Addressing & VLANs
Sections:
- Lab Topology
- Deployment Settings
- Deployment Setting Configuration
- VLAN Configuration
- Per Port VLAN Assignment
Resources:
Overview:
- In a Cisco Meraki MX Firewall, addressing and VLANs are key components used to segment and organize your network to ensure both security and performance
- The MX security appliance can be deployed with a deployment setting (Routed or Passthrough/VPN Concentrator) that determines how the device handles network traffic
- In this lab exercise, I will demonstrate how to define VLANs, assign LAN ports specific VLANs and configure the deployment settings
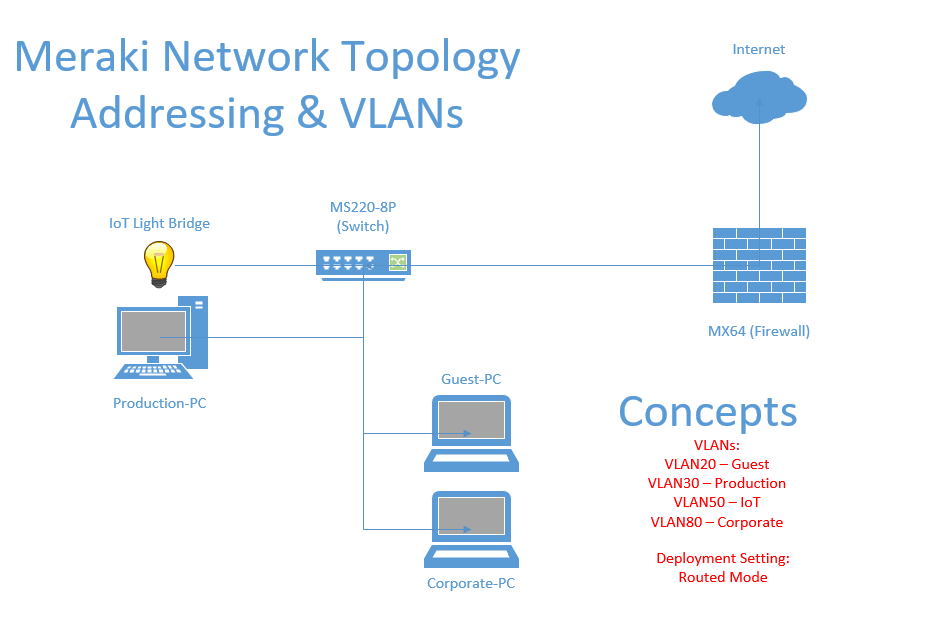
Lab Topology
Deployment Settings
Deployment Mode Overview
