SSL VPN
Sections:
- SSL VPN Overview
- SSL VPN Configuration
- Windows Sophos Connect Client Install
- IOS OpenVPN Client Install
- Adding a Windows FTP Server
- SSL VPN Full Tunnel Deployment
- (Pending) SSL VPN Certificates
Resources:
- Remote Access SSL VPN Overview
- Configure Remote Access SSL VPN with Sophos Connect Client
- SSL VPN Global Settings
- Add a Remote Access SSL VPN Policy
- VPN Portal
- Sophos Connect Client
- Sophos Connect Client: Compatibility with Platforms
- Configure Remote Access SSL VPN as a Full Tunnel
- Sophos DNS and DNS Host Entries
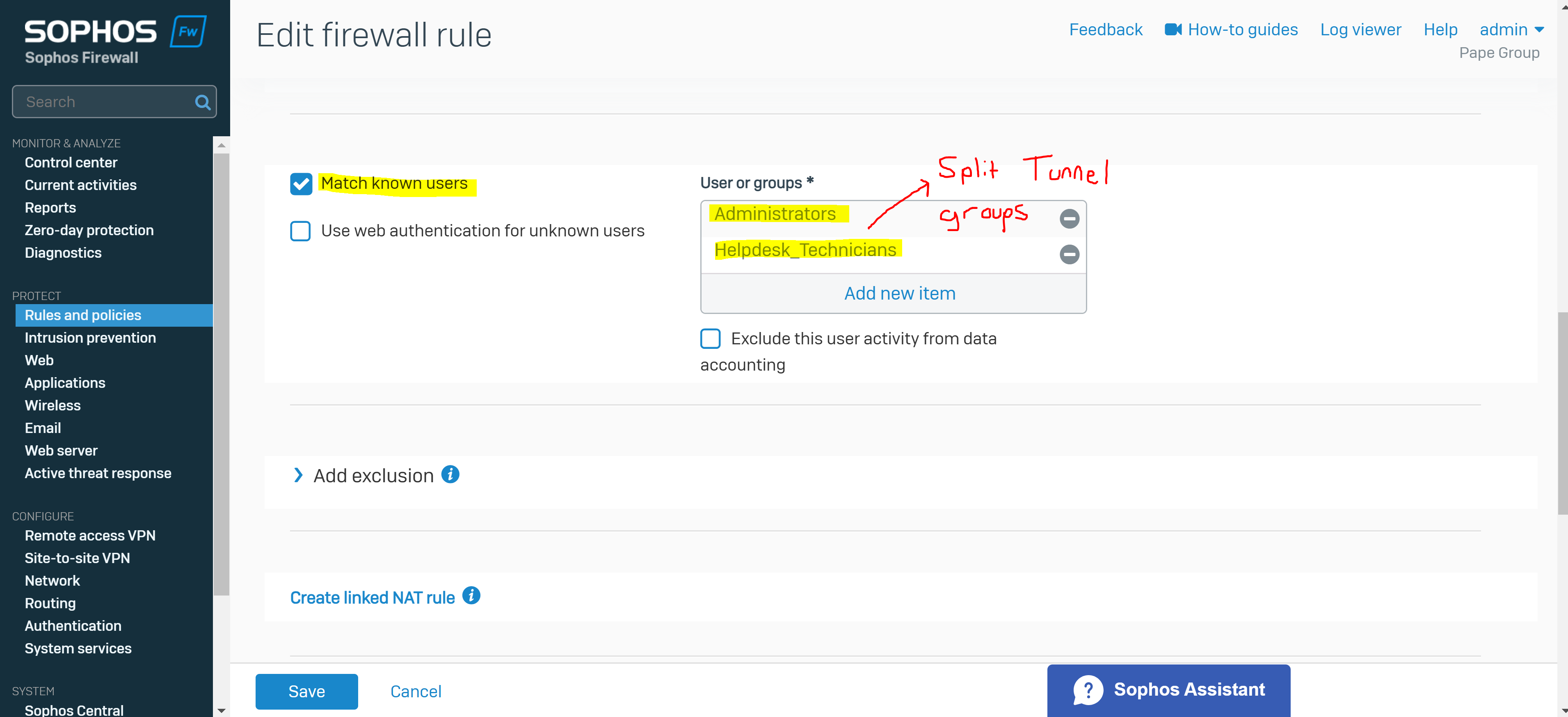
- SSL VPN - Different Groups
- Troubleshoot Remote Access VPN
- Troubleshoot SSL VPN Remote Access Connectivity
Overview:
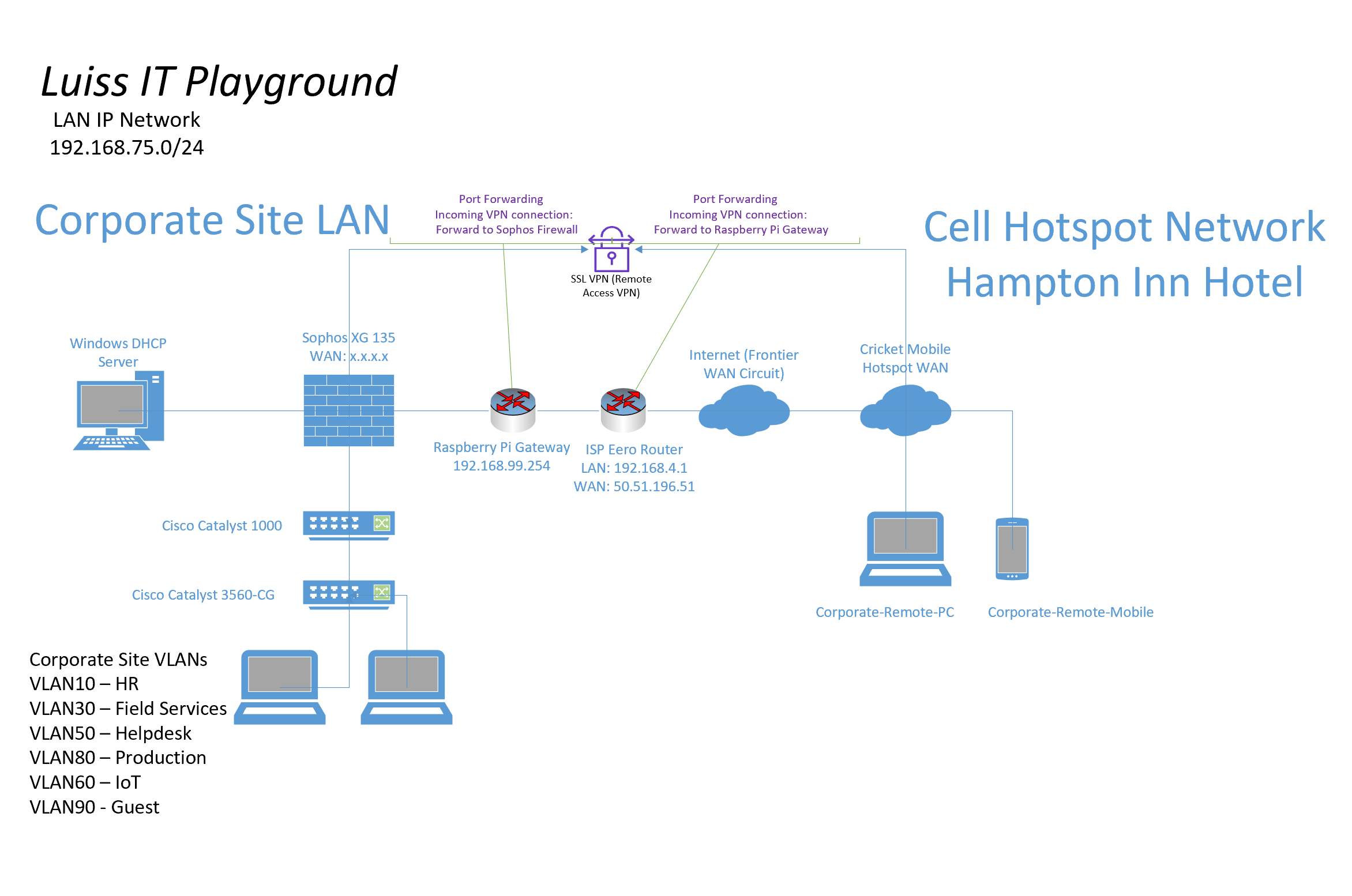
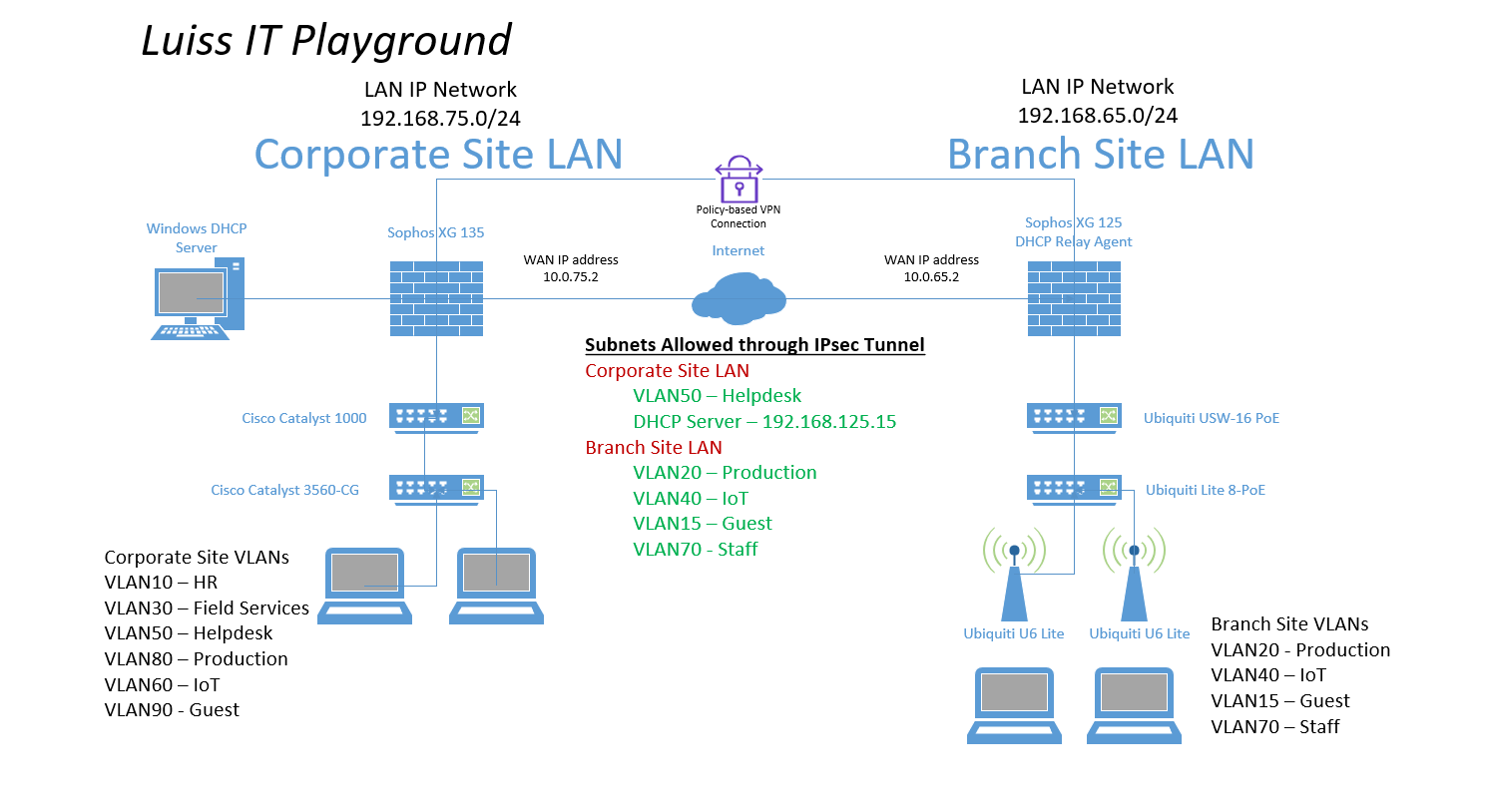
- In this section, I will be setting up a Split-tunnel and Full-tunnel SSL VPN on the Corporate site Sophos Firewall
- You can enable remote users to connect to the Corporate network securely over the Internet using remote access SSL VPN connections
- Users can establish IPv4 and IPv6 SSL VPN connections. These connections use the OpenVPN protocol. Remote access requires digital certificates and a username and password for authentication
- In this lab demonstration, I will follow the steps to configure these SSL VPNs, install the Sophos Connect client for Windows, install a third party OpenVPN client for Apple devices, configure port forwarding rules, and add a Windows FTP server allowing VPN clients to map a network drive to access these internal resources
SSL VPN Fundamentals
Overview
- An SSL VPN (Secure Sockets Layer Virtual Private Network) is a type of VPN that uses SSL (or its successor, TLS) encryption protocols to provide secure remote access to a private network over the Internet
- This type of VPN is commonly used for connecting users to corporate or organizational networks in a secure way
- Key features and components of SSL VPN:
Key Features and Components
Security
- SSL encryption ensures that the data transmitted between the user and the network is secure, preventing unauthorized access or interception
Access Control
- SSL VPNs typically offer granular access control, allowing administrators to specify what parts of the network or resources a user can access
Ease of Use
- SSL VPNs often offer a user-friendly web or VPN software portal where users can simply log in through their device to access network resources
Flexible & Scalable
- SSL VPNs can support remote workers, mobile devices, and business partners easily, making them flexible for different access needs
How SSL VPN Works
Authentication
- The user connects to the SSL VPN portal using a web browser or a specialized SSL VPN client
- The connection is initiated by navigating to the SSL VPN server's URL (for instance, 'https://vpn.example.com'), where the server's SSL certificate is presented to the user's browser to establish trust
- The user is prompted for login credentials (username/password, two-factor authentication, or other methods) to verify their identity
Establishing an SSL/TLS Tunnel
- After the user successfully authenticates, the SSL VPN server establishes an encrypted SSL/TLS tunnel between the user's device and the server
