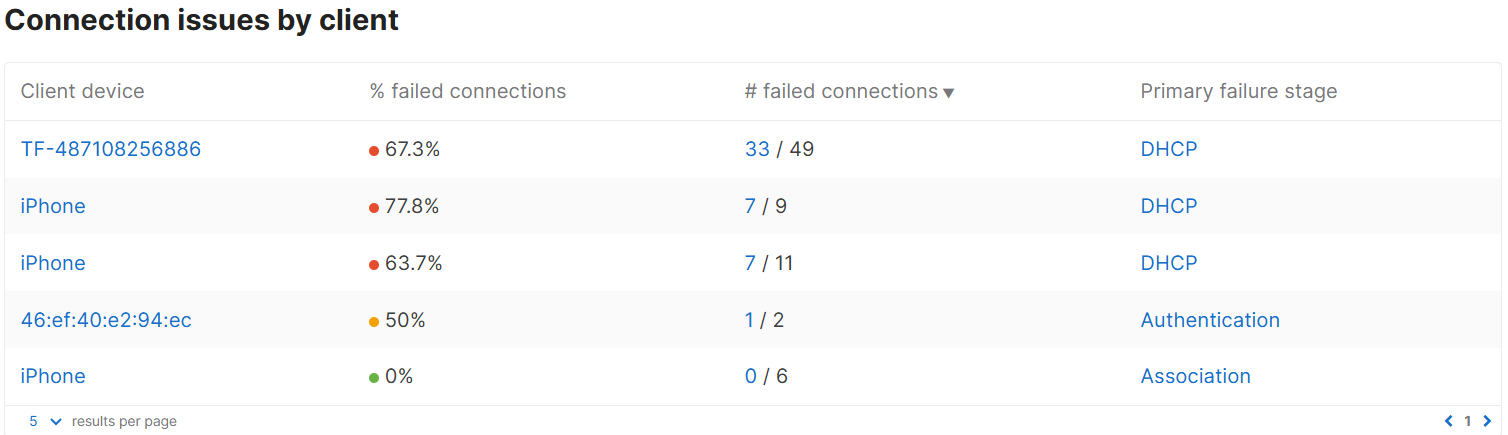
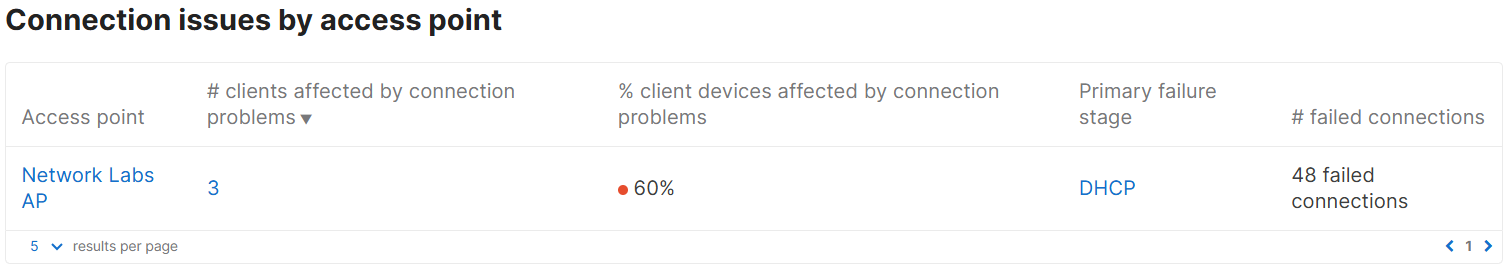
Connection Log Section
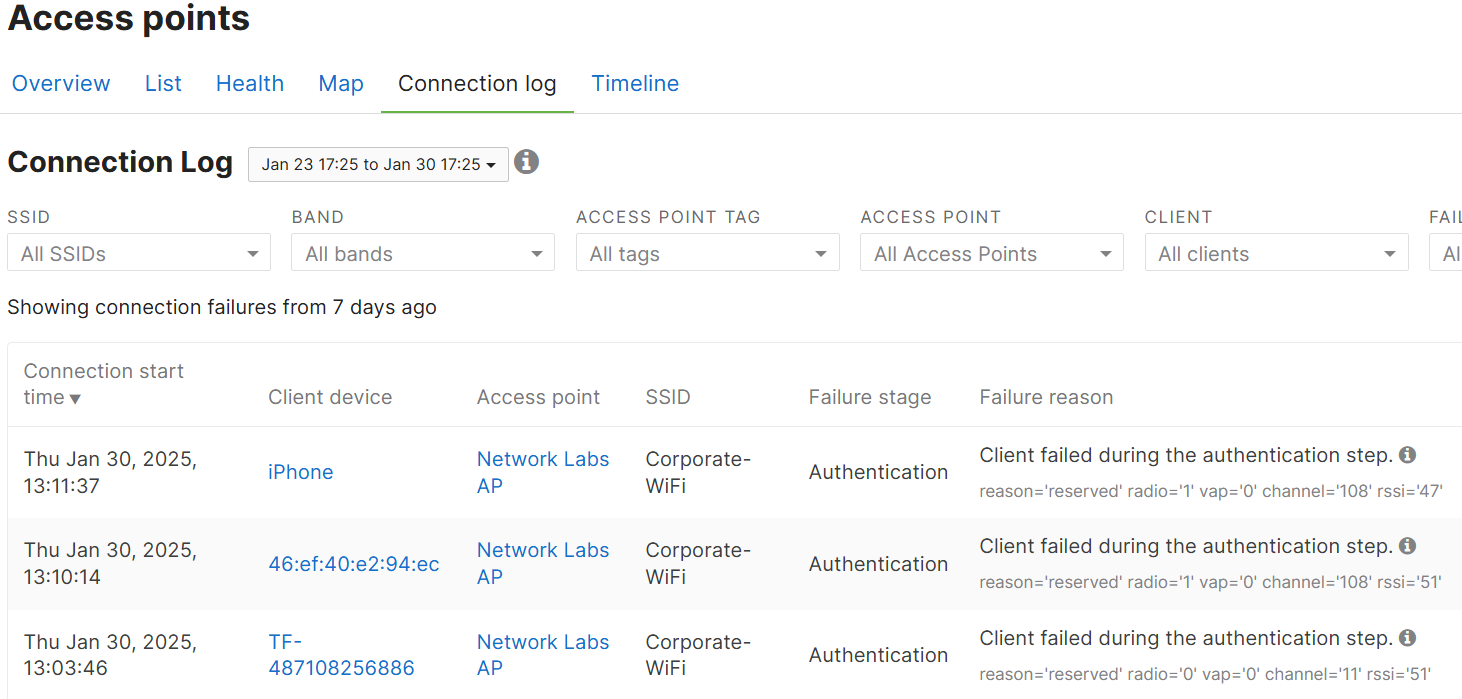
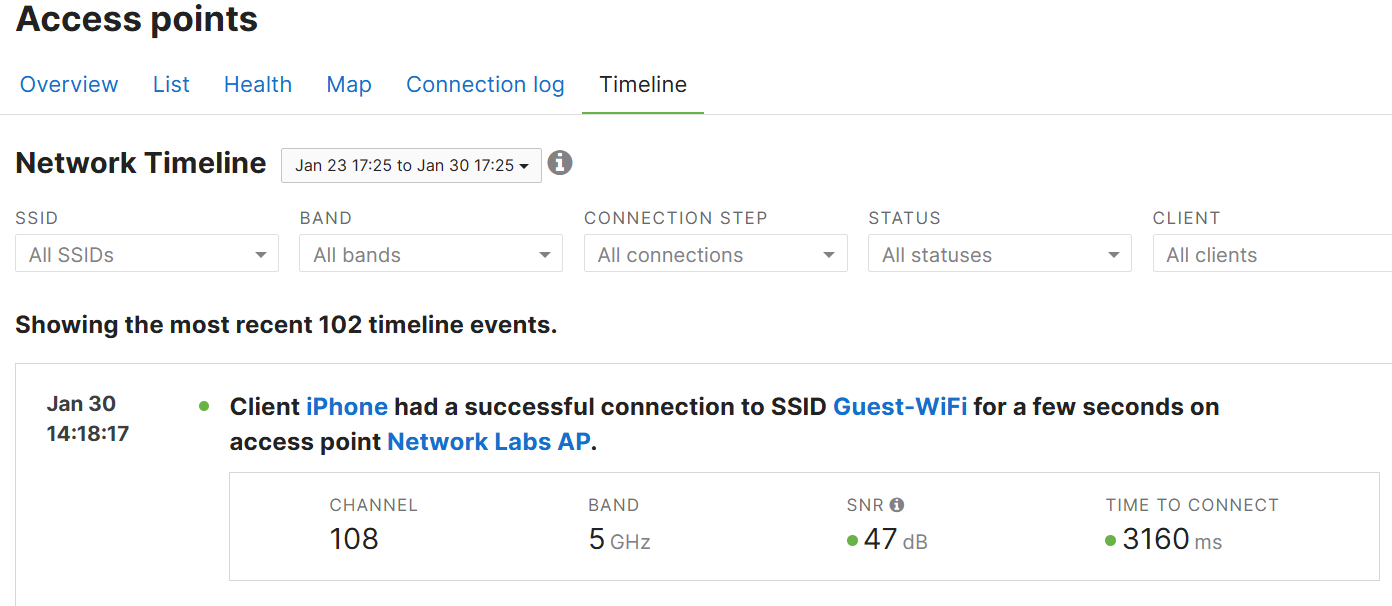
Timeline Section
Monitoring Air Marshal
Overview:
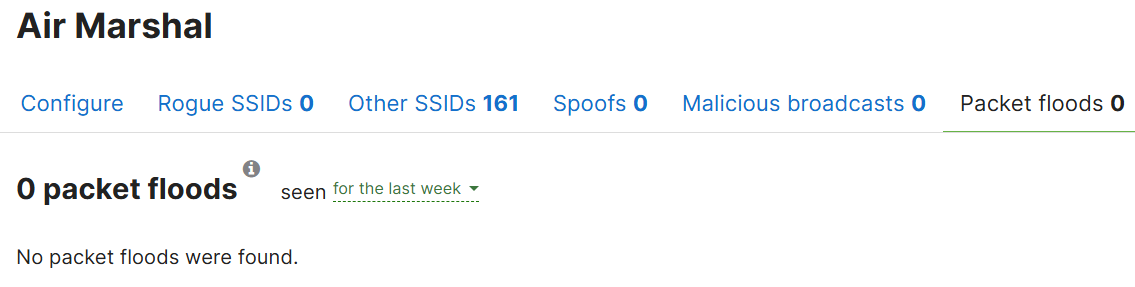
- Air Marshal is a security and wireless intrusion detection/prevention feature available for Cisco Meraki MR access points