- The Meraki MX security appliance supports Routed or Passthrough modes which is essential for defining how the appliance interacts with other devices in the network
Deployment Modes
- Routed Mode
- In a routed mode scenario, the Meraki firewall acts as the gateway for the network and is the default mode and the most common deployment method for Meraki networks. In this mode, the MX appliance is responsible for routing traffic between the internal LAN network and external networks including the Internet. To summarize, the MX firewall would provide internet connectivity, routing, and security to the internal network LAN
- Passthrough Mode
- In a passthrough mode scenario, the Meraki firewall is effectively bypassed for routing functions. The MX appliance does not perform layer 3 routing but still provides security features such as firewalling, VPN, and monitoring. To summarize, the MX firewall functions purely as a security appliance in front of an existing router or gateway
Client Tracking Overview
- The MX security appliance defines ways to identify clients based on either MAC address or IP address
- This MX feature allows administrators to track and manage client devices for purposes such as security, performance monitoring, and network optimization
- It's important to note that all other Cisco Meraki devices will only distinguish clients based on MAC addresses
Client Tracking Modes
- MAC Address
- In most cases, it is recommended to set this mode to the default 'MAC address' method
- In this mode, the MX appliance is in the same broadcast domain as all clients in the network therefore allowing the MX to view client MAC addresses as traffic passes
- IP Address
- This scenario is recommended for cases in split networks, where all layer 3 Meraki only devices, are in separate dashboard networks
- A second use case of this method is when there is a non-Meraki layer 3 switch performing inter-VLAN routing downstream of the MX appliance
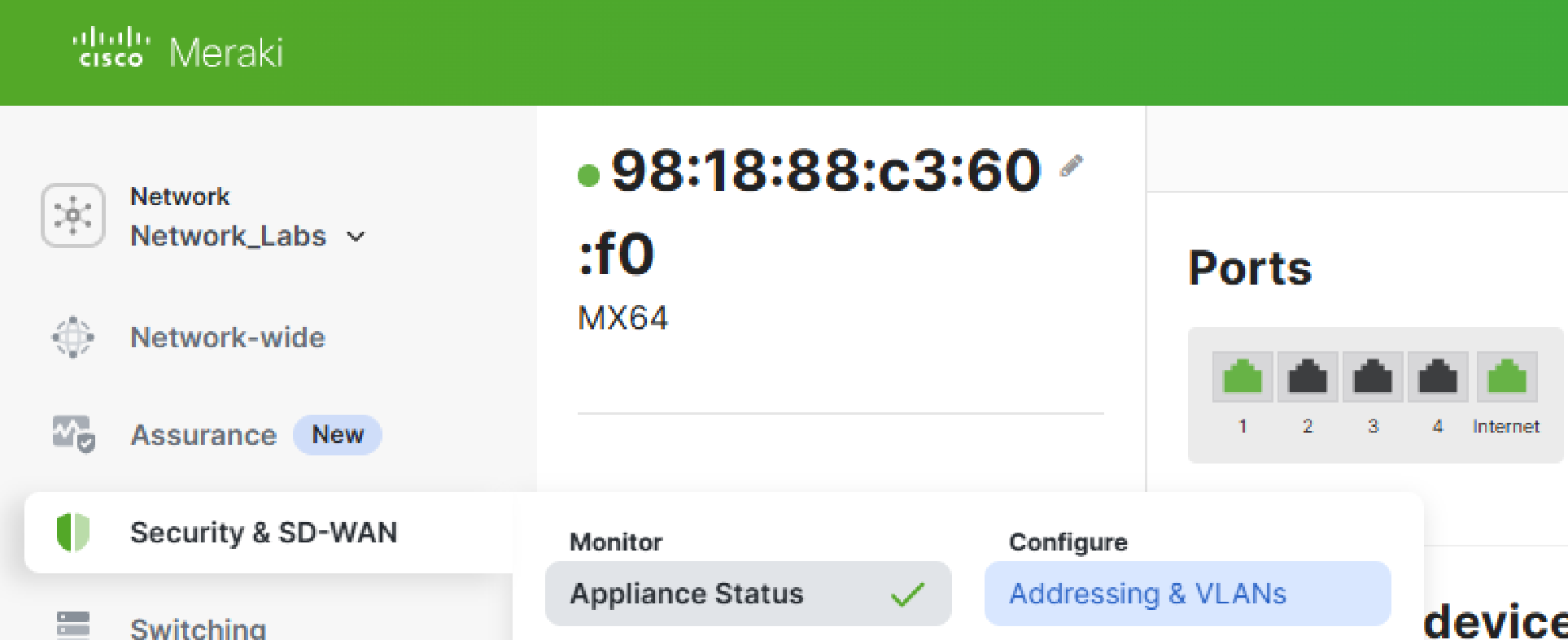
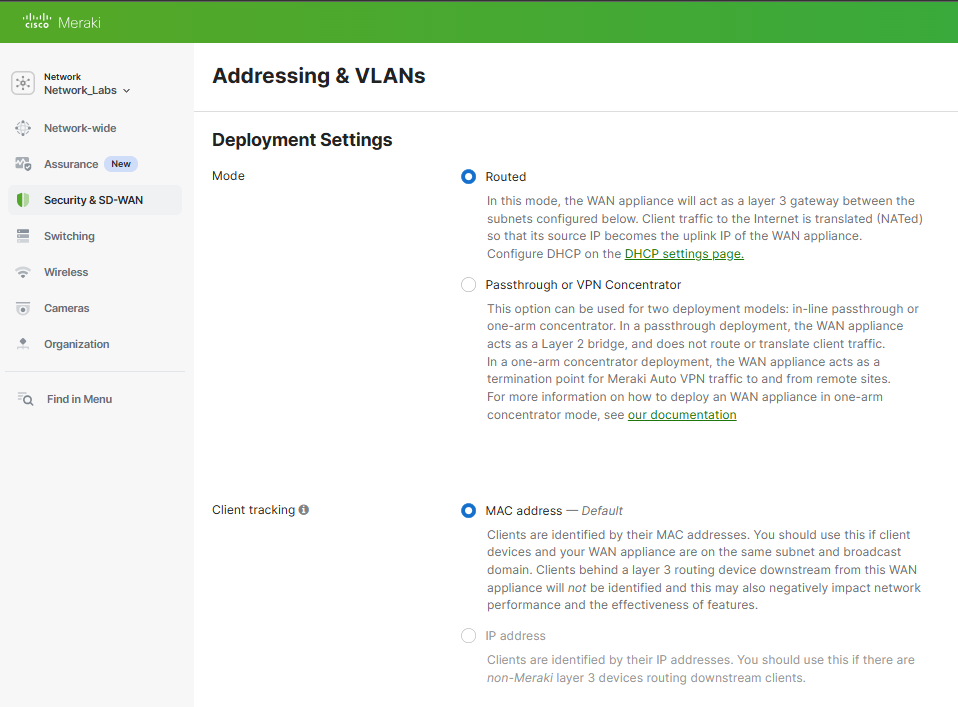
Configuration - Deployment Settings
Scenario:
- In this lab exercise, I will define the 'Routed' deployment mode for the devices on my Meraki network and utilize the 'MAC address' client tracking method
Configuration - VLANs