- SSL/TLS protocols ensure that the data transmitted between the client and the server is encrypted, preventing eavesdropping or tampering by third parties
Data Encryption & Communication
- Once the SSL/TLS tunnel is established, all data exchanged between the client and the VPN server is encrypted
- This tunnel essentially creates a secure 'pipe' for communication, even if the user is on a public network (Wi-Fi at a coffee shop, etc.)
Access to Internal Resources
- Depending on the configuration of the SSL VPN, users can access specific resources like intranet websites, email servers, or even remote desktop connections
- Some SSL VPNs provide access via a web interface, where users can interact with internal resources via their browser. Others might offer a full-fledged VPN client for accessing network resources as if the user were physically on the internal network
End of Session
- Once the user is done with their session, they log out, and the encrypted SSL/TLS tunnel is closed, terminating the secure connection
- The server may also have session timeouts or idle timeouts to automatically disconnect users after a period of inactivity
Benefits of SSL VPN
Ease of Setup & Configuration
- Configuration is generally simpler for both administrators and users
- Setup only requires a standard web browser for access, or a specialized VPN software client for gaining access to the corporate network
Better Compatibility with Web Applications
- SSL VPNs are particularly well-suited for accessing web-based applications (such as email, file shares, or internal websites) because they use standard web protocols (HTTP/HTTPS) to encrypt traffic
- This allows users to access resources via a web portal without needing to configure access for each individual application
Flexibility for Different Devices
- SSL VPNs work across a wide range of devices, including desktops, laptops, and mobile devices
- Users only need a browser or VPN client to connect, and there's less dependency on specific operating systems or device configurations
Network Address Translation (NAT) Traversal
- SSL VPNs typically have better support for NAT traversal (the ability to work through firewalls and routers that perform network address translation)
- Because SSL VPNs use HTTPS, they can bypass many of the restrictions that might block IPsec traffic on certain networks (such as public Wi-Fi networks)
Granular Access Control
- SSL VPNs allow for more granular access control, particularly in terms of determining what applications or resources a user can access once connected
- Administrators can configure role-based access to ensure users can only see the resources they are authorized to access
Scalability for Remote or Mobile Workers
- SSL VPNs are highly scalable for large numbers of remote or mobile users that need access to internal resources
Potential Drawbacks
Limited Network Access (Compared to IPsec VPN)
- SSL VPNs are often designed for access to specific resources (web-based applications, files, etc.) rather than full network access
- If a user needs broader access to an entire internal network, an IPsec VPN or other types of VPN might be more appropriate
- IPsec VPNs are typically preferred for connecting multiple office locations in a secure and reliable manner, especially when handling large amounts of data traffic between sites