- It is designed to detect and protect against wireless security threats, particularily those related to rogue access points, unauthorized devices, and other wireless attacks in the environment
- Air Marshal provides admins with real time visibility into the wireless landscape, enabling them to take action to mitigate threats and maintain a secure network
Air Marshal Menu
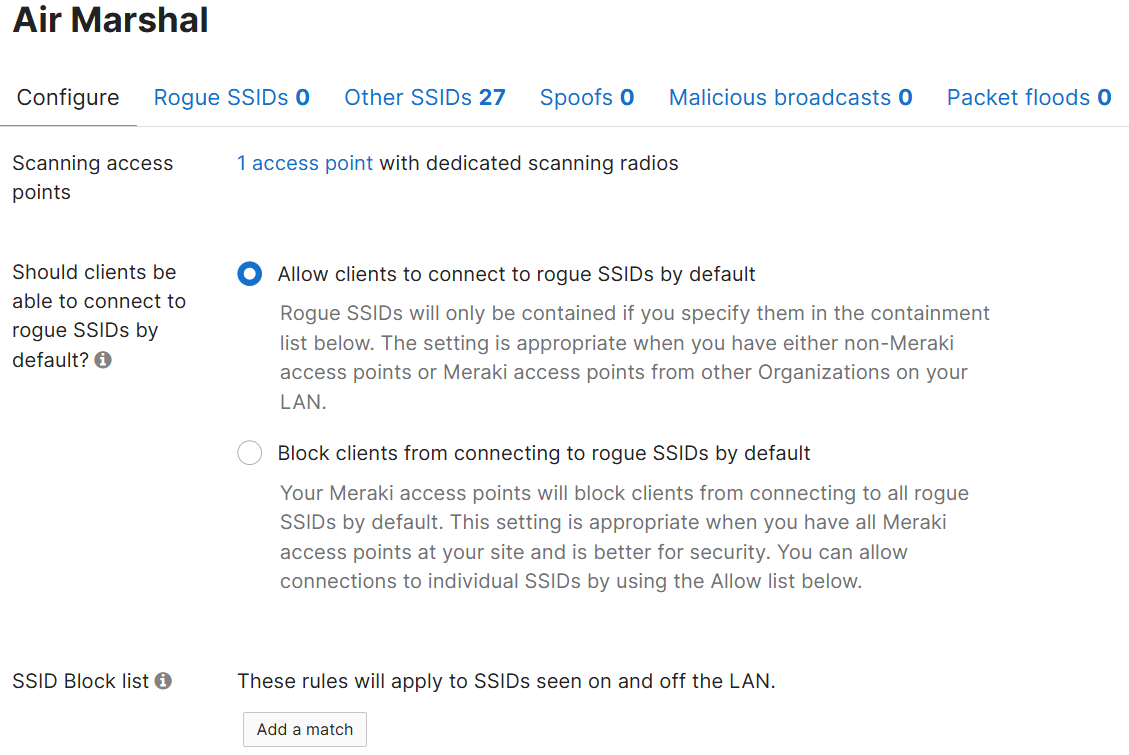