Scenario:
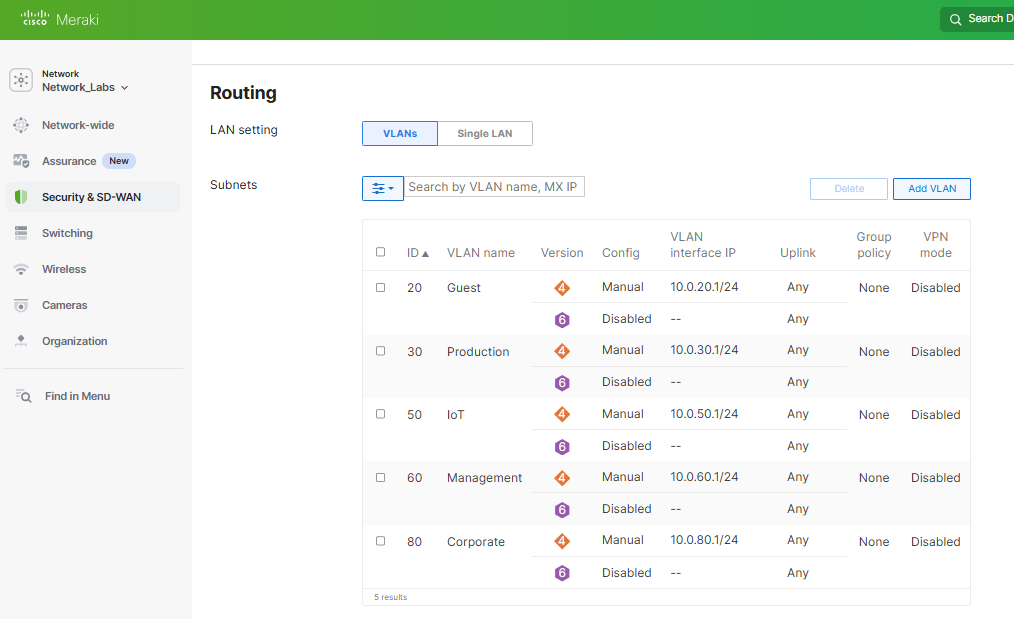
- The Meraki MX appliance offers an easy way to define VLANs to segment the network into smaller subnets improving security for different traffic types and traffic management. In this lab exercise, I will demonstrate going through the steps of defining the VLANs listed in my network topology
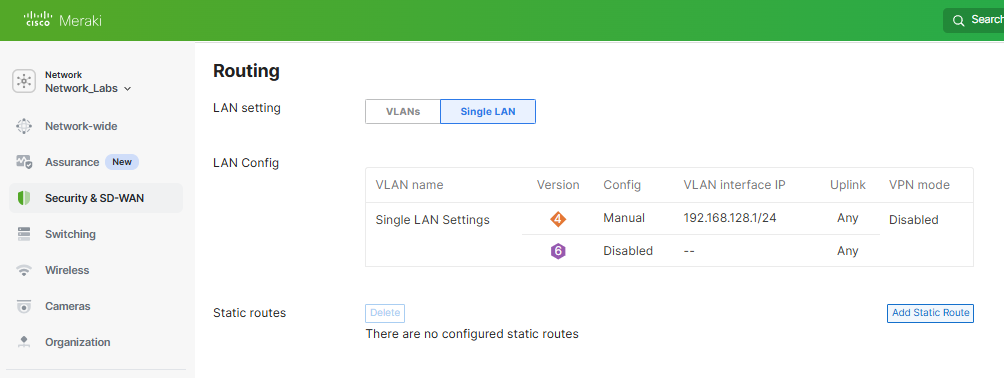
- By default, the MX appliance comes pre-configured with VLAN1 defined in the '192.168.128.0/24' network
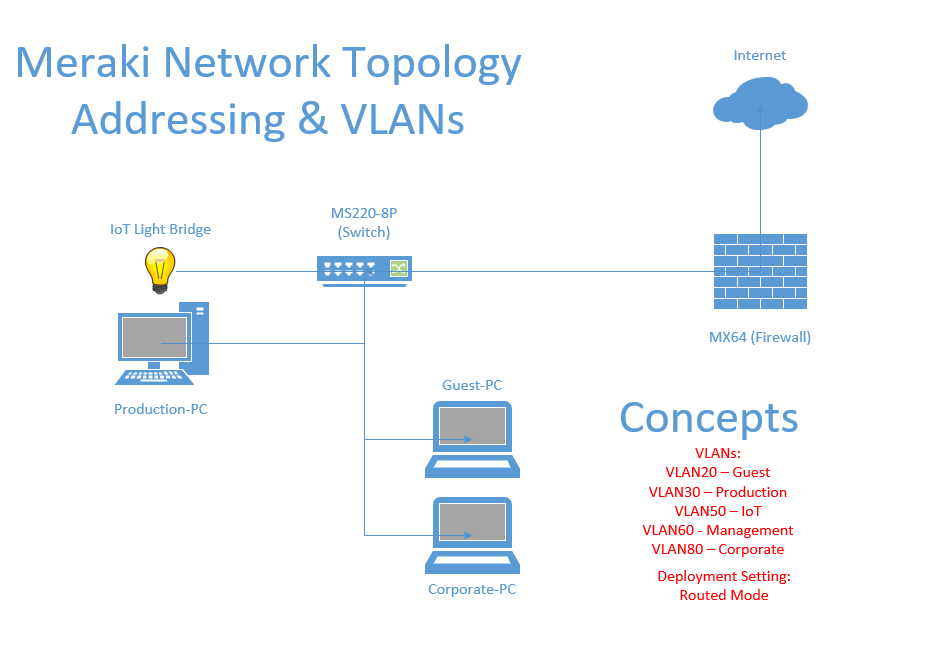
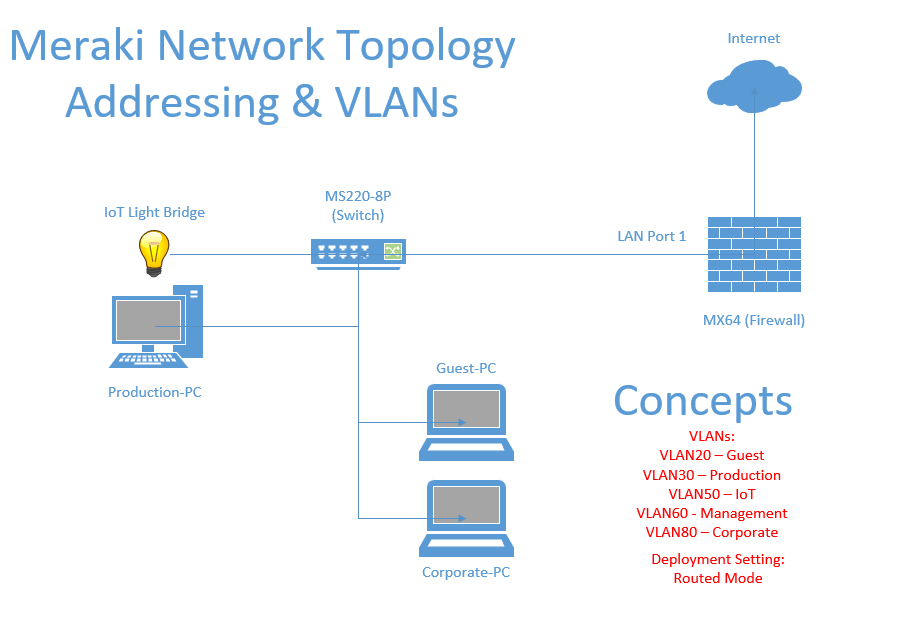
Network Topology
Meraki MX - Default Addressing & VLANs Page
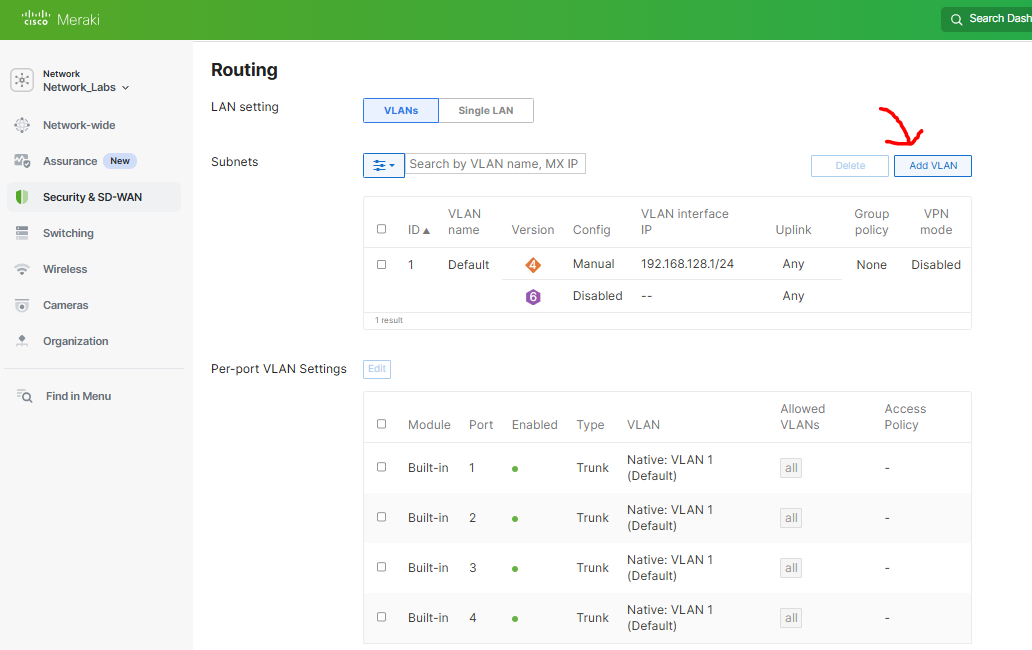
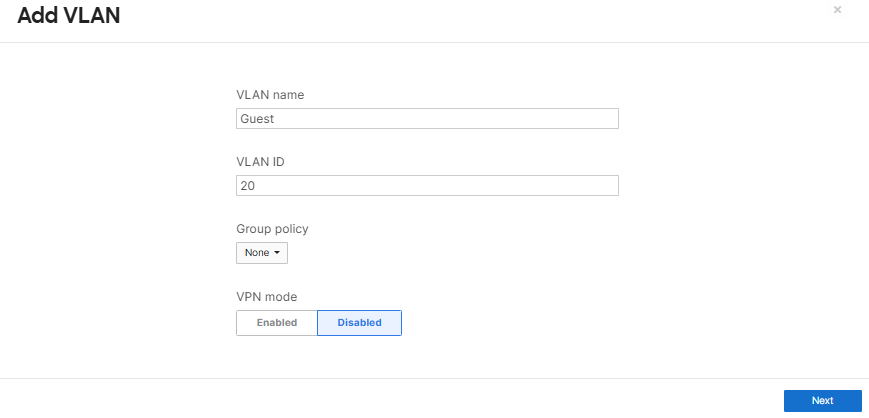
Defining a new VLAN