Performance and Speed Limitations
- SSL VPNs can introduce additional latency in comparison to IPsec VPNs, especially when used over long-distance or high-latency public networks
- SSL VPNs involve extra overhead due to encryption and the use of HTTPS (which might not be optimized for VPN traffic)
Security Concerns (If Misconfigured)
- SSL VPNs rely on a web-based portal for access, which means vulnerabilities in the portal or web server can become potential entry points for attackers (if not properly secured (with strong encryption, multi-factor authentication, etc.), these portals could be a target)
Scalability Concerns for Large User Groups
- For very large organizations with thousands of concurrent users, SSL VPN solutions can become resource-intensive
- Since each user typically establishes a separate secure connection, the SSL VPN gateway might face performance bottlenecks or resource limits under heavy traffic conditions
SSL VPN Configuration
Overview
- For the Corporate site LAN, I will demonstrate configuring a Split-tunnel remote access VPN (SSL VPN) on the Sophos Firewall
- Sophos Firewall gives administrators the ability to define users centrally on the Sophos Firewall to establish the VPN connection via endpoint devices using the Sophos Connect client
- Optionally, you can select and define an external authentication server, such as Active Directory for user authentication
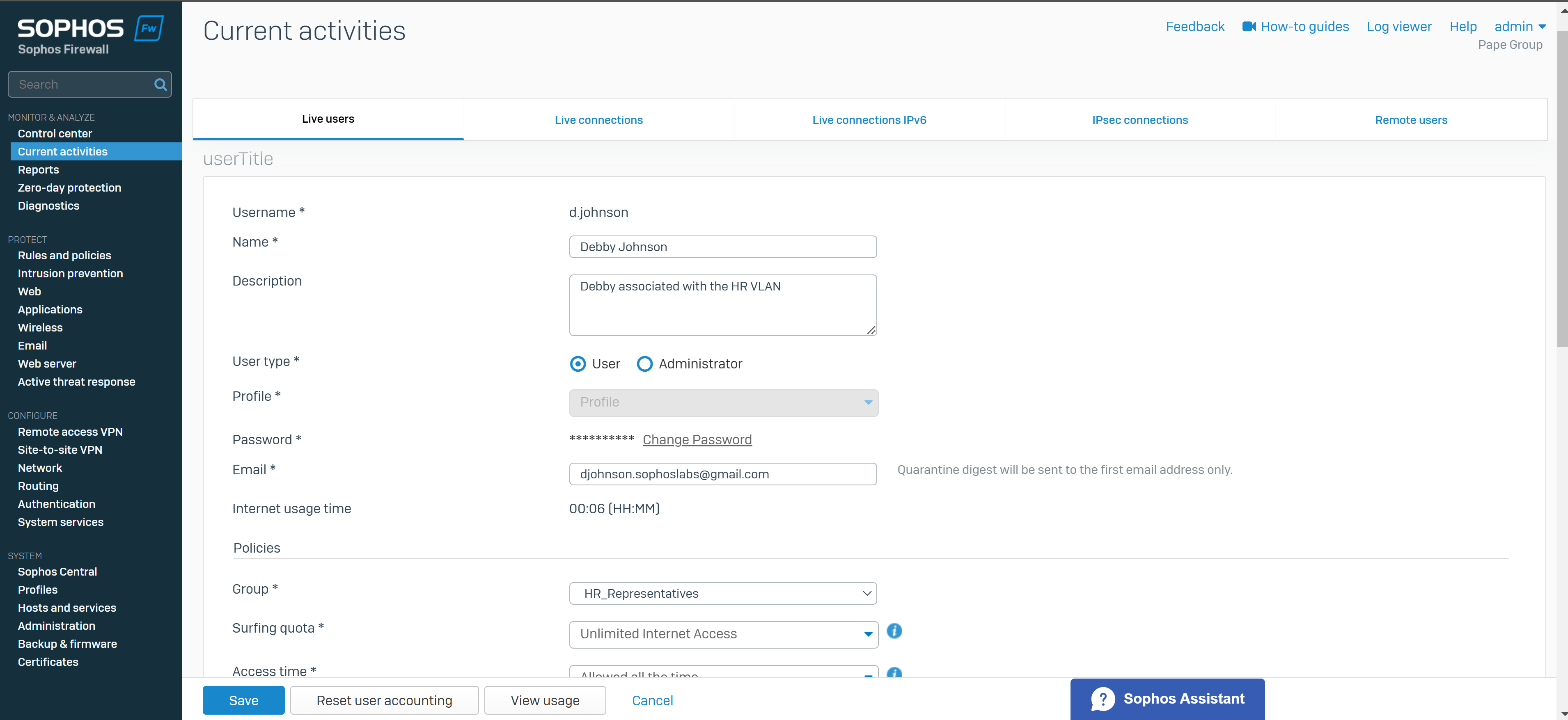
- In this demonstration, I will be creating local users on the Sophos Firewall for Remote SSL VPN (Sophos Firewall acting as the authentication server)
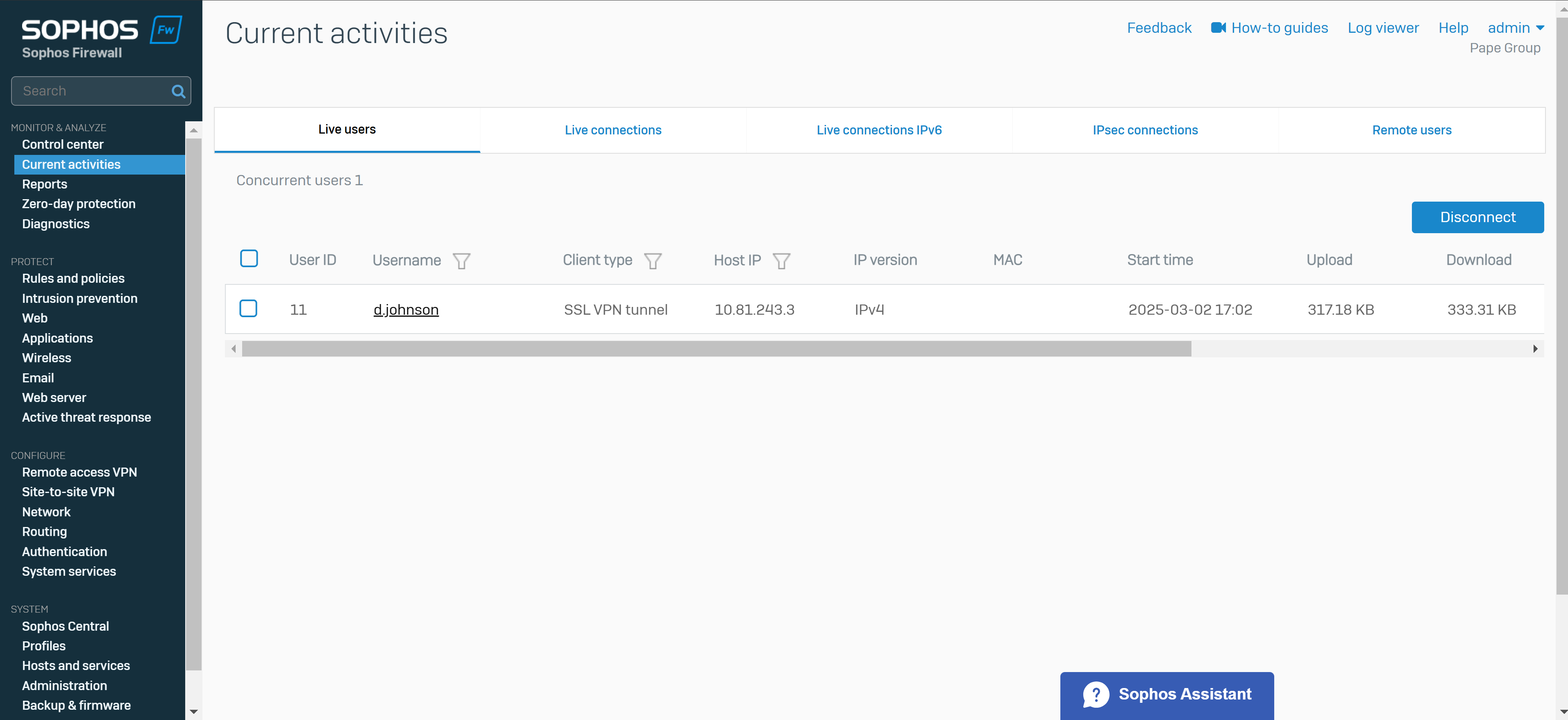
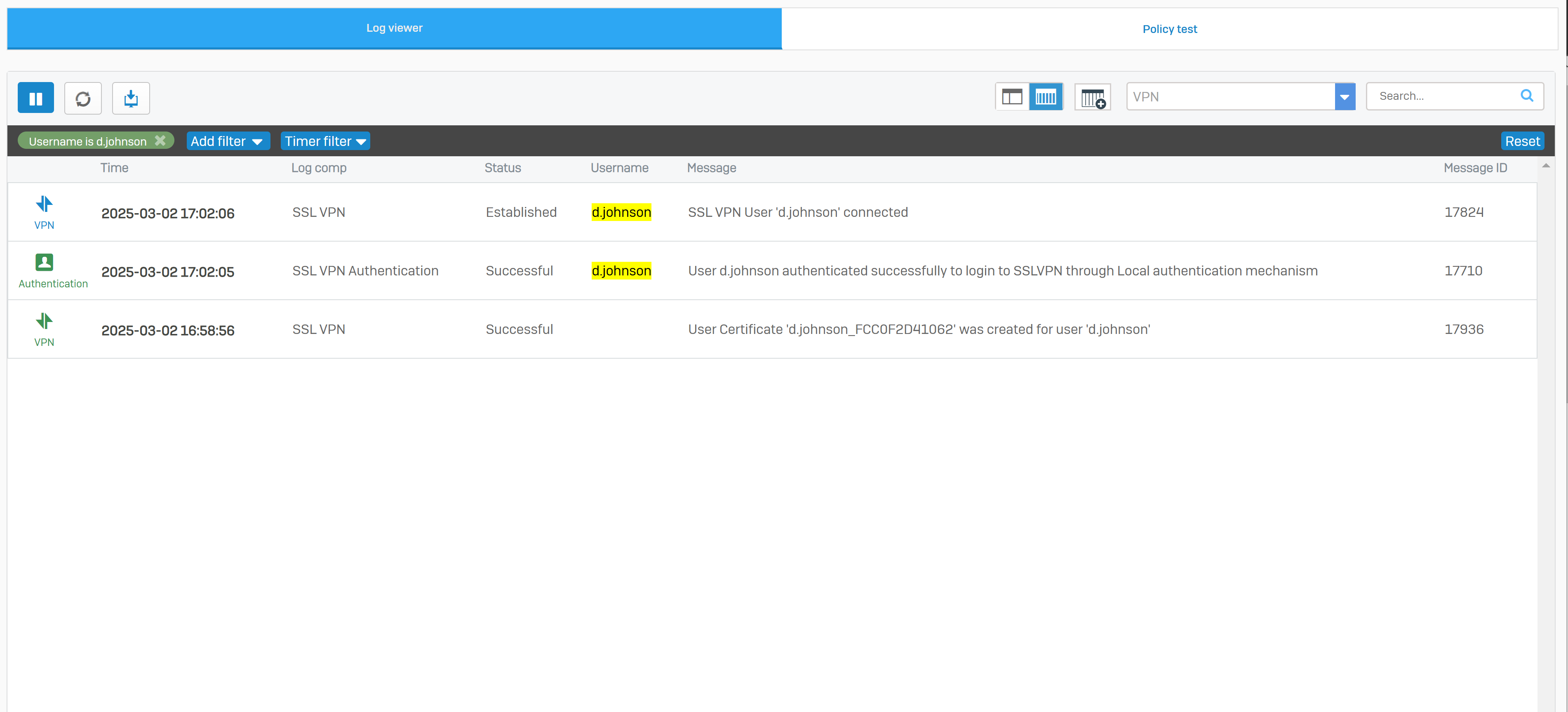
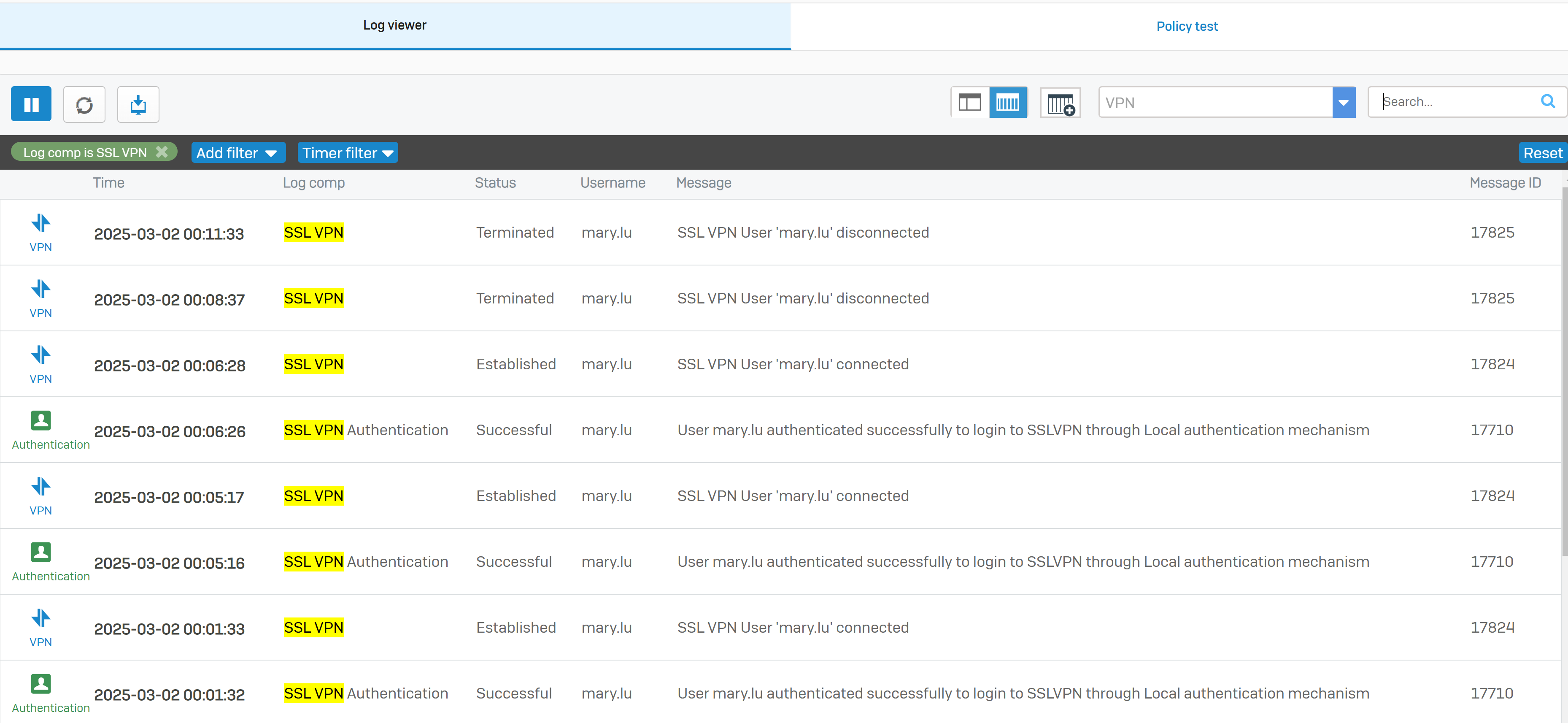
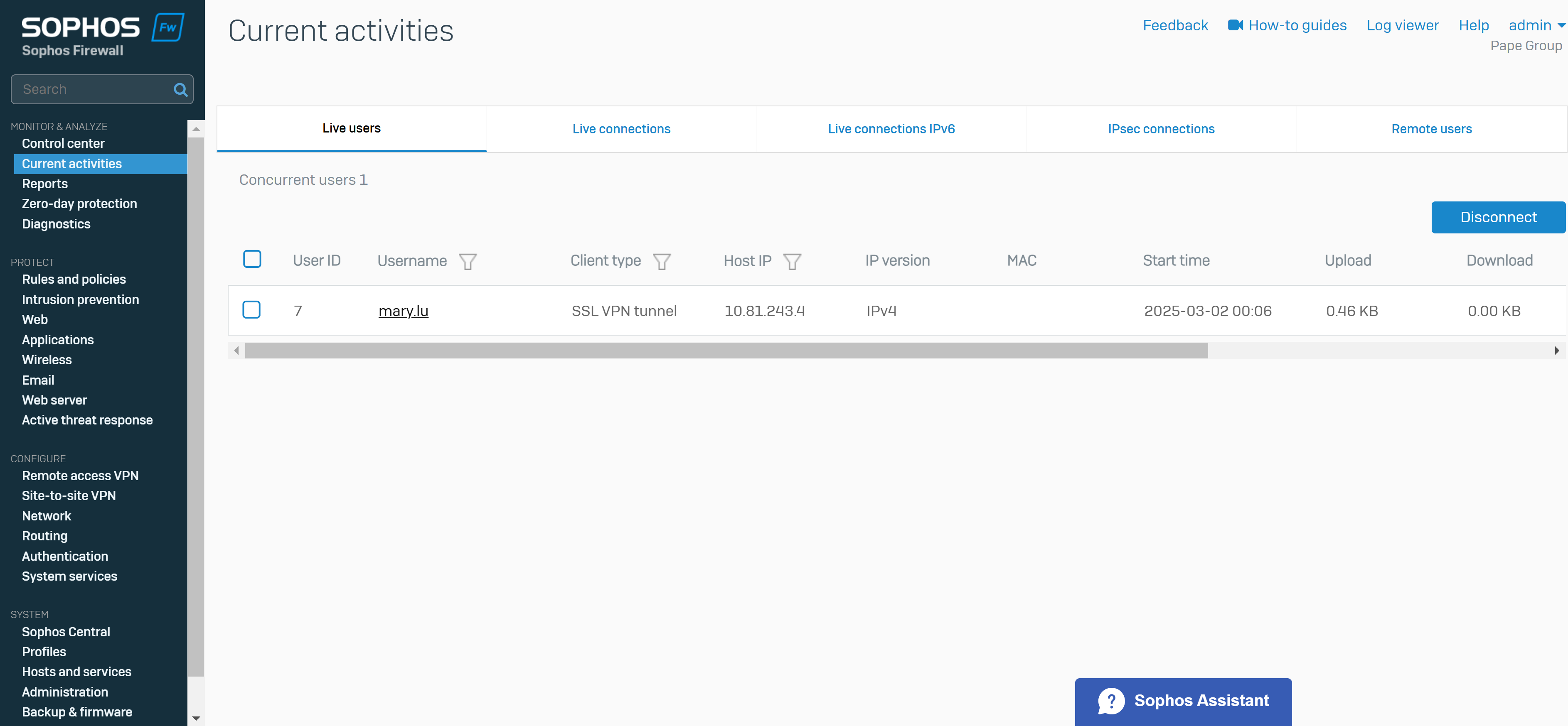
- Upon successfully configuring a remote access SSL VPN on the Corporate site Sophos Firewall, I will test and verify users are able to connect to internal resources on the Corporate LAN when connecting to the SSL VPN
Sophos Connect Client
- The Sophos Connect client allows you to enforce advanced security and flexibility settings, such as connecting the tunnel automatically
- Preliminary Configurations:
- Configure IP hosts for the local subnets
- Configure users and groups. Alternatively, configure an authentication server
- Check the authentication methods
- Post Configurations:
- Configure the SSL VPN settings
- Send the configuration file to users
- Add a firewall rule
- Send the Sophos Connect client to users. Alternatively, users can download it from the User or VPN portal
- Import the configuration file into the client and establish connection
- Restrictions
- Currently, the Sophos Connect client doesn't support Apple IOS or Android for SSLVPN
- It also doesn't support other mobile platforms for IPsec and SSL VPN
- For these endpoints, you can use the any third party OpenVPN clients
- Connect client: Compatibility with platforms
SSL VPN Topology
Create an IP Host for Local Subnet
Overview
- Reference: Hosts and Services (IP host)
- The local subnet defines the network resources that remote clients can access
- These IP host groups will eventually be added to firewall rules to ensure VPN clients can only access those internal hosts or networks
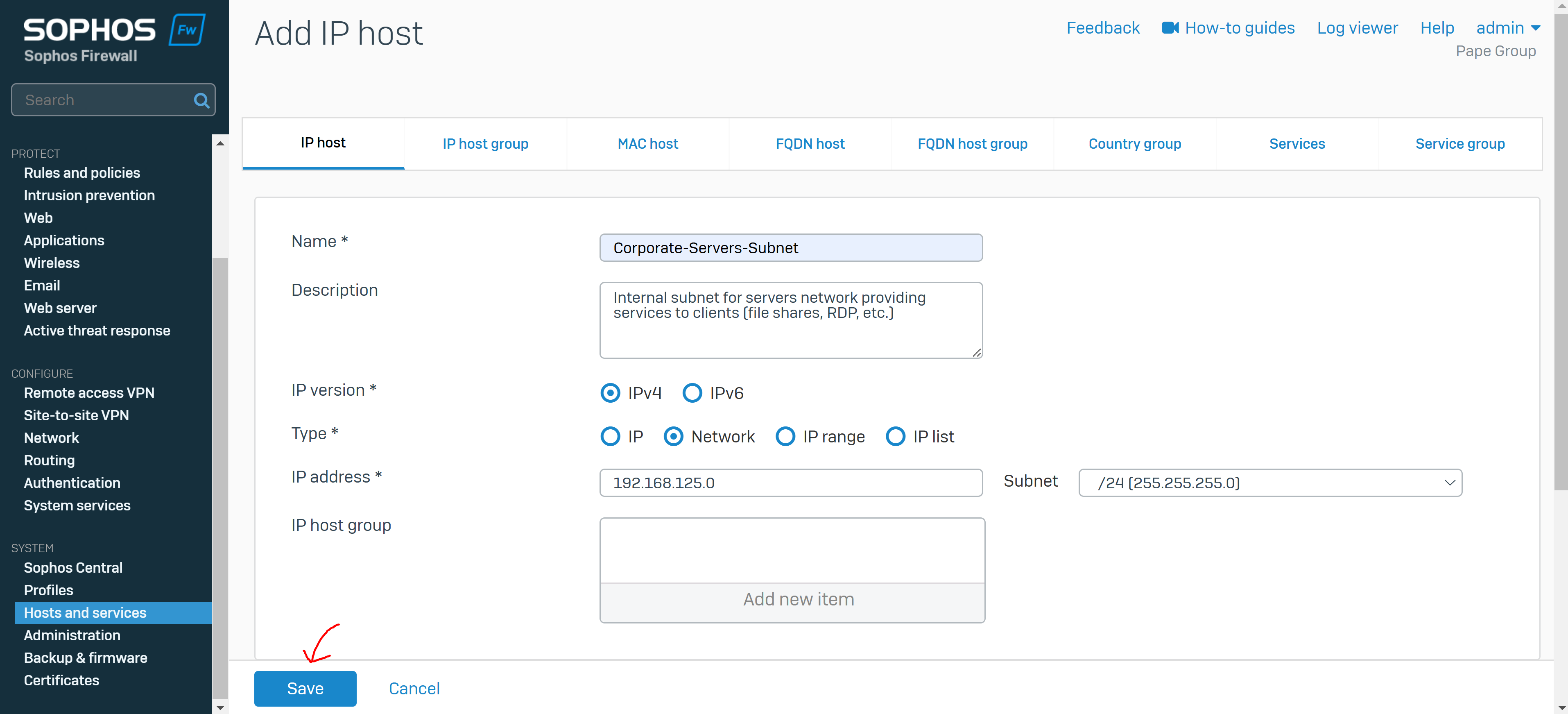
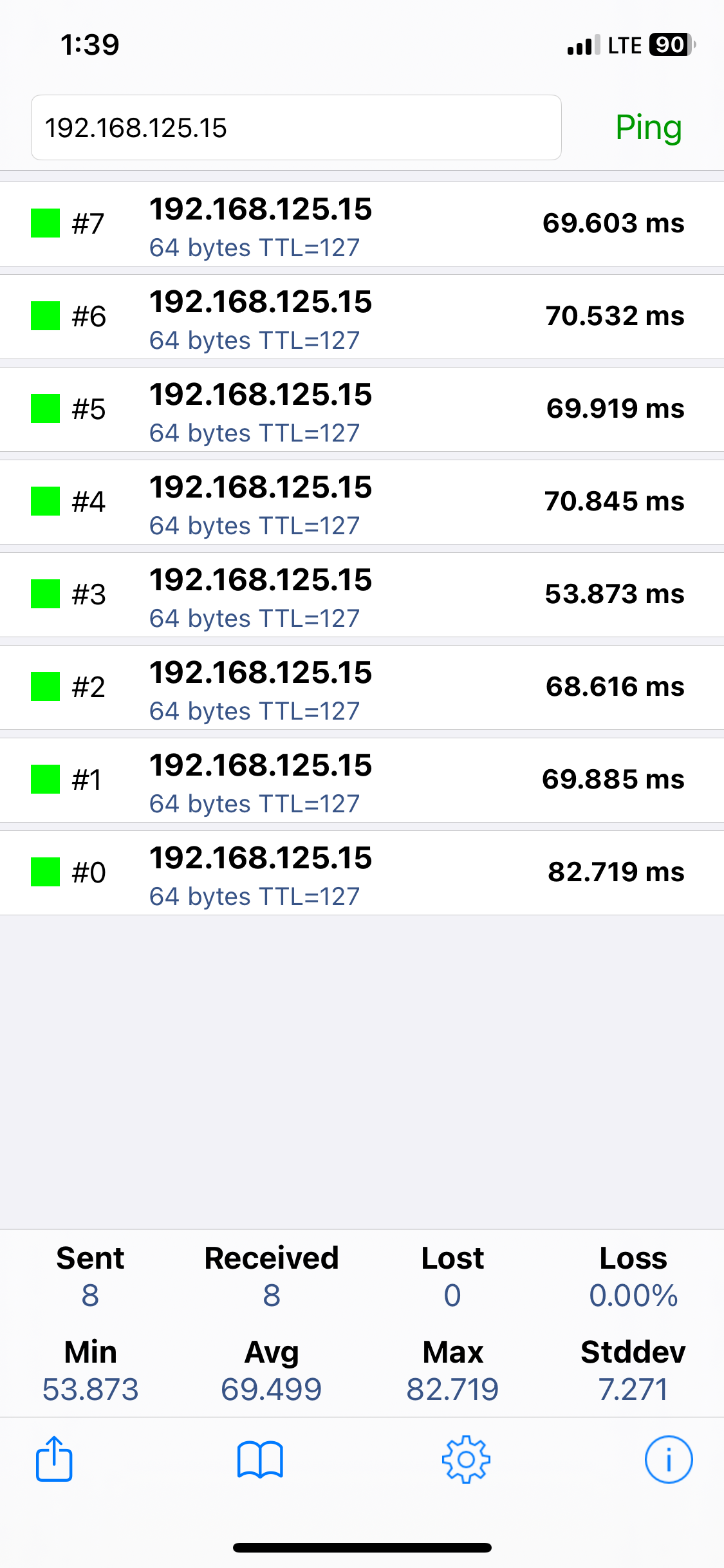