Configure Section
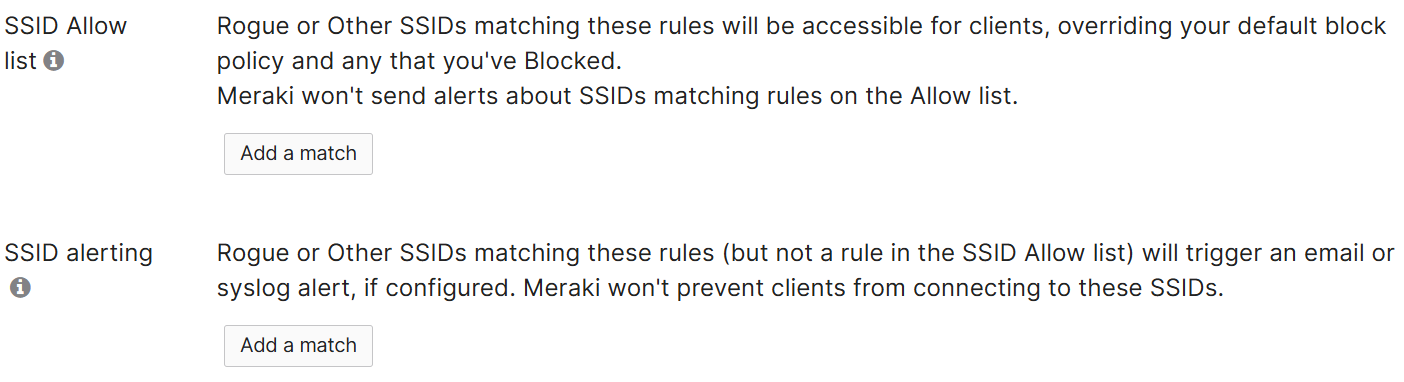
Rogue SSIDs Section
Other SSIDs Section
Spoofs Section
Malicious Broadcasts Section
Packet Floods Section
Monitoring Login Attempts
Overview:
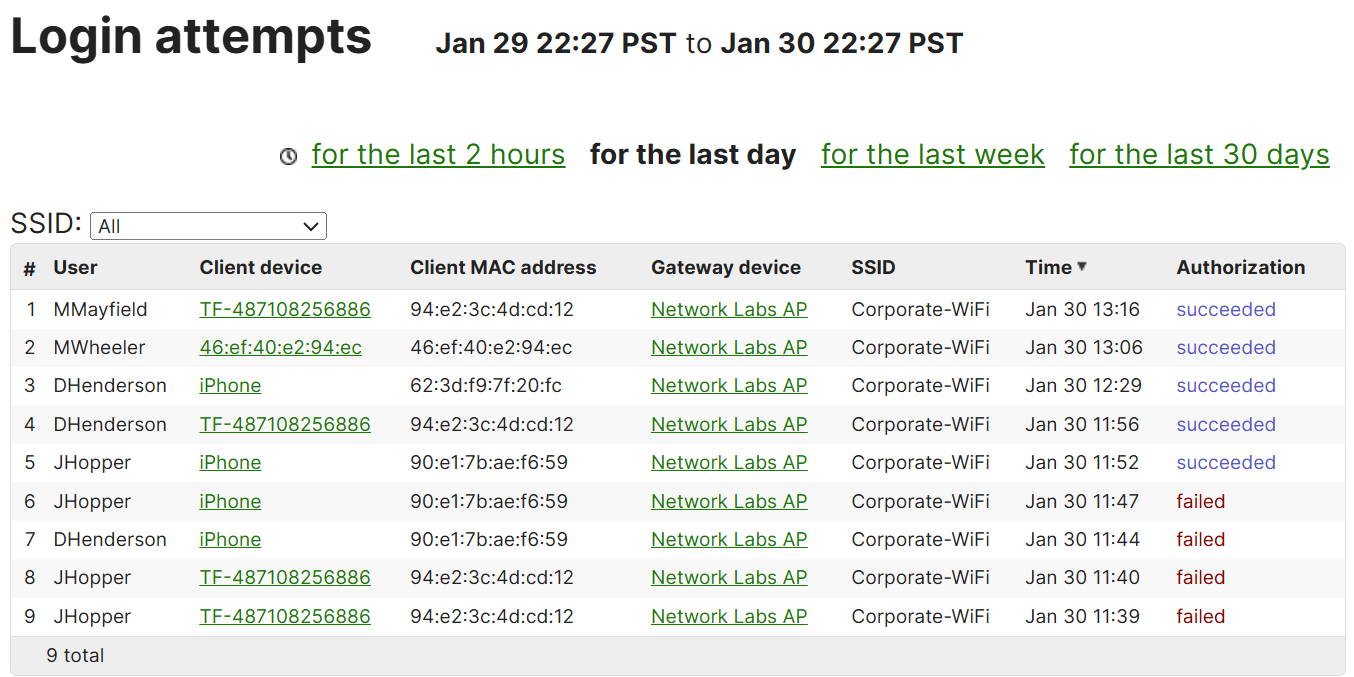
- The Login Attempts section is part of Meraki's wireless suite of monitoring tools
- This feature tracks and logs the authentication attempts made by devices trying to connect to the wireless network