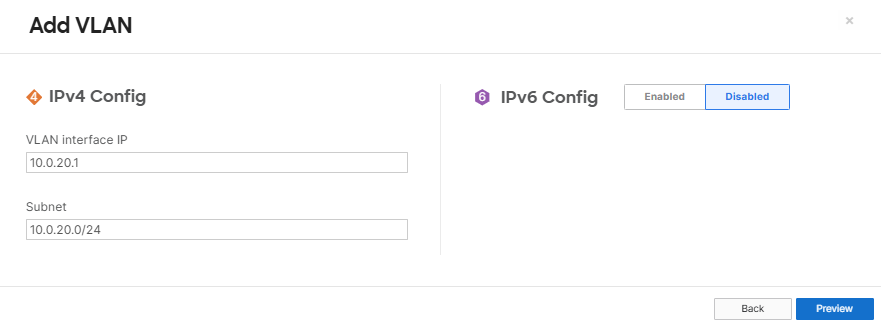
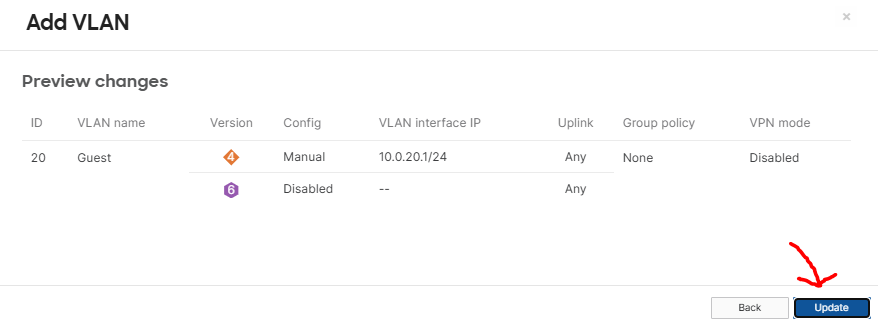
All VLANs in the Network Topology Defined
VLAN Port Assignment
Scenario:
- Upon defining VLANs on an MX security appliance, Meraki allows the administrator to assign the firewall LAN ports as either access or trunk ports with VLAN assignments
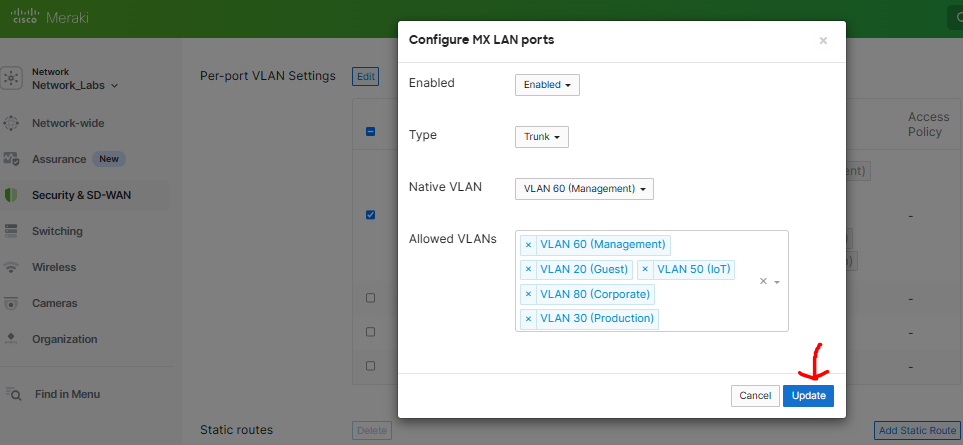
- In this lab scenario, I will designate LAN port '1' as the downstream link towards the MS220 switch in my lab topology
- LAN port '1' will be designated as a trunk link with the allowed VLANs 20,30,50,60 and 80
Network Topology
Enabling and Defining LAN Port 1 with the Port type 'Trunk' & Allowed VLANs
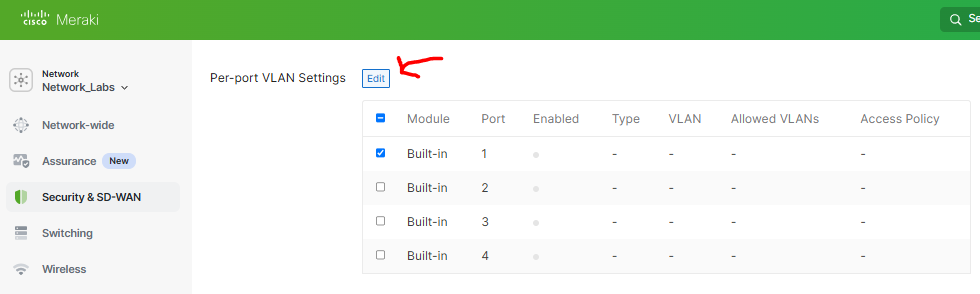
Disabling unused LAN ports as best practice