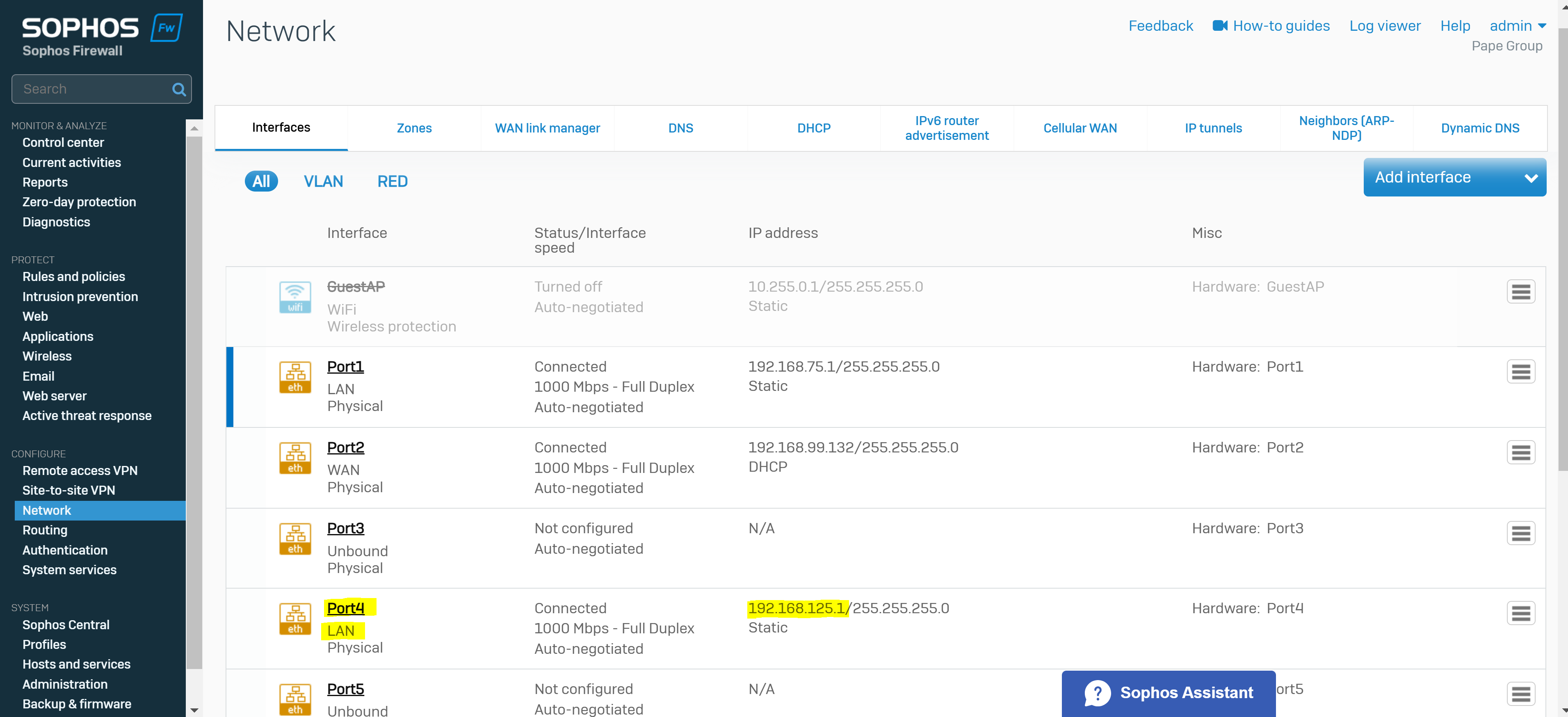
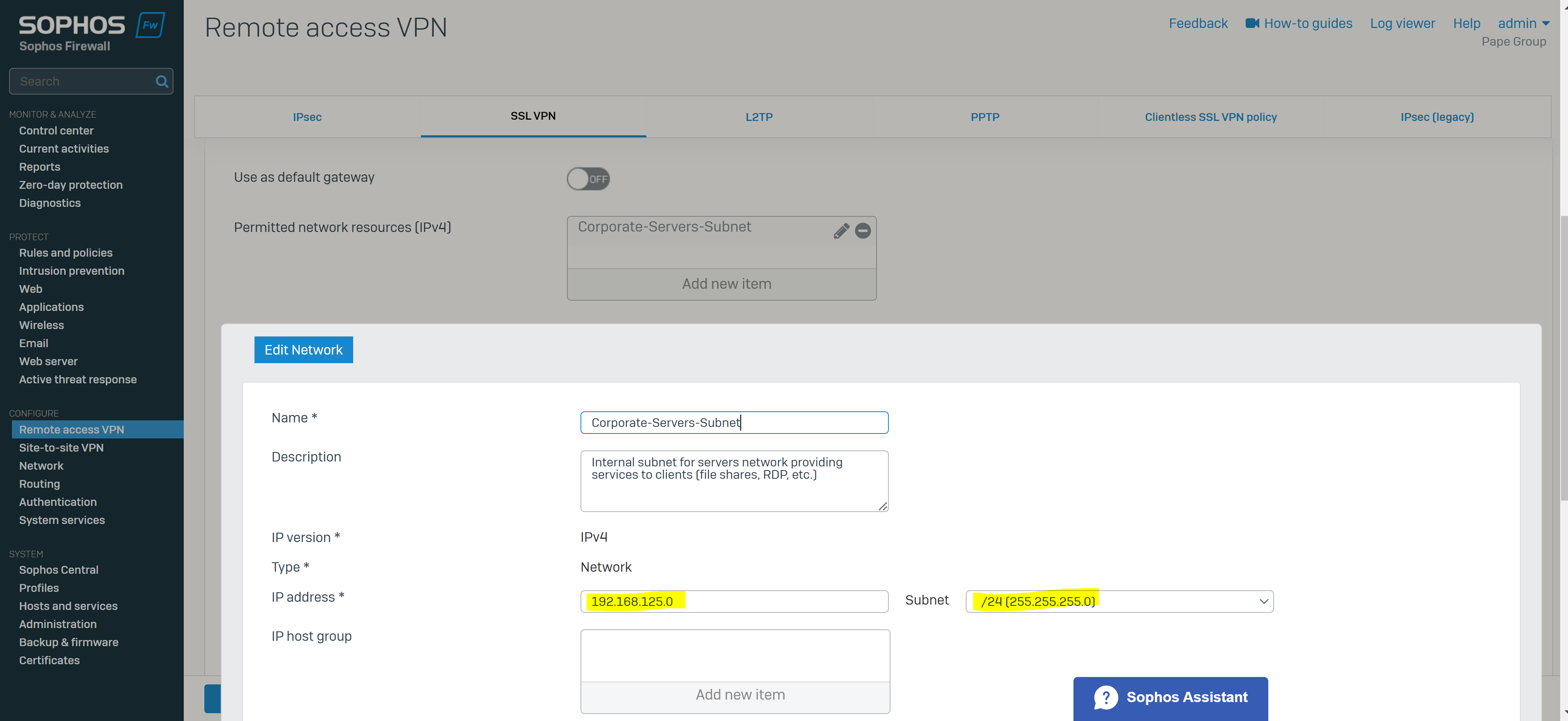
- If VPN clients will be utilizing an internal DNS server, ensure it it covered as a host or within a group
- In this demonstration, I will be grouping the internal servers network into a IP host that includes the Sophos Firewall interface IP address for the servers LAN (192.168.125.1) that will later be used as a DNS server for VPN clients
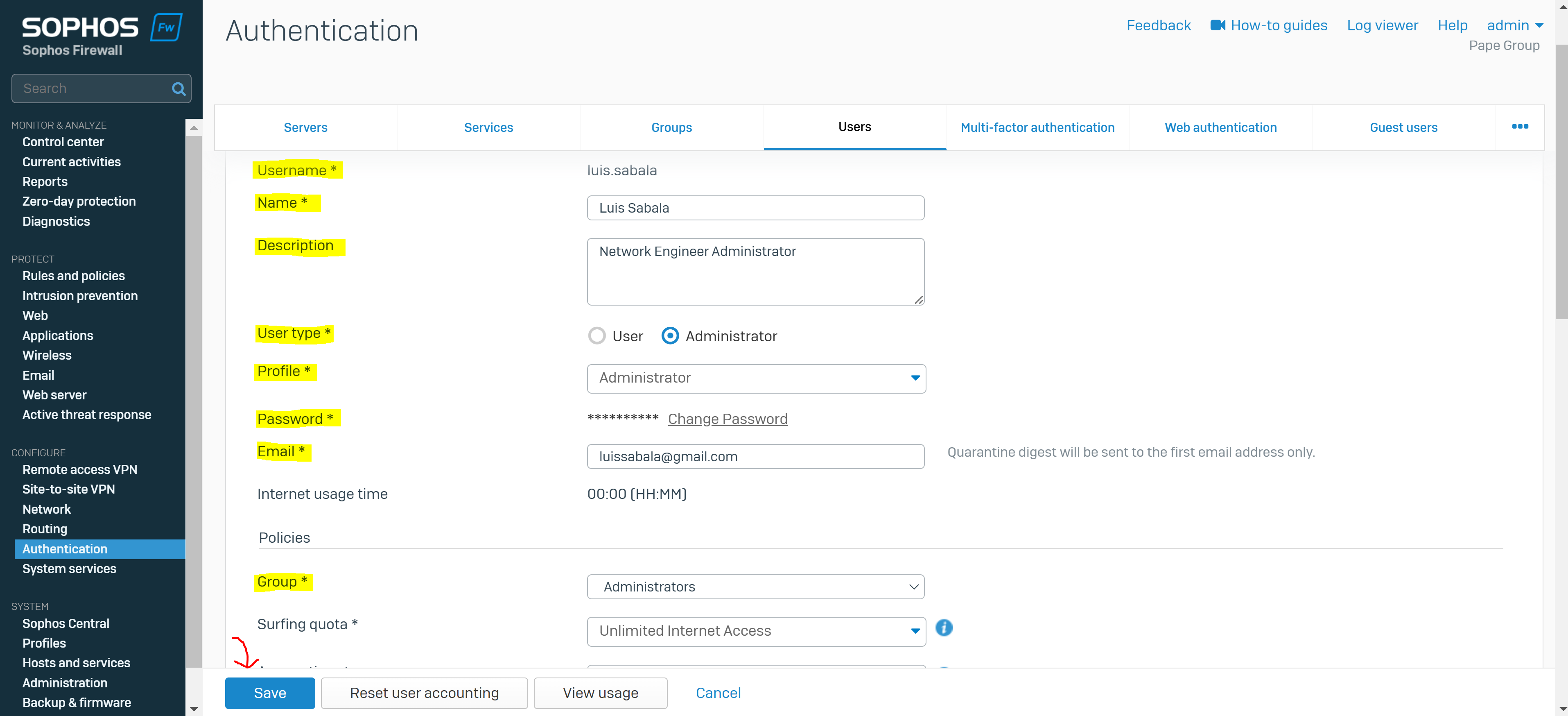
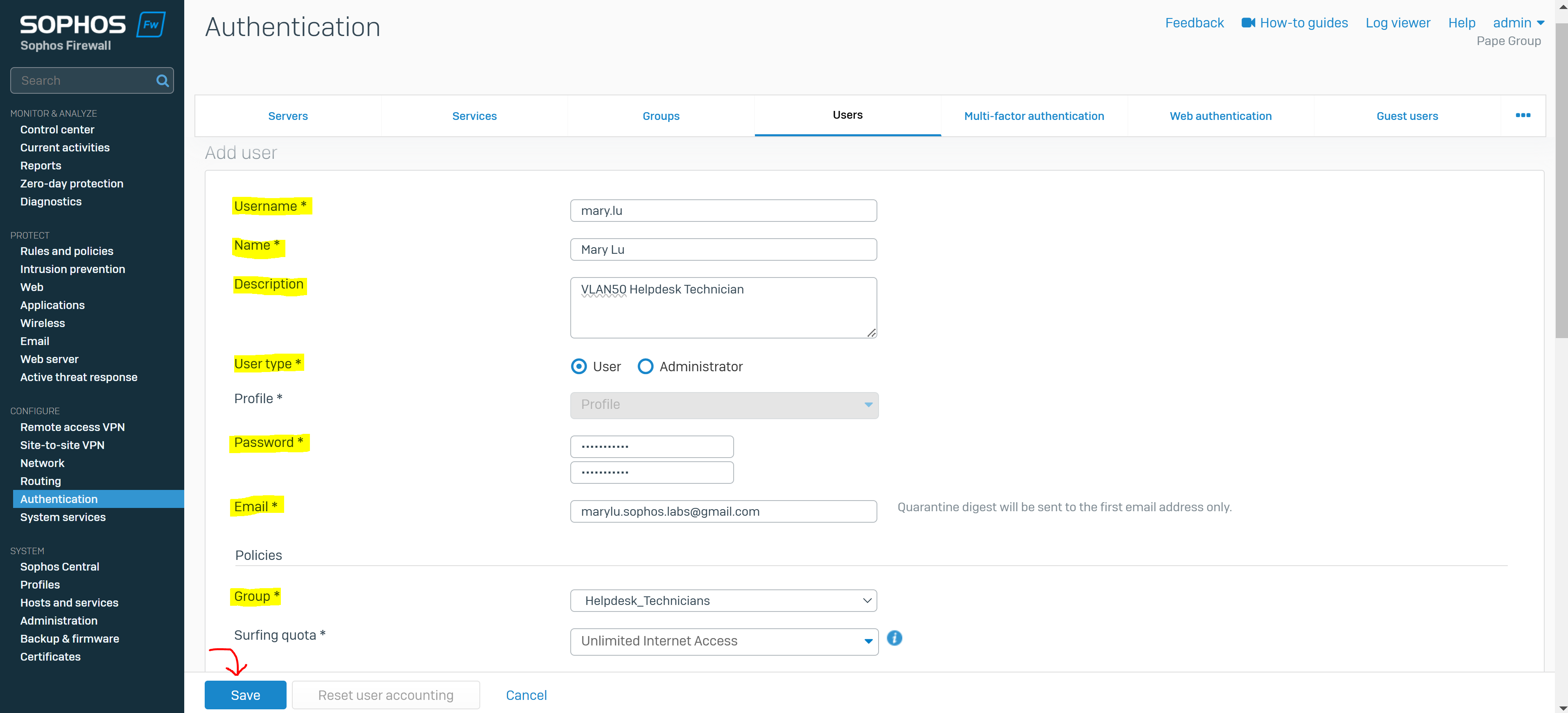
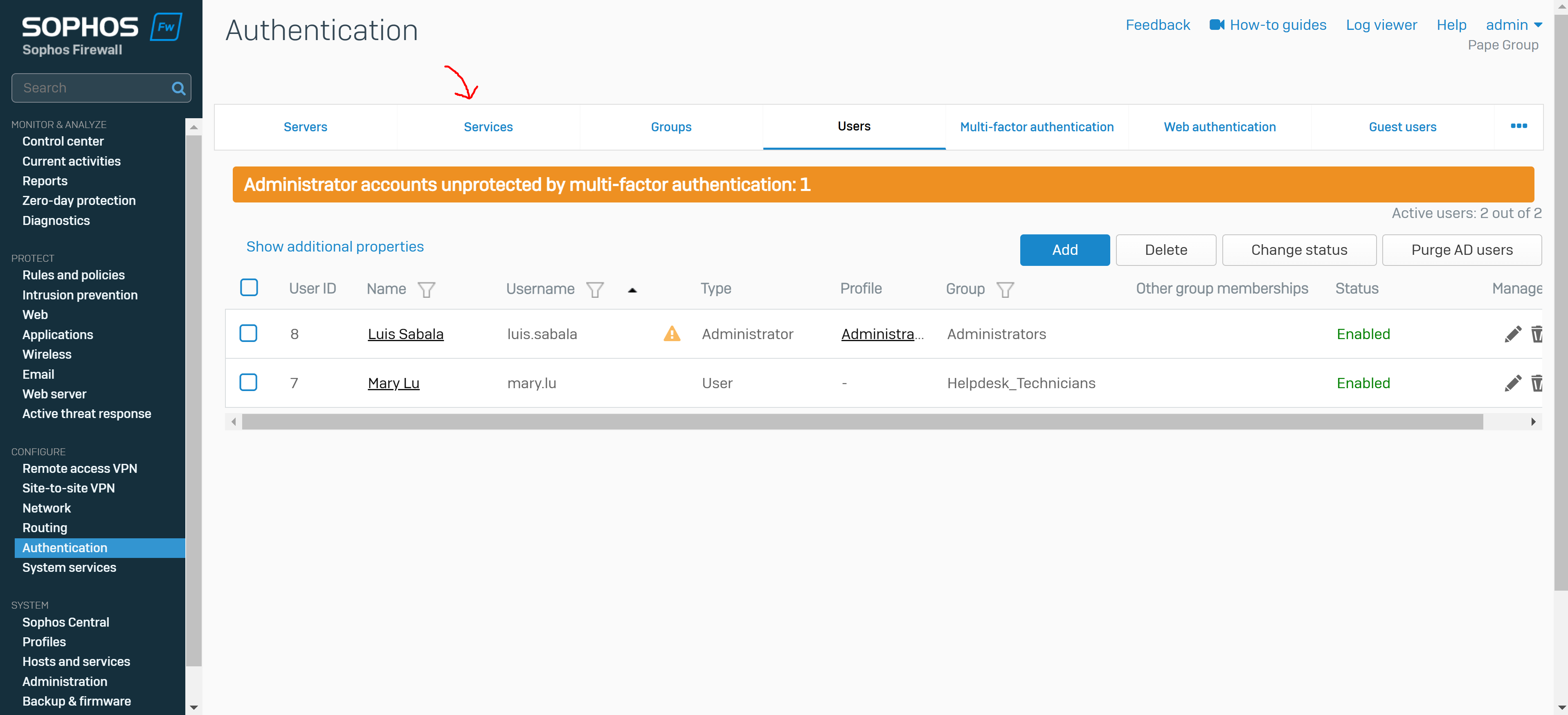
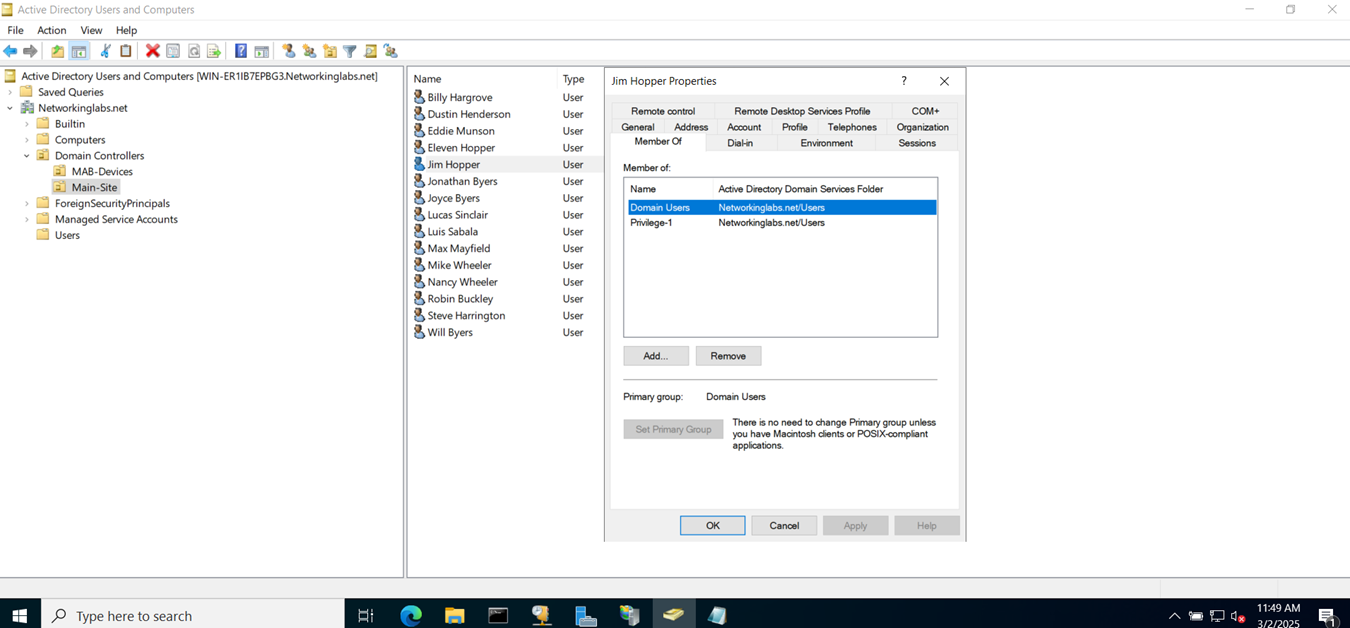
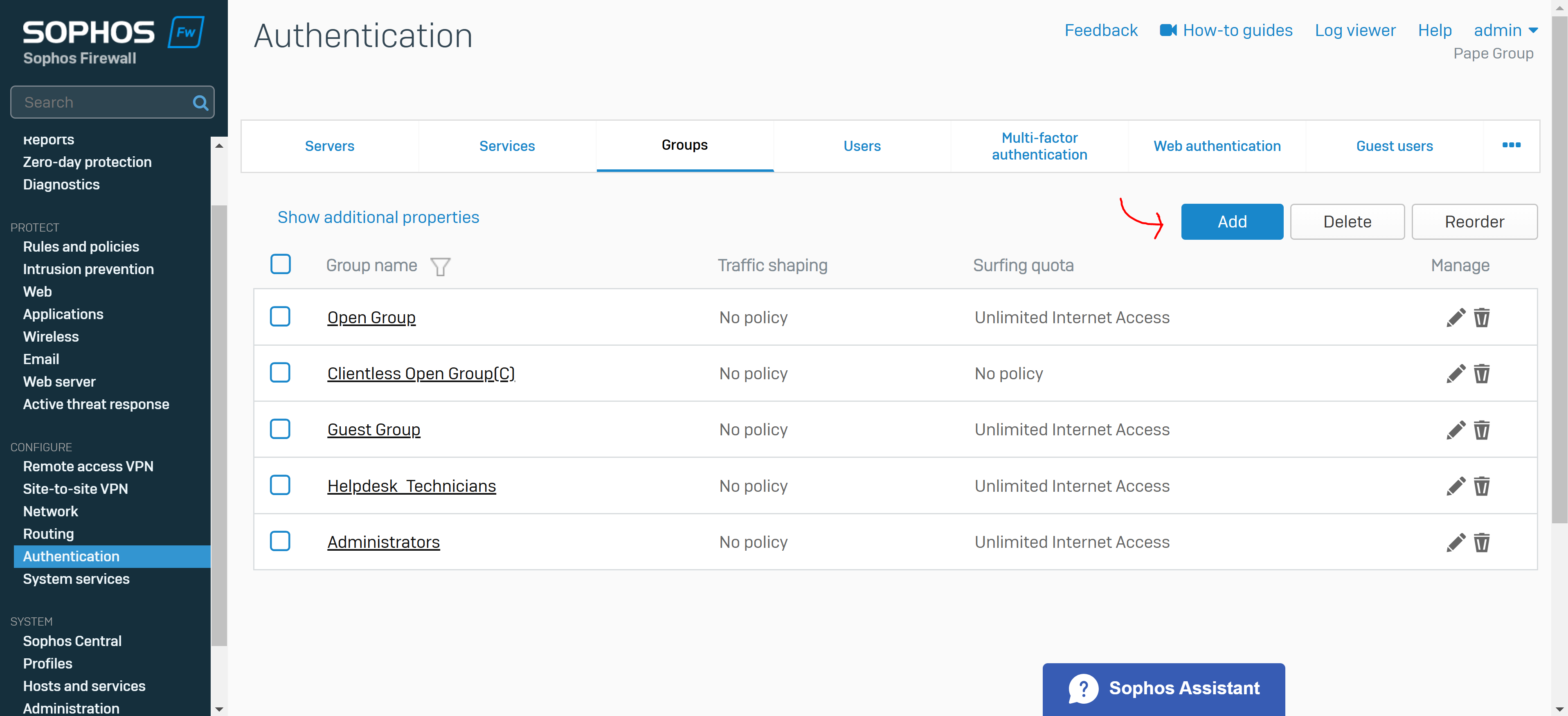
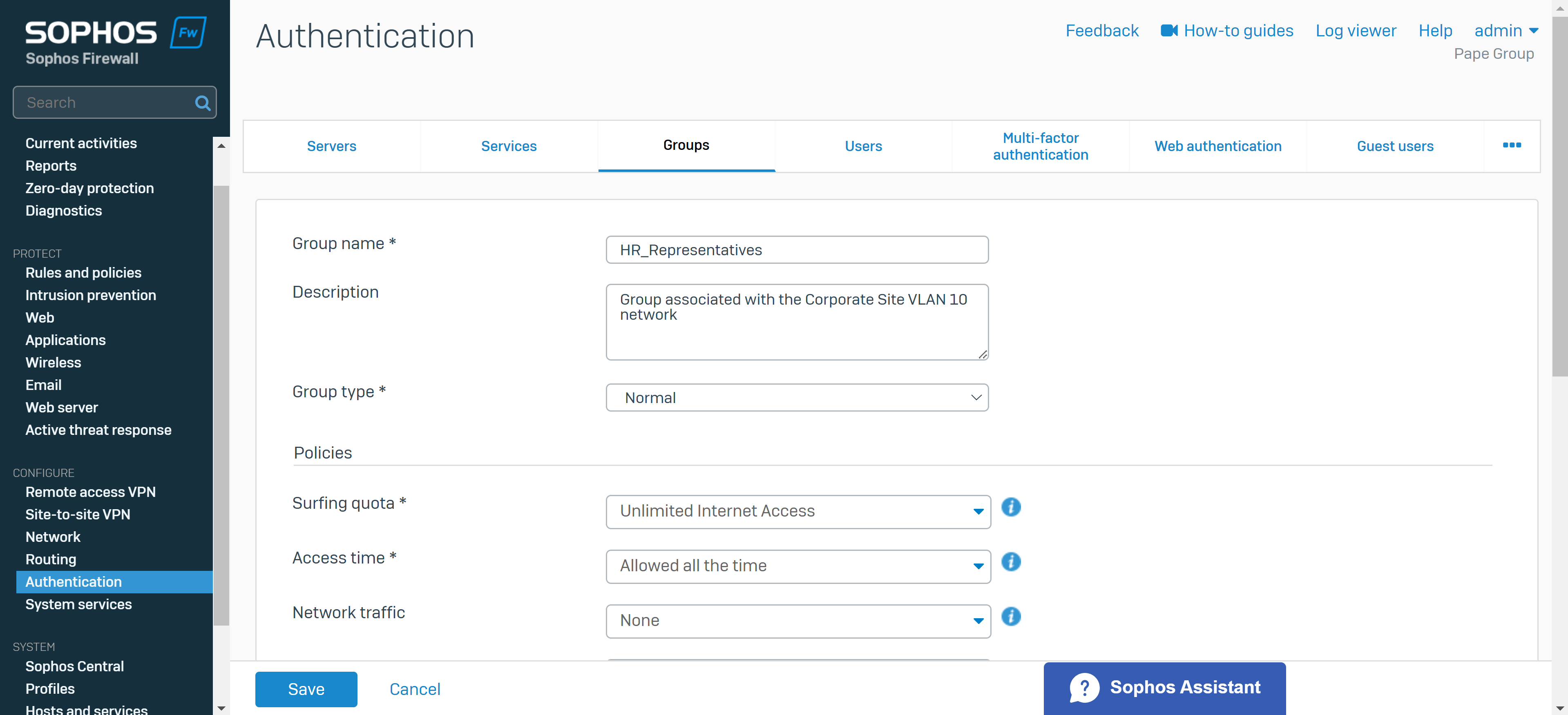
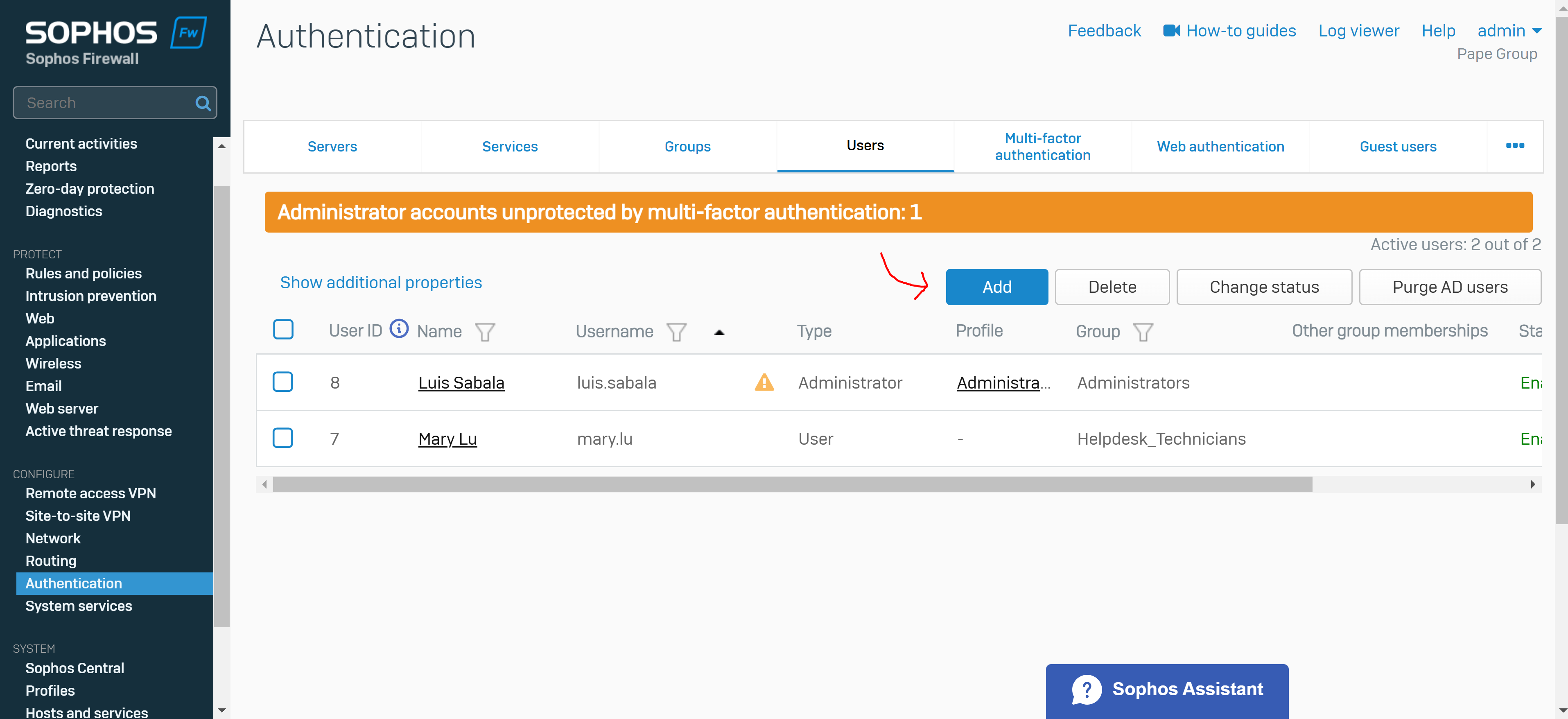
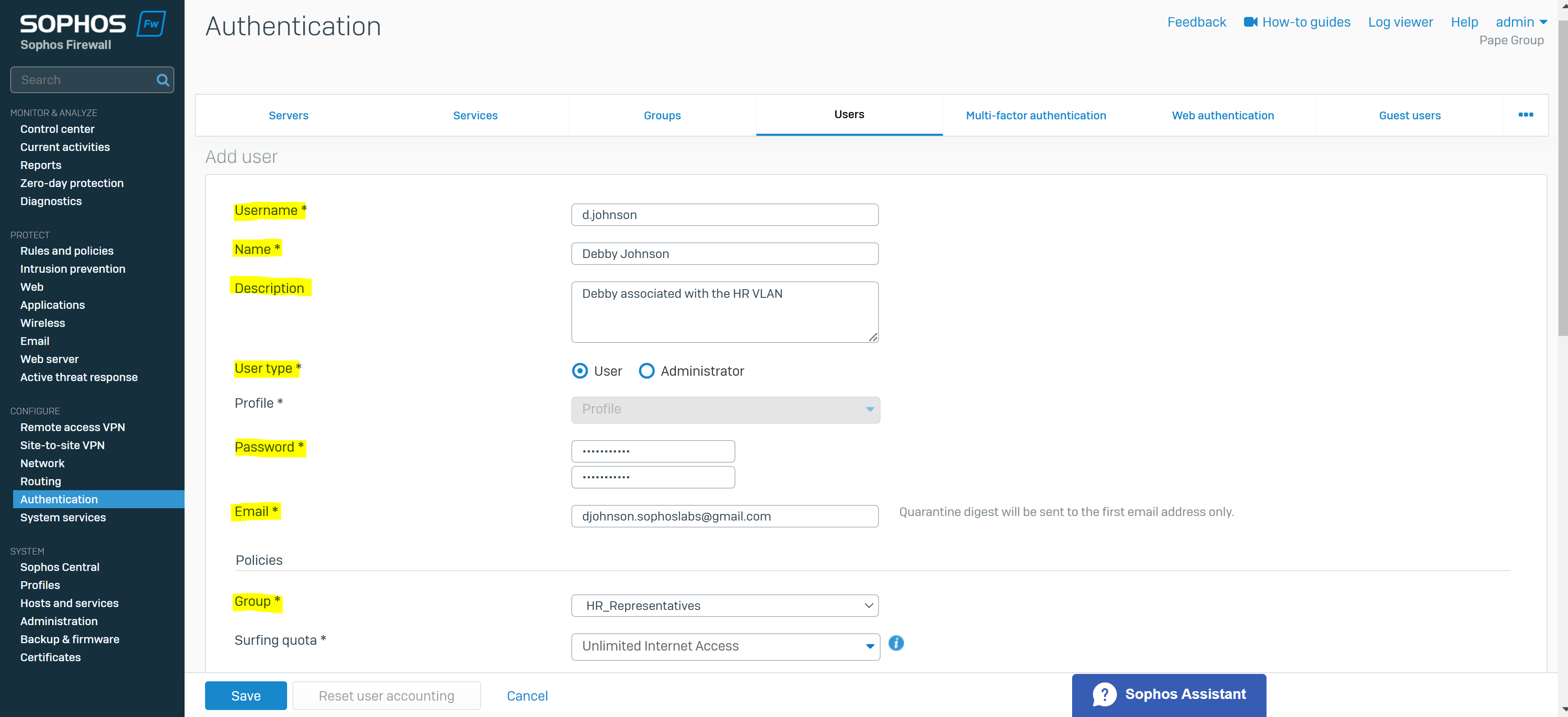
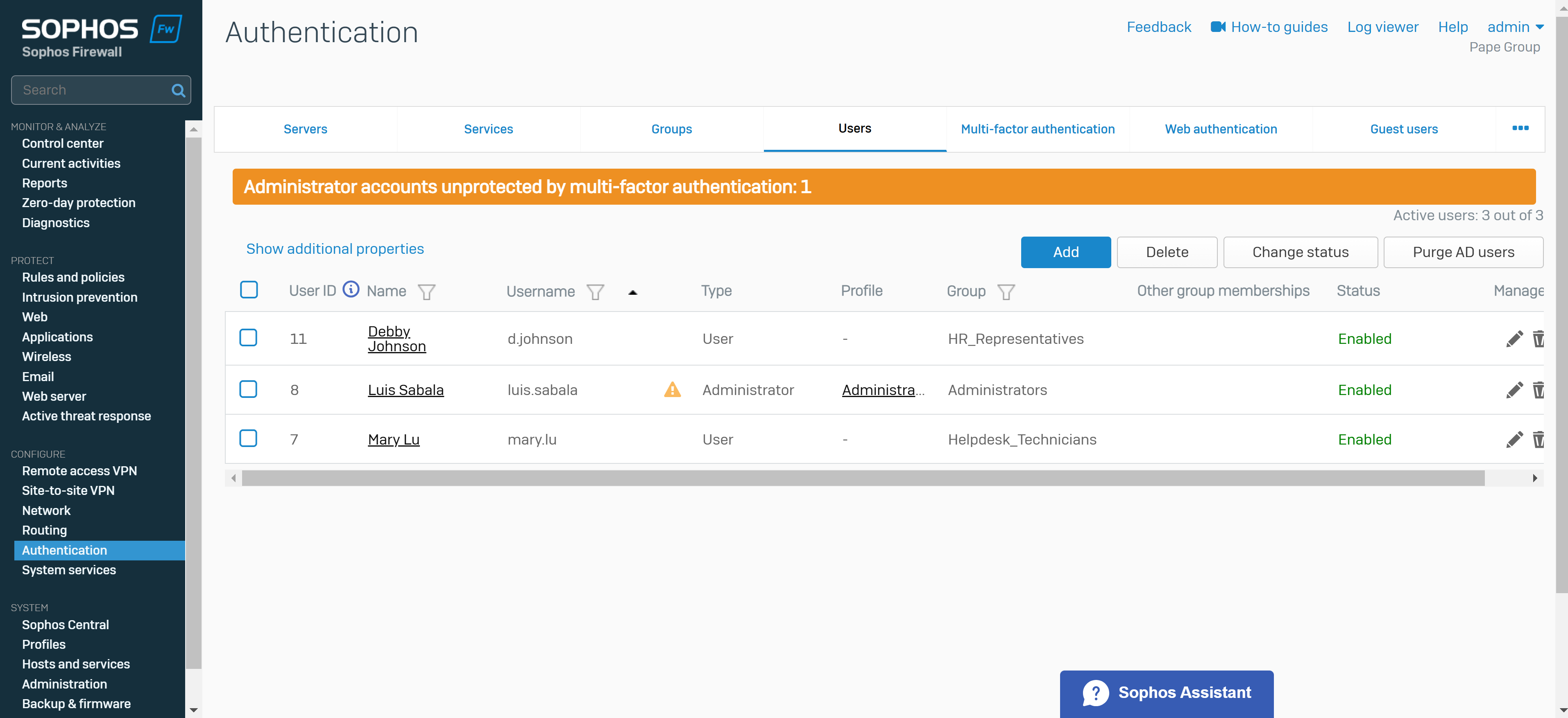
Create a User Group & Add Users
Overview
- Reference: Groups
- Reference: Users
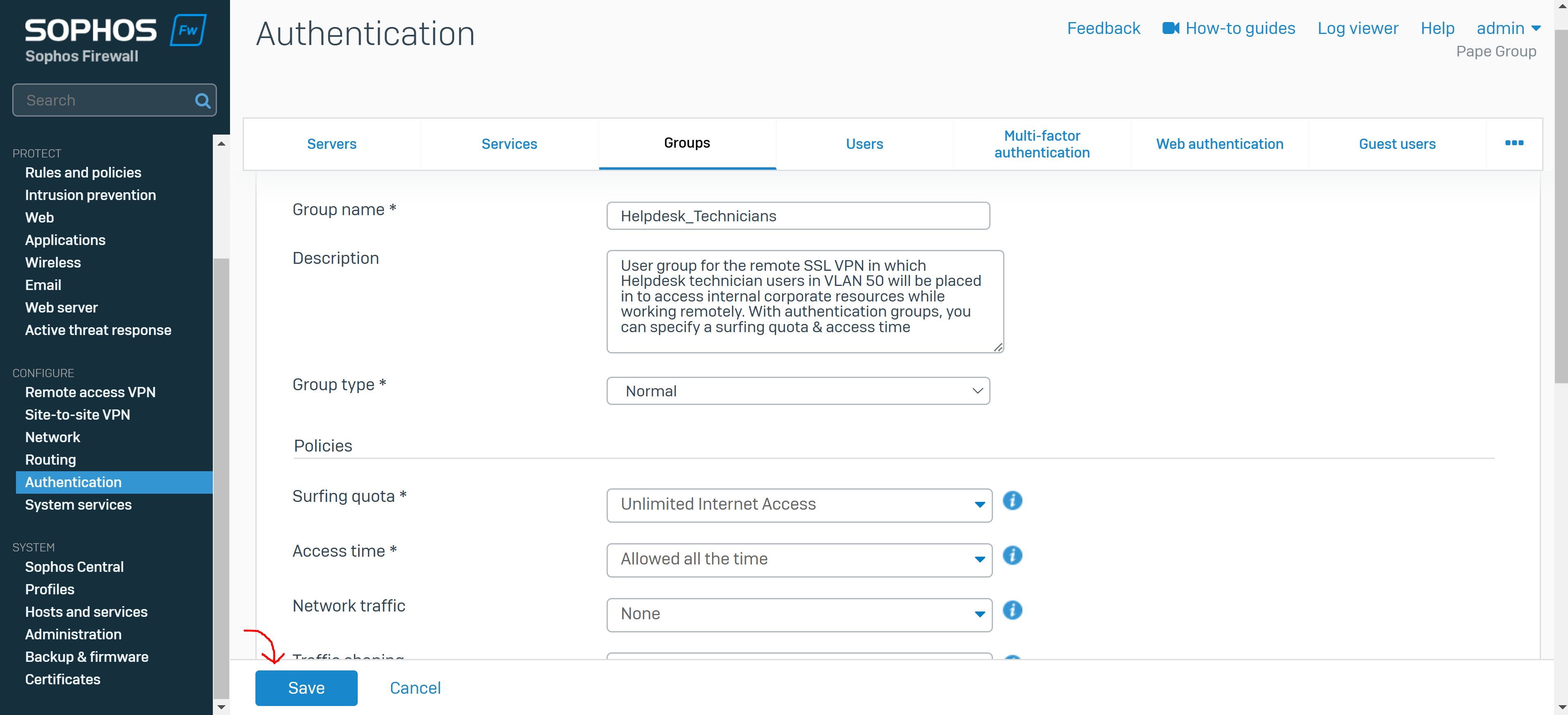
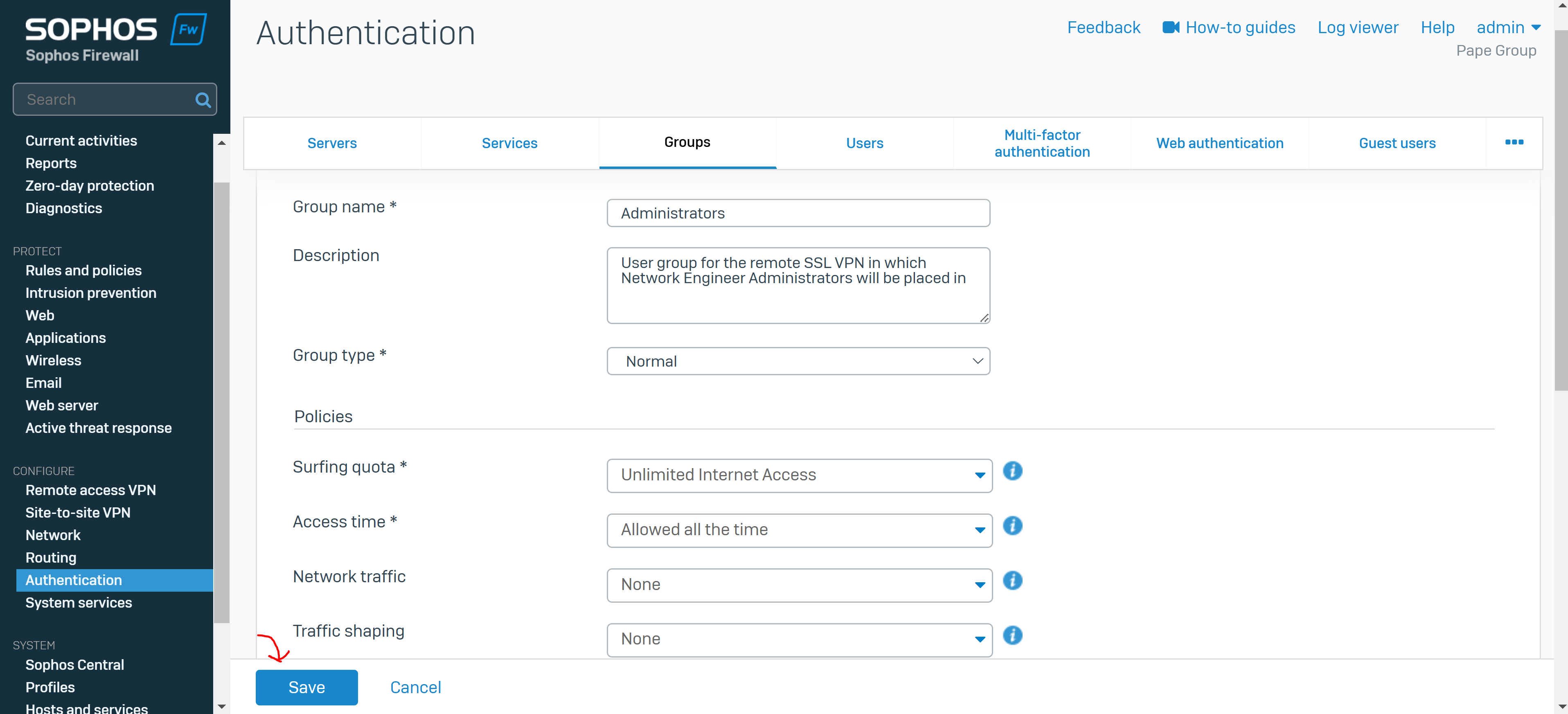
- You create a user group for the remote SSL VPN policy and add user(s)
- The group specifies a surfing quota and access time that can be adjusted based on the group permissions
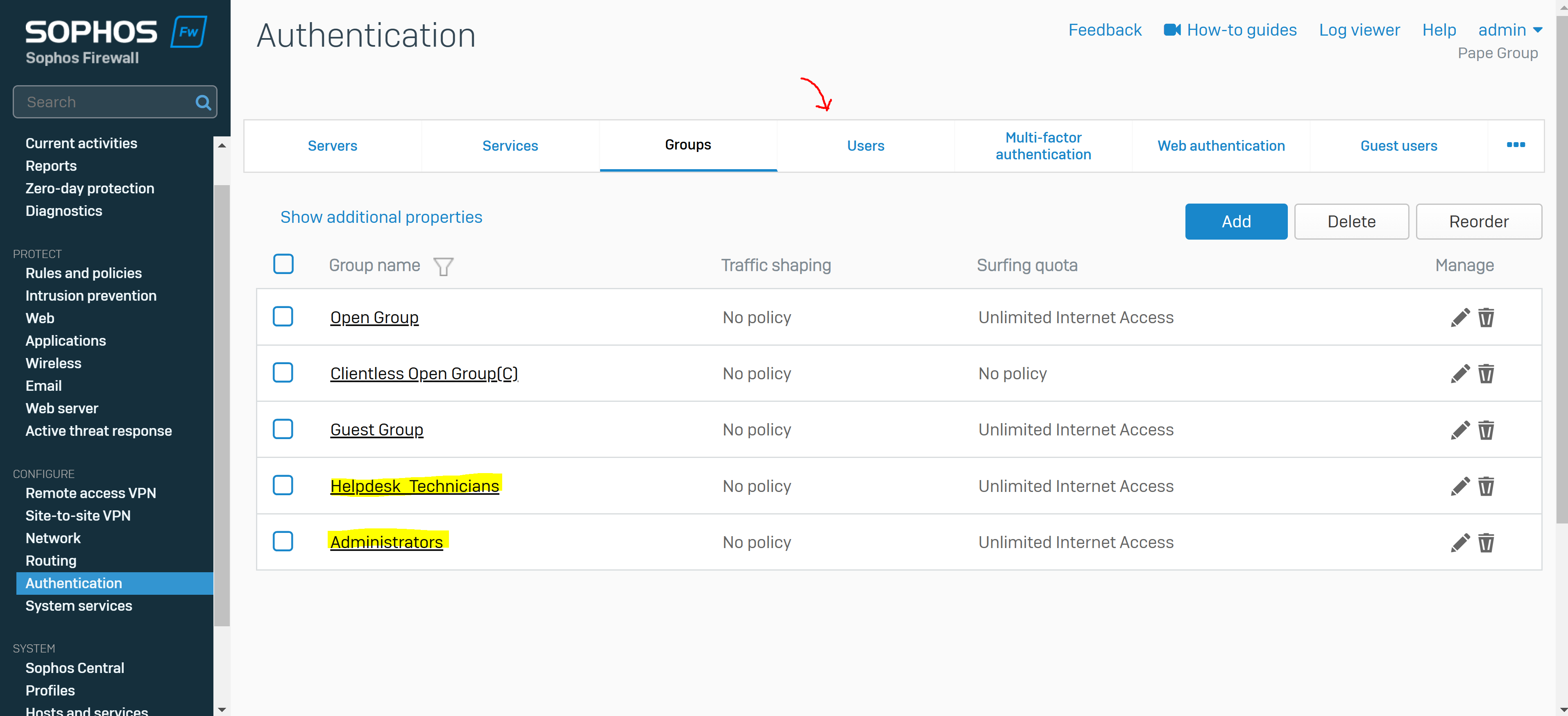
- In this demonstration, I will be defining an 'Administrators' and 'Helpdesk_Technicians' group and assign a user to each group that will later be specified in the SSL VPN policy
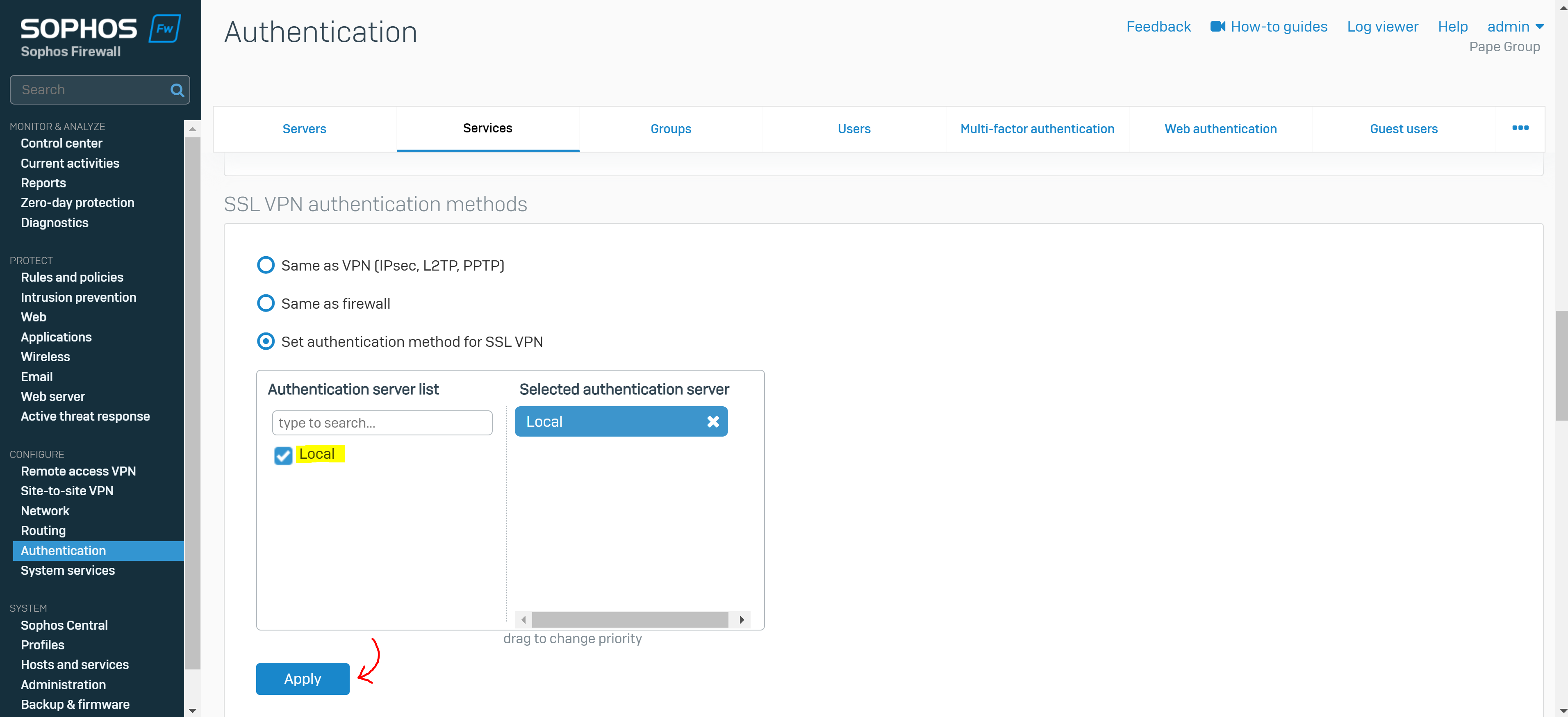
Check Authentication Services
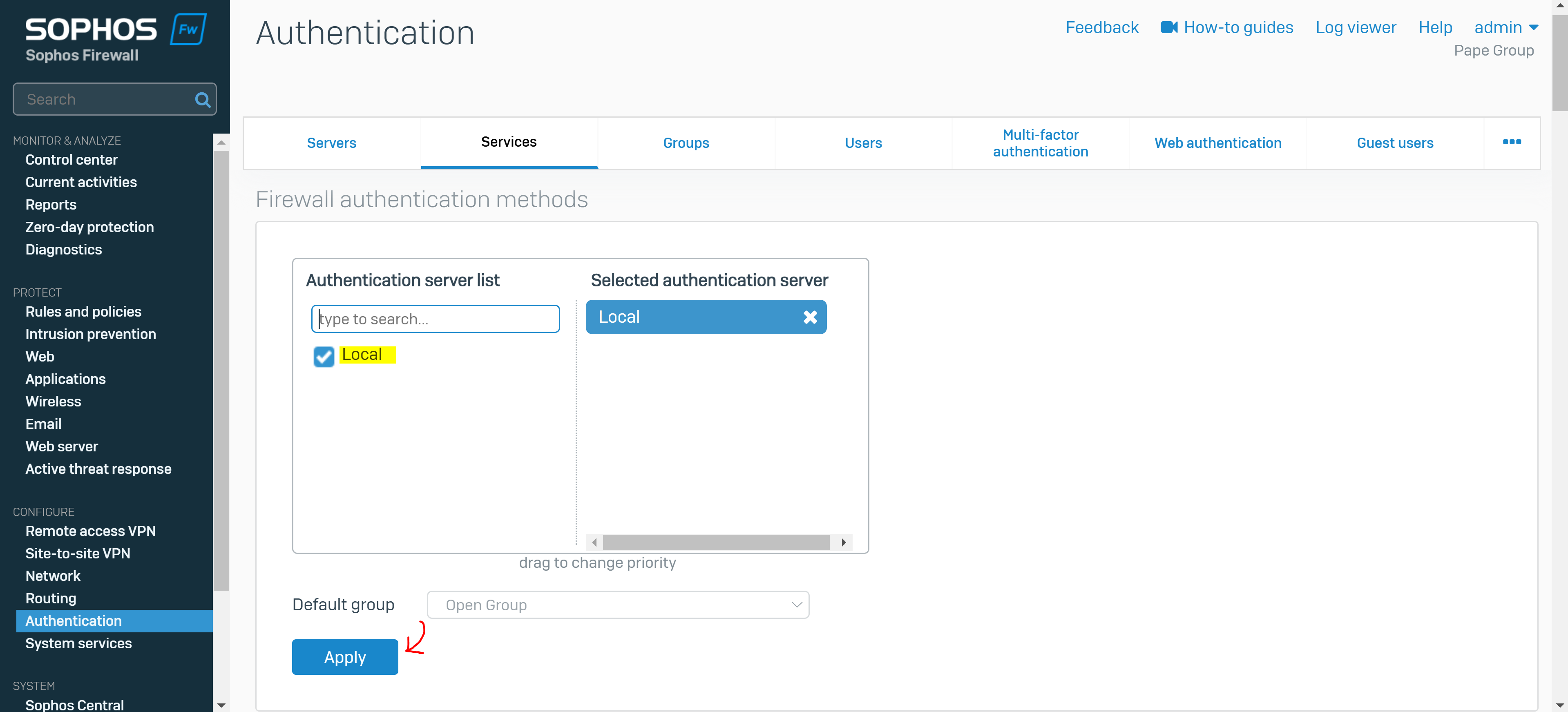
Overview
- Reference: Authentication Services
- On this page, you set the firewall and SSL VPN authentication methods
- Alternatively, you can select an external authentication server, such as Active Directory defined under 'Servers'
- In this demonstration, I will be setting the firewall and SSL VPN authentication methods to 'Local' in which the Sophos Firewall will then act as the authentication server
Specify IP Address Range for SSL VPN Clients
Overview
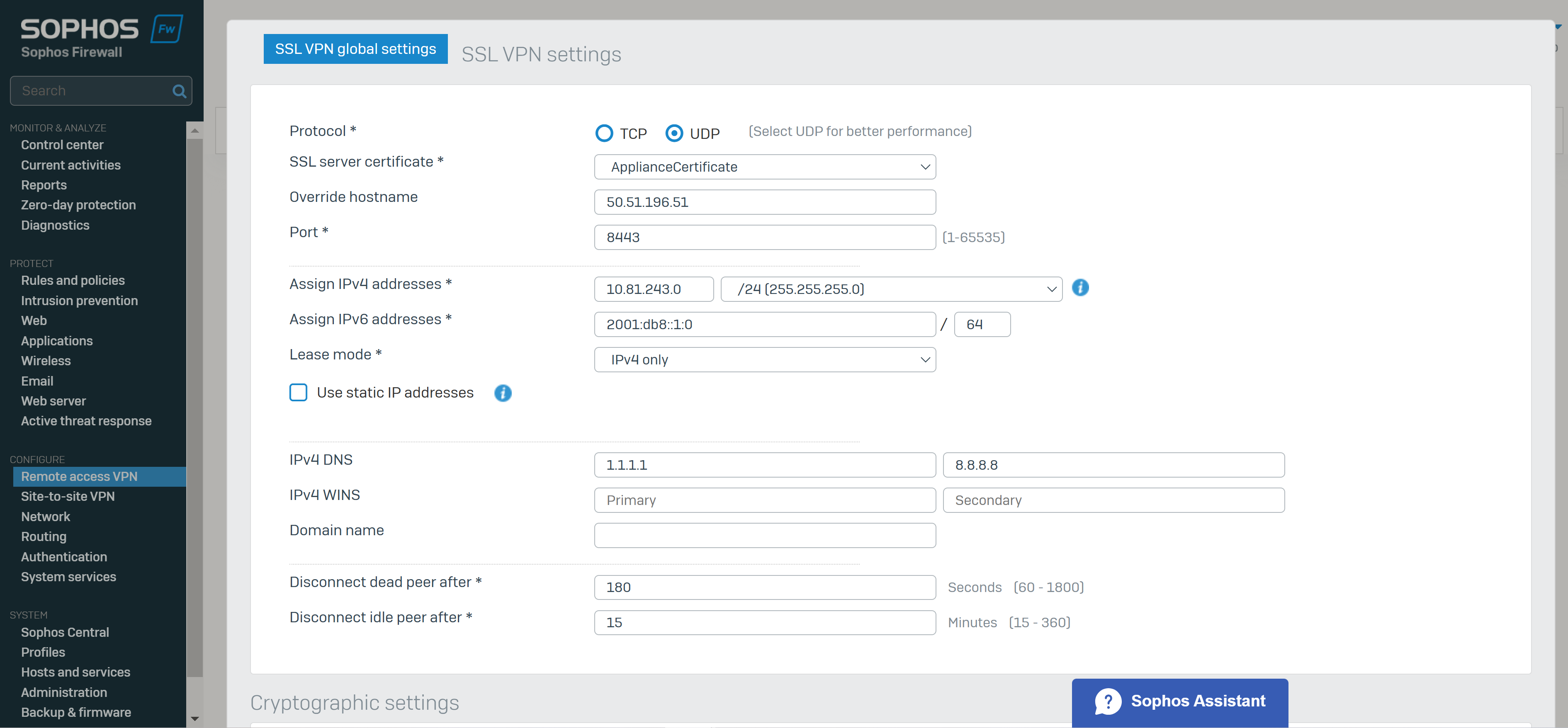
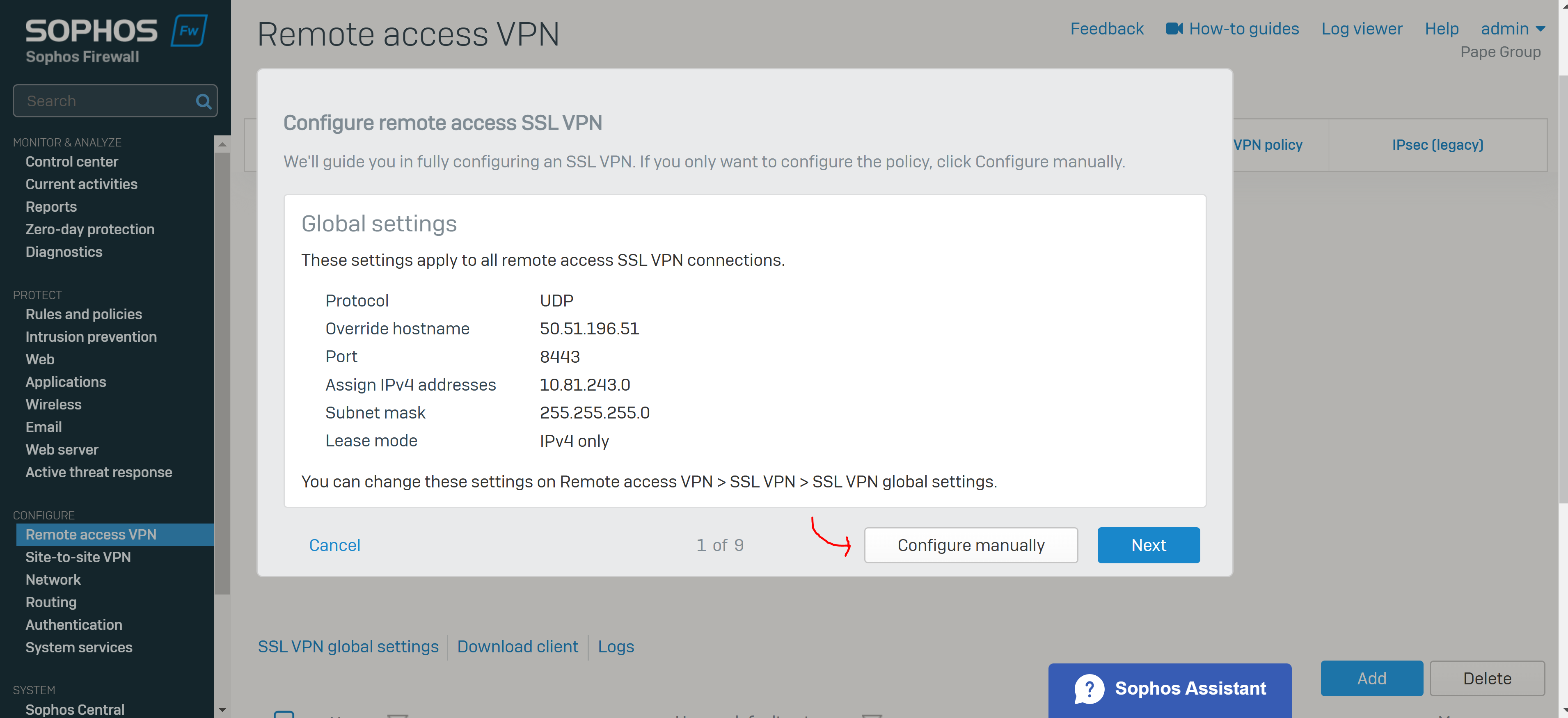
- Reference: SSL VPN Global Settings
- When SSL VPN clients connect to Sophos Firewall, it assigns IP addresses from the address range you specify in the SSL VPN global settings
- The address range must be set in a private RFC 1918 address range
- 10.0.0.0/8 (10.0.0.0 - 10.255.255.255)
- 172.16.0.0/12 (172.16.0.0 - 172.31.255.255)
- 192.168.0.0/16 (192.168.255.255)
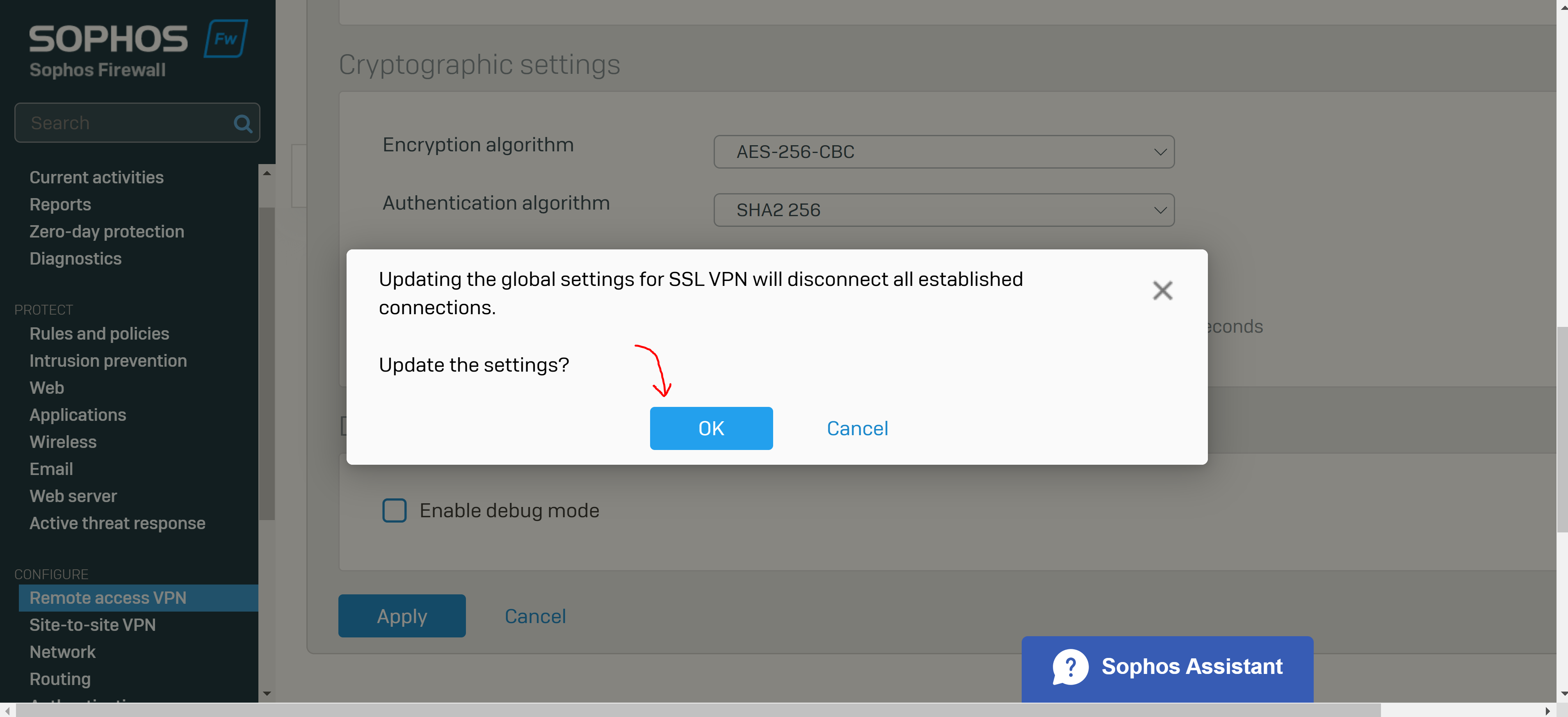
- The SSL VPN global settings apply to all remote access SSL VPN policies
- These settings are part of the '.ovpn' configuration file imported to the SSL VPN client
- Override Hostname Parameter
- SSL VPN clients connect to the IP addresses or hostname specified here
- By default if left blank, all the Sophos Firewall interfaces belonging to the zones from which you allow SSL VPN access (Local Service ACL) will be listed in the '.ovpn' configuration file
- VPN clients will try to establish connections with the interfaces configured on 'Network > Interfaces' or the IP address or hostname manually specified
- In my lab scenario, my Sophos Firewall WAN IP address is being translated (NAT) by the upstream gateway (ISP router). In order for a Remote Access VPN to work in a NAT scenario, I need to specify my ISP router's publicly routable WAN IP address in the Override Hostname section and configure Port Forwarding on these gateway devices demonstrated here: Port Forwarding