- This feature helps network admins monitor potential security issues, identifying unauthorized access attempts, and troubleshoot client connection problems
Login Attempts Menu
Login Attempts Section
Monitoring Splash Logins
Overview:
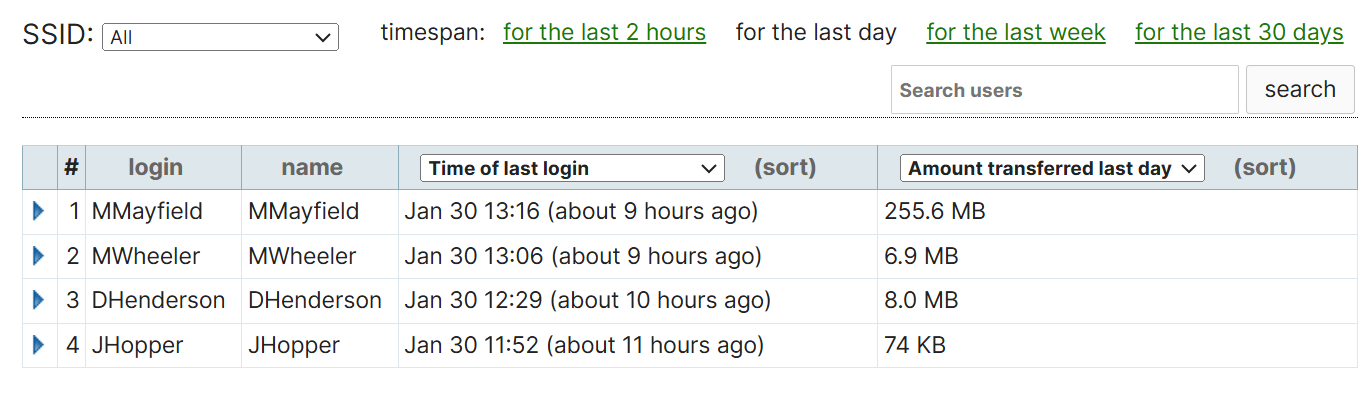
- The Splash Logins section is part of the Splash page functionality, typically used in environments where guest access or public Wi-Fi is provided