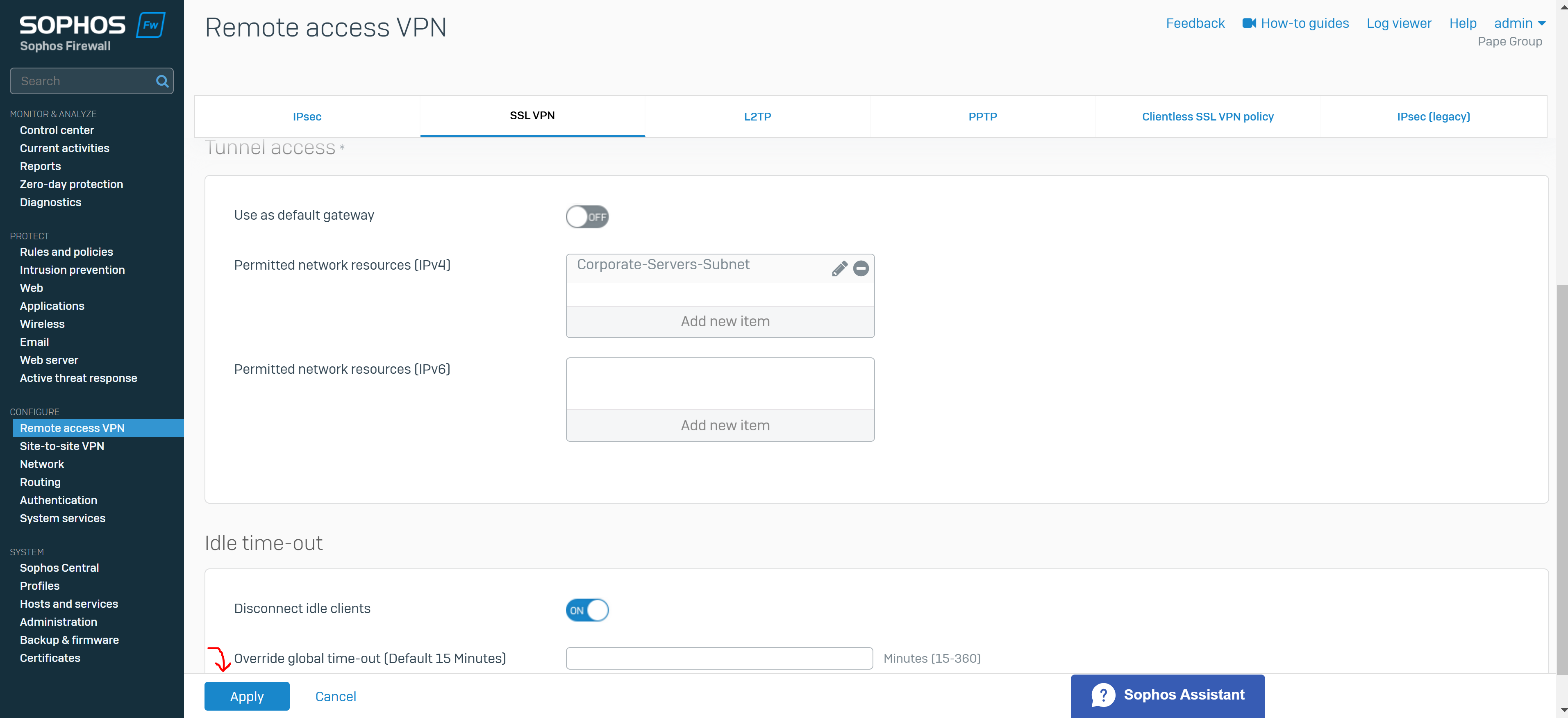
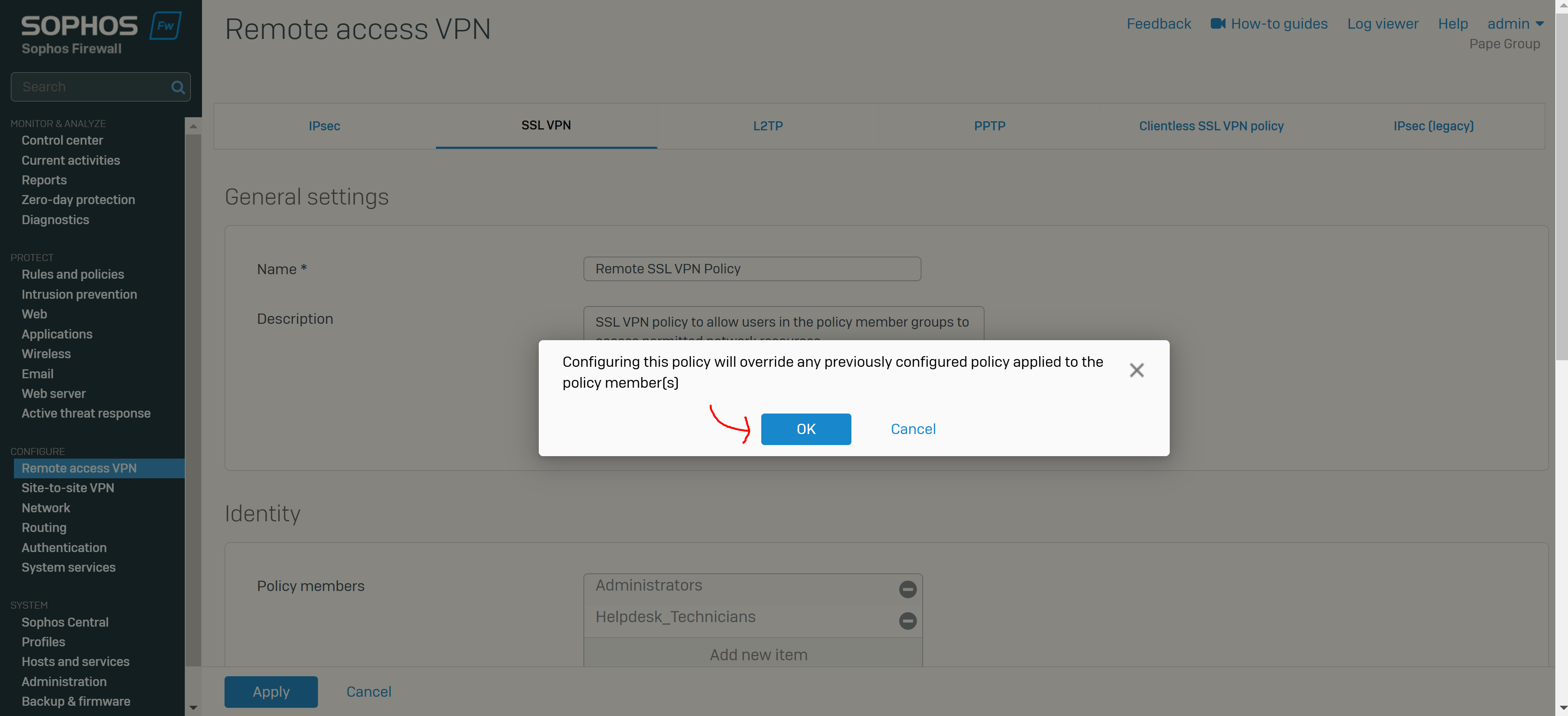
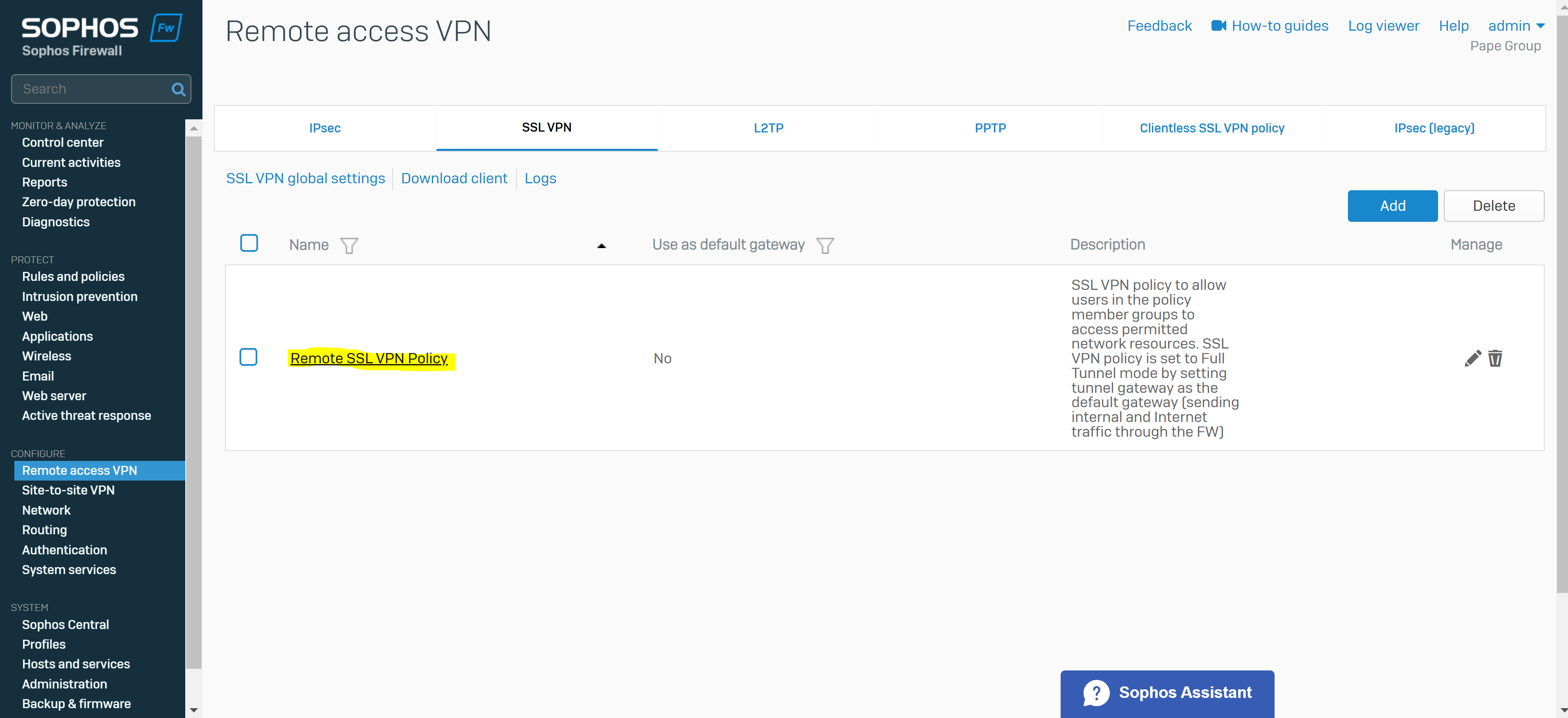
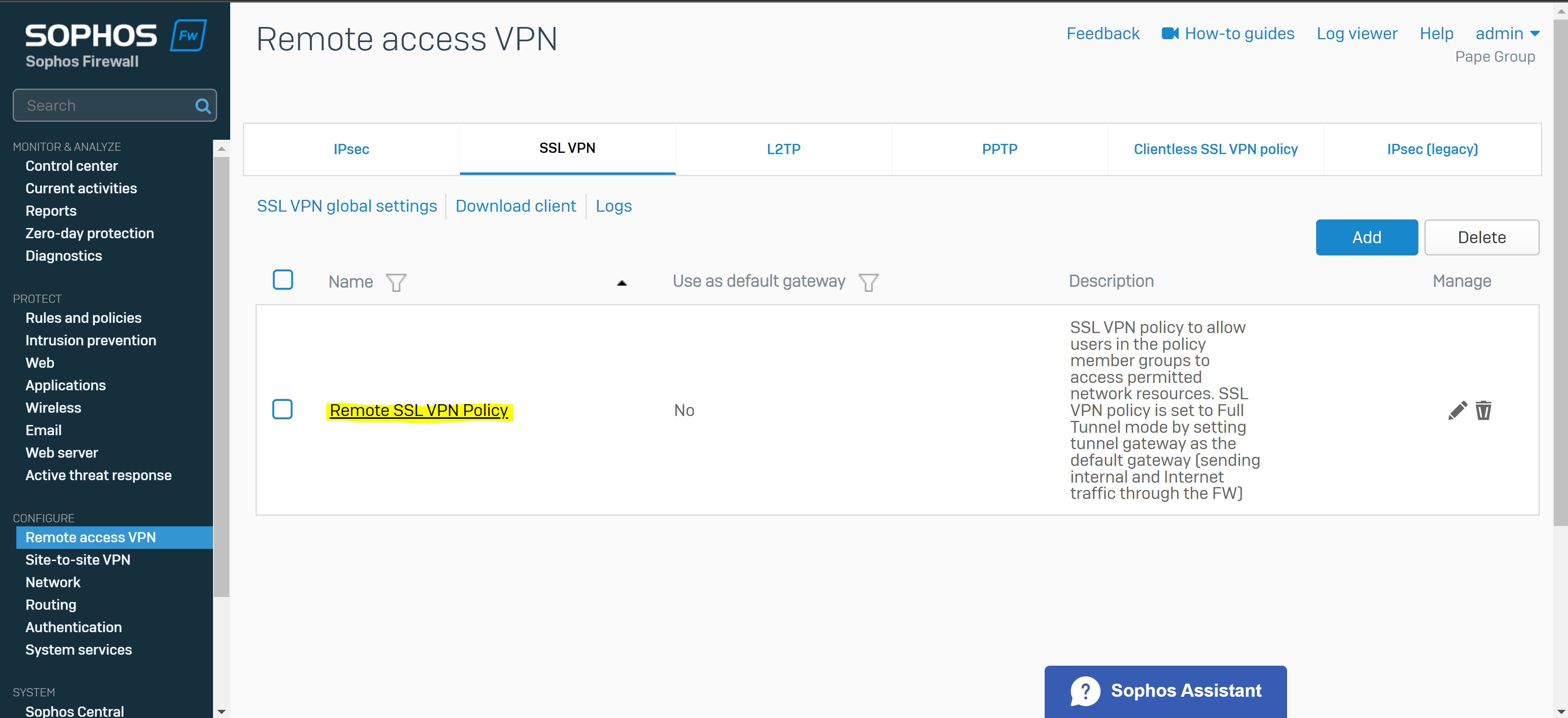
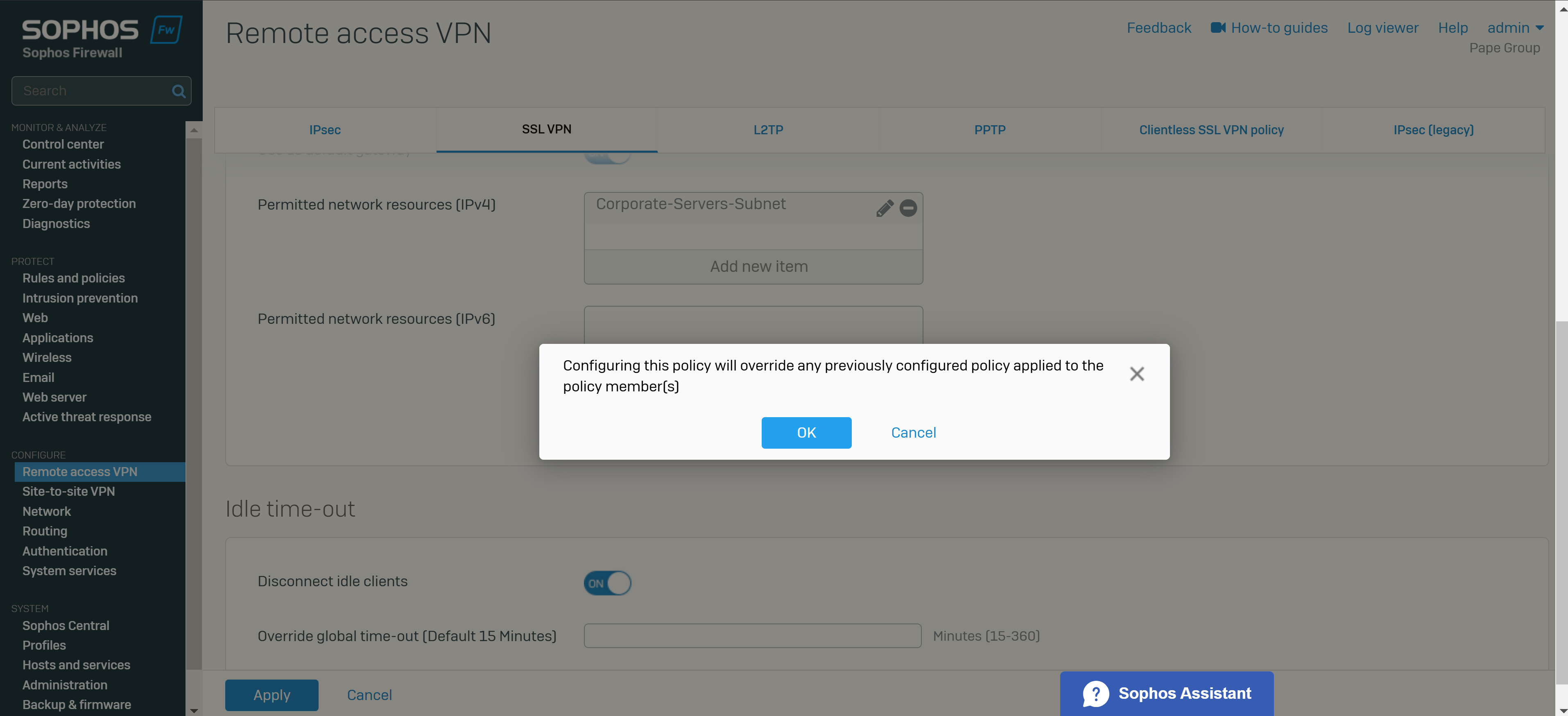
Add an SSL VPN Remote Access Policy
Overview
- Reference: Add a Remote Access SSL VPN Policy
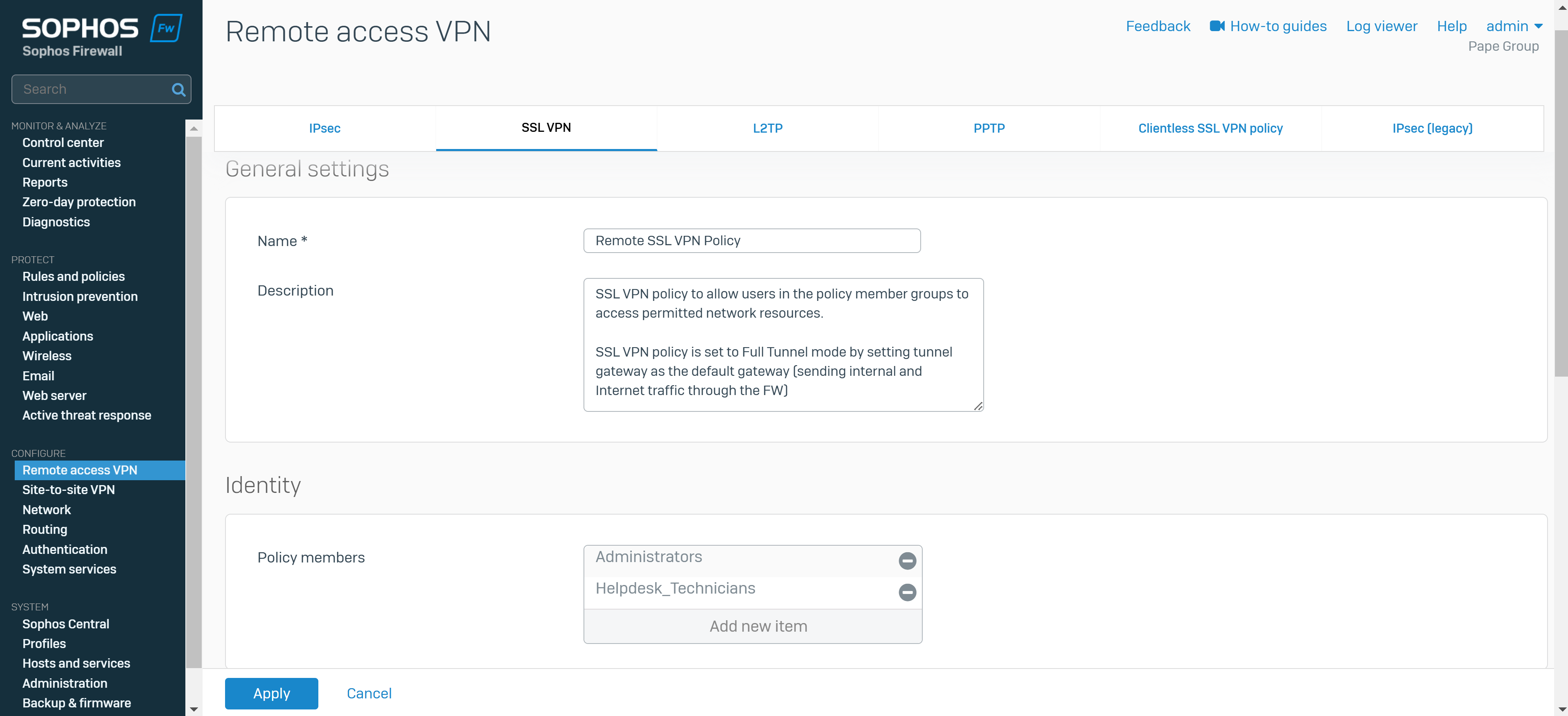
- You can configure remote access SSL VPN policies to allow users and groups to access the permitted network resources
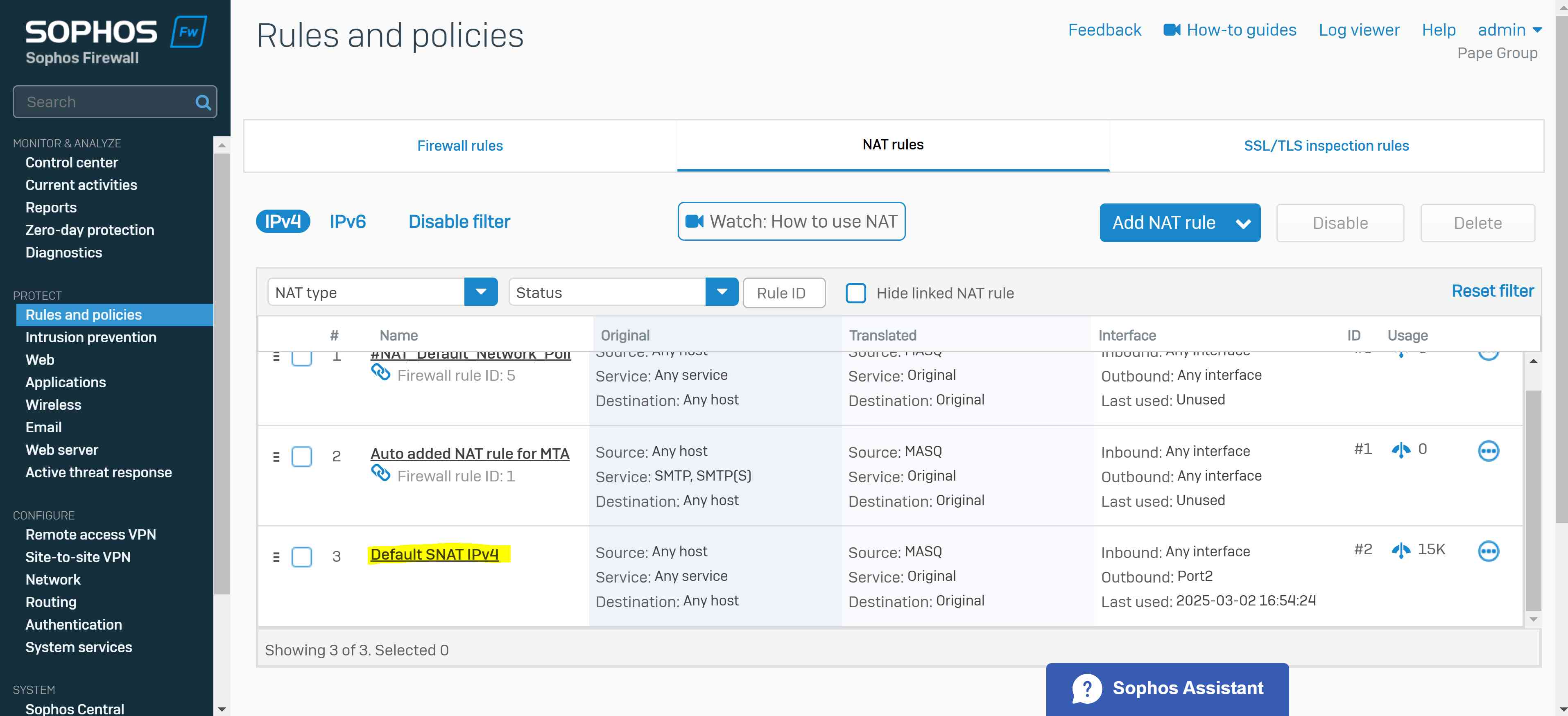
- Note: If you turn on the default gateway setting (Full Tunnel), the firewall's rules and protection policies apply to the remote users' Internet traffic. So, configure a firewall rule with the source zone set to 'VPN' and the destination zone set to 'ANY' to allow traffic to the Internet and the permitted resources. You must also check if the default IPv4 SNAT (source NAT) rule or an SNAT rule to masquerade outbound traffic exists. If it doesn't, you must configure a linked NAT rule to translate the SSL VPN leased IP addresses to a publicly routable IP address. See Check the SNAT rule
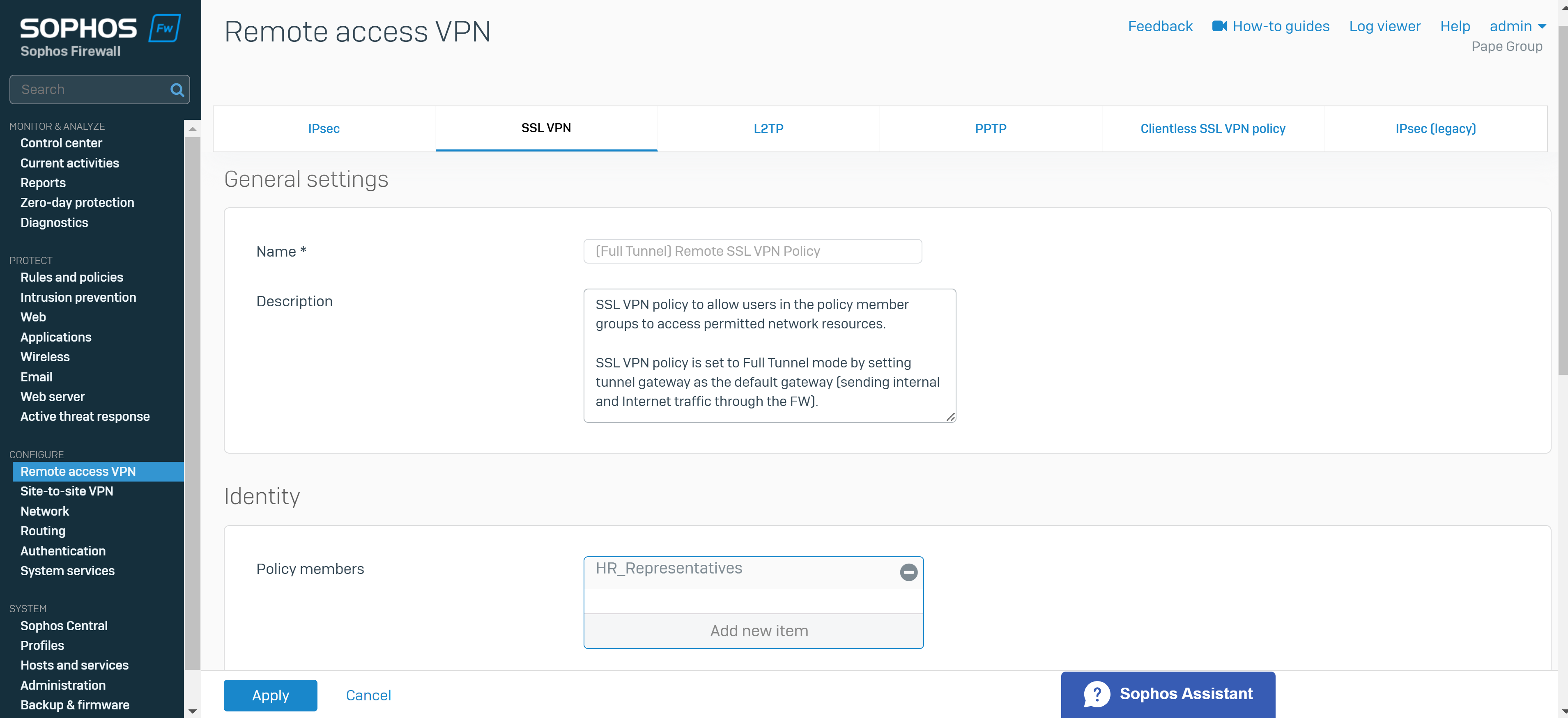
- In this demonstration, I will define a Split-tunnel SSL VPN policy, add the authentication groups defined previously as Policy members, and add the IP host network defined previously as the Permitted network resource for these authentication groups
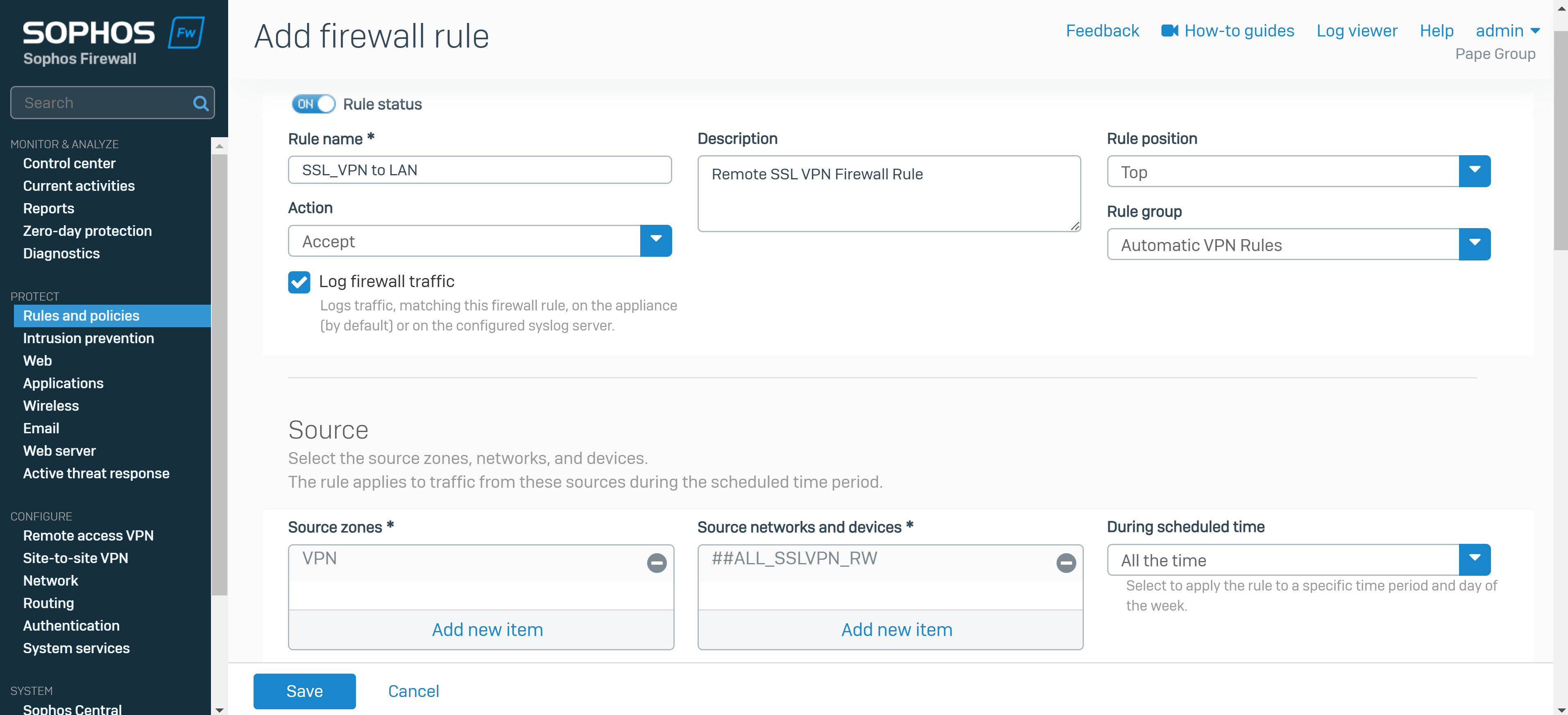
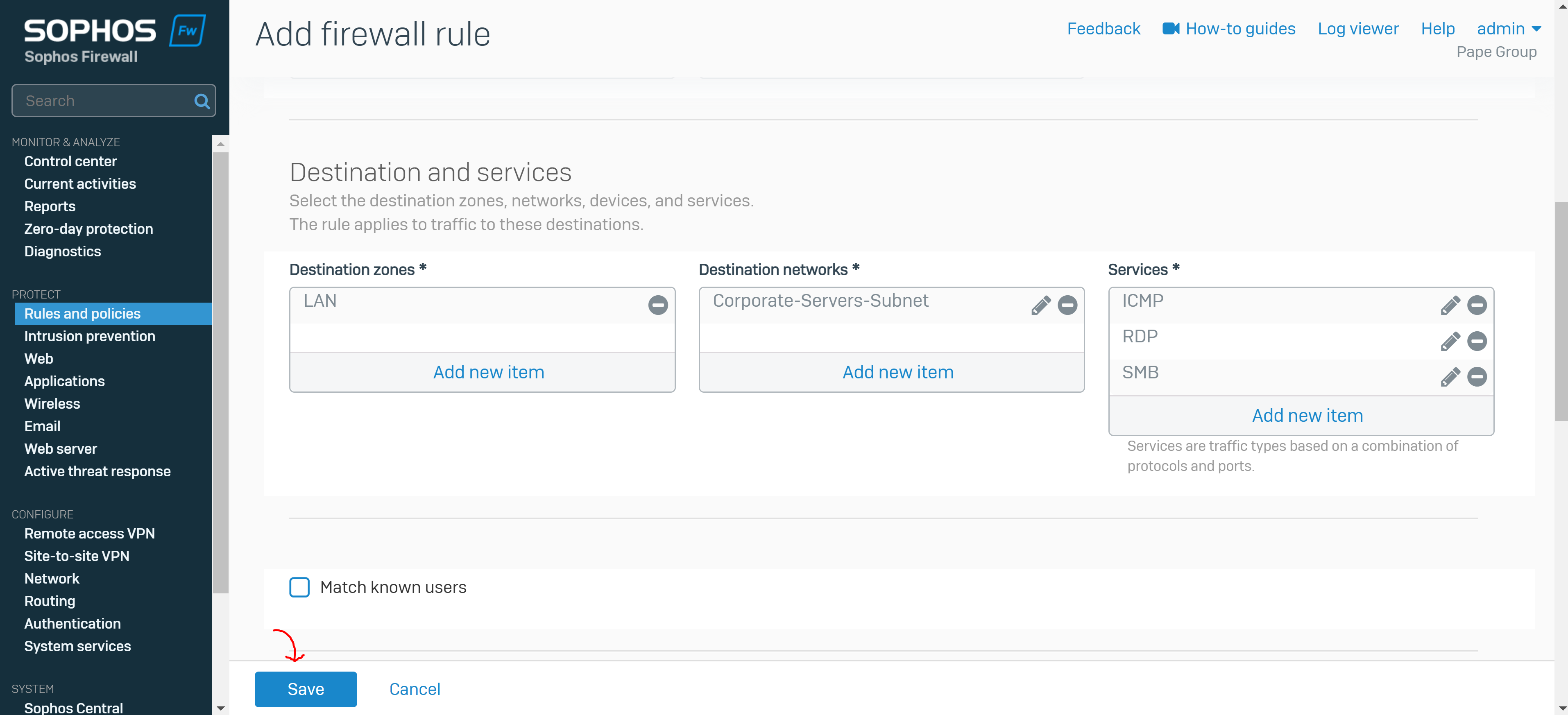
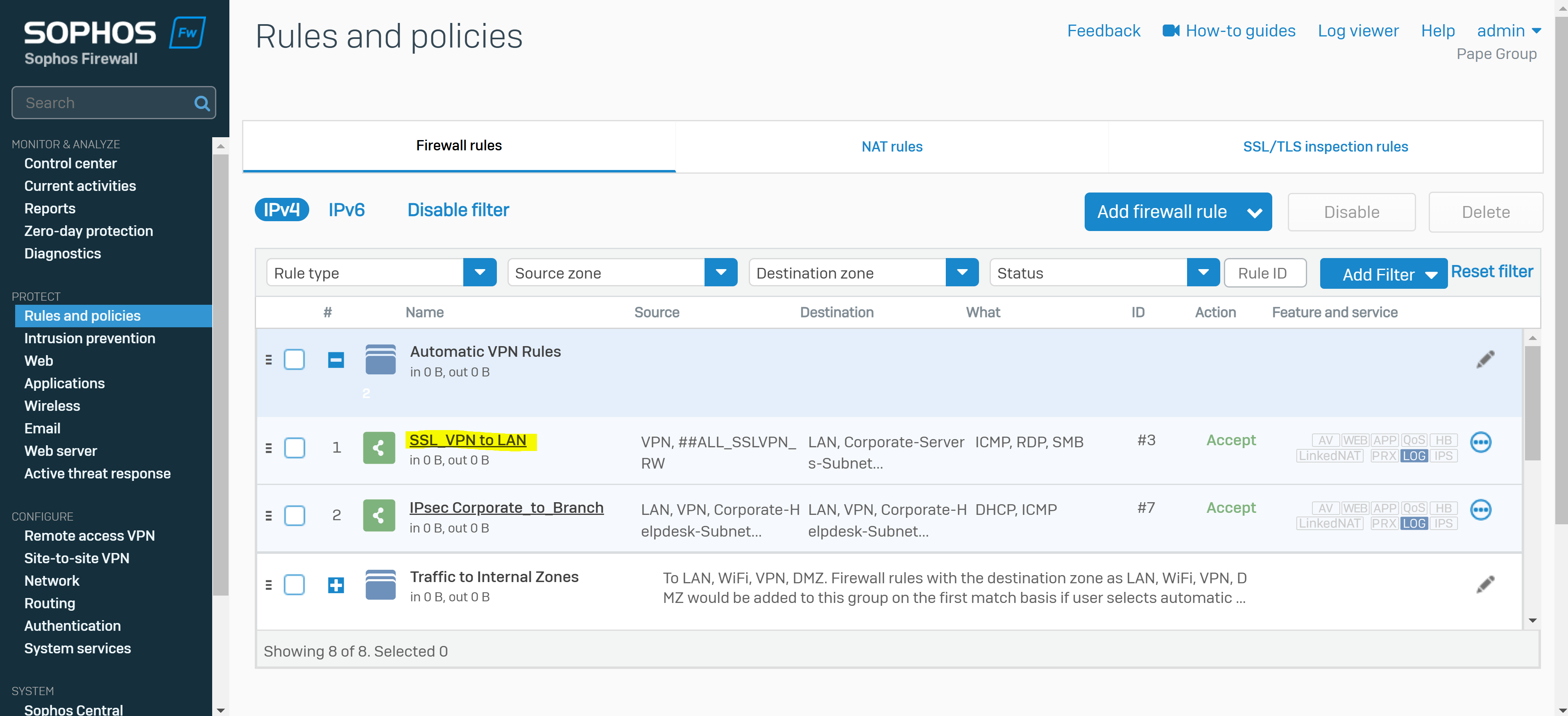
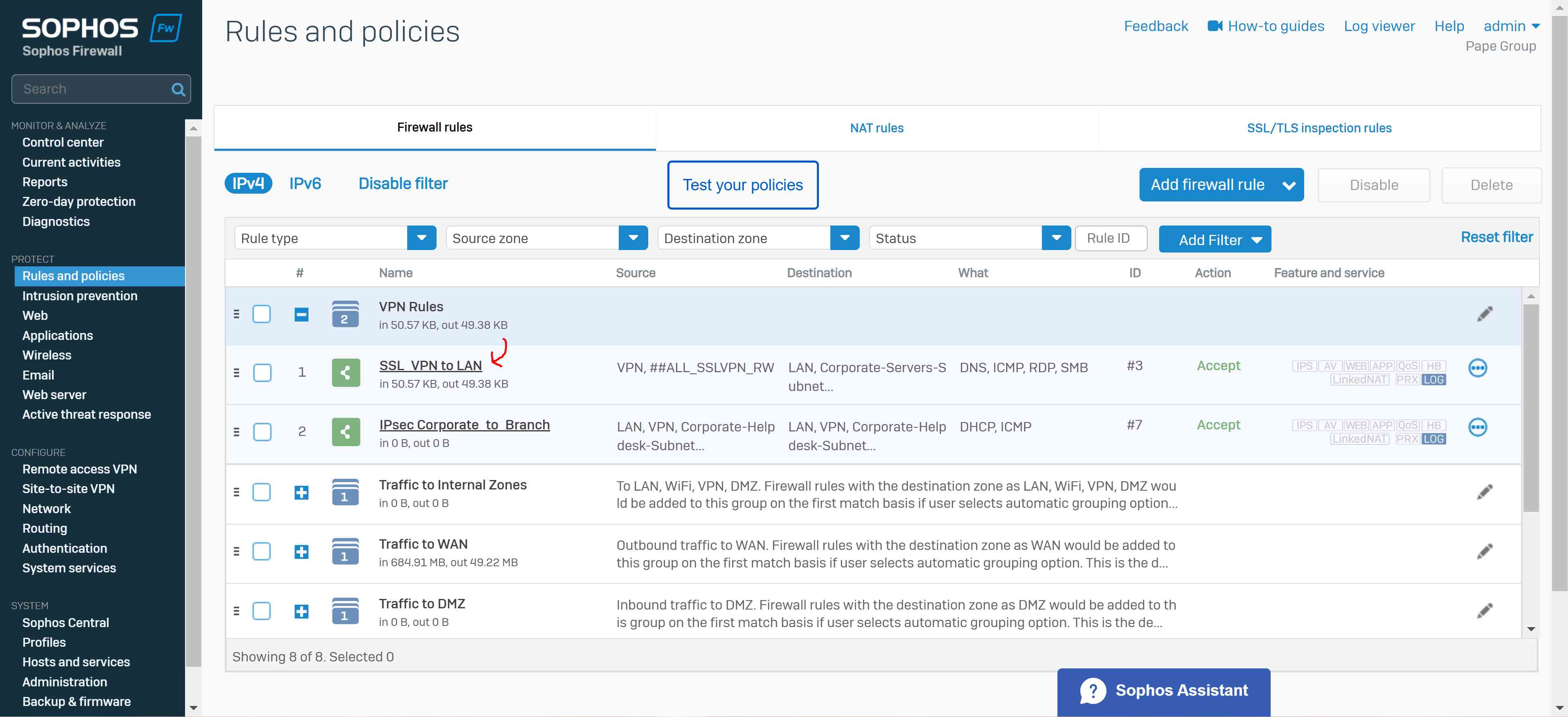
Add a Firewall Rule
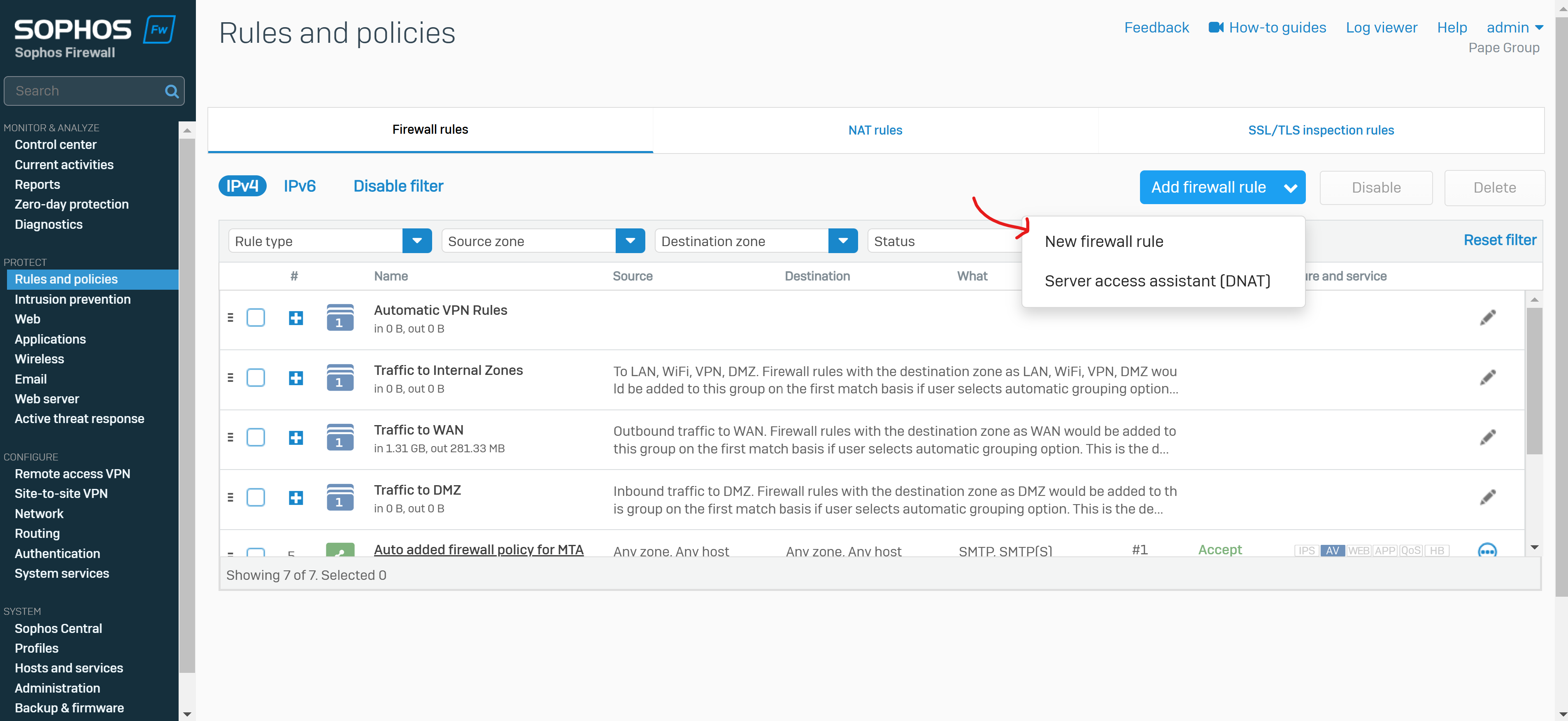
Overview
- A Firewall rule must be defined to allow VPN users to access resources on the network once they've established a connection
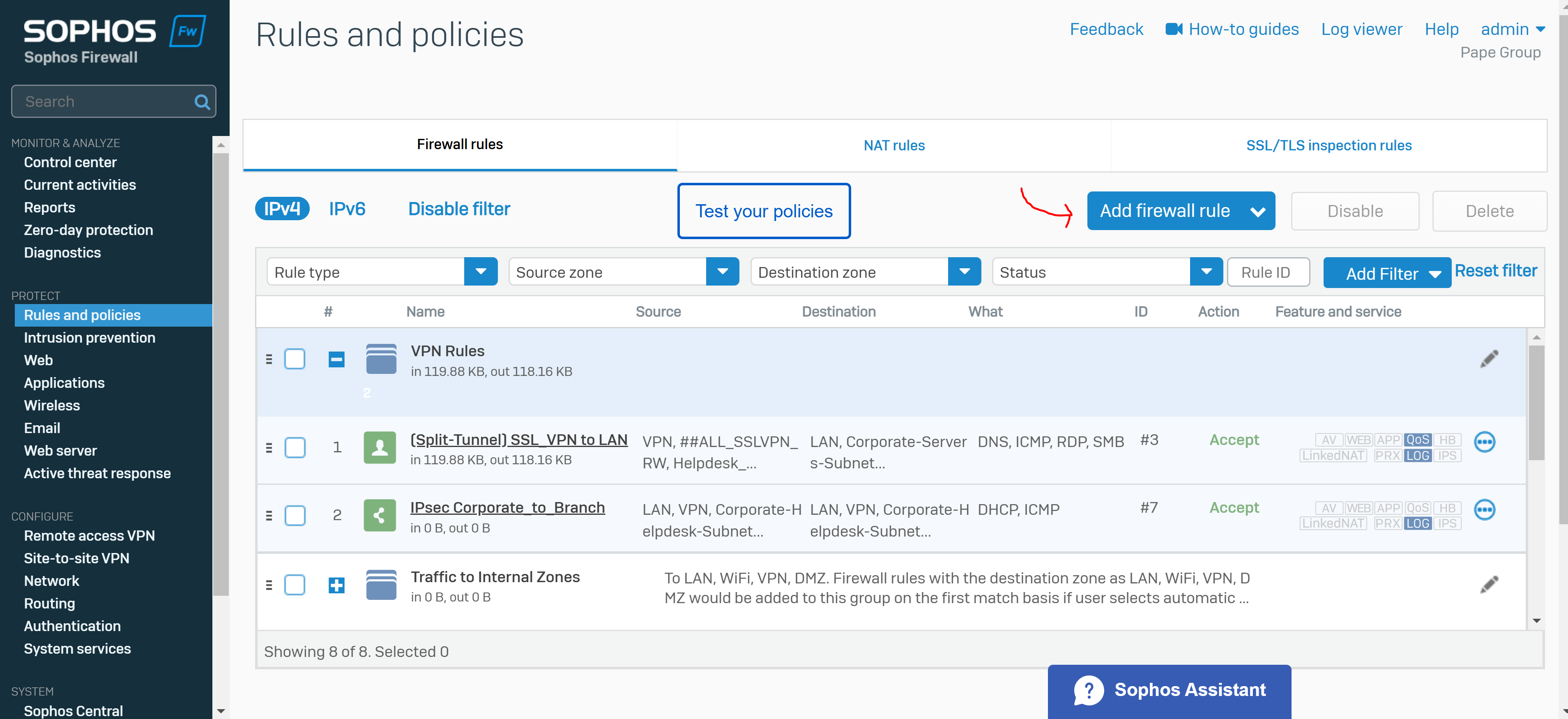
- In this demonstration, I will define a firewall rule for the Split-tunnel SSL VPN policy in which VPN clients will only be redirected to the Sophos Firewall for internal resources securely but not when it comes to WAN access
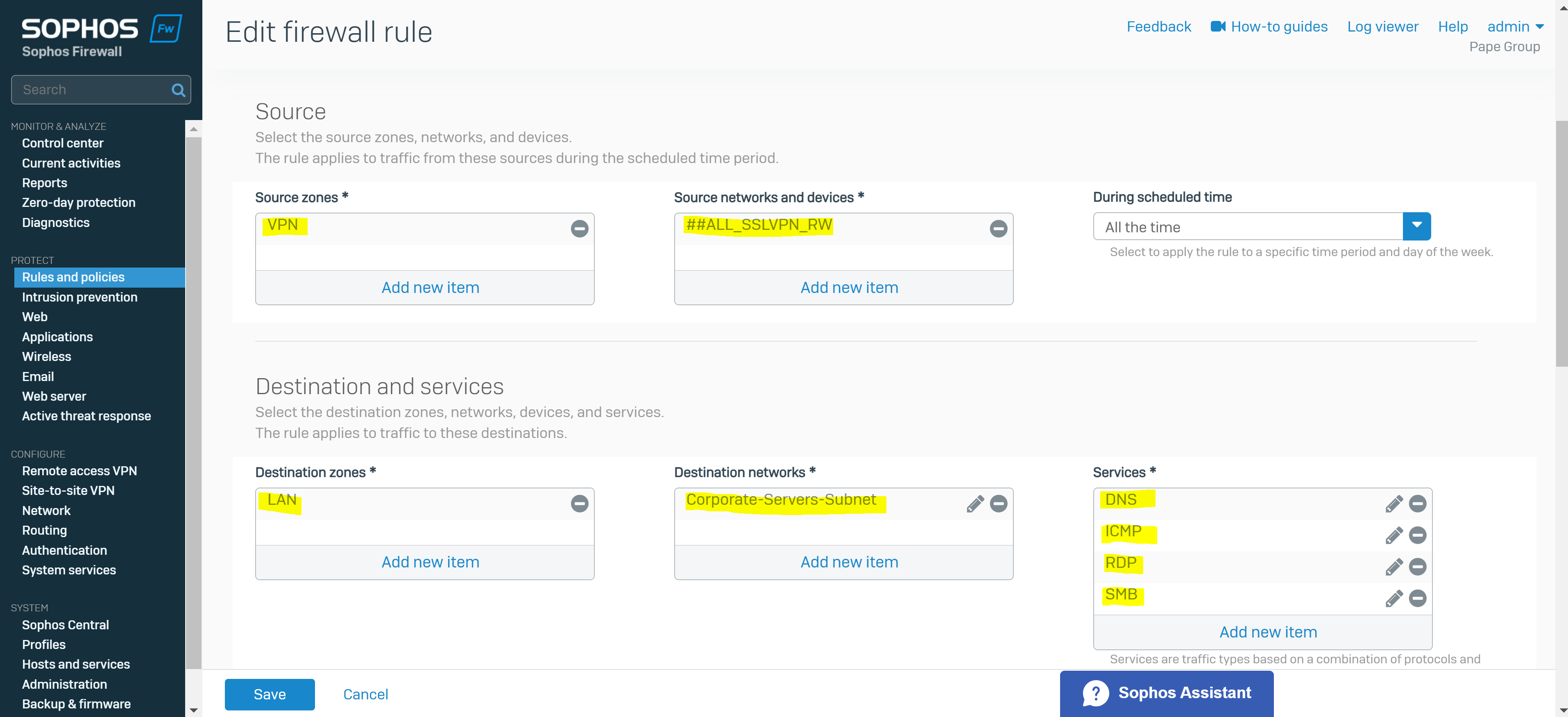
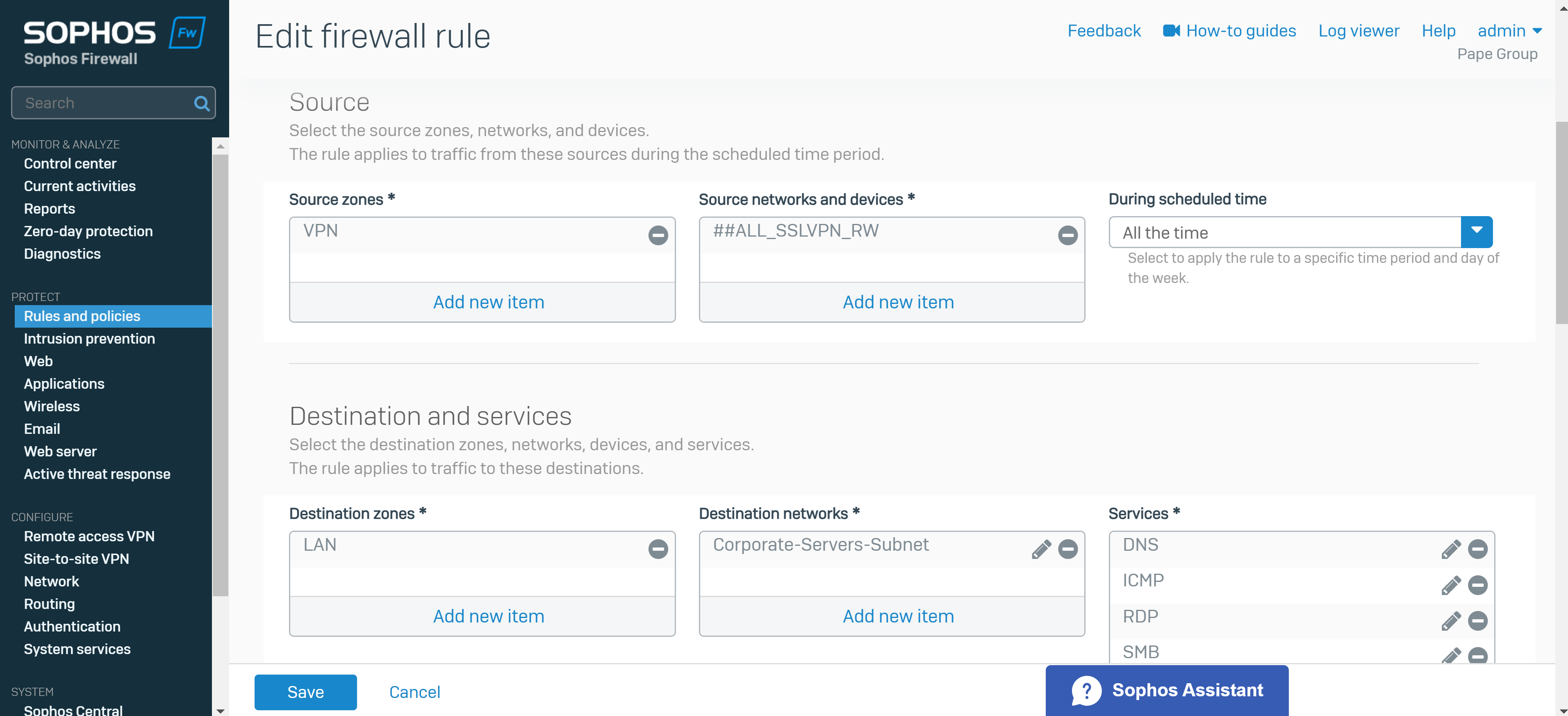
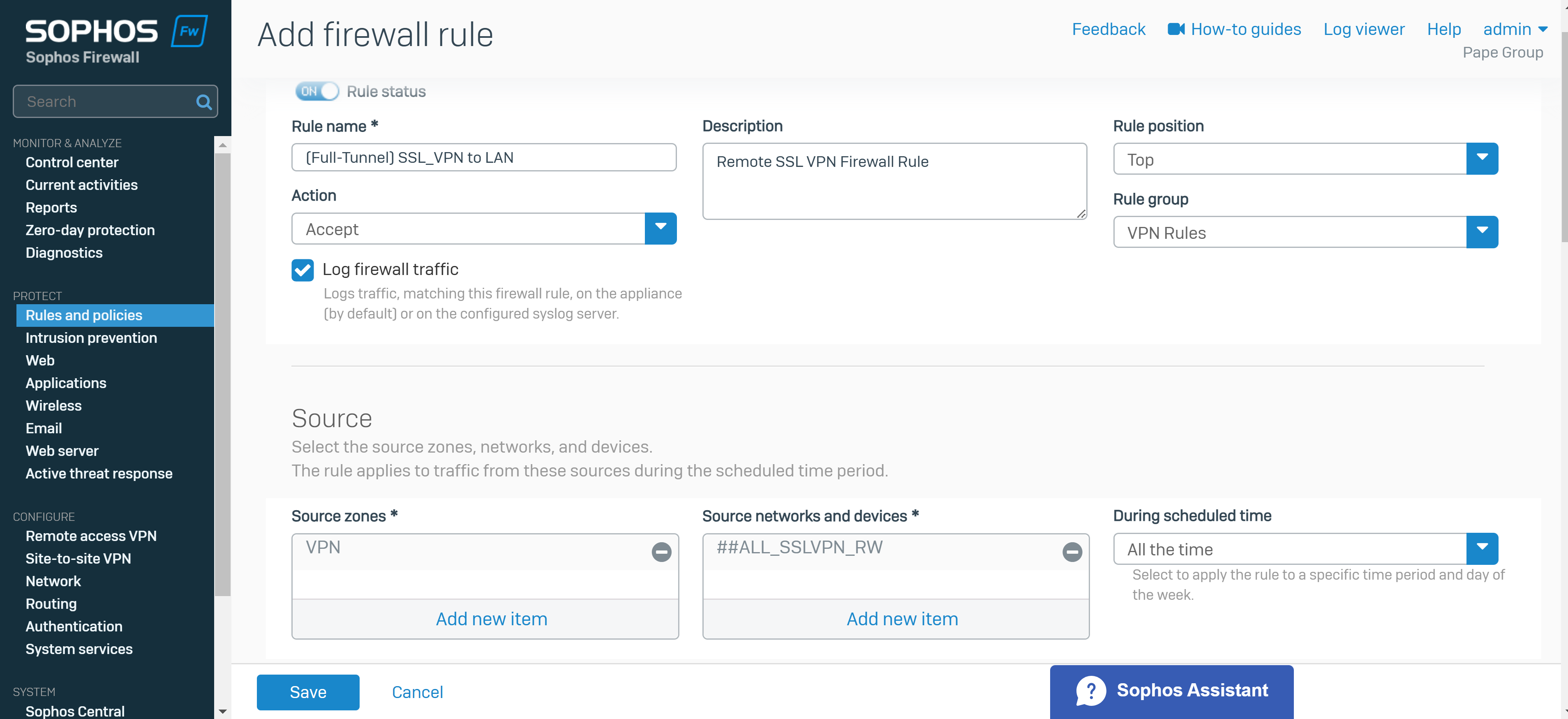
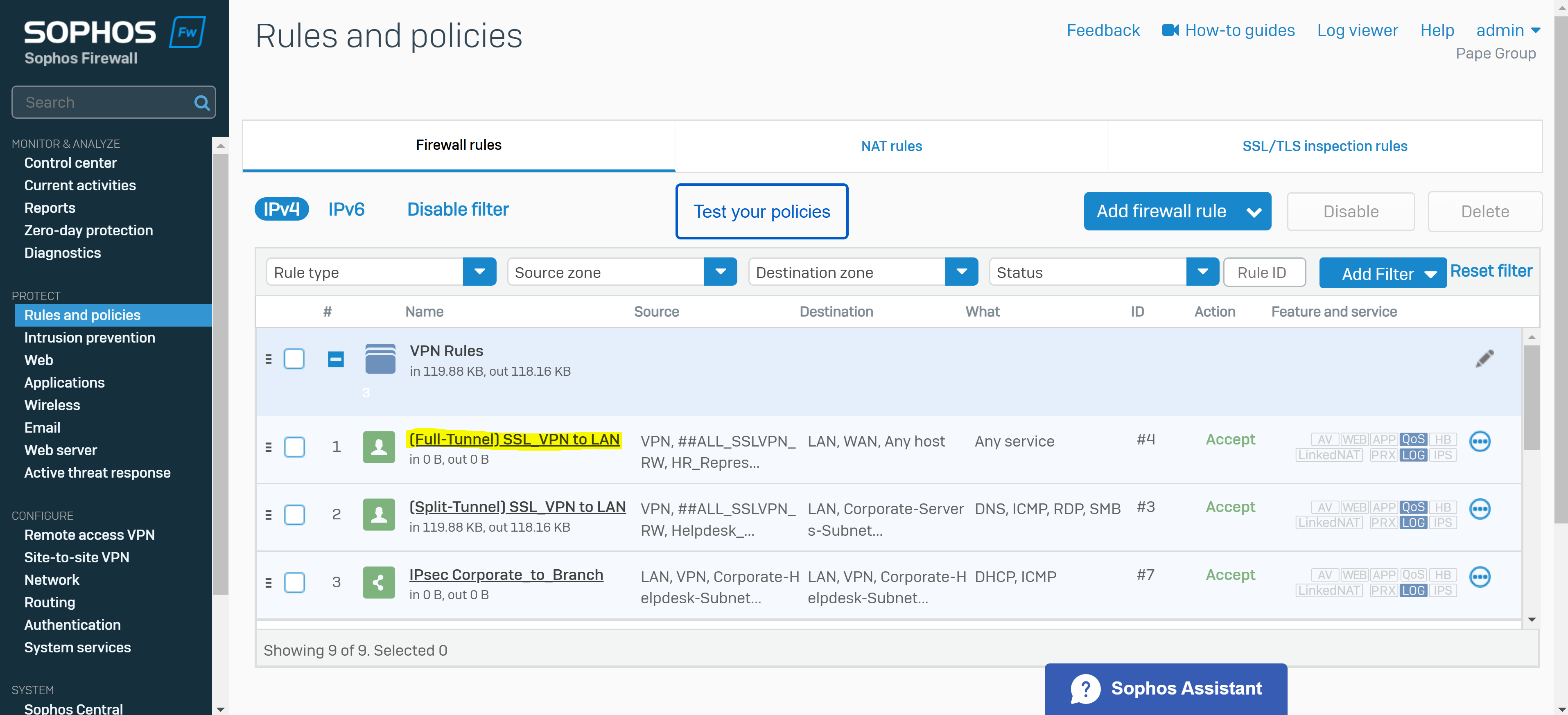
- Under source zone, select 'VPN'. For source networks and devices, select '##ALL_SSLVPN_RW' for IPv4 or '##ALL_SSLVPN_RW6' for IPv6
- Under destination zones, select the zones of the resources you want to give remote access to. For destination networks, select the IP host you've created for the permitted network resources and select any services that can be accessed from those destination networks (ICMP, RDP, and SMB in my case)
- Note: If you turn on the default gateway setting (Full Tunnel), the firewall's rules and protection policies apply to the remote users' Internet traffic. So, configure a firewall rule with the source zone set to 'VPN' and the destination zone set to 'ANY' to allow traffic to the Internet and the permitted resources. You must also check if the default IPv4 SNAT (source NAT) rule or an SNAT rule to masquerade outbound traffic exists. If it doesn't, you must configure a linked NAT rule to translate the SSL VPN leased IP addresses to a publicly routable IP address. See Check the SNAT rule
Device Access - Check Local Service ACL
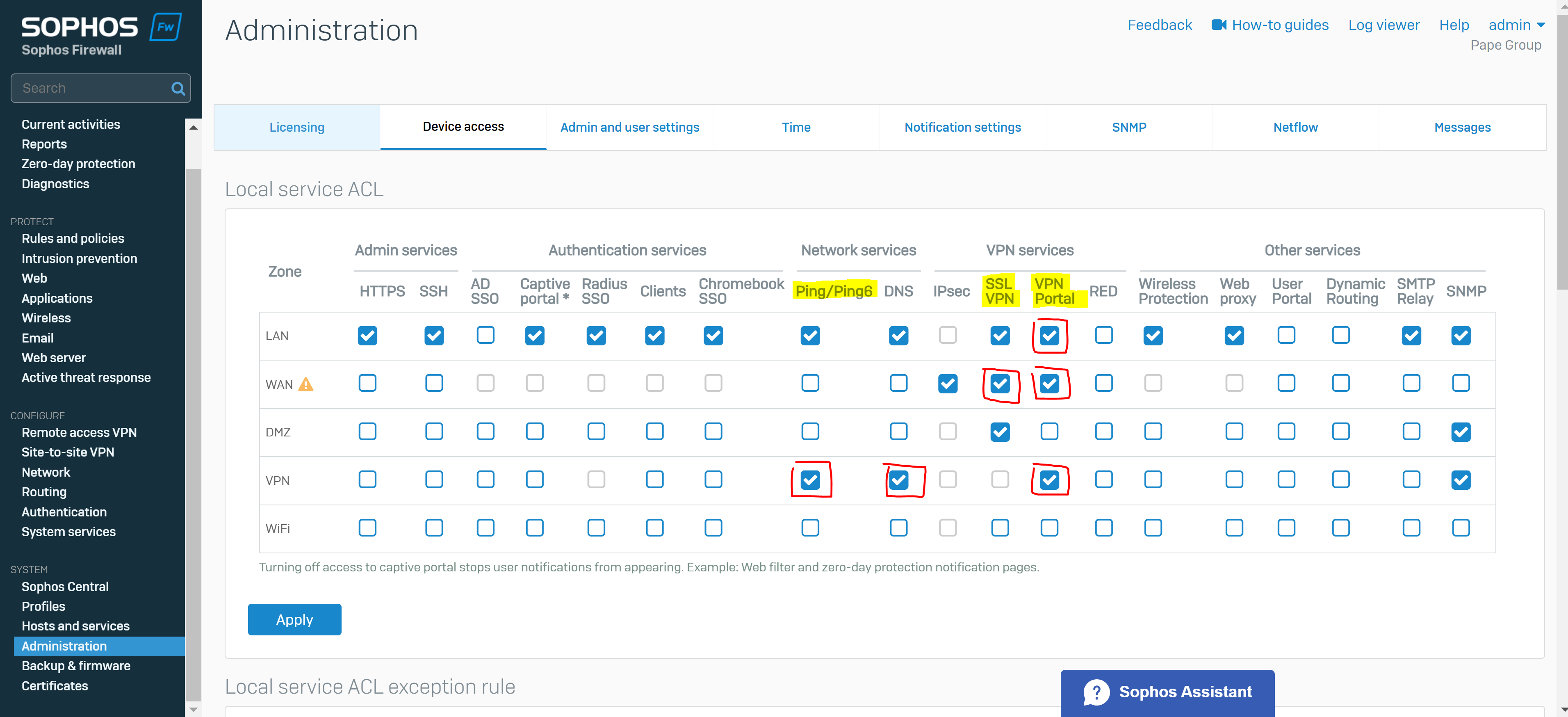
Overview
- Reference: Device Access (Local Service ACL)
- You must give access to some services for remote users from the required zones
- Selecting 'SSL VPN' under the WAN zone allows remote users to establish SSL VPN connections
- Selecting 'VPN portal' under the VPN, WAN, and LAN zones allows users from these zones to access the VPN portal so they can download the VPN client and configuration file
- Note: Starting from v20 on SFOS, the SSL VPN '.ovpn' configuration file is moved from User portal to VPN portal, accessible on port 443 by default
- Note: Sophos recommends that administrators turn off access to the User and VPN portal from the WAN zone after users download the VPN client and configuration file
- Selecting 'Ping/Ping6' under the VPN zone allows users to ping the firewall's IP address through the VPN to check connectivity
- Optionally, selecting 'DNS' under the VPN zone allows users to resolve domain names through VPN if you've specialized the Sophos firewall for DNS resolution in VPN settings
Port Forwarding
Overview
- In certain network deployment scenarios such as NAT devices located downstream of the ISP router, Port Forwarding is required to successfully allow external devices on the Internet to access specific services or applications on a local network, such as a private home or office network
- Port Forwarding works by forwarding traffic from a particular port on your router to a specific device or server inside your network with a private IP address
Networking Fundamentals
- In normal NAT translation services, when a device with a private IP address in your local network makes an outbound connection out to the Internet, the default gateway or router translates the private IP address to its own public IP address and keeps track of the connection in a state table. When a response comes back, the router knows which internal device requested it and forwards the response to the right device
- Now the issue with inbound connections with no active translation tables on the firewall or router, the gateway does not automatically know which device inside your network should receive the incoming request. The gateway only knows the external public IP, not which internal private IP to send the traffic to
- With Port Forwarding, it acts as a rule or map for the gateway, telling it, "When an inbound request arrives on this specific external port, forward it to this internal device's IP address and port." Essentially, port forwarding opens a "gate" on your gateway for that traffic to get to the right internal device
- Without Port Forwarding, the gateway would block most inbound connections because it does not know where to send them. By setting up port forwarding, you allow certain types of inbound traffic from the Internet to reach specific devices inside your private network
My Lab Use Case
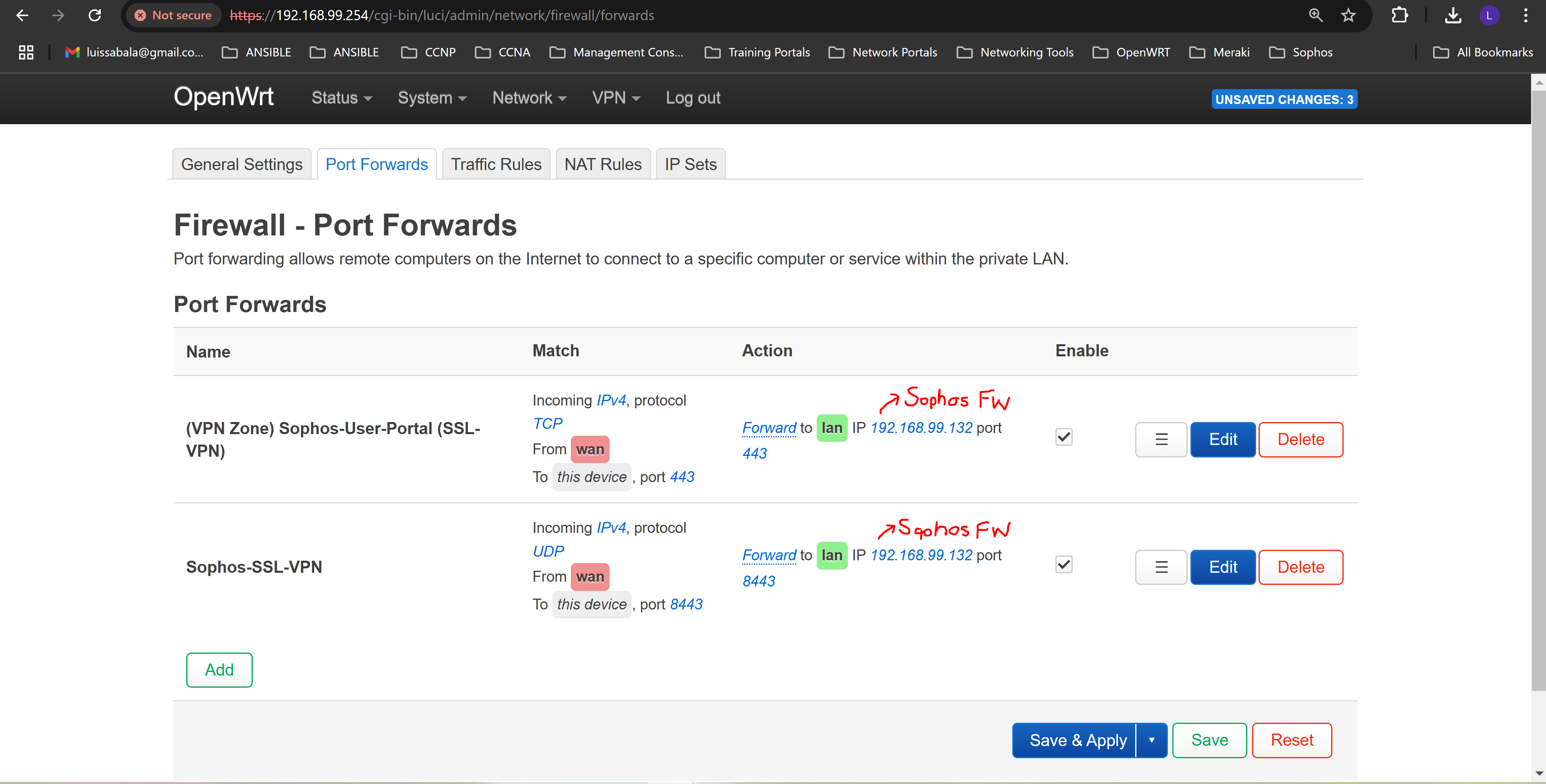
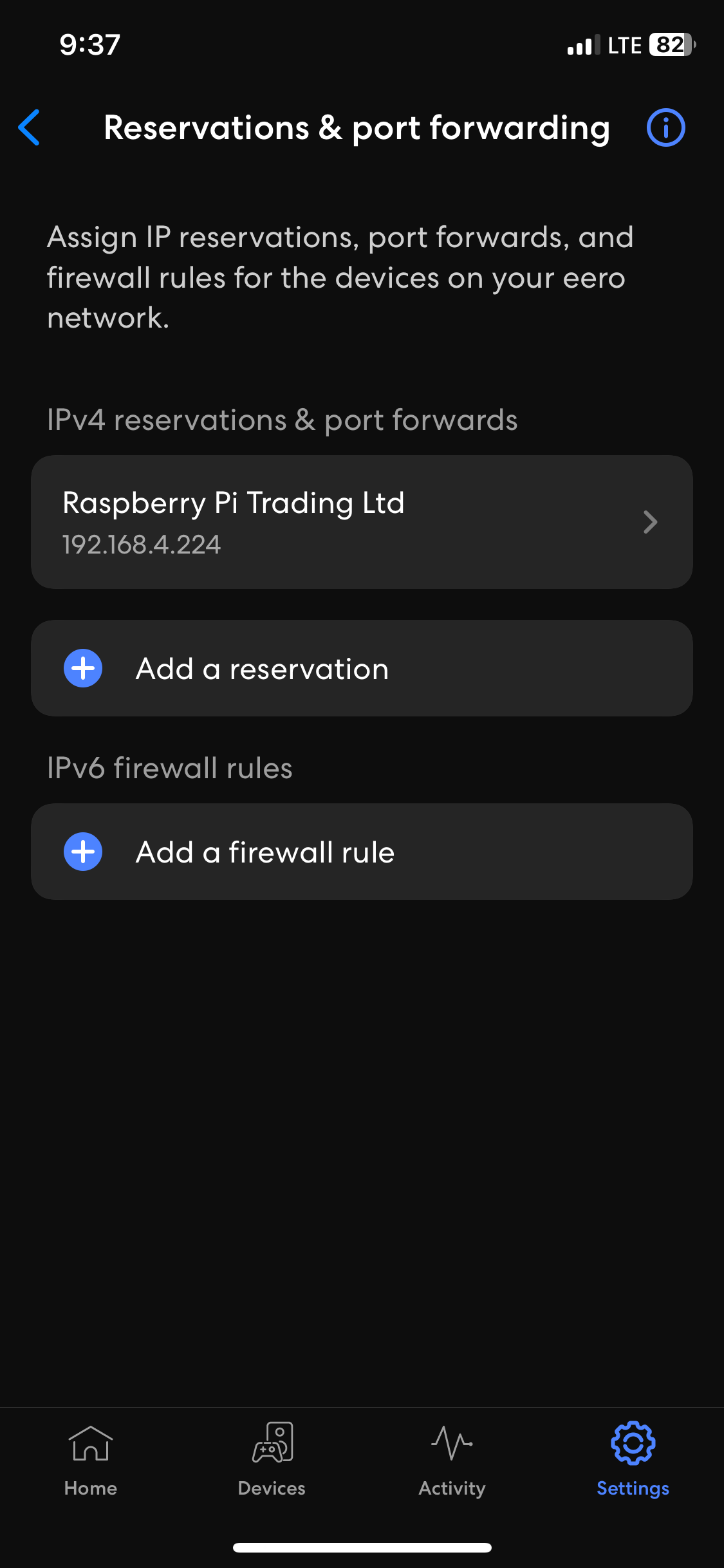
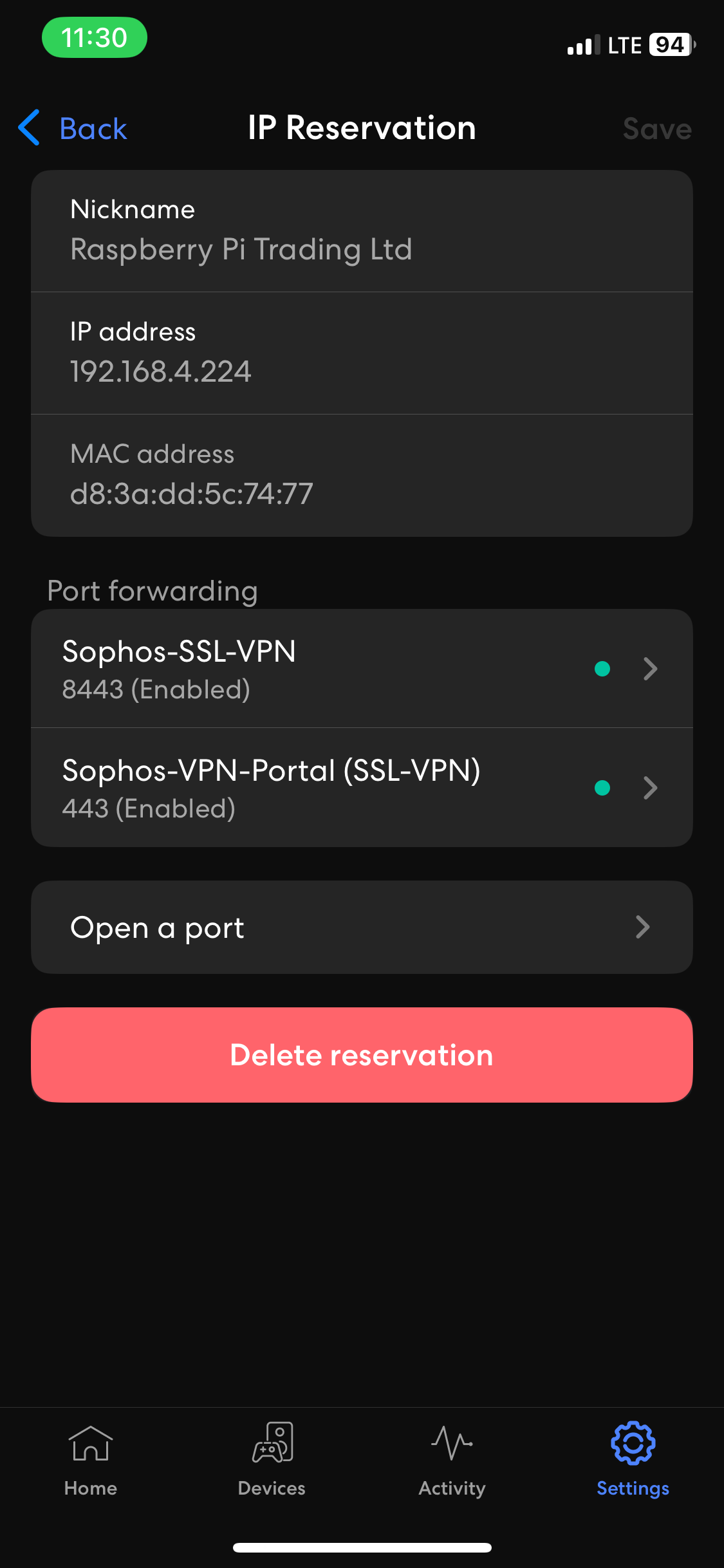
- In my lab environment, it was required of me to set up port forwarding on my ISP equipment router in addition to the downstream Raspberry Pi serving as the default gateway for my Corporate site LAN in this lab