- This section logs the details of users who authenticate via the splash page (successful and failed login attempts), which is the page that clients see before being granted access to the Internet
Splash Logins Menu
Splash Logins Section
Monitoring Bluetooth Clients
Overview:
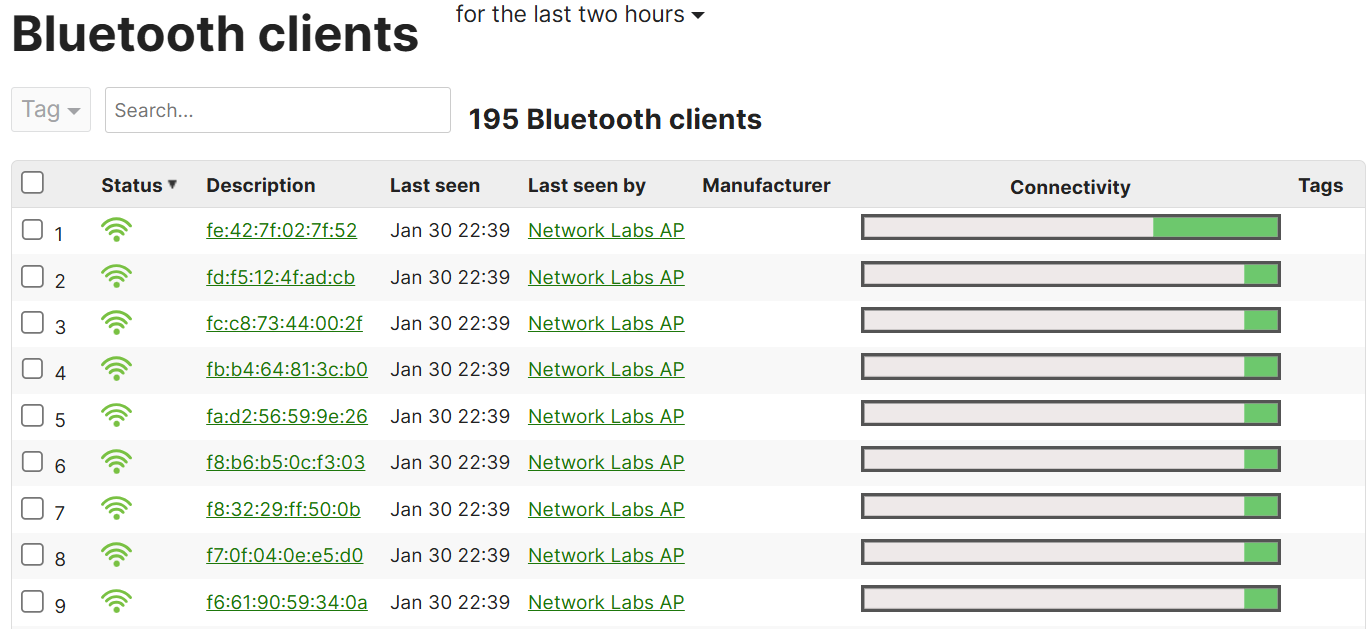
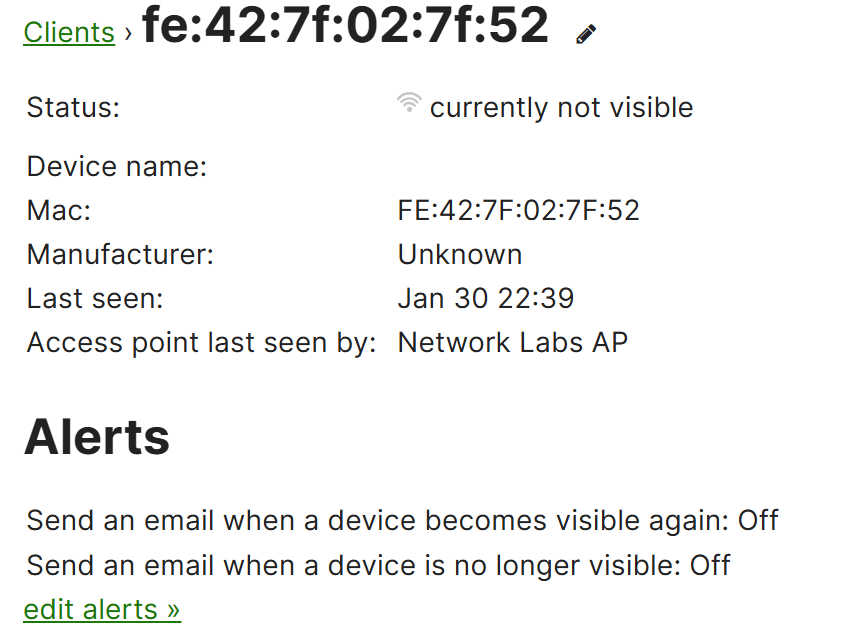