- I have illustrated the images below defining the Port Forwarding rules configured on the ISP Eero router through the mobile application and my Raspberry Pi running the OpenWRT firmware
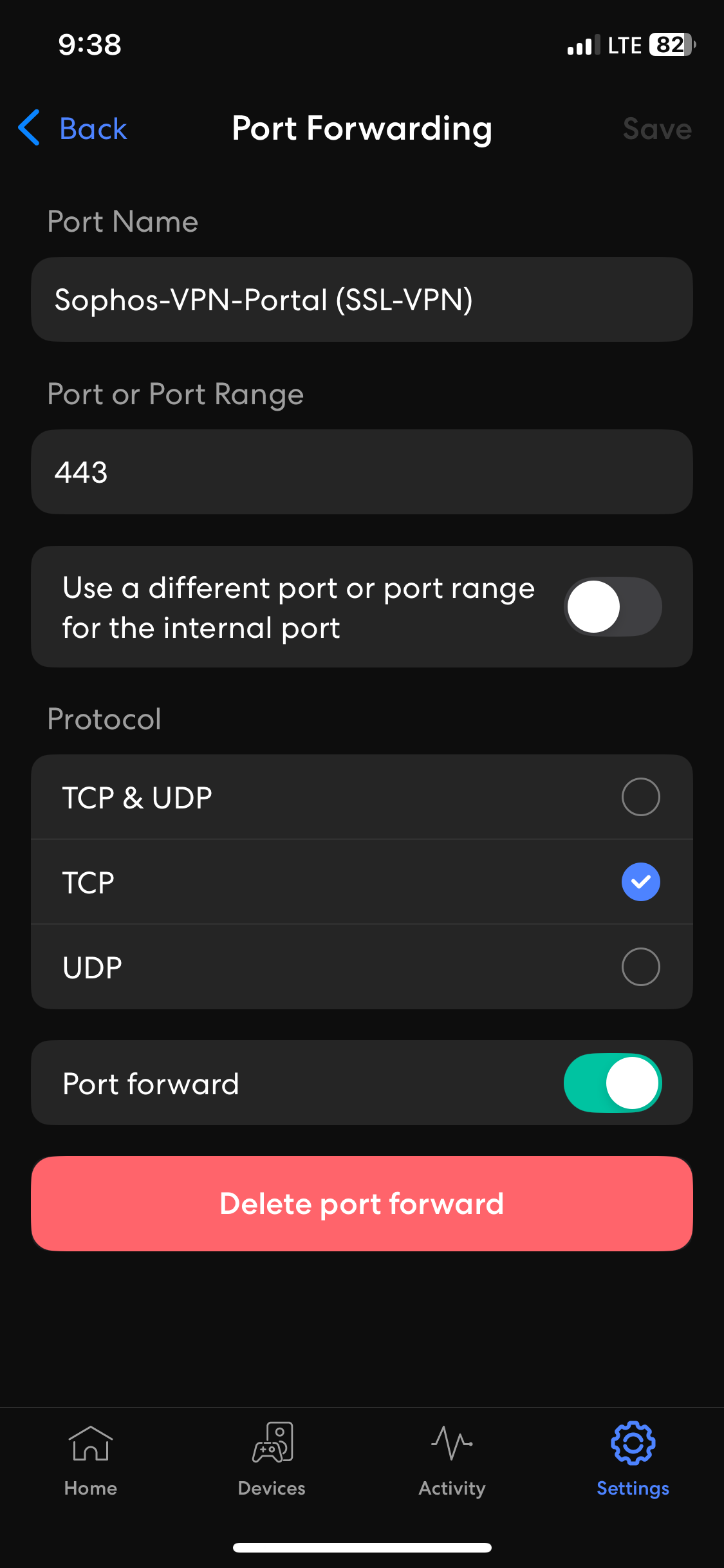
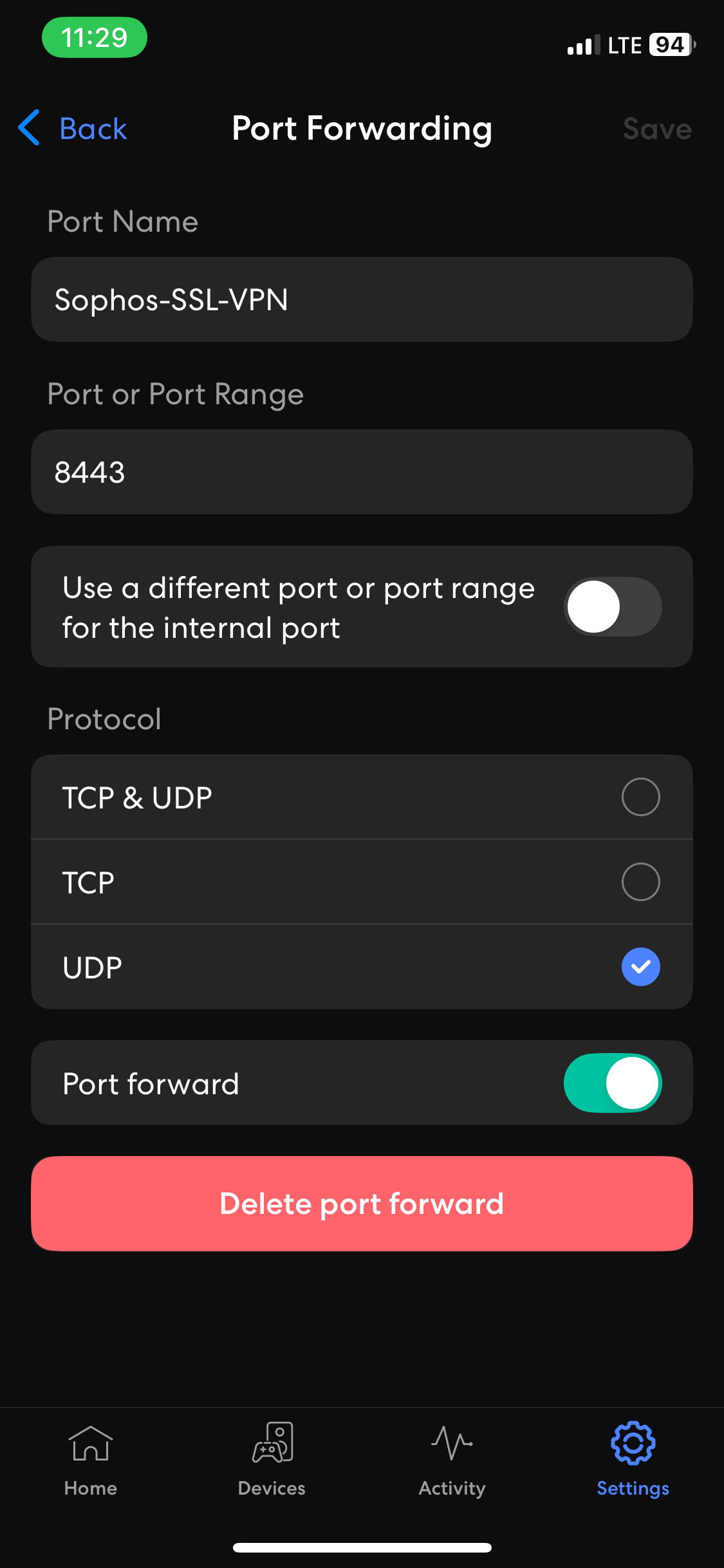
- For Sophos Remote Access VPN solution, (TCP port 443) and (UDP port 8443) are opened and used by the Sophos Firewall (TCP 443 for the VPN portal accessible from the WAN and VPN zones) and (UDP 8443 for the SSL VPN (HTTPS) protocol)
SSL VPN Topology

Port Forwarding Setup
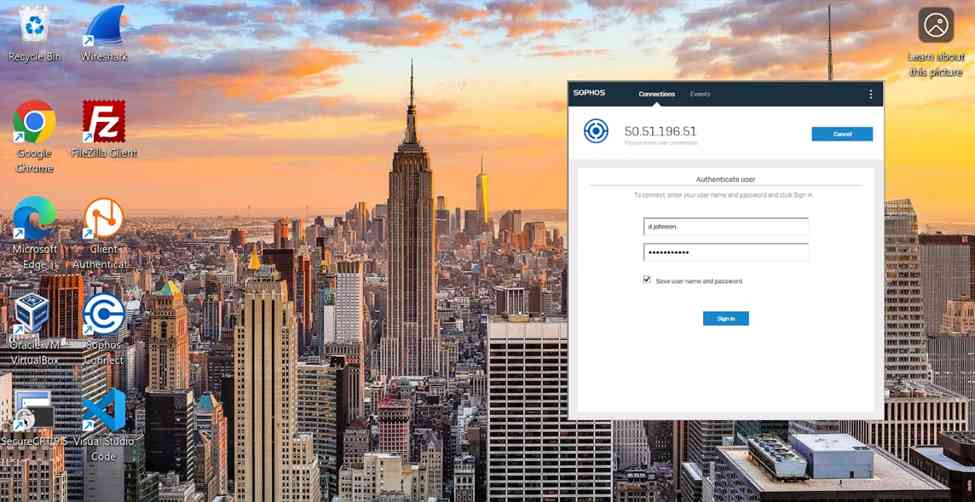
Windows Sophos Connect Client
Overview
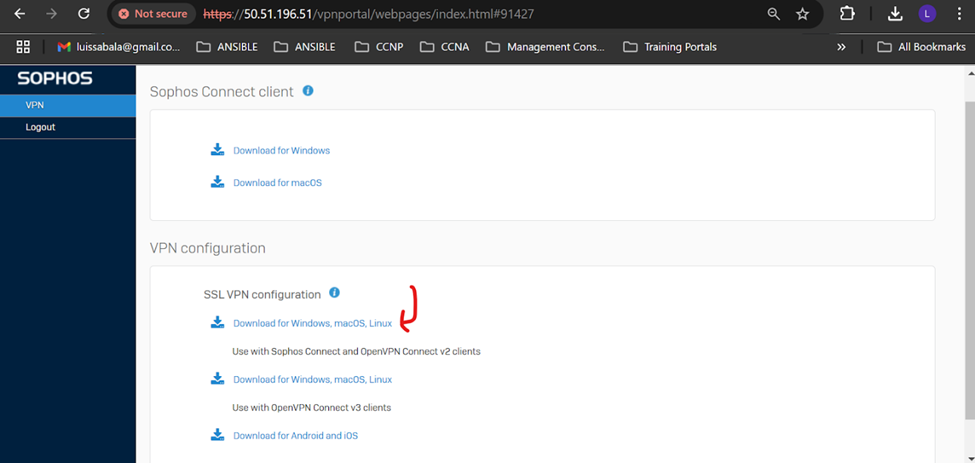
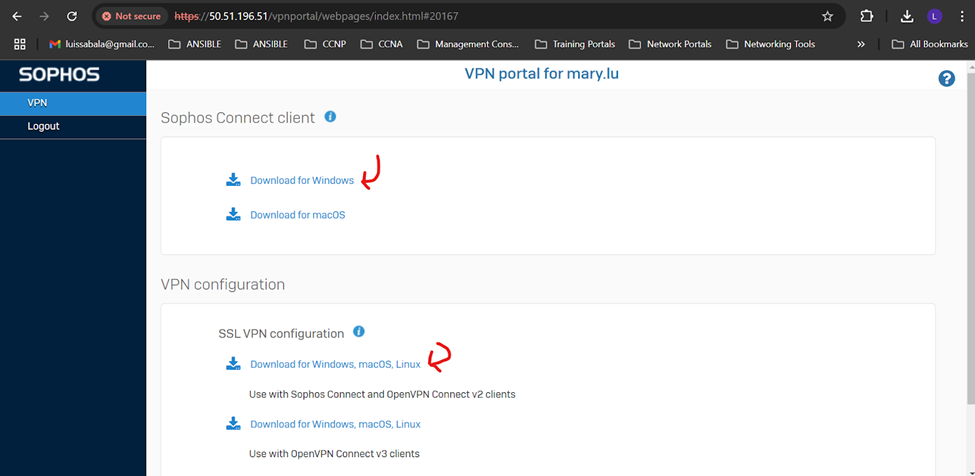
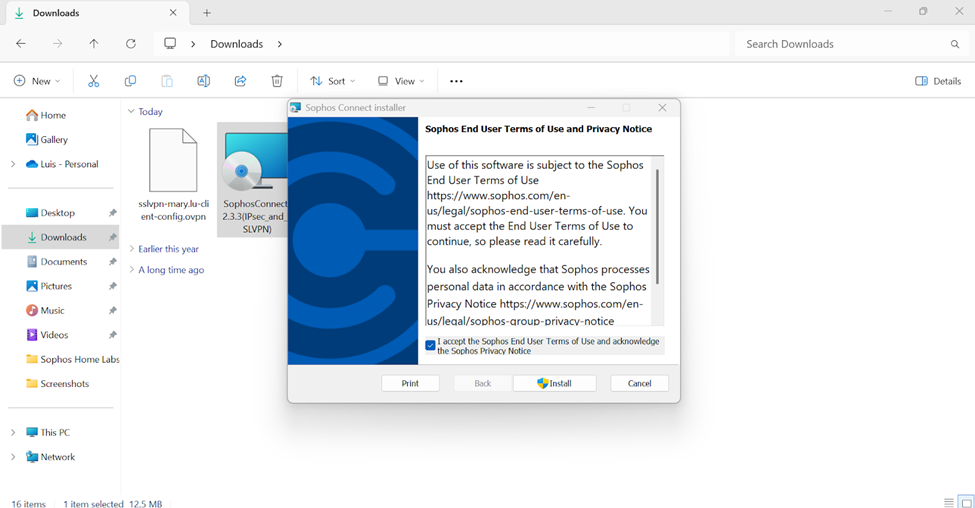
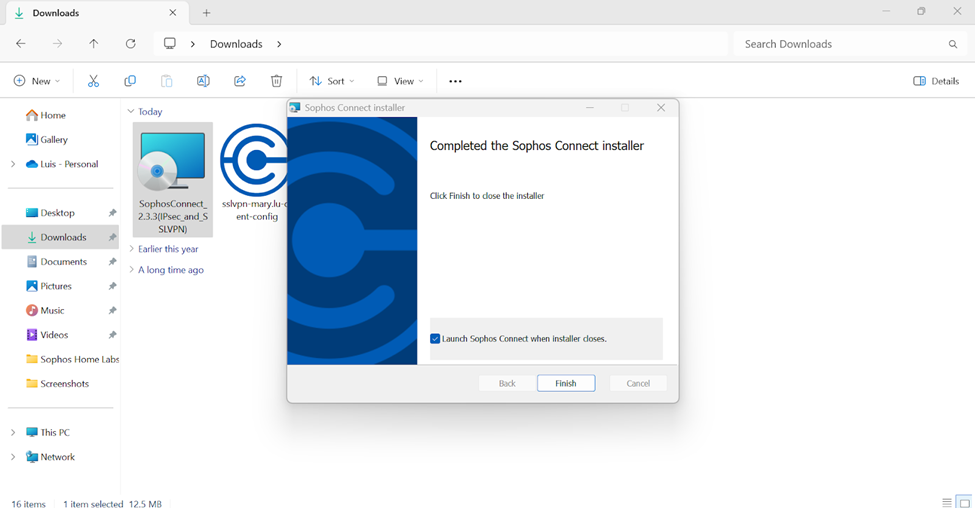
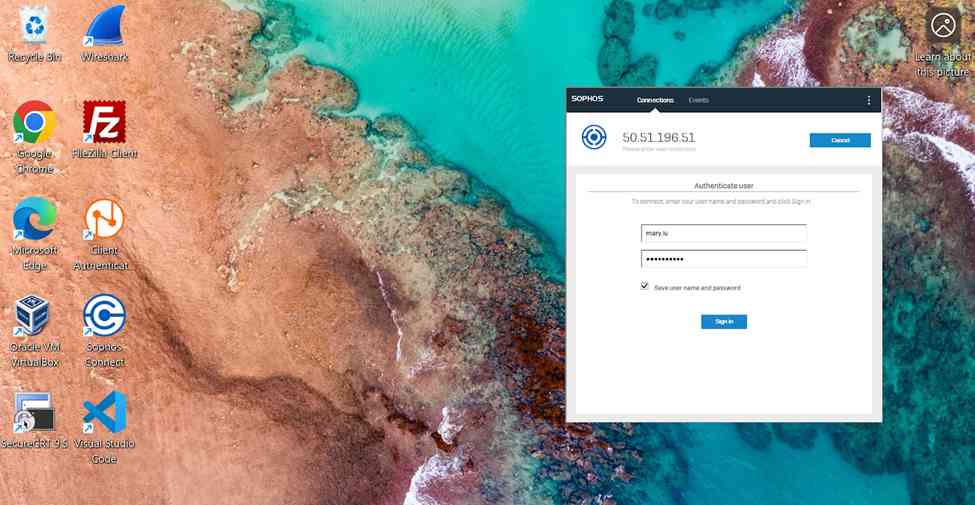
- To establish remote access SSL VPN connections, users must install the Sophos Connect client on their endpoint devices and import the '.ovpn' file to the client
- You can download the Sophos Connect client installer from the Sophos Firewall web admin console and share it with users
- Alternatively, users can download the Sophos Connect client from the User or VPN portal
- Sophos Connect client: Compatibility with platforms
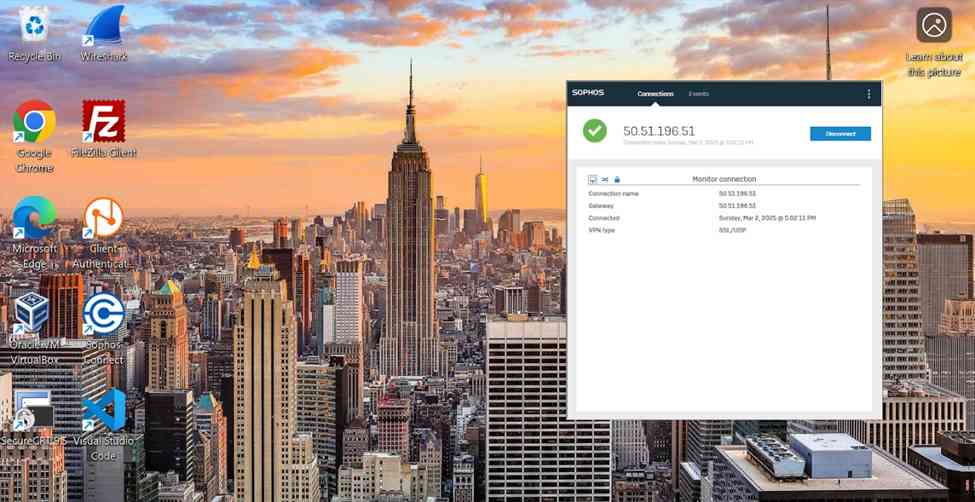
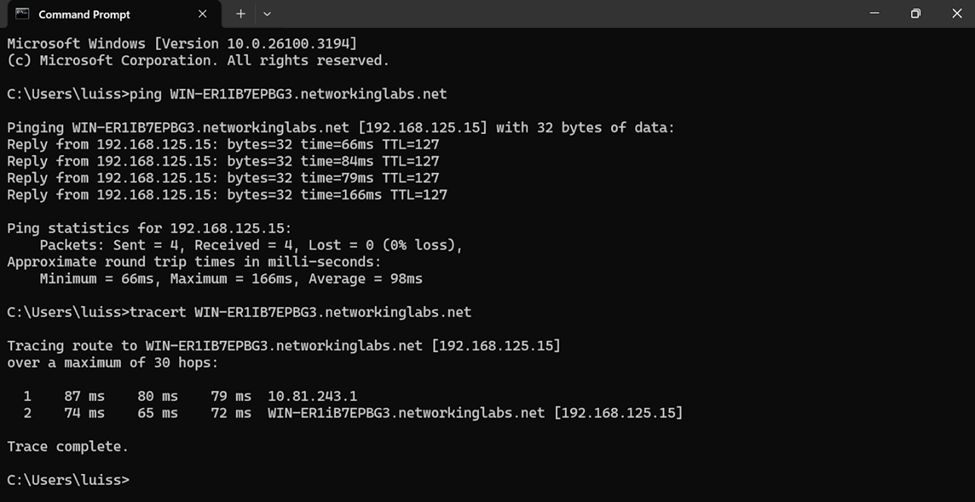
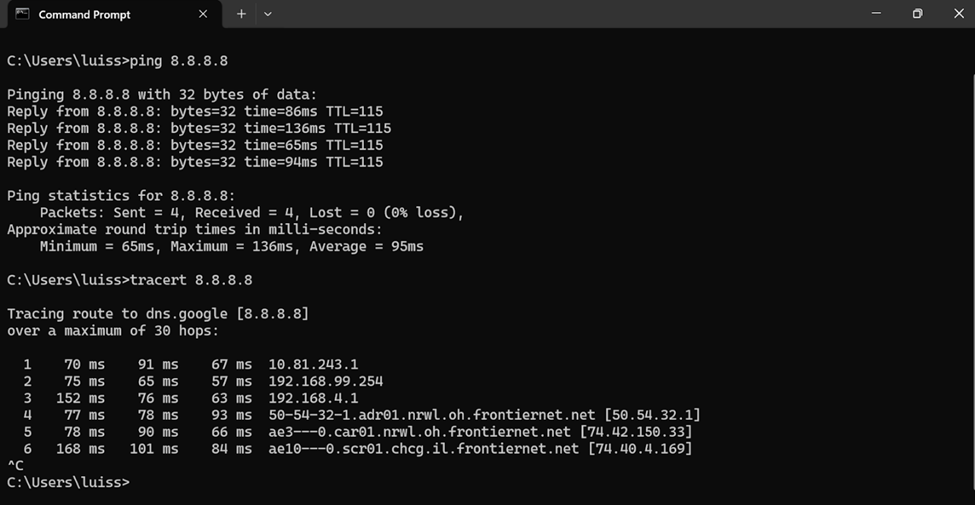
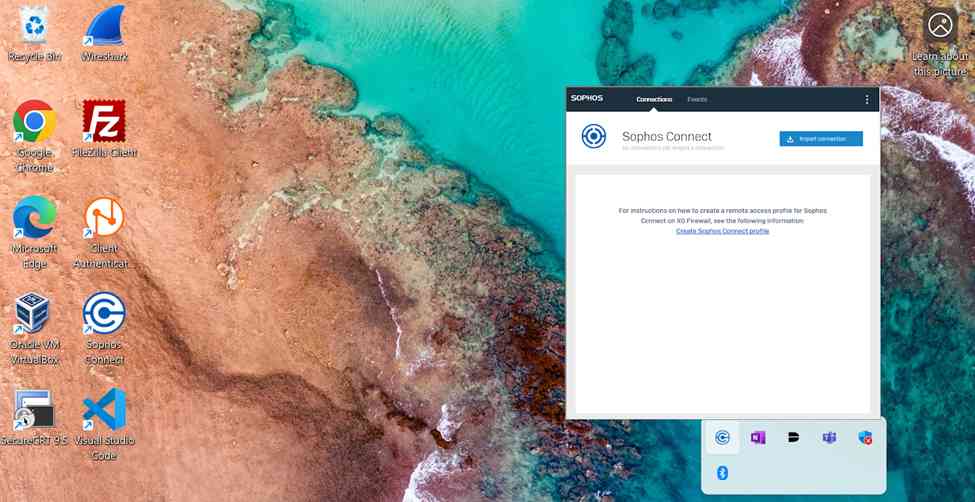
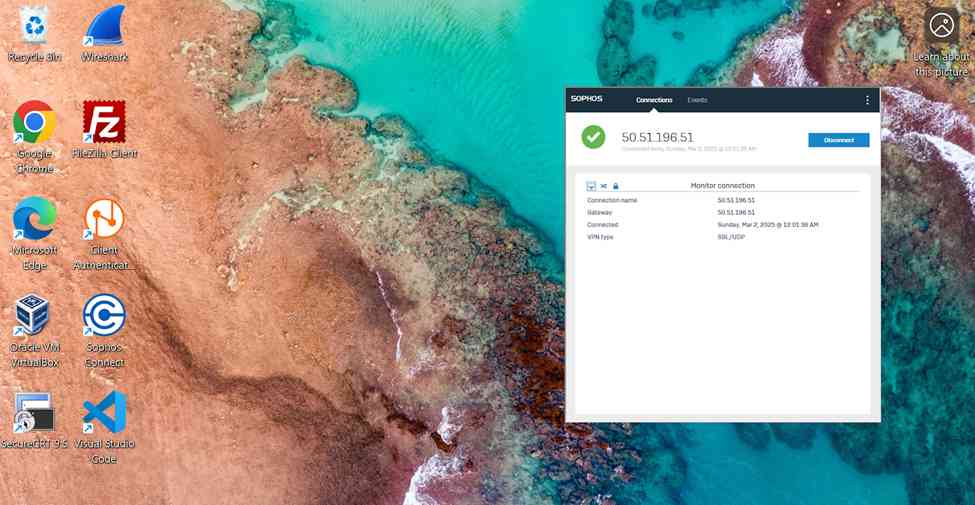
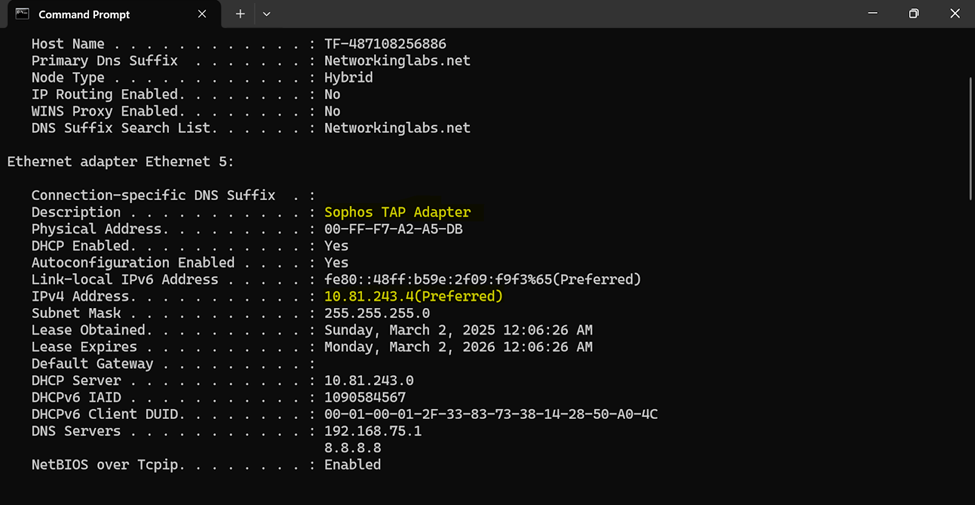
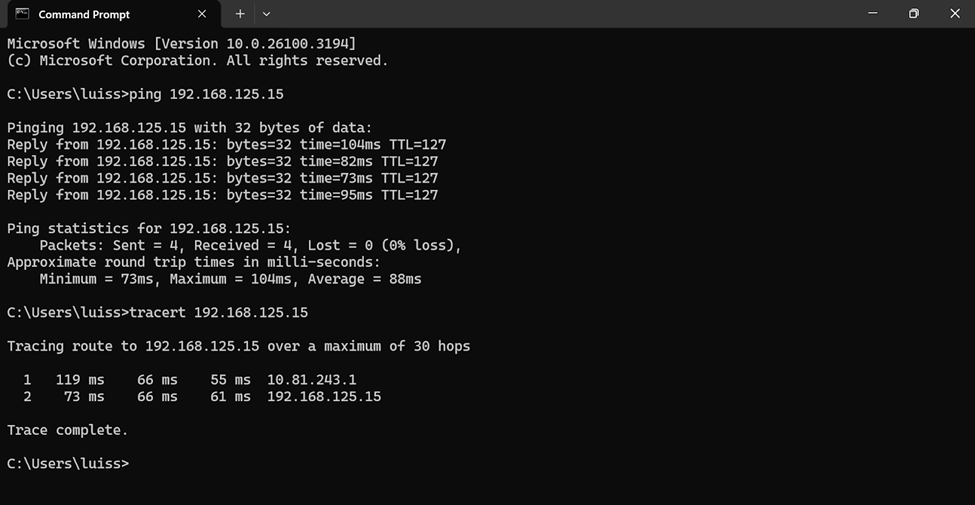
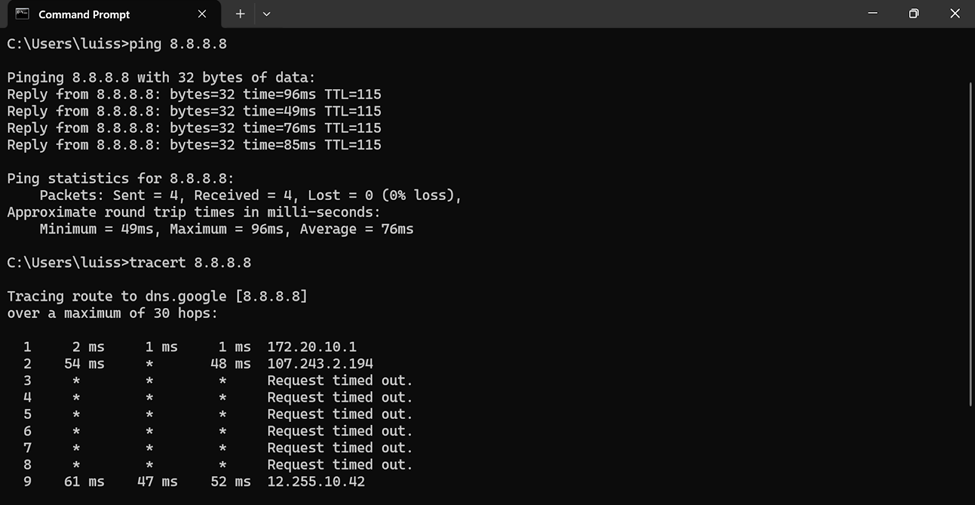
- In this demonstration, I will be installing the Sophos Connect client and importing the configuration file on a Windows machine and verifying connectivity to the Corporate site Servers LAN through the VPN and access to the WAN in a Split tunnel VPN deployment
SSL VPN Topology

Sophos Connect Client Installation


IOS OpenVPN Client
Overview
- Currently, the Sophos Connect client doesn't support IOS (IPhone) or Android devices for SSL VPN and as a workaround, it is recommended that users use the OpenVPN Connect client
- OpenVPN is a free, open-source VPN protocol that encrypts Internet traffic to protect online privacy and is compatible with many operating systems and devices
- Alternatively, users can download from a variety of OpenVPN third party software options
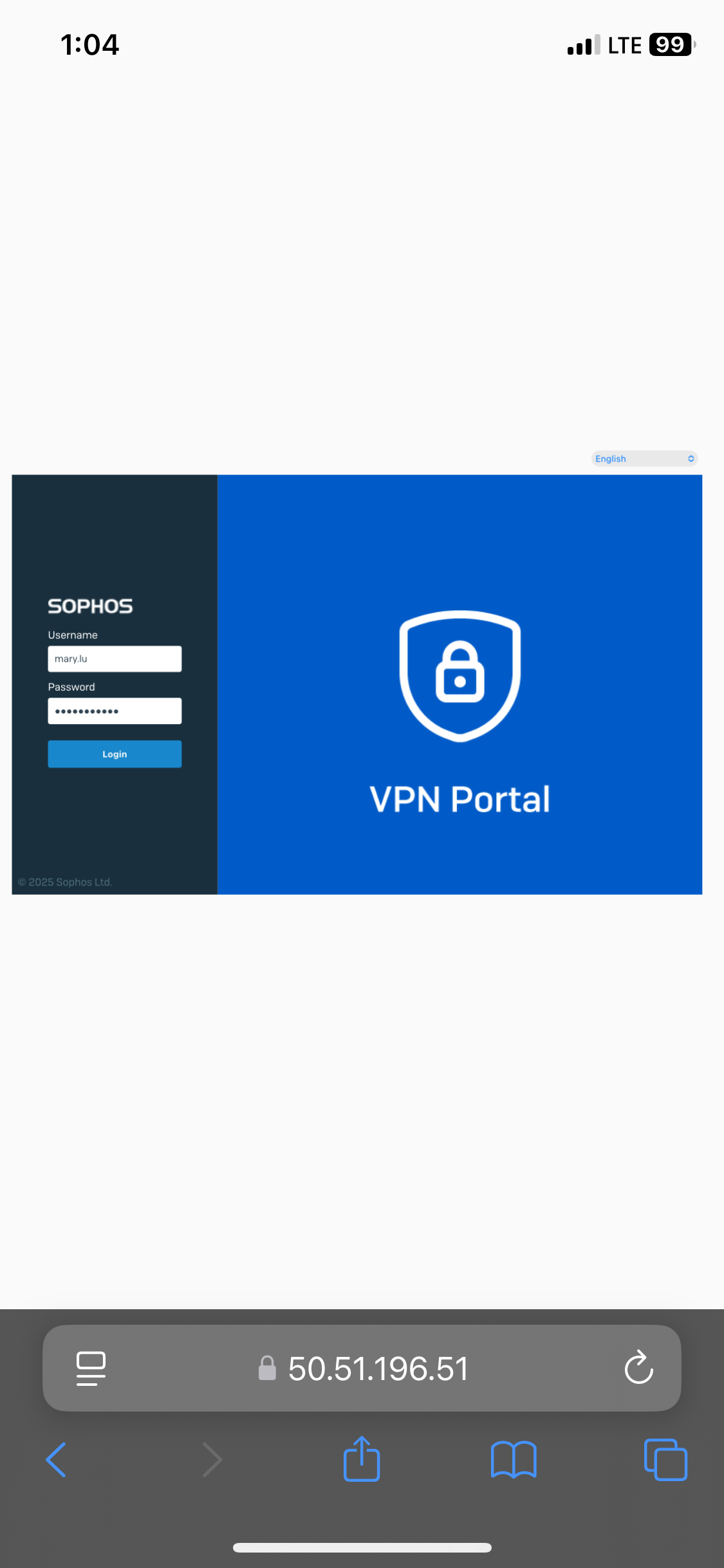
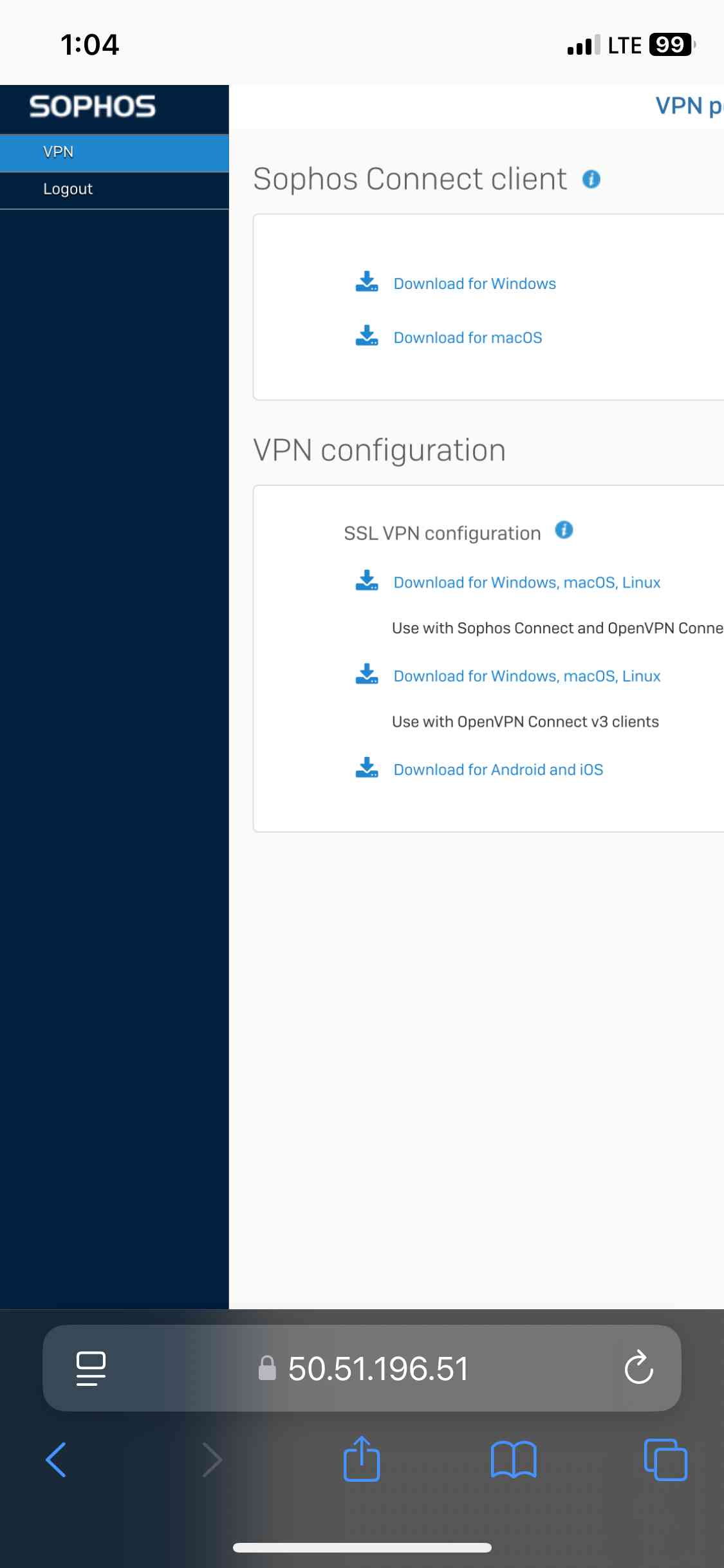
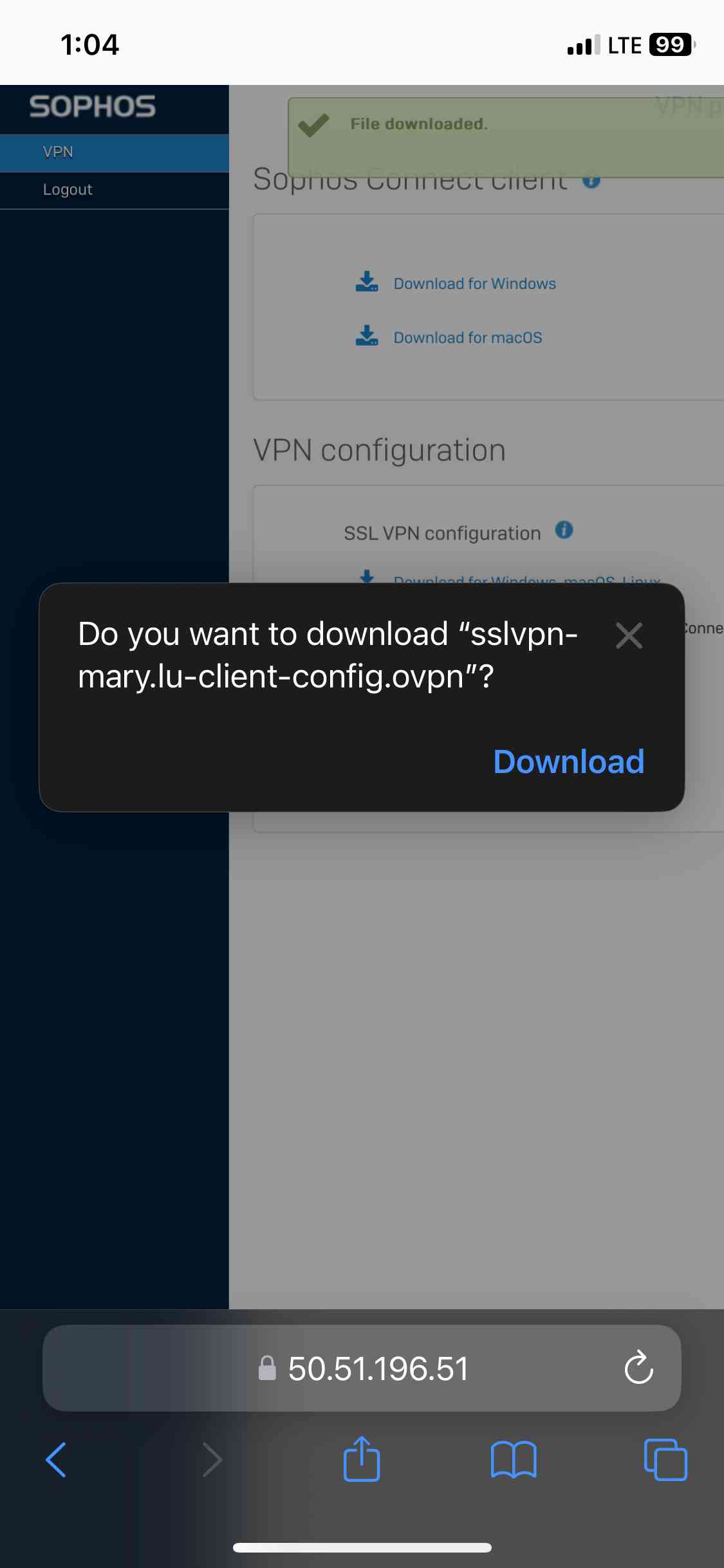
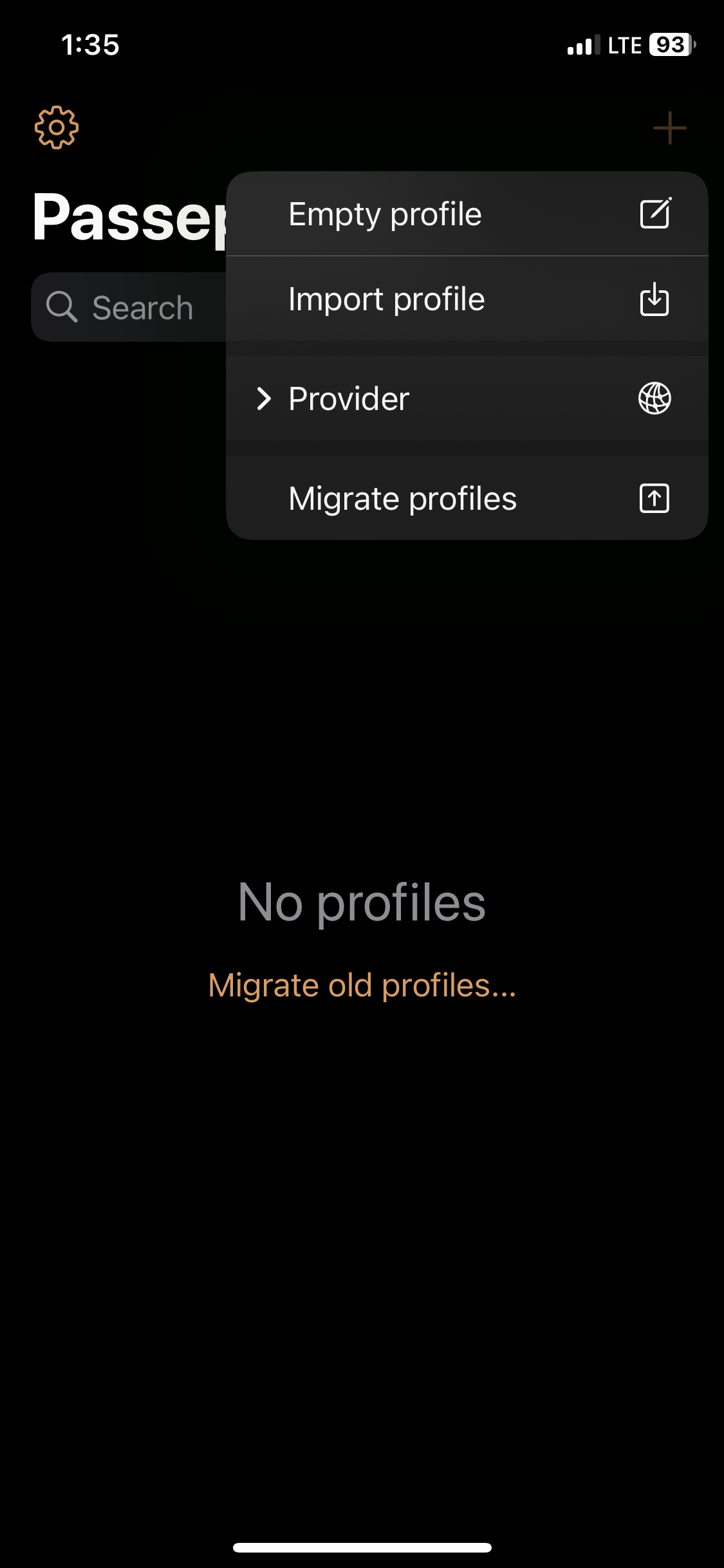
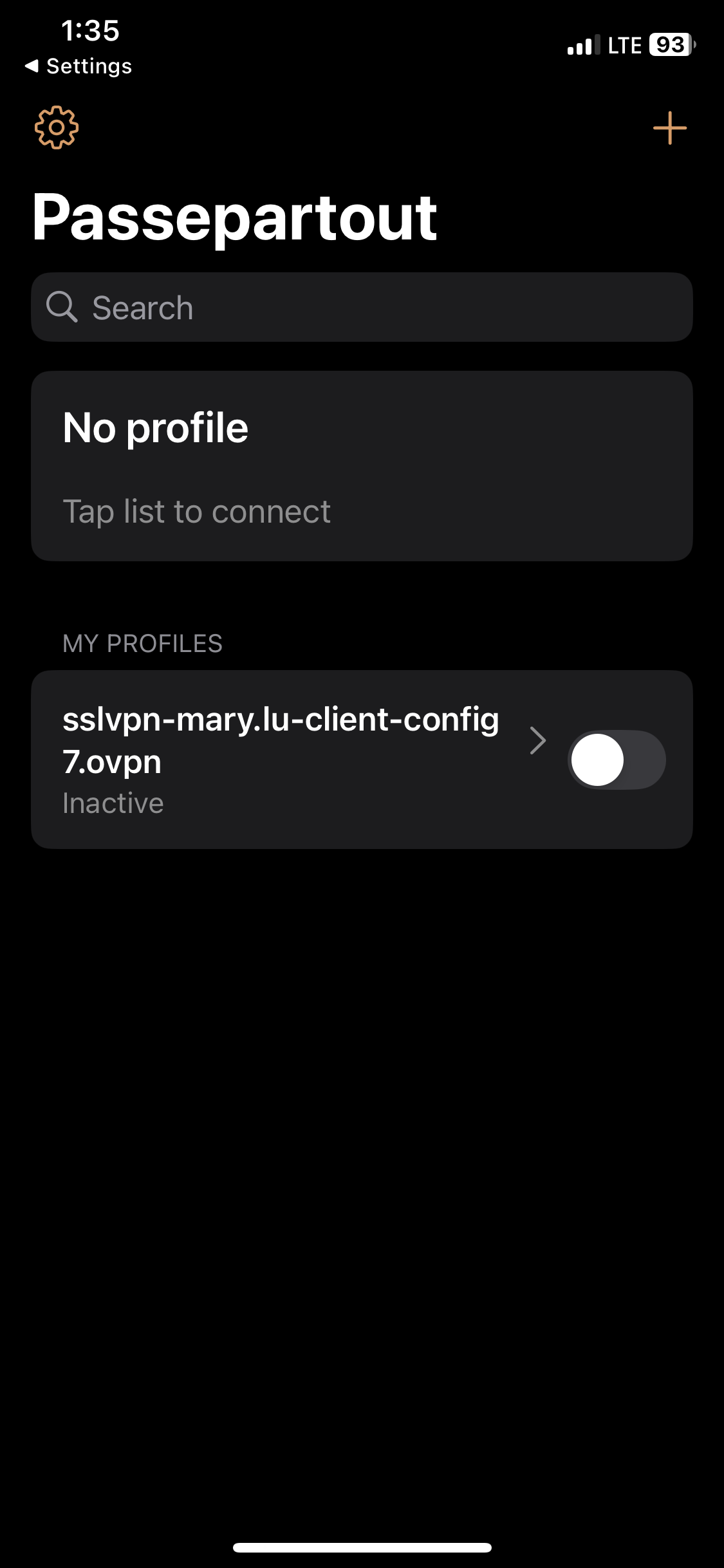
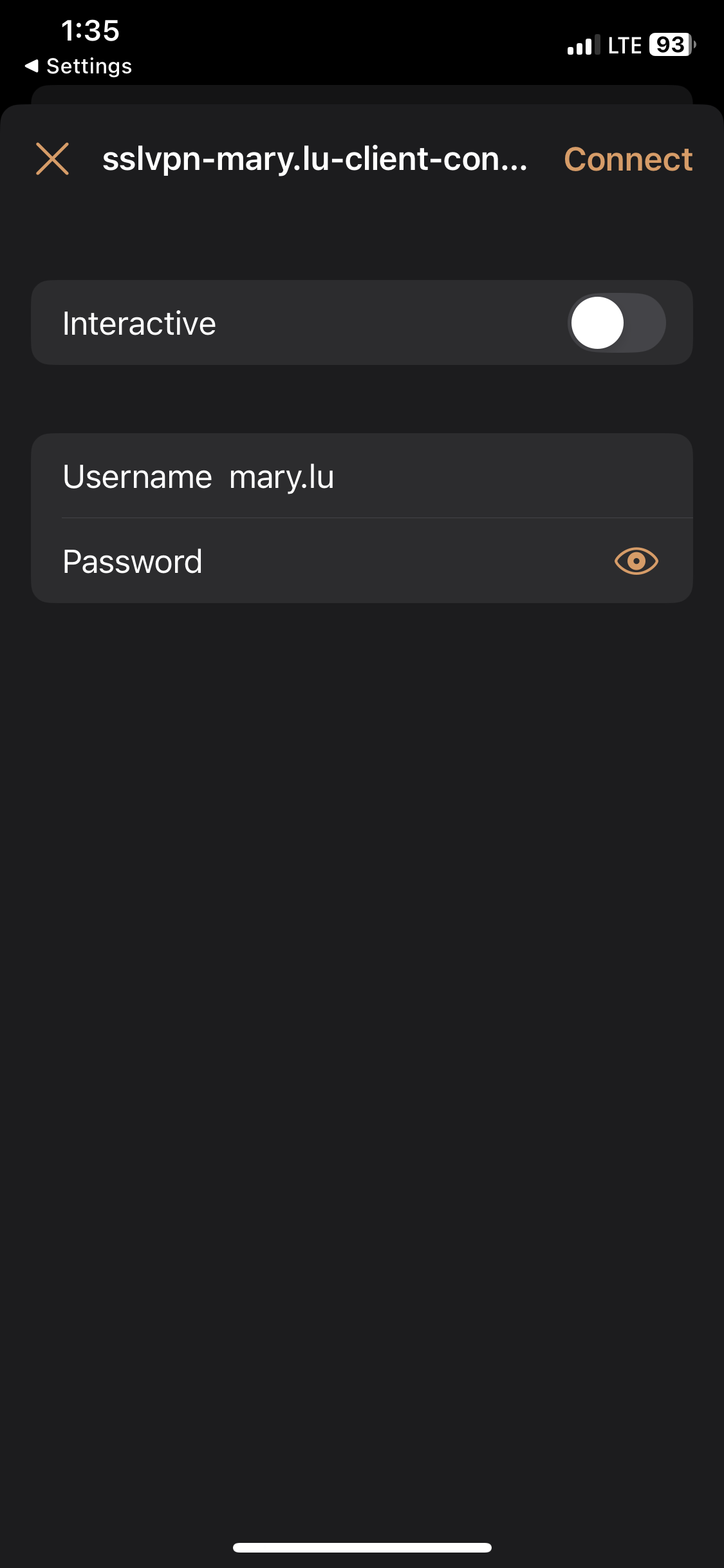
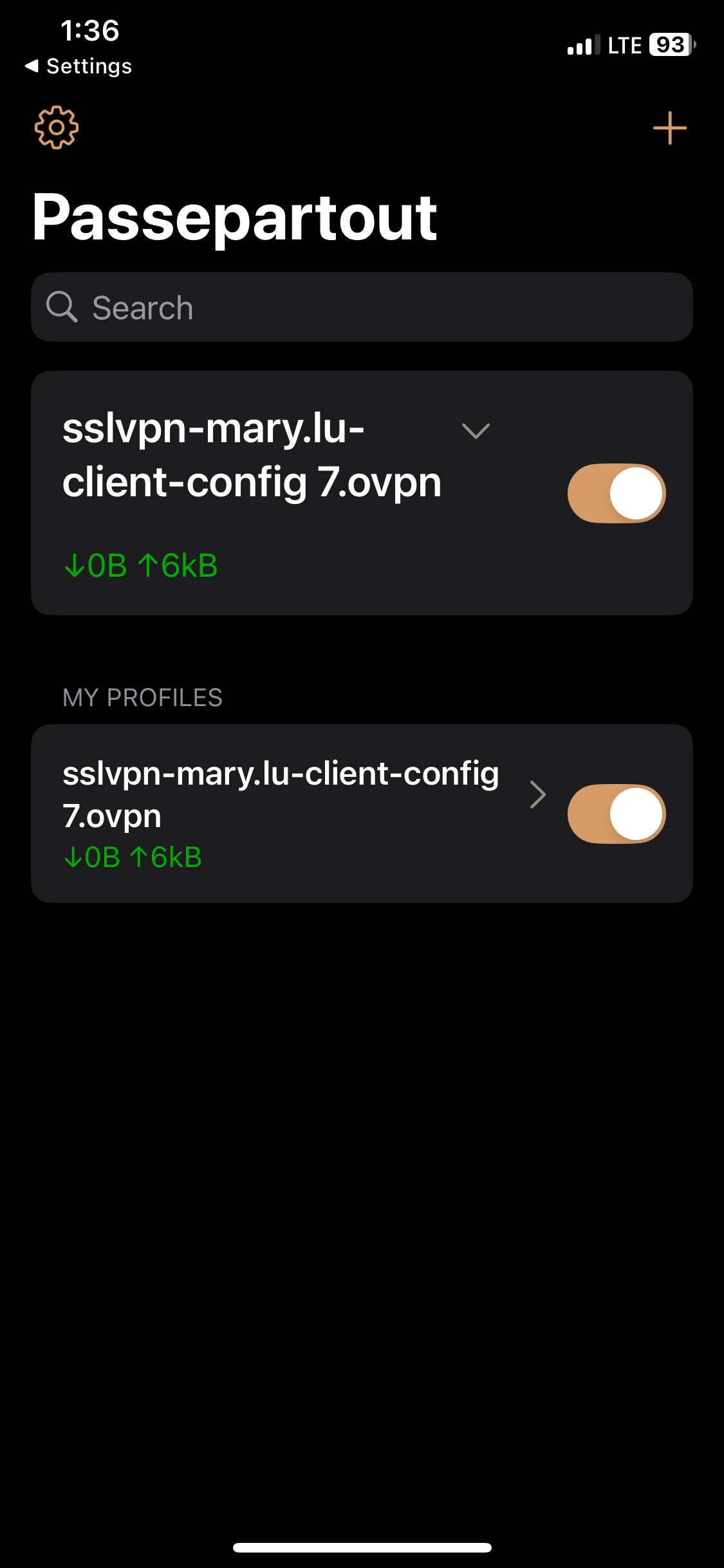
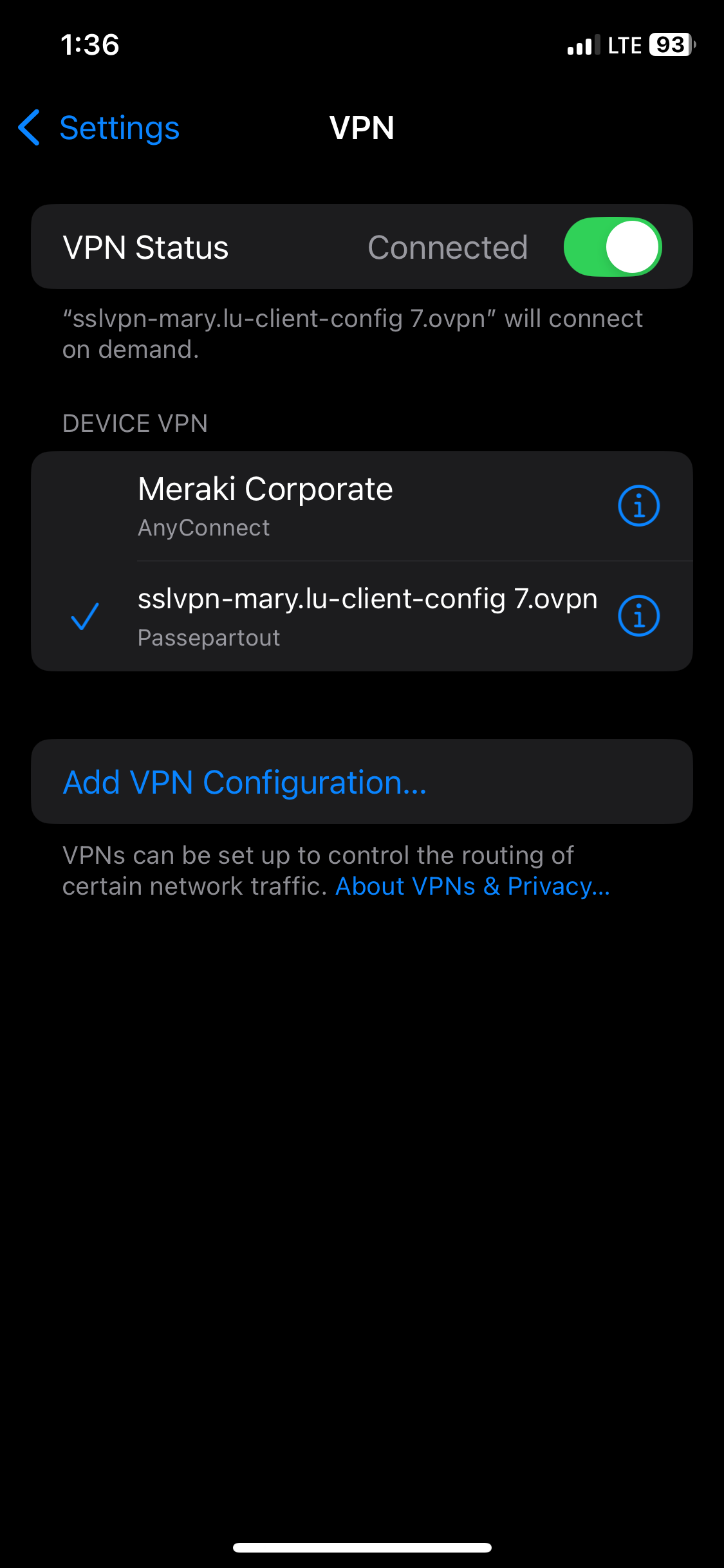
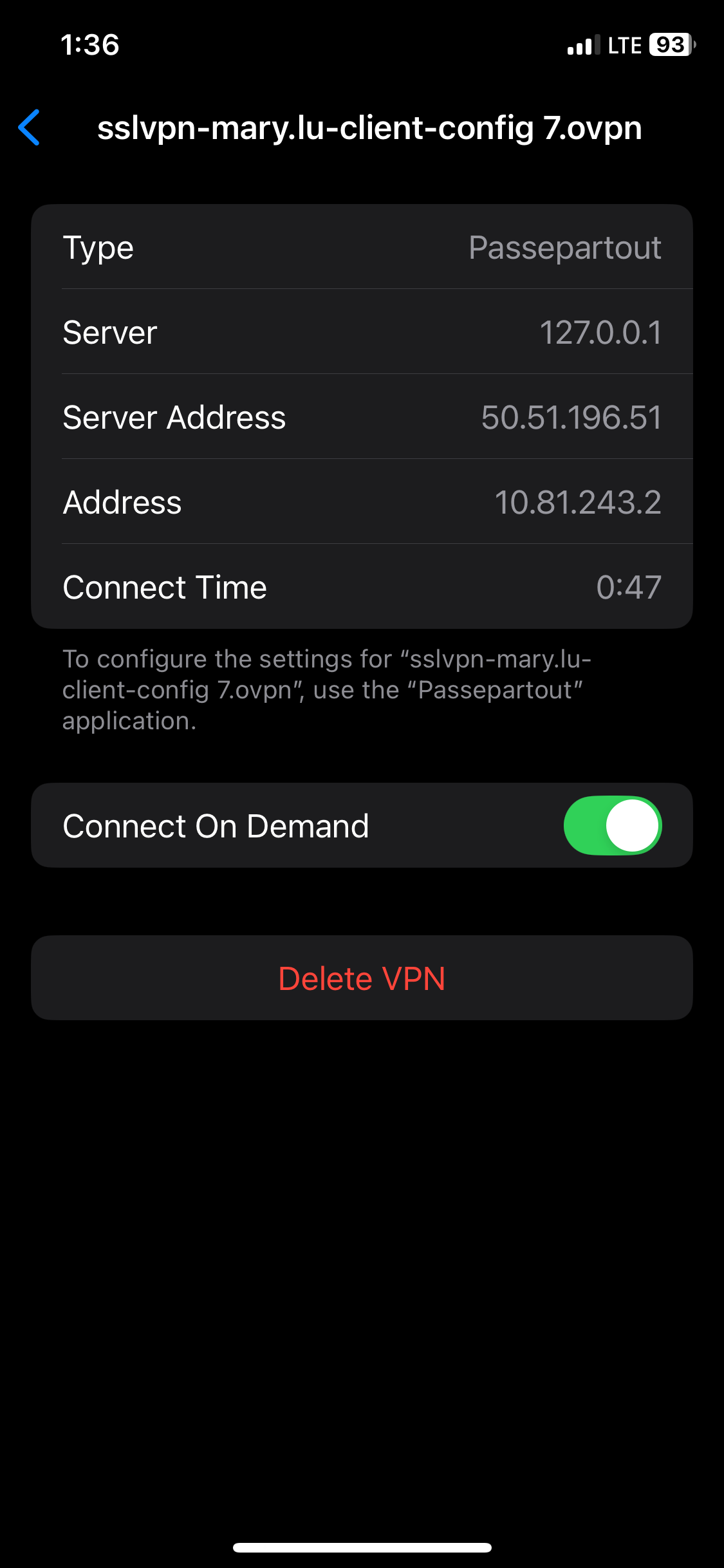
- In this demonstration, I will be downloading the '.ovpn' configuration file from the Sophos VPN portal and importing it to the Passepartout OpenVPN client on an Iphone device
- Common OpenVPN Clients:
- Apple Platform: Passepartout
- Multi Platform: OpenVPN Connect
- Windows Platform: Securepoint
SSL VPN Topology

OpenVPN Client Installation
Adding a Windows File Server
Overview
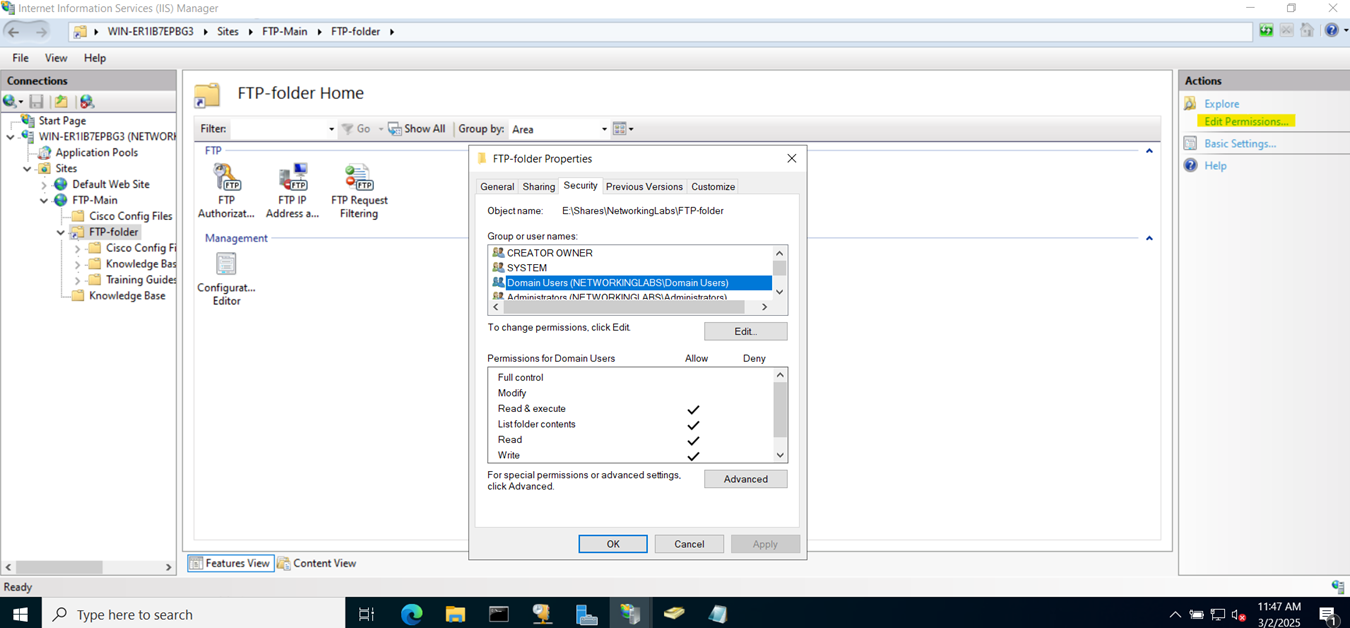
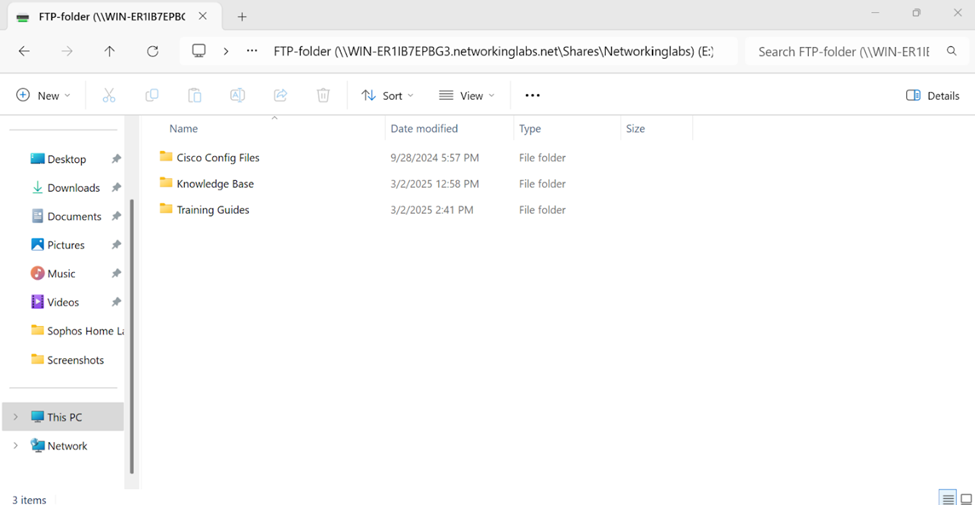
- In this section, I will be allowing SSL VPN clients to access a File server located in the Corporate site LAN
- With SSL VPN policies, you can specify the permitted network resources including any servers clients will need the ability to access remotely
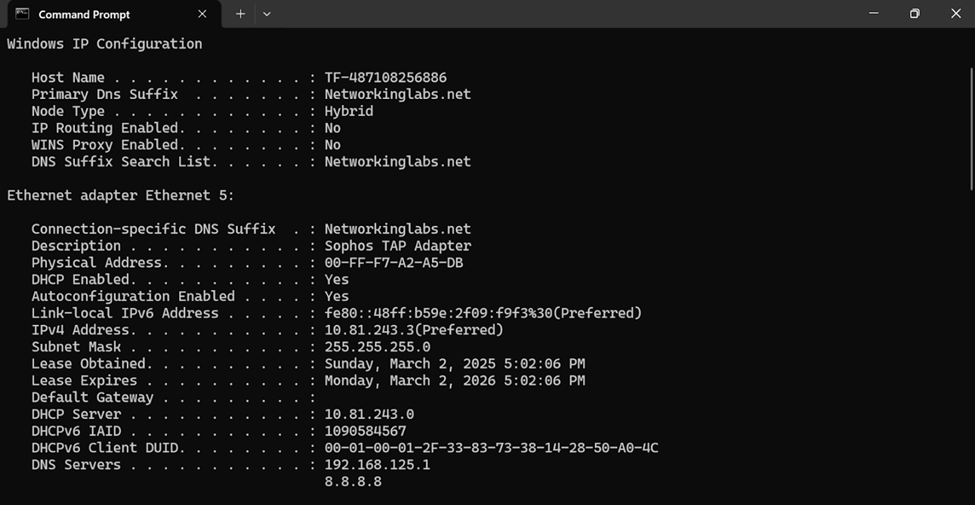
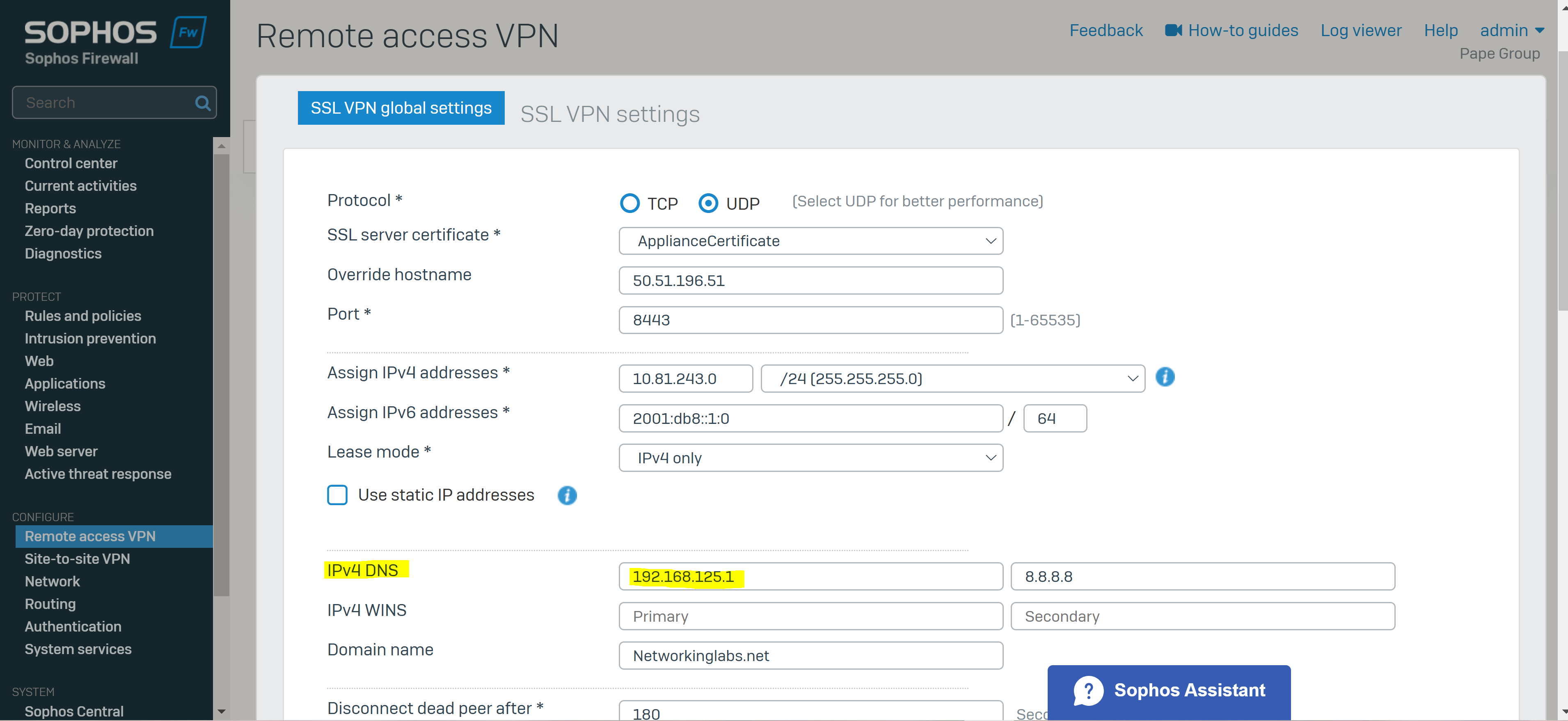
- In this demonstration, the Sophos Firewall acting as the VPN server gateway to the internal network will also be configured to act as a DNS server for the SSL VPN clients
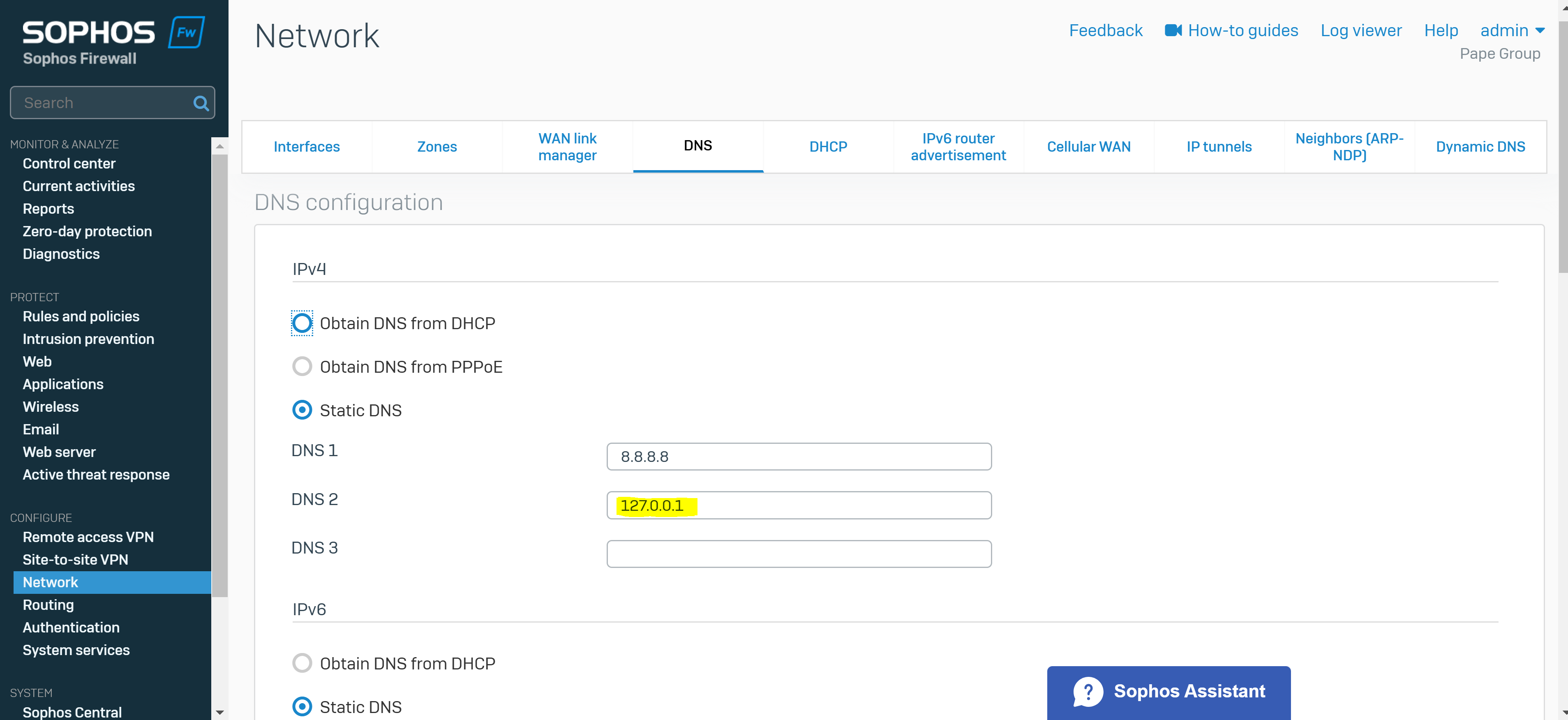
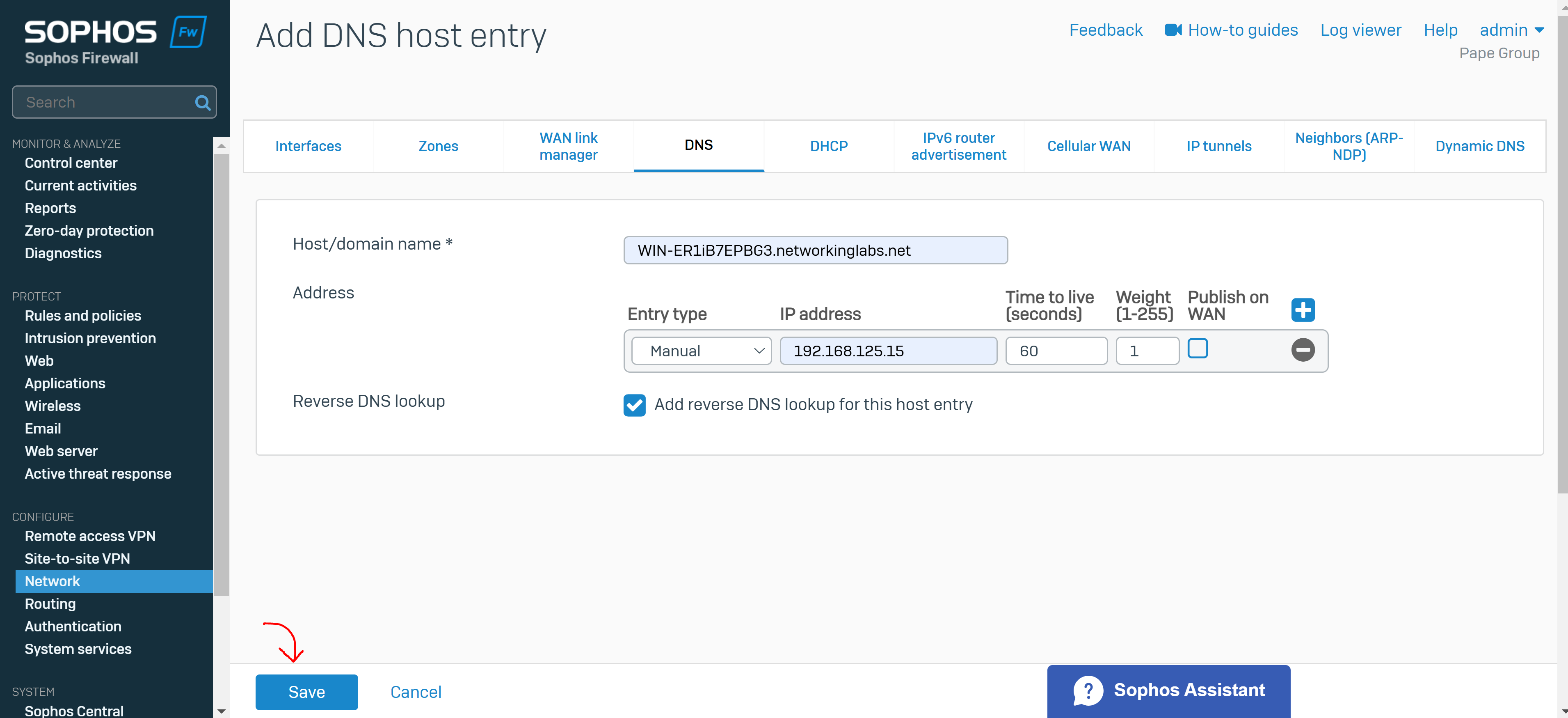
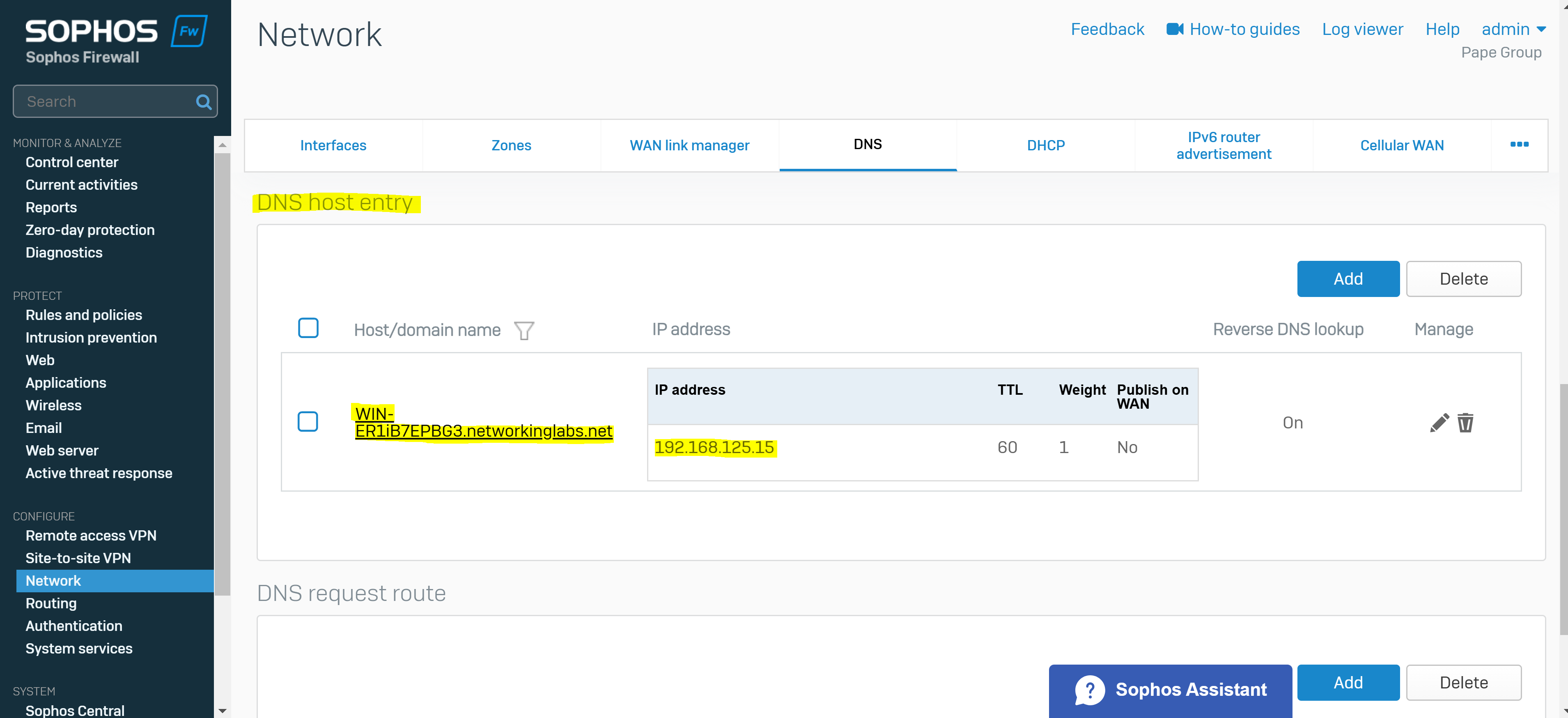
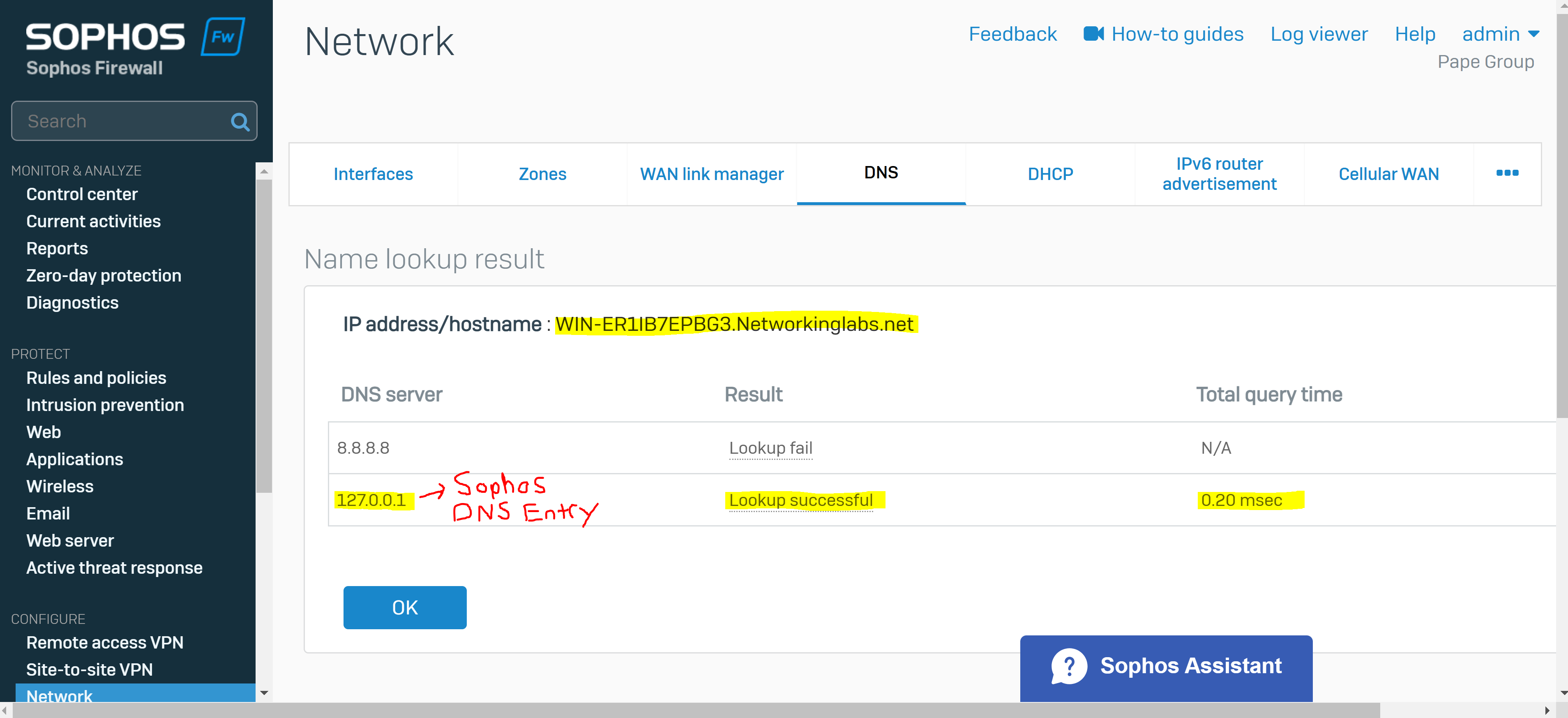
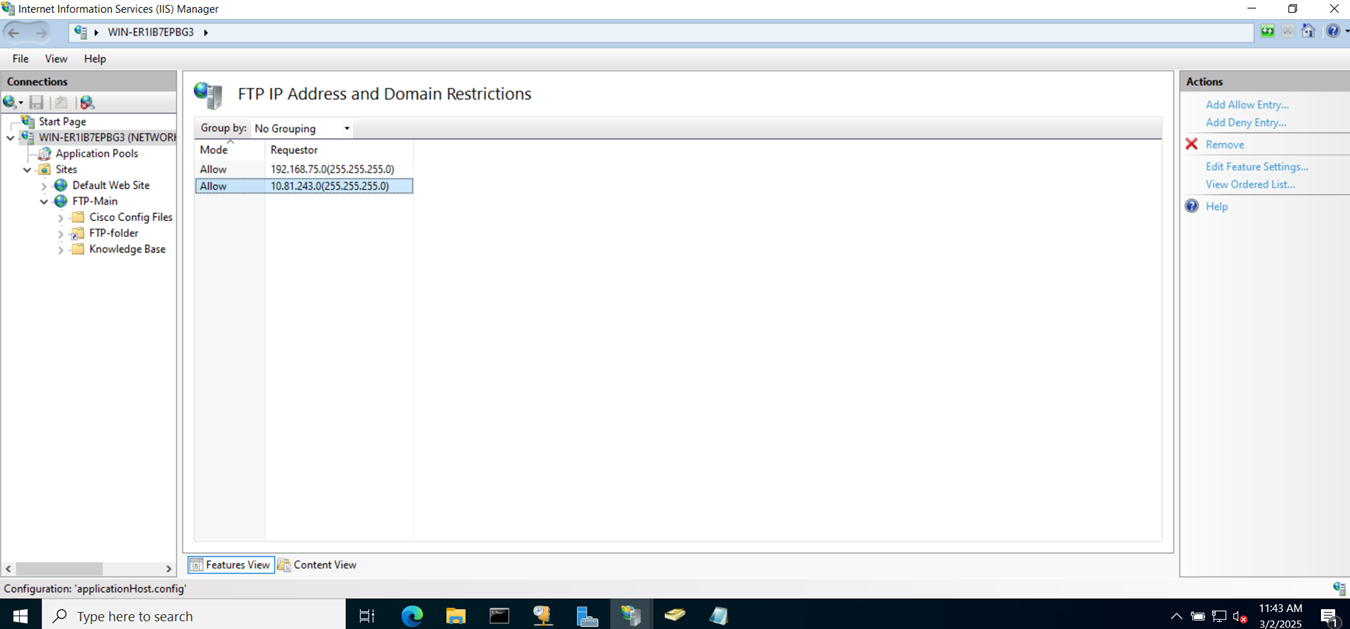
- With Sophos DNS host entries, you can resolve requests for specific hosts or domain names. If the host requested by the user matches the DNS host entry, the Sophos Firewall resolves the query using the IP address specified
- It's important to note that any DNS servers that are to be accessible by the VPN clients, is specified in the 'Permitted network resources' under the SSL VPN policy
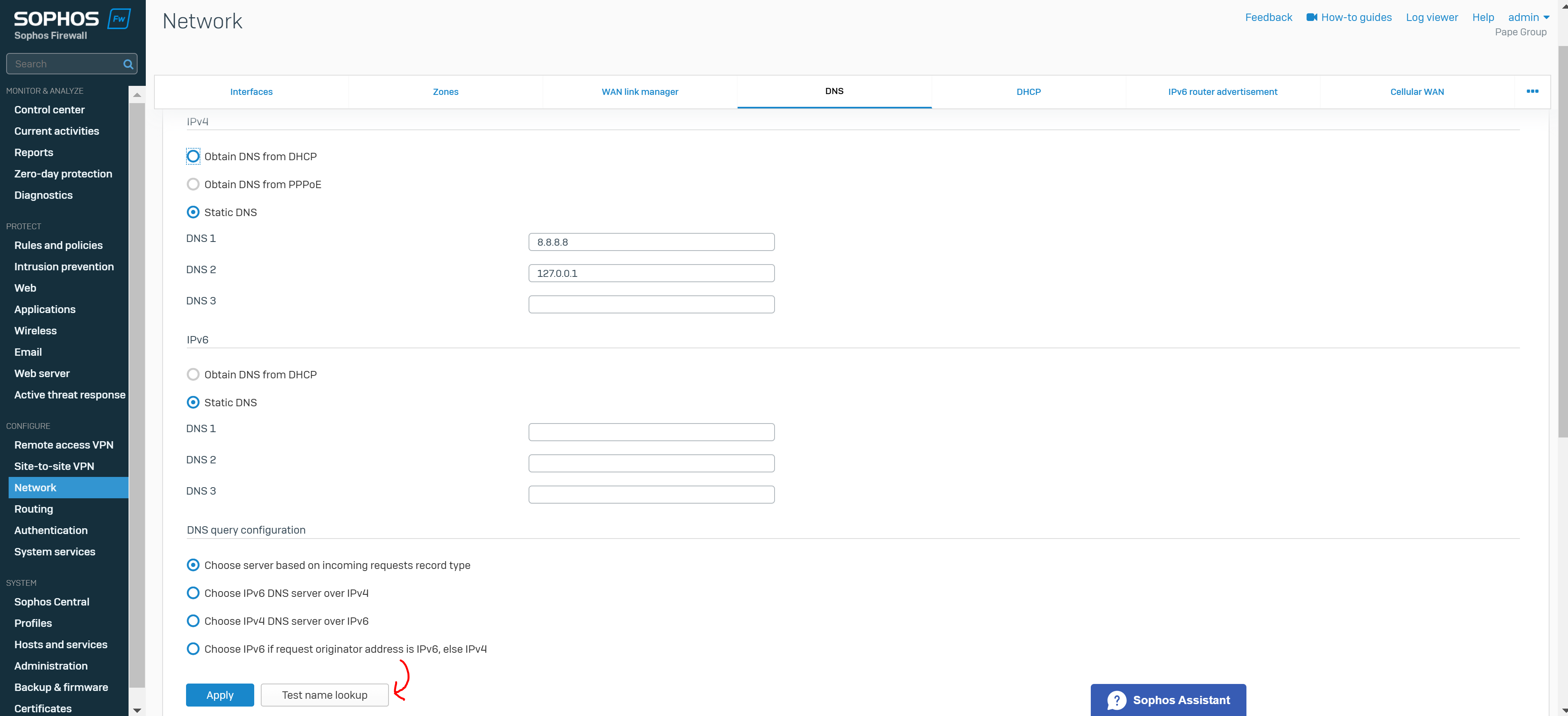
- It's also crucial you specify the Sophos Firewall as a DNS server itself under global DNS configuration in addition to any public DNS servers for WAN access
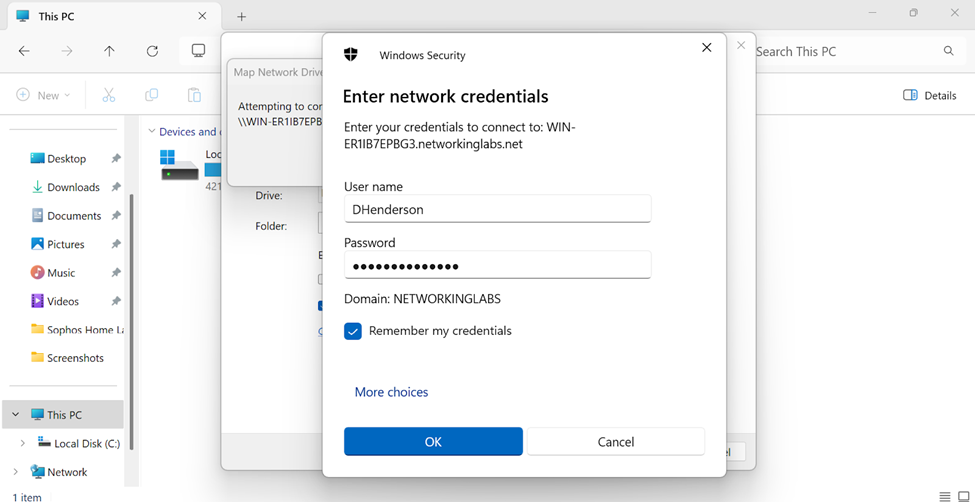
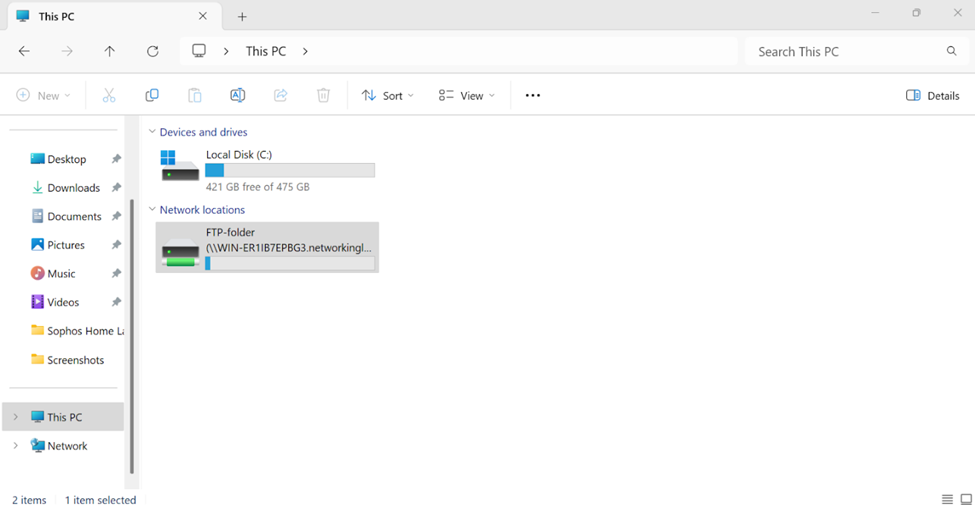
- Lastly, I will verify and add a network file share from a Windows connected VPN client to have the ability to access internal files through the VPN using Active Directory credentials
SSL VPN Topology
Sophos Firewall - DNS Host Entries
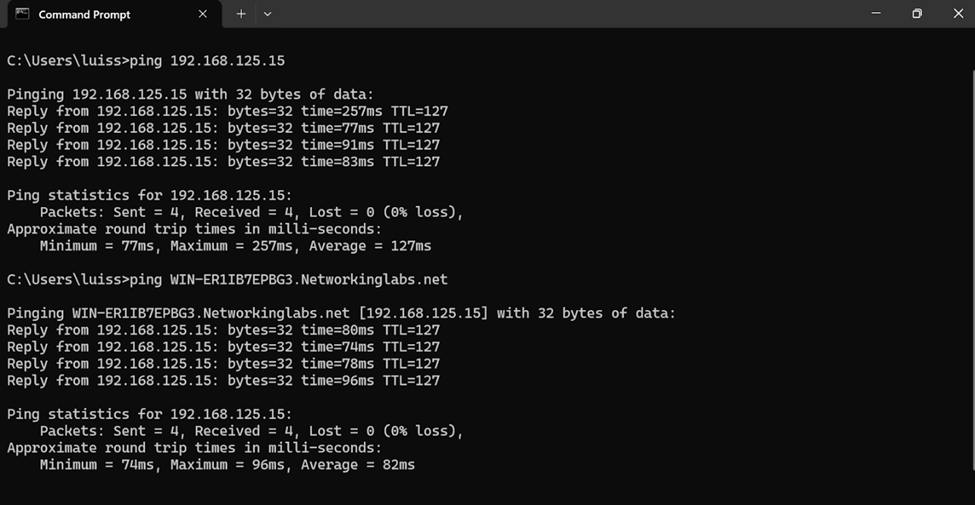
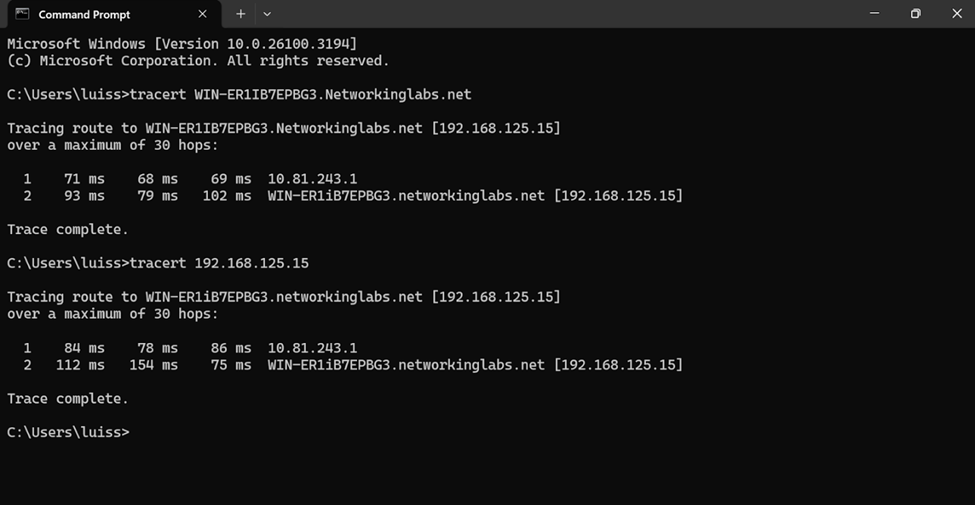
Windows Server FTP Configuration
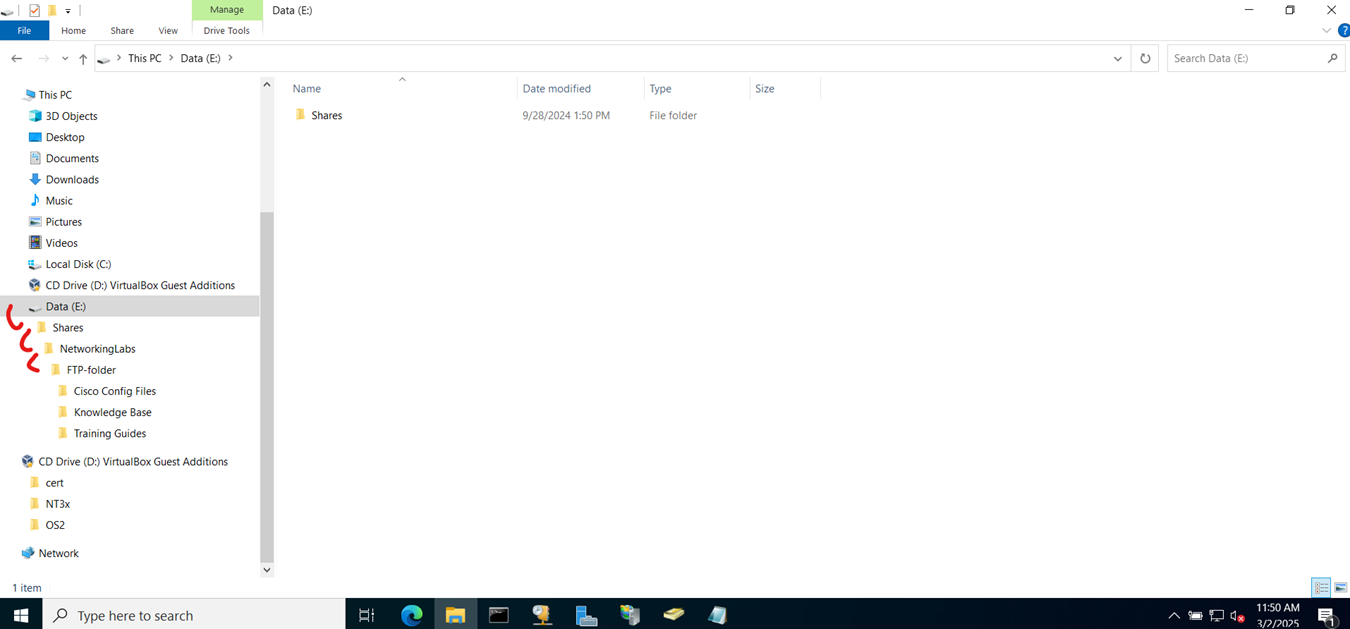
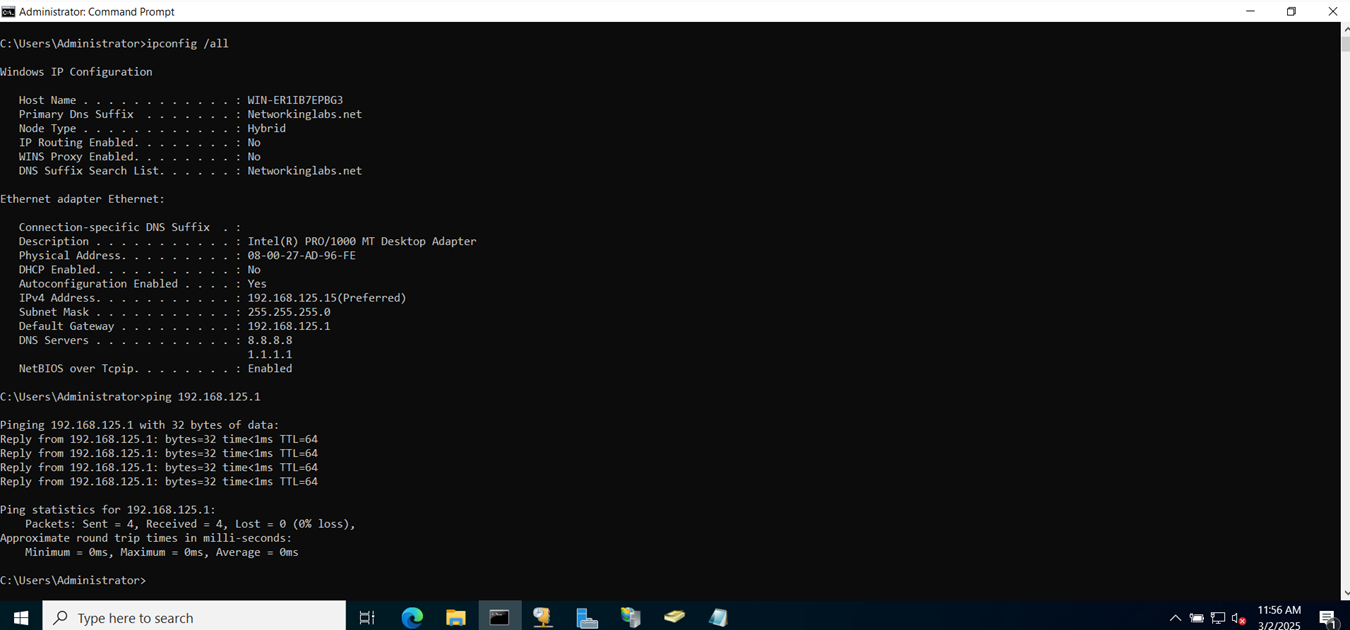
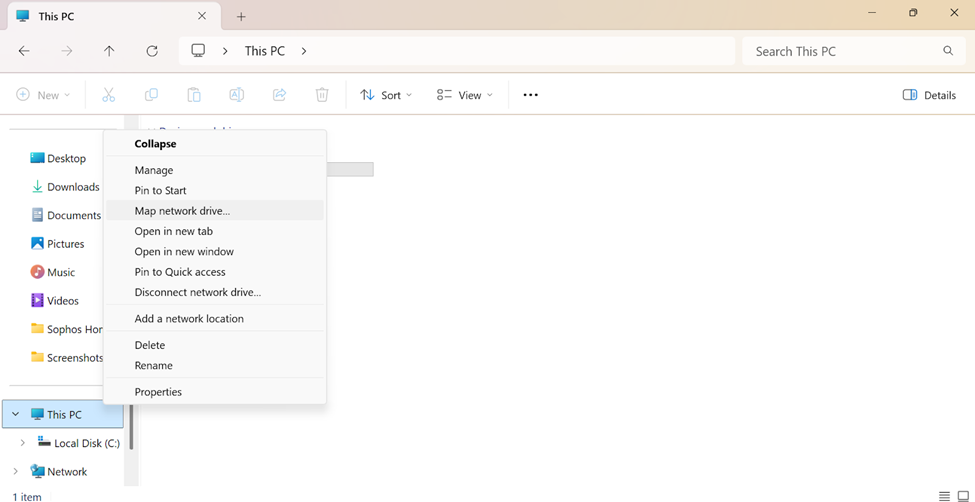
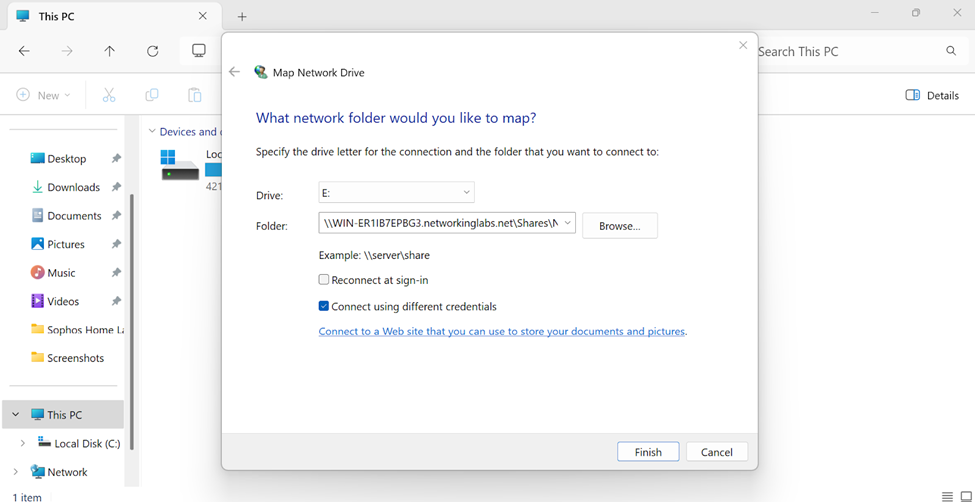
Adding File Shares to VPN Client
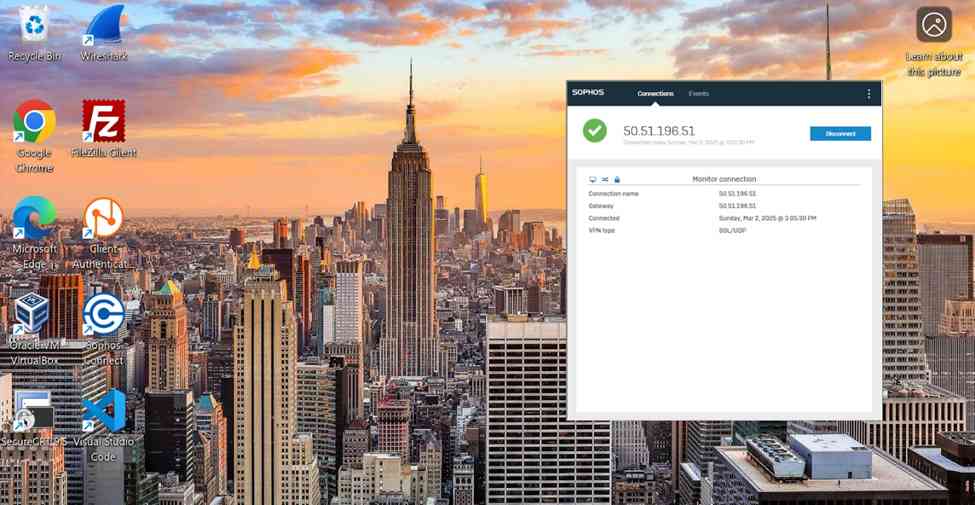
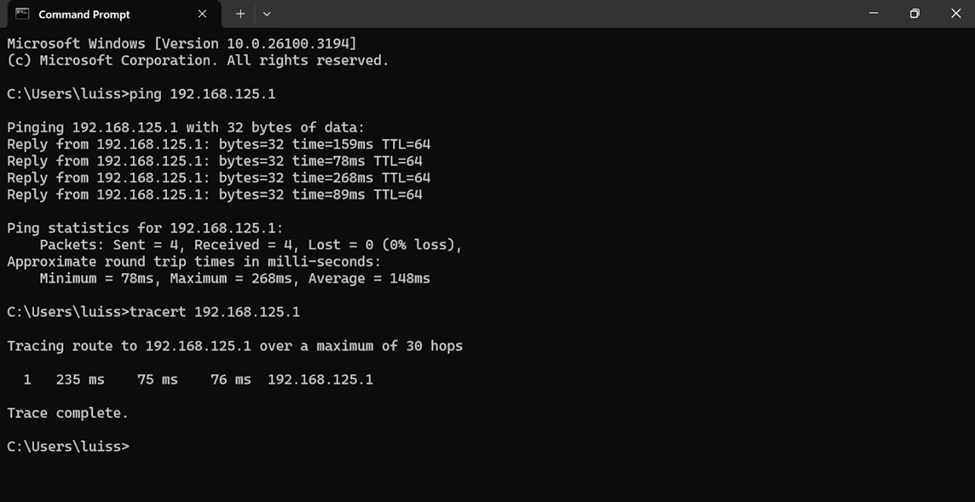
Configure SSL VPN as Full Tunnel
Overview
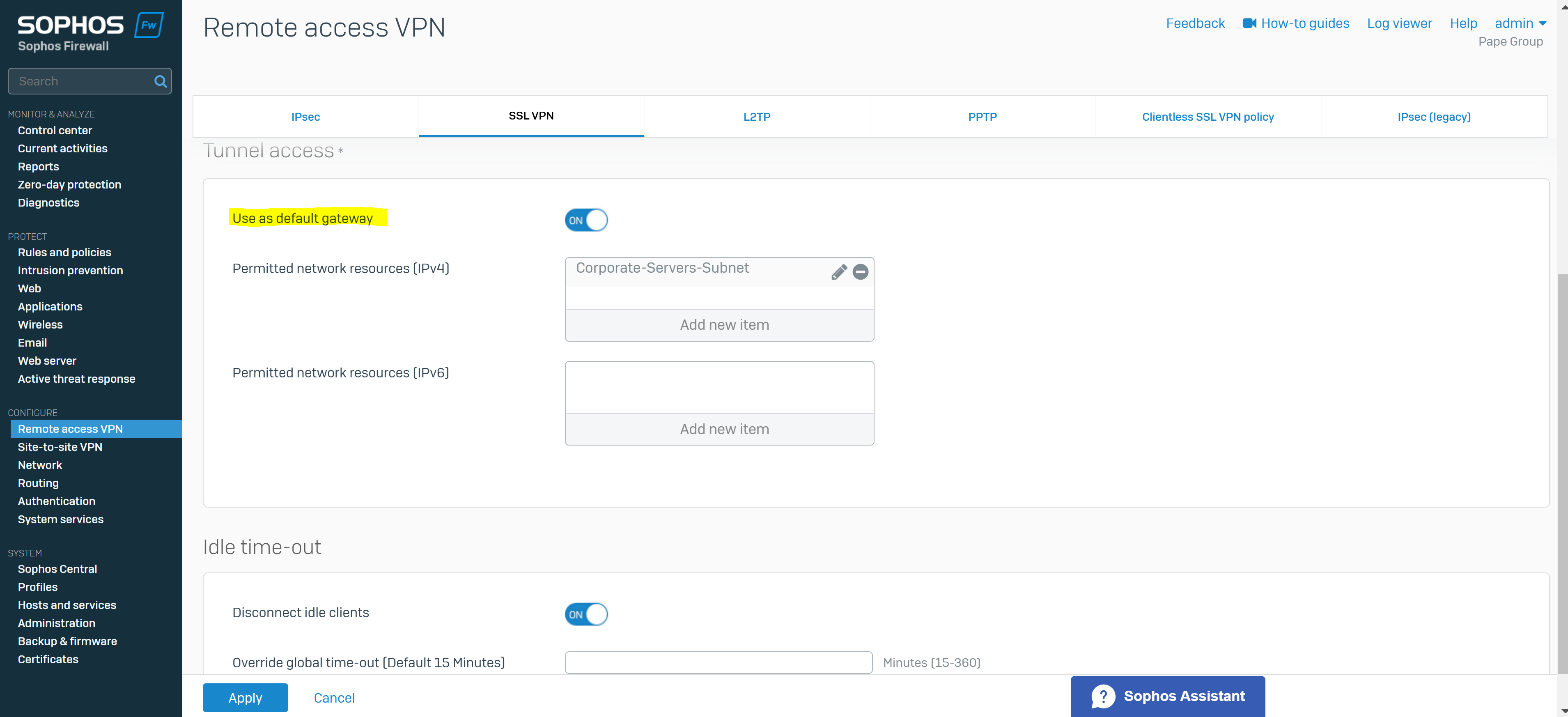
- When you configure remote access SSL VPN connections in full tunnel mode, all traffic from remote access SSL VPN users flows through the firewall
- Users can only access the permitted network resources you select in the SSL VPN policy
- Prerequisites:
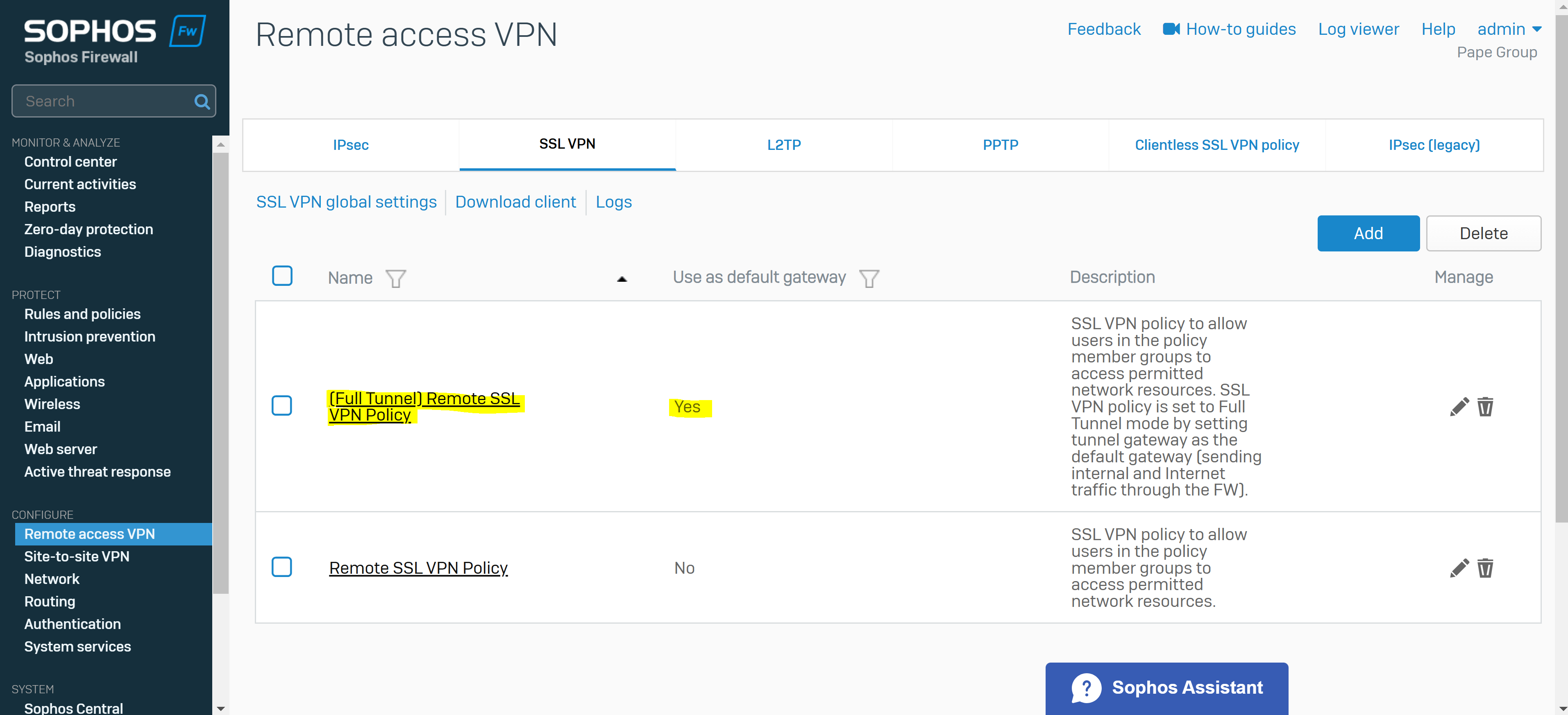
- In this demonstration, I will configure a Full tunnel SSL VPN policy in addition to the Split tunnel SSL VPN policy already defined
- Defining Split tunnel and Full tunnel SSL VPN policies follow the same configuration procedures with minor Full tunnel deployment differences
- Defining a separate authentication group for the Full tunnel SSL VPN policy
- Enabling the 'Use as default gateway' configuration parameter in the SSL VPN policy
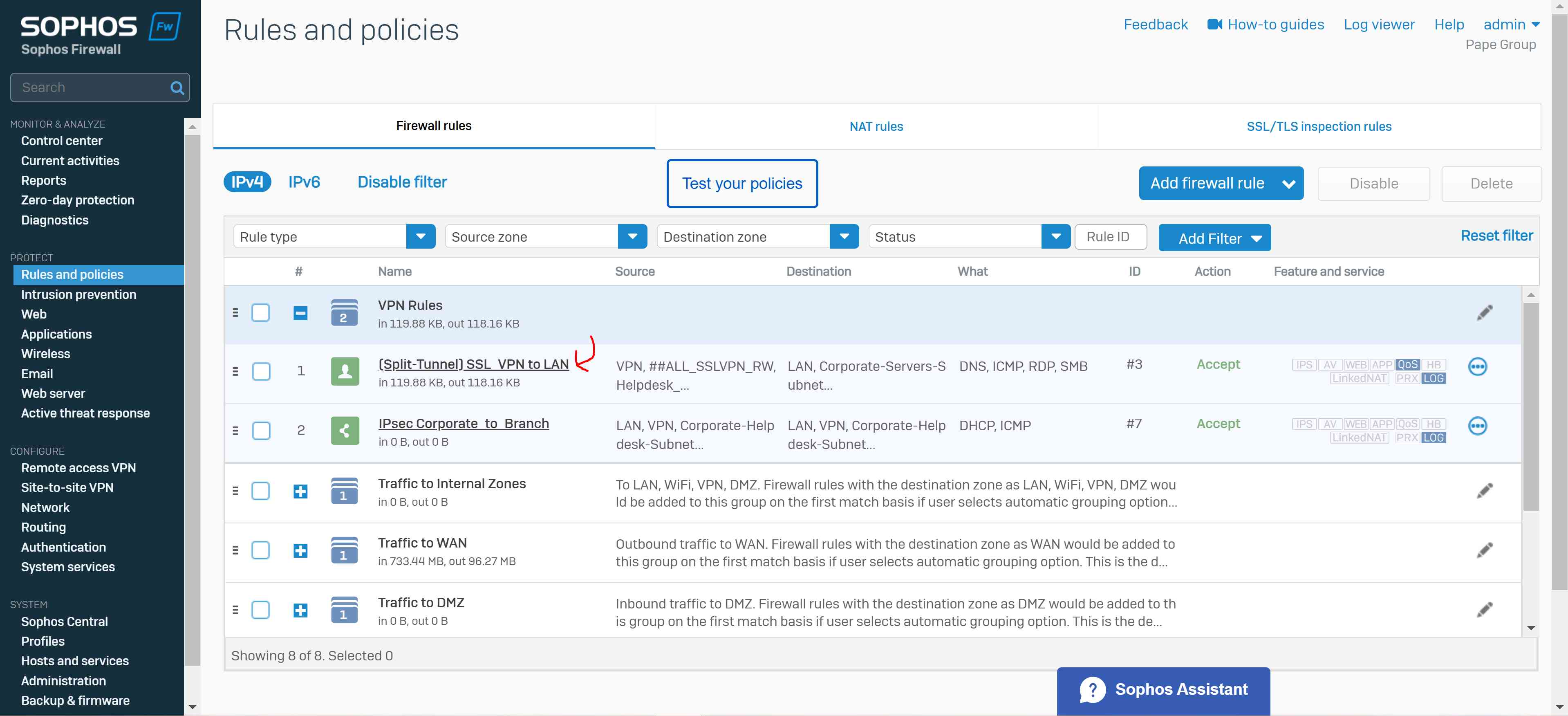
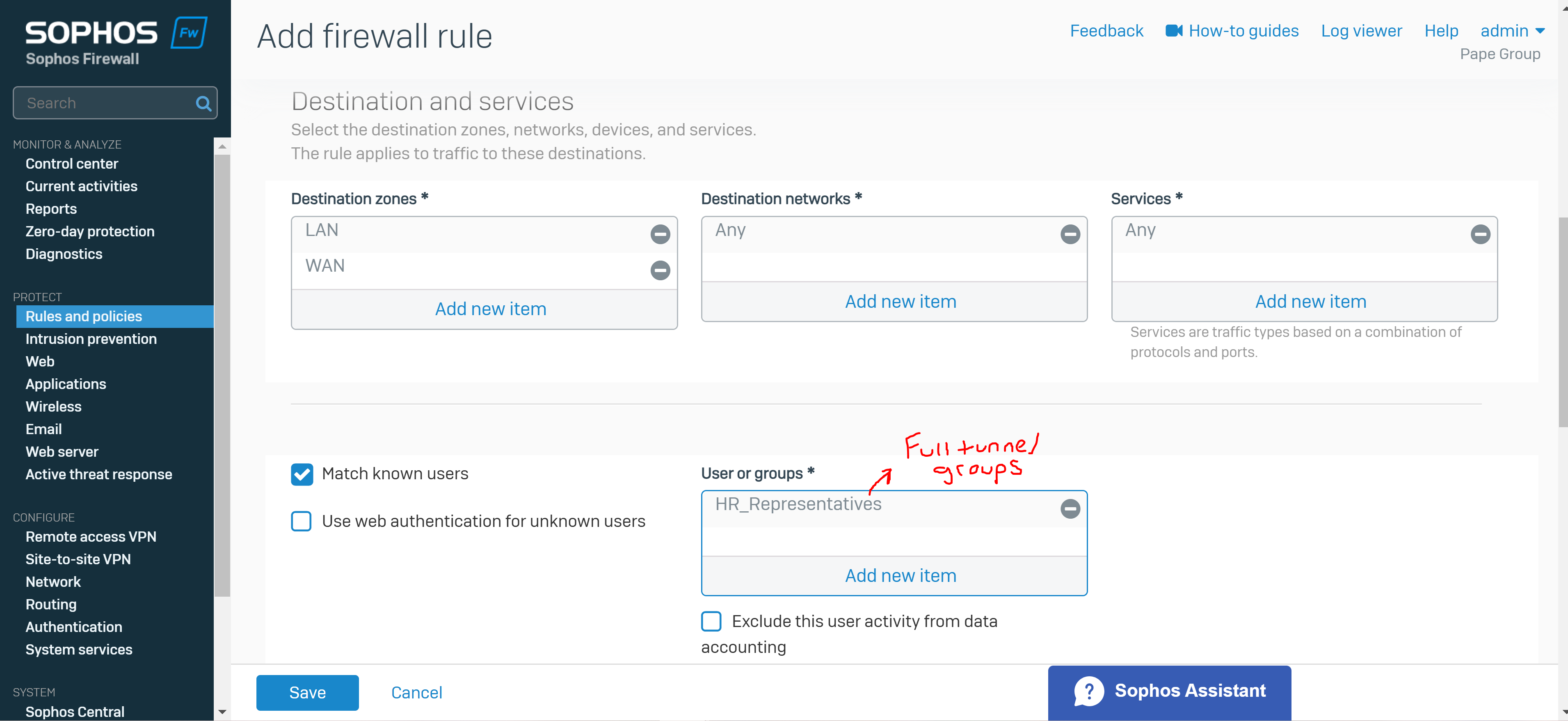
- Adding a separate firewall rule that allows the destination zones 'WAN' and 'LAN' from the source 'VPN' zone
- If utilizing multiple SSL VPN policies, enable the 'match known users' parameter within the firewall rule and select the appropriate authentication groups
- After configuration, I will verify and test the Full tunnel deployment using the Sophos Connect client on a Windows machine
SSL VPN Topology

Create a User Group & Add a User
Add SSL VPN Remote Access Policy
Add a Firewall Rule
Full Tunnel Verification via Sophos Connect Client