- The Bluetooth Clients section provides visibility into Bluetooth enabled devices that are interacting with the Meraki network through the Bluetooth Low Energy (BLE) functionality
- This feature can be used for a variety of purposes, including tracking the presence of devices (such as smartphones or BLE-enabled IoT devices), managing proximity-based interactions, and enabling specific Bluetooth-based services like location tracking or proximity alerts
Bluetooth Clients Menu
Bluetooth Clients Section
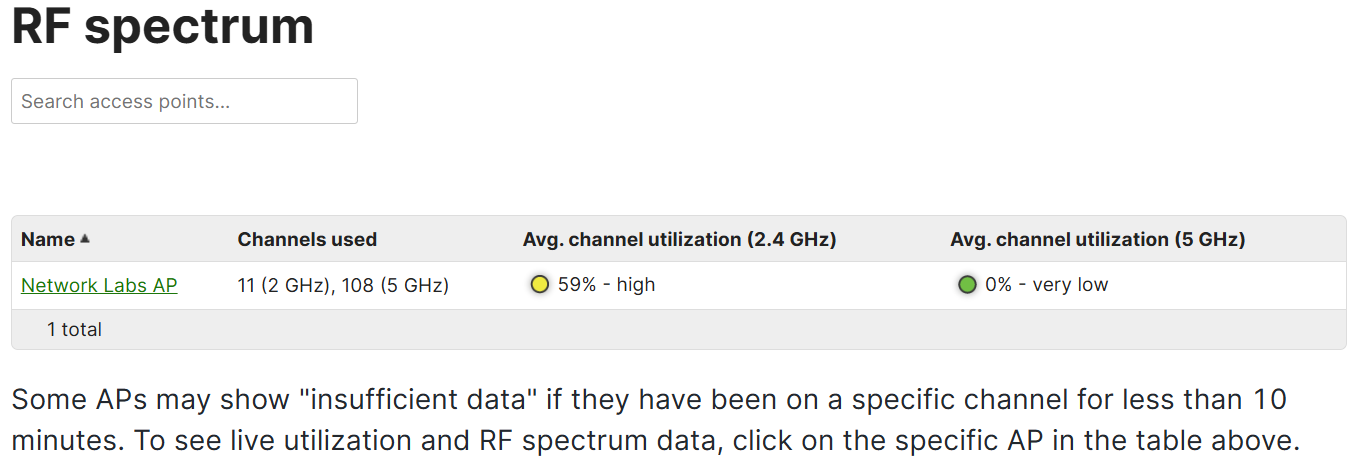
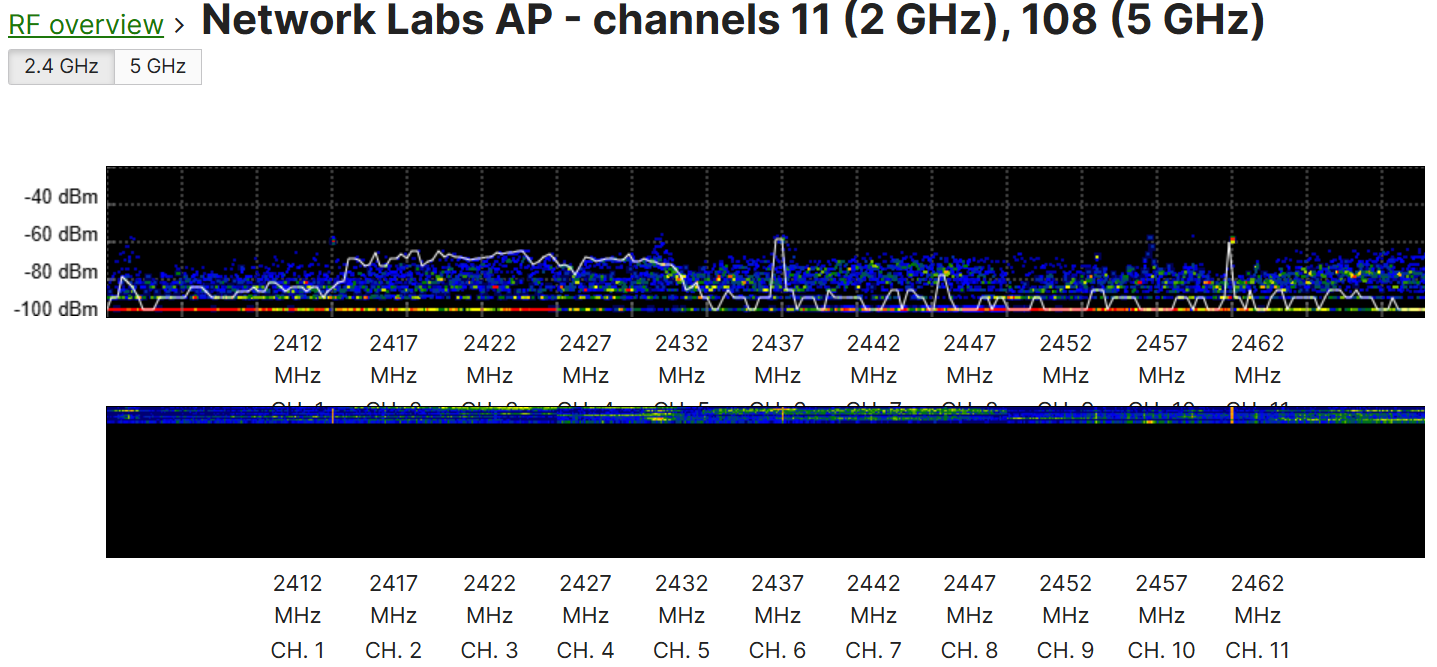
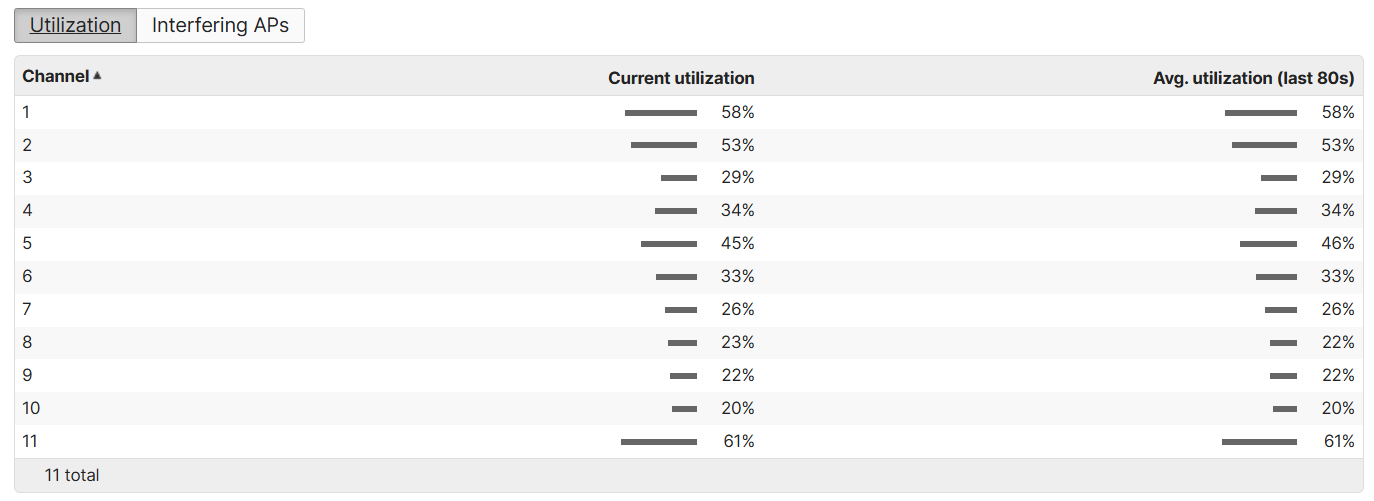
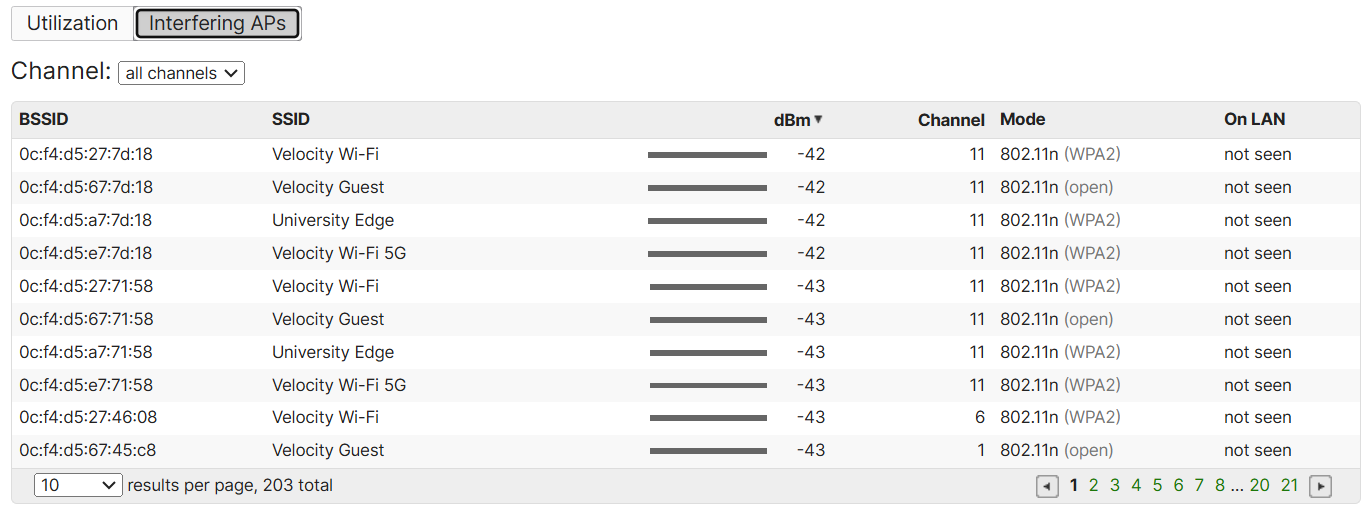
Monitoring RF Spectrum
Overview:
- The RF Spectrum section is a feature that provides insights into the radio frequency (RF) environment surrounding the Meraki access points
- This section helps admins monitor and analyze the wireless spectrum for potential interference or issues that may affect the performance of the Wi-FI network
- By leveraging the built-in radio scanners on Meraki MR access points, the RF Spectrum feature allows you to detect and visulaize RF noise, channel congestion, and other wireless activity in real time
RF Spectrum Menu
RF Spectrum Section